The Cryptographic Edge: Server Protection Strategies is paramount in today’s digital landscape, where cyber threats are constantly evolving. This exploration delves into the multifaceted world of server security, examining how cryptographic techniques form the bedrock of robust defense mechanisms. We’ll cover encryption methods, authentication protocols, key management, intrusion detection, and much more, providing a comprehensive guide to safeguarding your valuable server assets.
From understanding the nuances of symmetric and asymmetric encryption to implementing multi-factor authentication and navigating the complexities of secure key management, this guide offers practical strategies and best practices for bolstering your server’s defenses. We’ll also explore the role of VPNs, WAFs, and regular security audits in building a layered security approach that effectively mitigates a wide range of threats, from data breaches to sophisticated cyberattacks.
By understanding and implementing these strategies, you can significantly reduce your vulnerability and protect your critical data and systems.
Introduction: The Cryptographic Edge: Server Protection Strategies
The digital landscape is increasingly hostile, with cyber threats targeting servers relentlessly. Robust server security is no longer a luxury; it’s a critical necessity for businesses of all sizes. A single successful attack can lead to data breaches, financial losses, reputational damage, and even legal repercussions. This necessitates a multi-layered approach to server protection, with cryptography playing a central role in fortifying defenses against sophisticated attacks.Cryptography provides the foundation for secure communication and data protection within server environments.
It employs mathematical techniques to transform sensitive information into an unreadable format, protecting it from unauthorized access and manipulation. By integrating various cryptographic techniques into server infrastructure, organizations can significantly enhance their security posture and mitigate the risks associated with data breaches and other cyberattacks.
Cryptographic Techniques for Server Security
Several cryptographic techniques are instrumental in securing servers. These methods work in tandem to create a robust defense system. Effective implementation requires a deep understanding of each technique’s strengths and limitations. For example, relying solely on one method might leave vulnerabilities exploitable by determined attackers.Symmetric-key cryptography uses a single secret key for both encryption and decryption. Algorithms like AES (Advanced Encryption Standard) are widely used for securing data at rest and in transit.
The strength of symmetric-key cryptography lies in its speed and efficiency, but secure key exchange remains a crucial challenge.Asymmetric-key cryptography, also known as public-key cryptography, uses a pair of keys: a public key for encryption and a private key for decryption. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are prominent examples. Asymmetric cryptography is particularly useful for digital signatures and key exchange, addressing the key distribution limitations of symmetric-key methods.
However, it’s generally slower than symmetric-key cryptography.Hashing algorithms, such as SHA-256 and SHA-3, create one-way functions that generate unique fingerprints (hashes) of data. These hashes are used for data integrity verification, ensuring data hasn’t been tampered with. Any alteration to the data will result in a different hash value, immediately revealing the compromise. While hashing doesn’t encrypt data, it’s an essential component of many security protocols.Digital certificates, based on public-key infrastructure (PKI), bind public keys to identities.
They are crucial for secure communication over networks, verifying the authenticity of servers and clients. HTTPS, for instance, relies heavily on digital certificates to ensure secure connections between web browsers and servers. A compromised certificate can severely undermine the security of a system.
Implementation Considerations
The successful implementation of cryptographic techniques hinges on several factors. Proper key management is paramount, requiring secure generation, storage, and rotation of cryptographic keys. Regular security audits and vulnerability assessments are essential to identify and address weaknesses in the server’s cryptographic defenses. Staying updated with the latest cryptographic best practices and adapting to emerging threats is crucial for maintaining a strong security posture.
Furthermore, the chosen cryptographic algorithms should align with the sensitivity of the data being protected and the level of security required. Weak or outdated algorithms can be easily cracked, negating the intended protection.
Encryption Techniques for Server Data Protection
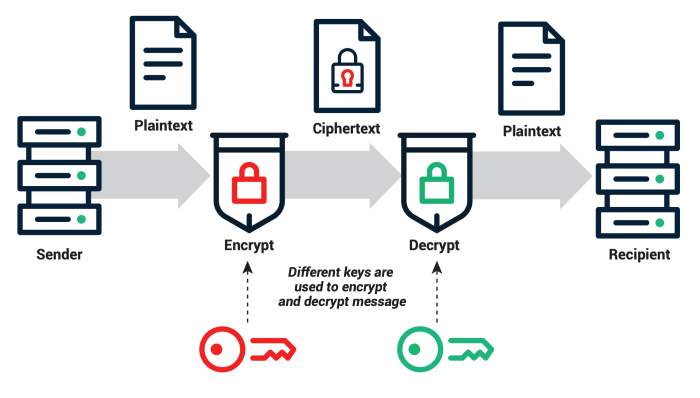
Robust server security necessitates a multi-layered approach, with encryption forming a crucial cornerstone. Effective encryption safeguards sensitive data both while at rest (stored on the server) and in transit (moving across networks). This section delves into the key encryption techniques and their practical applications in securing server infrastructure.
