The Cryptographic Shield: Safeguarding Your Server. In today’s interconnected world, servers are constantly under siege from cyber threats. Data breaches, unauthorized access, and malicious attacks are commonplace, jeopardizing sensitive information and crippling operations. A robust cryptographic shield is no longer a luxury but a necessity, providing the essential protection needed to maintain data integrity, confidentiality, and the overall security of your server infrastructure.
This guide delves into the critical role cryptography plays in bolstering server security, exploring various techniques and best practices to fortify your defenses.
From understanding the intricacies of symmetric and asymmetric encryption to implementing secure access controls and intrusion detection systems, we’ll explore a comprehensive approach to server security. We’ll dissect the strengths and weaknesses of different encryption algorithms, discuss the importance of regular security audits, and provide a detailed example of a secure server configuration. By the end, you’ll possess a practical understanding of how to build a resilient cryptographic shield around your valuable server assets.
Introduction
In today’s hyper-connected world, servers are the backbone of countless businesses and organizations, holding invaluable data and powering critical applications. The digital landscape, however, presents a constantly evolving threat landscape, exposing servers to a multitude of vulnerabilities. From sophisticated malware attacks and denial-of-service (DoS) assaults to insider threats and data breaches, the potential for damage is immense, leading to financial losses, reputational damage, and legal repercussions.
The consequences of a compromised server can be catastrophic.Cryptography plays a pivotal role in mitigating these risks. It provides the fundamental tools and techniques to secure data at rest and in transit, ensuring confidentiality, integrity, and authenticity. By employing cryptographic algorithms and protocols, organizations can significantly reduce their vulnerability to cyberattacks and protect their sensitive information.
The Cryptographic Shield: A Definition
In the context of server security, a “cryptographic shield” refers to the comprehensive implementation of cryptographic techniques to protect a server and its associated data from unauthorized access, modification, or destruction. This involves a layered approach, utilizing various cryptographic methods to safeguard different aspects of the server’s operation, from securing network communication to protecting data stored on the server’s hard drives.
It’s not a single technology but rather a robust strategy encompassing encryption, digital signatures, hashing, and access control mechanisms. A strong cryptographic shield acts as a multi-faceted defense system, significantly bolstering the overall security posture of the server.
Server Vulnerabilities and Cryptographic Countermeasures
Servers face a wide array of vulnerabilities. Weak or default passwords, outdated software with known security flaws, and misconfigured network settings are common entry points for attackers. Furthermore, vulnerabilities in applications running on the server can provide further attack vectors. Cryptographic countermeasures address these threats through several key mechanisms. For instance, strong password policies and multi-factor authentication (MFA) help prevent unauthorized access.
Regular software updates and patching address known vulnerabilities, while secure coding practices minimize the risk of application-level weaknesses. Network security measures like firewalls and intrusion detection systems further enhance the server’s defenses. Finally, data encryption, both at rest and in transit, protects sensitive information even if the server is compromised.
Encryption Techniques for Server Security
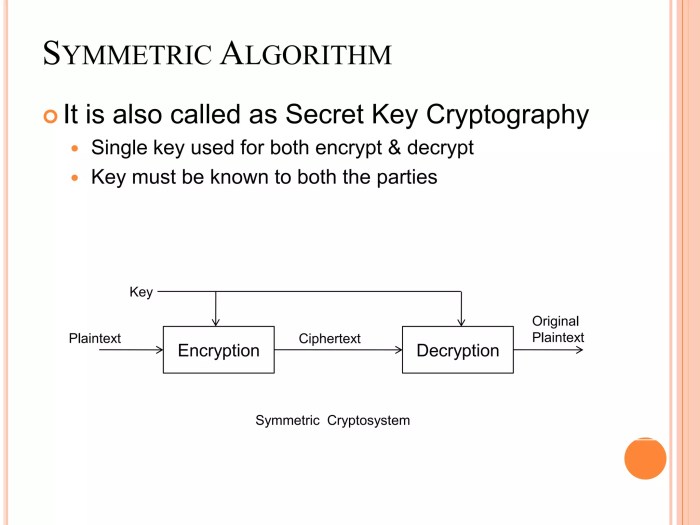
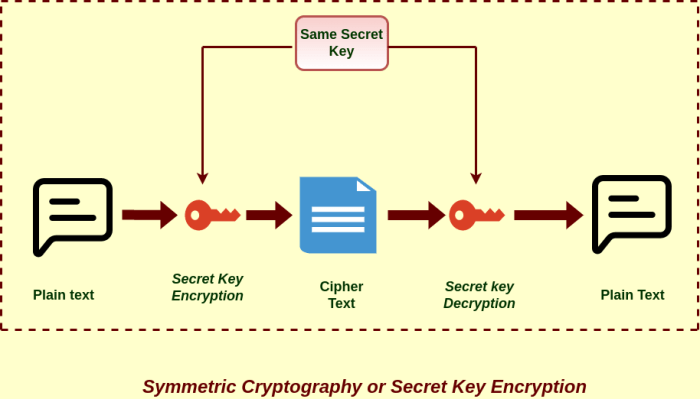
Encryption is a cornerstone of any effective cryptographic shield. Symmetric encryption, using the same key for encryption and decryption, is suitable for encrypting large amounts of data quickly. Examples include AES (Advanced Encryption Standard) and 3DES (Triple DES). Asymmetric encryption, using separate keys for encryption and decryption, is crucial for key exchange and digital signatures. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are commonly used asymmetric encryption algorithms.
The choice of encryption algorithm and key length depends on the sensitivity of the data and the desired security level. For example, AES-256 is generally considered a highly secure encryption algorithm for most applications. Hybrid encryption approaches, combining symmetric and asymmetric encryption, are often employed to leverage the strengths of both methods. This involves using asymmetric encryption to securely exchange a symmetric key, which is then used for faster symmetric encryption of the bulk data.
Encryption Techniques for Server Security
Securing servers requires robust encryption techniques to protect sensitive data from unauthorized access and manipulation. This section explores various encryption methods commonly used for server protection, highlighting their strengths and weaknesses. We’ll delve into symmetric and asymmetric encryption, the implementation of TLS/SSL certificates, and the role of digital signatures in ensuring data authenticity.
Symmetric and Asymmetric Encryption Algorithms
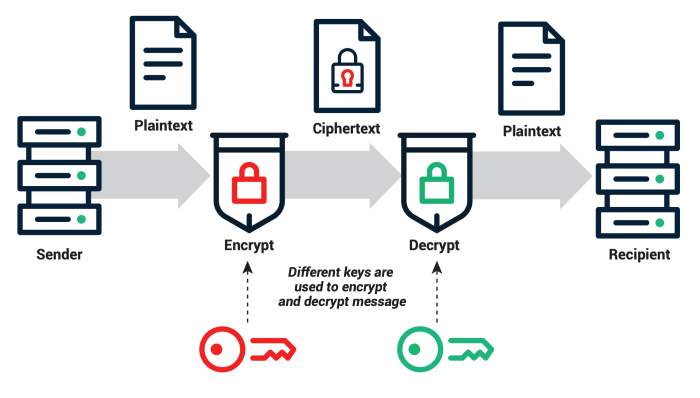
Symmetric encryption uses the same secret key for both encryption and decryption. This approach is generally faster than asymmetric encryption but requires a secure method for key exchange. Asymmetric encryption, on the other hand, employs a pair of keys: a public key for encryption and a private key for decryption. This eliminates the need for secure key exchange, as the public key can be freely distributed.
However, asymmetric encryption is computationally more intensive. Common symmetric algorithms include Advanced Encryption Standard (AES) and Triple DES (3DES), while widely used asymmetric algorithms include RSA and Elliptic Curve Cryptography (ECC). The choice between symmetric and asymmetric encryption often depends on the specific security requirements and performance considerations of the application. For instance, symmetric encryption is frequently used for encrypting large volumes of data, while asymmetric encryption is often used for key exchange and digital signatures.
TLS/SSL Certificate Implementation for Secure Communication
Transport Layer Security (TLS), and its predecessor Secure Sockets Layer (SSL), are cryptographic protocols that provide secure communication over a network. TLS/SSL certificates are digital certificates that bind a public key to an organization or individual. These certificates are issued by Certificate Authorities (CAs), trusted third-party organizations that verify the identity of the certificate holder. When a client connects to a server using TLS/SSL, the server presents its certificate to the client.
The client verifies the certificate’s authenticity by checking its chain of trust back to a trusted CA. Once verified, the client and server establish a secure connection using the server’s public key to encrypt communication. This ensures confidentiality and integrity of data exchanged between the client and server. The use of TLS/SSL is crucial for securing web traffic (HTTPS) and other network communications.