Symmetric and Asymmetric Encryption Algorithms
Symmetric encryption uses the same secret key for both encryption and decryption. This offers speed and efficiency, making it ideal for encrypting large volumes of data. Examples include AES (Advanced Encryption Standard) and 3DES (Triple DES). Conversely, asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption. This allows for secure key exchange and digital signatures, vital for authentication and data integrity.
RSA and ECC (Elliptic Curve Cryptography) are prominent examples. The choice between symmetric and asymmetric encryption often depends on the specific security needs; symmetric encryption is generally faster for bulk data, while asymmetric encryption is crucial for key management and digital signatures. A hybrid approach, combining both methods, is often the most practical solution.
Encryption at Rest
Encryption at rest protects data stored on server hard drives, SSDs, and other storage media. This is crucial for mitigating data breaches resulting from physical theft or unauthorized server access. Implementation involves encrypting data before it’s written to storage and decrypting it upon retrieval. Full-disk encryption (FDE) solutions, such as BitLocker for Windows and FileVault for macOS, encrypt entire storage devices.
File-level encryption provides granular control, allowing specific files or folders to be encrypted. Database encryption protects sensitive data within databases, often using techniques like transparent data encryption (TDE). Regular key rotation and secure key management are essential for maintaining the effectiveness of encryption at rest.
Encryption in Transit
Encryption in transit safeguards data as it travels across networks, protecting against eavesdropping and man-in-the-middle attacks. The most common method is Transport Layer Security (TLS), previously known as Secure Sockets Layer (SSL). TLS uses asymmetric encryption for initial key exchange and symmetric encryption for the bulk data transfer. Virtual Private Networks (VPNs) create secure tunnels over public networks, encrypting all traffic passing through them.
Implementing HTTPS for web servers ensures secure communication between clients and servers. Regular updates to TLS certificates and protocols are vital to maintain the security of in-transit data.
Hypothetical Server Encryption Strategy
A robust server encryption strategy might combine several techniques. For example, the server’s operating system and all storage devices could be protected with full-disk encryption (e.g., BitLocker). Databases could utilize transparent data encryption (TDE) to protect sensitive data at rest. All communication with the server, including web traffic and remote administration, should be secured using HTTPS and VPNs, respectively, providing encryption in transit.
Regular security audits and penetration testing are essential to identify and address vulnerabilities. A strong key management system, with regular key rotation, is also crucial to maintain the overall security posture. This layered approach ensures that data is protected at multiple levels, mitigating the risk of data breaches regardless of the attack vector.
Authentication and Authorization Mechanisms
Securing server access is paramount for maintaining data integrity and preventing unauthorized access. Robust authentication and authorization mechanisms are the cornerstones of this security strategy, ensuring only legitimate users and processes can interact with sensitive server resources. This section will delve into the critical aspects of these mechanisms, focusing on multi-factor authentication and common authentication protocols.Authentication verifies the identity of a user or process, while authorization determines what actions that authenticated entity is permitted to perform.
These two processes work in tandem to provide a comprehensive security layer. Effective implementation minimizes the risk of breaches and data compromise.
Multi-Factor Authentication (MFA) for Server Access
Multi-factor authentication significantly enhances server security by requiring users to provide multiple forms of verification before granting access. This layered approach makes it exponentially more difficult for attackers to gain unauthorized entry, even if they possess one authentication factor, such as a password. Implementing MFA involves combining something the user knows (password), something the user has (security token), and something the user is (biometric data).
The use of MFA drastically reduces the success rate of brute-force and phishing attacks, commonly used to compromise server accounts. For example, even if an attacker obtains a user’s password through phishing, they will still be blocked from accessing the server unless they also possess the physical security token or can provide the required biometric verification.