Digital Signatures for Server Software and Data Verification
Digital signatures use asymmetric cryptography to verify the authenticity and integrity of data. A digital signature is created by hashing the data and then encrypting the hash using the signer’s private key. Anyone with the signer’s public key can verify the signature by decrypting the hash and comparing it to the hash of the original data. If the hashes match, it confirms that the data has not been tampered with and originates from the claimed signer.
This mechanism is vital for verifying the authenticity of server software, ensuring that the software hasn’t been modified maliciously. It also plays a crucial role in verifying the integrity of data stored on the server, confirming that the data hasn’t been altered since it was signed.
Comparison of Encryption Algorithms
The following table compares the strengths and weaknesses of three commonly used encryption algorithms: AES, RSA, and ECC.
| Algorithm | Strength | Weakness | Typical Use Cases |
|---|---|---|---|
| AES | Fast, efficient, widely adopted, strong security with appropriate key lengths. | Vulnerable to side-channel attacks if not implemented carefully. Key management is crucial. | Data encryption at rest and in transit, file encryption. |
| RSA | Widely used, provides both encryption and digital signature capabilities. | Computationally slower than symmetric algorithms, key size needs to be large for strong security. Vulnerable to certain attacks if not properly implemented. | Key exchange, digital signatures, secure communication. |
| ECC | Provides strong security with smaller key sizes compared to RSA, faster than RSA. | Relatively newer technology, some implementation challenges remain. | Mobile devices, embedded systems, key exchange, digital signatures. |
Secure Access Control and Authentication
Securing server access is paramount to maintaining data integrity and preventing unauthorized modifications or breaches. A robust authentication and access control system forms the bedrock of a comprehensive server security strategy. This involves not only verifying the identity of users attempting to access the server but also carefully controlling what actions they can perform once authenticated. This section details the critical components of such a system.Strong passwords and multi-factor authentication (MFA) significantly strengthen server security by making unauthorized access exponentially more difficult.
Access control lists (ACLs) and role-based access control (RBAC) further refine security by granularly defining user permissions. A well-designed system combines these elements for a layered approach to protection.
Strong Passwords and Multi-Factor Authentication
Strong passwords, characterized by length, complexity, and uniqueness, are the first line of defense against unauthorized access. They should incorporate a mix of uppercase and lowercase letters, numbers, and symbols, and should be regularly changed. However, relying solely on passwords is insufficient. Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a one-time code generated by an authenticator app or sent via SMS.
This makes it significantly harder for attackers to gain access even if they obtain a password. For instance, a system requiring a password and a time-sensitive code from a Google Authenticator app provides significantly more protection than a password alone. The combination of these methods reduces the risk of successful brute-force attacks or phishing scams.
Access Control Lists (ACLs) and Role-Based Access Control (RBAC)
Access control lists (ACLs) provide granular control over access to specific server resources. Each resource, such as a file or directory, has an associated ACL that defines which users or groups have permission to read, write, or execute it. This allows for precise management of permissions, ensuring that only authorized users can access sensitive data. However, managing ACLs manually can become complex and error-prone, especially in large environments.Role-Based Access Control (RBAC) offers a more scalable and manageable approach.
RBAC assigns users to roles, each with a predefined set of permissions. This simplifies access management by grouping users with similar responsibilities and assigning permissions at the role level rather than individually. For example, a “database administrator” role might have full access to the database server, while a “web developer” role might only have read access to specific directories.
This streamlined approach reduces administrative overhead and improves consistency. Implementing RBAC often involves integrating with directory services like Active Directory or LDAP for user and group management.
Secure Authentication System Design
This section Artikels the design of a secure authentication system for a hypothetical server environment. The system incorporates strong passwords, multi-factor authentication, and role-based access control.This hypothetical server environment will use a combination of techniques. First, all users will be required to create strong, unique passwords meeting complexity requirements enforced by the system. Second, MFA will be implemented using time-based one-time passwords (TOTP) generated by an authenticator app.
Third, RBAC will be used to manage user access. Users will be assigned to roles such as “administrator,” “developer,” and “guest,” each with specific permissions defined within the system. Finally, regular security audits and password rotation policies will be implemented to further enhance security. The system will also log all authentication attempts, successful and failed, for auditing and security monitoring purposes.
This detailed logging allows for rapid identification and response to potential security incidents.