Common Authentication Protocols in Server Environments
Several authentication protocols are widely used in server environments, each offering different levels of security and complexity. The choice of protocol depends on factors such as the sensitivity of the data, the network infrastructure, and the resources available. Understanding the strengths and weaknesses of each protocol is crucial for effective security planning.
Comparison of Authentication Methods
| Method | Strengths | Weaknesses | Use Cases |
|---|---|---|---|
| Password-based authentication | Simple to implement and understand. | Susceptible to phishing, brute-force attacks, and password reuse. | Low-security internal systems, legacy applications (when combined with other security measures). |
| Multi-factor authentication (MFA) | Highly secure, resistant to many common attacks. | Can be more complex to implement and manage, may impact user experience. | High-security systems, access to sensitive data, remote server access. |
| Public Key Infrastructure (PKI) | Strong authentication and encryption capabilities. | Complex to set up and manage, requires careful certificate management. | Secure communication channels, digital signatures, secure web servers (HTTPS). |
| Kerberos | Provides strong authentication within a network, uses ticket-granting system for secure communication. | Requires a centralized Kerberos server, can be complex to configure. | Large enterprise networks, Active Directory environments. |
| RADIUS | Centralized authentication, authorization, and accounting (AAA) for network access. | Can be a single point of failure if not properly configured and secured. | Wireless networks, VPN access, remote access servers. |
Secure Key Management Practices
Cryptographic keys are the lifeblood of secure server operations. Their proper generation, storage, and management are paramount to maintaining the confidentiality, integrity, and availability of sensitive data. Weak key management practices represent a significant vulnerability, often exploited by attackers to compromise entire systems. This section details best practices for secure key management, highlighting associated risks and providing a step-by-step guide for implementation.
Effective key management involves a multi-faceted approach encompassing key generation, storage, rotation, and destruction. Each stage presents unique challenges and necessitates robust security measures to mitigate potential threats. Failure at any point in this lifecycle can expose sensitive information and render security controls ineffective.
Key Generation Best Practices
Generating cryptographically strong keys is the foundational step in secure key management. Keys must be sufficiently long to resist brute-force attacks and generated using robust, cryptographically secure random number generators (CSPRNGs). Avoid using predictable or easily guessable values. The strength of an encryption system is directly proportional to the strength of its keys. Weak keys, generated using flawed algorithms or insufficient entropy, can be easily cracked, compromising the security of the entire system.
For example, a short, predictable key might be easily discovered through brute-force attacks, allowing an attacker to decrypt sensitive data. Using a CSPRNG ensures the randomness and unpredictability necessary for robust key security.
Secure Key Storage Mechanisms
Once generated, keys must be stored securely, protected from unauthorized access or compromise. This often involves a combination of hardware security modules (HSMs), encrypted databases, and robust access control mechanisms. HSMs offer a physically secure environment for storing and managing cryptographic keys, protecting them from software-based attacks. Encrypted databases provide an additional layer of protection, ensuring that even if the database is compromised, the keys remain inaccessible without the decryption key.
Implementing robust access control mechanisms, such as role-based access control (RBAC), limits access to authorized personnel only. Failure to secure key storage can lead to catastrophic data breaches, potentially exposing sensitive customer information, financial records, or intellectual property. For instance, a poorly secured database containing encryption keys could be easily accessed by malicious actors, granting them complete access to encrypted data.
Robust server protection relies heavily on cryptographic strategies like encryption and digital signatures. Maintaining data integrity is paramount, and just as you need a well-defined plan for your digital security, you also need a plan for your physical well-being; consider checking out this resource on healthy eating for weight loss: 8 Resep Rahasia Makanan Sehat: Turun 10kg dalam 30 Hari.
Returning to server security, remember that strong authentication mechanisms are equally vital for preventing unauthorized access and maintaining the overall cryptographic edge.
Key Rotation and Revocation Procedures
Regular key rotation is crucial for mitigating the risk of key compromise. Periodically replacing keys with newly generated ones minimizes the window of vulnerability in case a key is compromised. A well-defined key revocation process is equally important, enabling immediate disabling of compromised keys to prevent further exploitation. Key rotation schedules should be determined based on risk assessment and regulatory compliance requirements.
For example, a financial institution handling sensitive financial data might implement a more frequent key rotation schedule compared to a company with less sensitive data. This proactive approach minimizes the impact of potential breaches by limiting the duration of exposure to compromised keys.