Data Integrity and Protection
Data integrity, the assurance that data has not been altered or destroyed in an unauthorized manner, is paramount for server security. Compromised data integrity can lead to incorrect decisions, financial losses, reputational damage, and legal liabilities. Cryptographic techniques play a crucial role in maintaining this integrity by providing mechanisms to detect and prevent tampering. The methods used ensure that data remains consistent and reliable, trustworthy, and verifiable.
Maintaining data integrity involves employing methods to detect and prevent unauthorized modifications. This includes both accidental corruption and malicious attacks. Effective strategies leverage cryptographic hash functions, digital signatures, and message authentication codes (MACs) to create a verifiable chain of custody for data, guaranteeing its authenticity and preventing subtle or overt alterations.
Cryptographic Hash Functions for Data Integrity
Cryptographic hash functions are one-way functions that take an input (data) of any size and produce a fixed-size output, called a hash value or digest. Even a tiny change in the input data results in a significantly different hash value. This property is essential for detecting data tampering. If the hash value of a received data file matches the previously calculated and stored hash value, it strongly suggests the data hasn’t been modified.
Several widely used cryptographic hash functions offer varying levels of security and efficiency. SHA-256 (Secure Hash Algorithm 256-bit) and SHA-512 (Secure Hash Algorithm 512-bit) are prominent examples, offering robust collision resistance, meaning it’s computationally infeasible to find two different inputs that produce the same hash value. These are frequently used in various applications, from verifying software downloads to securing digital signatures.
Another example is MD5 (Message Digest Algorithm 5), although it is now considered cryptographically broken due to vulnerabilities discovered in its collision resistance, and should not be used for security-sensitive applications.
Detecting and Preventing Data Tampering
Data tampering can be detected by comparing the hash value of the received data with the original hash value. If the values differ, it indicates that the data has been altered. This method is used extensively in various contexts, such as verifying the integrity of software downloads, ensuring the authenticity of digital documents, and protecting the integrity of databases.
Preventing data tampering requires a multi-layered approach. This includes implementing robust access control mechanisms, using secure storage solutions, regularly backing up data, and employing intrusion detection and prevention systems. Furthermore, the use of digital signatures, which combine hashing with public-key cryptography, provides an additional layer of security by verifying both the integrity and the authenticity of the data.
Examples of Cryptographic Hash Functions in Practice
Consider a scenario where a software company distributes a new software update. They calculate the SHA-256 hash of the update file before distribution and publish this hash value on their website. Users can then download the update, calculate the SHA-256 hash of the downloaded file, and compare it to the published hash. A mismatch indicates that the downloaded file has been tampered with during the download process, either accidentally or maliciously.
This prevents users from installing potentially malicious software. Similarly, blockchain technology heavily relies on cryptographic hash functions to ensure the integrity of each block in the chain, making it virtually impossible to alter past transactions without detection.
Intrusion Detection and Prevention
A robust server security strategy necessitates a multi-layered approach, and intrusion detection and prevention systems (IDS/IPS) form a critical component. These systems act as vigilant guardians, constantly monitoring network traffic and server activity for malicious behavior, significantly bolstering the defenses established by encryption and access controls. Their effectiveness, however, can be further amplified through the strategic integration of cryptographic techniques.IDS and IPS work in tandem to identify and respond to threats.
An IDS passively monitors network traffic and system logs, identifying suspicious patterns indicative of intrusions. Conversely, an IPS actively intervenes, blocking or mitigating malicious activity in real-time. This proactive approach minimizes the impact of successful attacks, preventing data breaches and system compromises.
IDS/IPS Functionality and Cryptographic Enhancement
IDS/IPS leverage various techniques to detect intrusions, including signature-based detection (matching known attack patterns), anomaly-based detection (identifying deviations from normal behavior), and statistical analysis. Cryptographic techniques play a crucial role in enhancing the reliability and security of these systems. For example, digital signatures can authenticate the integrity of system logs and configuration files, ensuring that they haven’t been tampered with by attackers.
Encrypted communication channels between the IDS/IPS and the server protect the monitoring data from eavesdropping and manipulation. Furthermore, cryptographic hashing can be used to verify the integrity of system files, enabling the IDS/IPS to detect unauthorized modifications. The use of strong encryption algorithms, such as AES-256, is essential to ensure the confidentiality and integrity of the data processed by the IDS/IPS.
Consider a scenario where an attacker attempts to inject malicious code into a server. An IDS employing cryptographic hashing would immediately detect the change in the file’s hash value, triggering an alert.