Step-by-Step Guide for Implementing a Secure Key Management System
- Conduct a thorough risk assessment: Identify and assess potential threats and vulnerabilities related to key management.
- Define key management policies and procedures: Establish clear guidelines for key generation, storage, rotation, and revocation.
- Select appropriate key management tools: Choose HSMs, encryption software, or other tools that meet security requirements.
- Implement robust access control mechanisms: Limit access to keys based on the principle of least privilege.
- Establish key rotation schedules: Define regular intervals for key replacement based on risk assessment.
- Develop key revocation procedures: Artikel steps for disabling compromised keys immediately.
- Regularly audit and monitor the system: Ensure compliance with security policies and identify potential weaknesses.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) play a crucial role in securing servers by identifying and responding to malicious activities. Their effectiveness is significantly enhanced through the integration of cryptographic techniques, providing a robust layer of defense against sophisticated attacks. These systems leverage cryptographic principles to verify data integrity, authenticate users, and detect anomalies indicative of intrusions.IDPS systems utilize cryptographic techniques to enhance security by verifying the authenticity and integrity of system data and communications.
This verification process allows the IDPS to distinguish between legitimate system activity and malicious actions. By leveraging cryptographic hashes and digital signatures, IDPS can detect unauthorized modifications or intrusions.
Digital Signatures and Hashing in Intrusion Detection, The Cryptographic Edge: Server Protection Strategies
Digital signatures and hashing algorithms are fundamental to intrusion detection. Digital signatures, created using asymmetric cryptography, provide authentication and non-repudiation. A system’s legitimate software and configuration files can be digitally signed, allowing the IDPS to verify their integrity. Any unauthorized modification will invalidate the signature, triggering an alert. Hashing algorithms, on the other hand, generate a unique fingerprint (hash) of a file or data stream.
The IDPS can compare the current hash of a file with a previously stored, legitimate hash. Any discrepancy indicates a potential intrusion. This process is highly effective in detecting unauthorized file modifications or the introduction of malware. The combination of digital signatures and hashing provides a comprehensive approach to data integrity verification.
Common IDPS Techniques and Effectiveness
Several techniques are employed by IDPS systems to detect and prevent intrusions. Their effectiveness varies depending on the sophistication of the attack and the specific configuration of the IDPS.
- Signature-based detection: This method involves comparing system events against a database of known attack signatures. It’s effective against known attacks but can be bypassed by novel or polymorphic malware. For example, a signature-based system might detect a known SQL injection attempt by recognizing specific patterns in network traffic or database queries.
- Anomaly-based detection: This approach establishes a baseline of normal system behavior and flags deviations from that baseline as potential intrusions. It’s effective against unknown attacks but can generate false positives if the baseline is not accurately established. For instance, a sudden surge in network traffic from an unusual source could trigger an anomaly-based alert, even if the traffic is not inherently malicious.
- Heuristic-based detection: This technique relies on rules and algorithms to identify suspicious patterns in system activity. It combines aspects of signature-based and anomaly-based detection and offers a more flexible approach. A heuristic-based system might flag a process attempting to access sensitive files without proper authorization, even if the specific method isn’t in a known attack signature database.
- Intrusion Prevention: Beyond detection, many IDPS systems offer prevention capabilities. This can include blocking malicious network traffic, terminating suspicious processes, or implementing access control restrictions based on detected threats. For example, an IDPS could automatically block a connection attempt from a known malicious IP address or prevent a user from accessing a restricted directory.
Virtual Private Networks (VPNs) and Secure Remote Access
VPNs are crucial for securing server access and data transmission, especially in today’s distributed work environment. They establish encrypted connections between a user’s device and a server, creating a secure tunnel through potentially insecure networks like the public internet. This protection extends to both the integrity and confidentiality of data exchanged between the two points. The benefits of VPN implementation extend beyond simple data protection, contributing significantly to a robust layered security strategy.VPNs achieve this secure connection by employing various cryptographic protocols, effectively shielding sensitive information from unauthorized access and eavesdropping.
The choice of protocol often depends on the specific security requirements and the level of compatibility needed with existing infrastructure. Understanding these protocols is key to appreciating the overall security posture provided by a VPN solution.
VPN Cryptographic Protocols
IPsec (Internet Protocol Security) and OpenVPN are two widely used cryptographic protocols that underpin the security of many VPN implementations. IPsec operates at the network layer (Layer 3 of the OSI model), offering strong encryption and authentication for IP packets. It utilizes various encryption algorithms, such as AES (Advanced Encryption Standard), and authentication mechanisms, such as ESP (Encapsulating Security Payload) and AH (Authentication Header), to ensure data confidentiality and integrity.
OpenVPN, on the other hand, is a more flexible and open-source solution that operates at the application layer (Layer 7), allowing for greater customization and compatibility with a broader range of devices and operating systems. It often employs TLS (Transport Layer Security) or SSL (Secure Sockets Layer) for encryption and authentication. The choice between IPsec and OpenVPN often depends on factors such as performance requirements, security needs, and the level of administrative control desired.
For example, IPsec is often preferred in environments requiring high performance and robust security at the network level, while OpenVPN might be more suitable for situations requiring greater flexibility and customization.
VPNs in a Layered Security Approach
VPNs function as a critical component within a multi-layered security architecture for server protection. They complement other security measures such as firewalls, intrusion detection systems, and robust access control lists. Imagine a scenario where a company uses a firewall to control network traffic, restricting access to the server based on IP addresses and port numbers. This initial layer of defense is further strengthened by a VPN, which encrypts all traffic between the user and the server, even if the user is connecting from a public Wi-Fi network.
This layered approach ensures that even if one security layer is compromised, others remain in place to protect the server and its data. For instance, if an attacker manages to bypass the firewall, the VPN encryption will prevent them from accessing or decrypting the transmitted data. This layered approach significantly reduces the overall attack surface and improves the resilience of the server against various threats.
The combination of strong authentication, encryption, and secure key management within the VPN, coupled with other security measures, creates a robust and comprehensive security strategy.
Web Application Firewalls (WAFs) and Secure Coding Practices
Web Application Firewalls (WAFs) and secure coding practices represent crucial layers of defense in protecting server-side applications from a wide range of attacks. While WAFs act as a perimeter defense, scrutinizing incoming traffic, secure coding practices address vulnerabilities at the application’s core. A robust security posture necessitates a combined approach leveraging both strategies.WAFs utilize various techniques, including cryptographic principles, to identify and block malicious requests.
They examine HTTP headers, cookies, and the request body itself, looking for patterns indicative of known attacks. This analysis often involves signature-based detection, where known attack patterns are matched against incoming requests, and anomaly detection, which identifies deviations from established traffic patterns. Cryptographic principles play a role in secure communication between the WAF and the web application, ensuring that sensitive data exchanged during inspection remains confidential and integrity is maintained.
For example, HTTPS encryption protects the communication channel between the WAF and the web server, preventing eavesdropping and tampering. Furthermore, digital signatures can verify the authenticity of the WAF and the web application, preventing man-in-the-middle attacks.
WAFs’ Leverage of Cryptographic Principles
WAFs leverage several cryptographic principles to enhance their effectiveness. Digital signatures, for instance, verify the authenticity of the WAF and the web server, ensuring that communications are not intercepted and manipulated by malicious actors. The use of HTTPS, employing SSL/TLS encryption, safeguards the confidentiality and integrity of data exchanged between the WAF and the web application, preventing eavesdropping and tampering.
Hashing algorithms are often employed to detect modifications to application code or configuration files, providing an additional layer of integrity verification. Public key infrastructure (PKI) can be utilized for secure key exchange and authentication, enhancing the overall security of the WAF and its interaction with other security components.
Secure Coding Practices to Minimize Vulnerabilities
Secure coding practices focus on eliminating vulnerabilities at the application’s source code level. This involves following established security guidelines and best practices throughout the software development lifecycle (SDLC). Key aspects include input validation, which prevents malicious data from being processed by the application, output encoding, which prevents cross-site scripting (XSS) attacks, and the secure management of session tokens and cookies, mitigating session hijacking risks.
The use of parameterized queries or prepared statements in database interactions helps prevent SQL injection attacks. Regular security audits and penetration testing are also crucial to identify and address vulnerabilities before they can be exploited. Furthermore, adhering to established coding standards and utilizing secure libraries and frameworks can significantly reduce the risk of introducing vulnerabilities.