Best Practices for Implementing Intrusion Detection and Prevention
Implementing effective intrusion detection and prevention requires a comprehensive strategy encompassing both technological and procedural elements. A layered approach, combining multiple IDS/IPS solutions and security measures, is crucial to mitigating the risk of successful attacks.
The following best practices should be considered:
- Deploy a multi-layered approach: Utilize a combination of network-based and host-based IDS/IPS systems for comprehensive coverage.
- Regularly update signatures and rules: Keep your IDS/IPS software up-to-date with the latest threat intelligence to ensure effective detection of emerging threats. This is critical, as attackers constantly develop new techniques.
- Implement strong authentication and authorization: Restrict access to the IDS/IPS management console to authorized personnel only, using strong passwords and multi-factor authentication.
- Regularly review and analyze logs: Monitor IDS/IPS logs for suspicious activity and investigate any alerts promptly. This proactive approach helps identify and address potential vulnerabilities before they can be exploited.
- Integrate with other security tools: Combine IDS/IPS with other security solutions, such as firewalls, SIEM systems, and vulnerability scanners, to create a comprehensive security posture.
- Conduct regular security audits: Periodically assess the effectiveness of your IDS/IPS implementation and identify areas for improvement. This ensures the ongoing effectiveness of your security measures.
- Employ robust cryptographic techniques: Utilize strong encryption algorithms to protect communication channels and data integrity within the IDS/IPS system itself.
Regular Security Audits and Updates
Proactive security measures are crucial for maintaining the integrity and confidentiality of server data. Regular security audits and software updates form the bedrock of a robust server security strategy, minimizing vulnerabilities and mitigating potential threats. Neglecting these practices significantly increases the risk of breaches, data loss, and financial repercussions.Regular security audits and vulnerability assessments are essential for identifying weaknesses in a server’s security posture before malicious actors can exploit them.
These audits involve systematic examinations of the server’s configuration, software, and network connections to detect any misconfigurations, outdated software, or vulnerabilities that could compromise security. Vulnerability assessments, often conducted using automated scanning tools, identify known security flaws in the server’s software and operating system. The findings from these audits inform a prioritized remediation plan to address the identified risks.
Vulnerability Assessment and Remediation
Vulnerability assessments utilize automated tools to scan a server for known security flaws. These tools analyze the server’s software, operating system, and network configuration, comparing them against known vulnerabilities in databases like the National Vulnerability Database (NVD). A report detailing the identified vulnerabilities, their severity, and potential impact is generated. This report guides the remediation process, prioritizing the patching of critical vulnerabilities first.
For example, a vulnerability assessment might reveal an outdated version of Apache HTTP Server with known exploits. Remediation would involve updating the server to the latest version, eliminating the identified vulnerability.
Patching and Updating Server Software
Patching and updating server software is a critical step in mitigating security vulnerabilities. Software vendors regularly release patches to address known security flaws and improve system stability. A well-defined patching process ensures that these updates are applied promptly and efficiently. This typically involves downloading the patches from the vendor’s website, testing them in a non-production environment, and then deploying them to the production server during scheduled maintenance windows.
Failing to update software leaves the server exposed to known exploits, increasing the risk of successful attacks. For instance, neglecting to patch a known vulnerability in a database system could lead to a data breach, resulting in significant data loss and legal repercussions.
Hypothetical Server Security Audit Scenario
Imagine a hypothetical security audit of a web server hosting an e-commerce platform. The audit reveals several critical vulnerabilities: an outdated version of PHP, a missing security patch for the web server’s software, and weak password policies for administrative accounts. The assessment also identifies a lack of intrusion detection and prevention systems. The audit report would detail each vulnerability, its severity (e.g., critical, high, medium, low), and the potential impact (e.g., data breach, denial of service).
Recommendations would include updating PHP to the latest version, applying the missing security patches, implementing stronger password policies (e.g., enforcing password complexity and regular changes), and installing an intrusion detection and prevention system. Furthermore, the audit might recommend regular security awareness training for administrative personnel.
Illustrative Example: A Secure Server Configuration
This section details a secure server configuration incorporating previously discussed cryptographic methods and security practices. The example focuses on a web server, but the principles are applicable to other server types. The architecture emphasizes layered security, with each layer providing multiple defense mechanisms against potential threats.This example uses a combination of hardware and software security measures to protect sensitive data and ensure the server’s availability and integrity.
A visual representation would depict a layered approach, with each layer represented by concentric circles, progressing from the physical hardware to the application layer.