Common Web Application Vulnerabilities and Cryptographic Countermeasures
Secure coding practices and WAFs work in tandem to mitigate various web application vulnerabilities. The following table illustrates some common vulnerabilities and their corresponding cryptographic countermeasures:
| Vulnerability | Description | Cryptographic Countermeasure | Implementation Notes |
|---|---|---|---|
| SQL Injection | Malicious SQL code injected into input fields to manipulate database queries. | Parameterized queries, input validation, and output encoding. | Use prepared statements or parameterized queries to prevent direct SQL execution. Validate all user inputs rigorously. |
| Cross-Site Scripting (XSS) | Injection of malicious scripts into web pages viewed by other users. | Output encoding, Content Security Policy (CSP), and input validation. | Encode all user-supplied data before displaying it on a web page. Implement a robust CSP to control the resources the browser is allowed to load. |
| Cross-Site Request Forgery (CSRF) | Tricking a user into performing unwanted actions on a web application in which they’re currently authenticated. | Synchronizer tokens, double submit cookie, and HTTP referer checks. | Use unique, unpredictable tokens for each request. Verify that the request originates from the expected domain. |
| Session Hijacking | Unauthorized access to a user’s session by stealing their session ID. | HTTPS, secure cookie settings (HttpOnly, Secure flags), and regular session timeouts. | Always use HTTPS to protect session data in transit. Configure cookies to prevent client-side access and ensure timely session expiration. |
Regular Security Audits and Vulnerability Assessments
Proactive security assessments are crucial for maintaining the integrity and confidentiality of server data. Regular audits and vulnerability assessments act as a preventative measure, identifying weaknesses before malicious actors can exploit them. This proactive approach significantly reduces the risk of data breaches, minimizes downtime, and ultimately saves organizations considerable time and resources in the long run. Failing to conduct regular security assessments increases the likelihood of costly incidents and reputational damage.Regular security audits and vulnerability assessments are essential for identifying and mitigating potential security risks within server infrastructure.
These assessments, including penetration testing, provide a comprehensive understanding of the current security posture, highlighting weaknesses that could be exploited by attackers. Cryptographic analysis plays a vital role in identifying vulnerabilities within encryption algorithms, key management practices, and other cryptographic components of the system. By systematically examining the cryptographic implementation, security professionals can uncover weaknesses that might otherwise go unnoticed.
Proactive Security Assessments and Penetration Testing
Proactive security assessments, including penetration testing, simulate real-world attacks to identify vulnerabilities. Penetration testing goes beyond simple vulnerability scanning by attempting to exploit identified weaknesses to determine the impact. This process allows organizations to understand the effectiveness of their security controls and prioritize remediation efforts based on the severity of potential breaches. For example, a penetration test might simulate a SQL injection attack to determine if an application is vulnerable to data manipulation or exfiltration.
Successful penetration testing results in a detailed report outlining identified vulnerabilities, their potential impact, and recommended remediation steps. This information is critical for improving the overall security posture of the server infrastructure.
Cryptographic Analysis in Vulnerability Identification
Cryptographic analysis is a specialized field focusing on evaluating the strength and weaknesses of cryptographic algorithms and implementations. This involves examining the mathematical foundations of the algorithms, analyzing the key management processes, and assessing the overall security of the cryptographic system. For instance, a cryptographic analysis might reveal a weakness in a specific cipher mode, leading to the identification of a vulnerability that could allow an attacker to decrypt sensitive data.
The findings from cryptographic analysis are instrumental in identifying vulnerabilities related to encryption, key management, and digital signatures. This analysis is crucial for ensuring that the cryptographic components of a server’s security architecture are robust and resilient against attacks.
Checklist for Conducting Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments should be a scheduled and documented process. A comprehensive checklist ensures that all critical aspects of the server’s security are thoroughly examined. The frequency of these assessments depends on the criticality of the server and the sensitivity of the data it handles.
- Inventory of all servers and network devices: A complete inventory provides a baseline for assessment.
- Vulnerability scanning: Use automated tools to identify known vulnerabilities in operating systems, applications, and network devices.
- Penetration testing: Simulate real-world attacks to assess the effectiveness of security controls.
- Cryptographic analysis: Review the strength and implementation of encryption algorithms and key management practices.
- Review of security logs: Analyze server logs to detect suspicious activity and potential breaches.
- Configuration review: Verify that security settings are properly configured and updated.
- Access control review: Examine user access rights and privileges to ensure principle of least privilege is adhered to.
- Patch management review: Verify that all systems are up-to-date with the latest security patches.
- Documentation review: Ensure that security policies and procedures are current and effective.