Server Hardware and Physical Security
The physical server resides in a secure data center with controlled access, environmental monitoring (temperature, humidity, power), and redundant power supplies. This ensures the server’s physical safety and operational stability. The server itself is equipped with a Trusted Platform Module (TPM) for secure boot and cryptographic key storage. The TPM helps prevent unauthorized access and ensures the integrity of the boot process.
Network connections are secured using physical security measures, such as locked cabinets and restricted access to network jacks.
Network Security
The server utilizes a dedicated, isolated network segment with strict firewall rules. Only authorized traffic is allowed in and out. A virtual private network (VPN) is used for remote access, encrypting all communication between remote users and the server. Intrusion Detection/Prevention Systems (IDS/IPS) constantly monitor network traffic for malicious activity. A web application firewall (WAF) protects the web application layer from common web attacks such as SQL injection and cross-site scripting (XSS).
Operating System and Software Security, The Cryptographic Shield: Safeguarding Your Server
The server runs a hardened operating system with regular security updates and patches applied. Principle of least privilege is strictly enforced, with user accounts possessing only the necessary permissions. All software is kept up-to-date, and regular vulnerability scans are performed. The operating system uses strong encryption for disk storage, ensuring that even if the physical server is compromised, data remains inaccessible without the decryption key.
Database Security
The database employs strong encryption at rest and in transit. Access to the database is controlled through role-based access control (RBAC), granting only authorized users specific privileges. Database auditing logs all access attempts, providing an audit trail for security monitoring. Data is regularly backed up to a separate, secure location, ensuring data recovery in case of a disaster.
Securing your server with a robust cryptographic shield is paramount for data protection. Effective server security, however, also hinges on visibility; getting your security expertise seen by the right audience requires smart SEO strategies, and you can learn how with this comprehensive guide: 12 Tips Ampuh SEO 2025: Ranking #1 dalam 60 Hari. Ultimately, a strong cryptographic shield combined with effective online marketing ensures both your data and your expertise are well-protected and easily discoverable.
Application Security
The web application employs robust input validation and sanitization to prevent injection attacks. Secure coding practices are followed to minimize vulnerabilities. HTTPS is used to encrypt all communication between the web server and clients. Regular penetration testing and code reviews are conducted to identify and address potential vulnerabilities. Session management is secure, using short-lived sessions with appropriate measures to prevent session hijacking.
Key Management
A robust key management system is implemented, using a hardware security module (HSM) to securely store and manage cryptographic keys. Key rotation is performed regularly to mitigate the risk of key compromise. Access to the key management system is strictly controlled and logged. This ensures the confidentiality and integrity of cryptographic keys used throughout the system.
Security Monitoring and Auditing
A centralized security information and event management (SIEM) system collects and analyzes security logs from various sources, including the operating system, firewall, IDS/IPS, and database. This allows for real-time monitoring of security events and facilitates proactive threat detection. Regular security audits are performed to verify the effectiveness of security controls and identify any weaknesses. A detailed audit trail is maintained for all security-related activities.
Concluding Remarks
Securing your server requires a multi-layered approach that integrates robust cryptographic techniques with proactive security measures. By understanding and implementing the strategies Artikeld—from choosing appropriate encryption algorithms and implementing strong authentication protocols to conducting regular security audits and staying updated on the latest vulnerabilities—you can significantly reduce your risk profile. Building a strong cryptographic shield isn’t a one-time event; it’s an ongoing process of vigilance, adaptation, and continuous improvement.
Investing in robust server security is not merely a cost; it’s a strategic imperative in today’s digital landscape, safeguarding your data, your reputation, and your business.
Detailed FAQs: The Cryptographic Shield: Safeguarding Your Server
What are the common vulnerabilities that servers face?
Common vulnerabilities include SQL injection, cross-site scripting (XSS), denial-of-service (DoS) attacks, and unauthorized access attempts through weak passwords or misconfigurations.
How often should I conduct security audits?
Regular security audits should be performed at least annually, and more frequently depending on the sensitivity of the data and the level of risk.
What is the difference between IDS and IPS?
An Intrusion Detection System (IDS) detects malicious activity, while an Intrusion Prevention System (IPS) actively blocks or prevents such activity.
What are some examples of cryptographic hash functions?
SHA-256, SHA-512, and MD5 are examples, although MD5 is considered cryptographically broken and should not be used for security-sensitive applications.