- Remediation of identified vulnerabilities: Implement necessary fixes and updates to address identified weaknesses.
- Reporting and documentation: Maintain a detailed record of all assessments, findings, and remediation efforts.
Incident Response and Recovery Strategies
A robust incident response plan is crucial for mitigating the impact of cryptographic compromises and server breaches. Effective strategies minimize data loss, maintain business continuity, and restore trust. This section details procedures for responding to such incidents and recovering from server compromises, emphasizing data integrity restoration.
Responding to Cryptographic Compromises
Responding to a security breach involving cryptographic compromises requires immediate and decisive action. The first step is to contain the breach by isolating affected systems to prevent further damage. This might involve disconnecting compromised servers from the network, disabling affected accounts, and changing all compromised passwords. A thorough investigation is then needed to determine the extent of the compromise, identifying the compromised cryptographic keys and the data affected.
This investigation should include log analysis, network traffic analysis, and forensic examination of affected systems. Based on the findings, remediation steps are taken, which may include revoking compromised certificates, generating new cryptographic keys, and implementing stronger security controls. Finally, a post-incident review is crucial to identify weaknesses in the existing security infrastructure and implement preventative measures to avoid future incidents.
Data Integrity Restoration After a Server Compromise
Restoring data integrity after a server compromise is a complex process requiring careful planning and execution. The process begins with verifying the integrity of backup data. This involves checking the integrity checksums or hashes of backup files to ensure they haven’t been tampered with. If the backups are deemed reliable, they are used to restore the affected systems.
However, if the backups are compromised, more sophisticated methods may be necessary, such as using data recovery tools to retrieve data from damaged storage media. After data restoration, a thorough validation process is required to ensure the integrity and accuracy of the restored data. This might involve comparing the restored data against known good copies or performing data reconciliation checks.
Finally, security hardening measures are implemented to prevent future compromises, including patching vulnerabilities, strengthening access controls, and implementing more robust monitoring systems.
Incident Response Plan Flowchart
The following describes a flowchart illustrating the steps involved in an incident response plan. The flowchart begins with the detection of a security incident. This could be triggered by an alert from an intrusion detection system, a security audit, or a user report. The next step is to initiate the incident response team, which assesses the situation and determines the scope and severity of the incident.
Containment measures are then implemented to limit the damage and prevent further spread. This may involve isolating affected systems, blocking malicious traffic, and disabling compromised accounts. Once the incident is contained, an investigation is launched to determine the root cause and extent of the breach. This may involve analyzing logs, conducting forensic analysis, and interviewing witnesses.
After the investigation, remediation steps are implemented to address the root cause and prevent future incidents. This might involve patching vulnerabilities, implementing stronger security controls, and educating users. Finally, a post-incident review is conducted to identify lessons learned and improve the incident response plan. The flowchart concludes with the restoration of normal operations and the implementation of preventative measures.
This iterative process ensures continuous improvement of the organization’s security posture.
Future Trends in Cryptographic Server Protection
The landscape of server security is constantly evolving, driven by advancements in cryptographic techniques and the emergence of new threats. Understanding these future trends is crucial for organizations seeking to maintain robust server protection in the face of increasingly sophisticated attacks. This section explores emerging cryptographic approaches, the challenges posed by quantum computing, and the rise of post-quantum cryptography.
Emerging Cryptographic Techniques and Their Impact on Server Security
Several emerging cryptographic techniques promise to significantly enhance server security. Homomorphic encryption, for instance, allows computations to be performed on encrypted data without decryption, offering enhanced privacy in cloud computing and distributed ledger technologies. This is particularly relevant for servers handling sensitive data where maintaining confidentiality during processing is paramount. Lattice-based cryptography, another promising area, offers strong security properties and is considered resistant to attacks from both classical and quantum computers.
Its potential applications range from securing communication channels to protecting data at rest on servers. Furthermore, advancements in zero-knowledge proofs enable verification of information without revealing the underlying data, a critical feature for secure authentication and authorization protocols on servers. The integration of these techniques into server infrastructure will lead to more resilient and privacy-preserving systems.
Challenges Posed by Quantum Computing to Current Cryptographic Methods
Quantum computing poses a significant threat to widely used cryptographic algorithms, such as RSA and ECC, which underpin much of current server security. Quantum computers, leveraging the principles of quantum mechanics, have the potential to break these algorithms far more efficiently than classical computers. This would compromise the confidentiality and integrity of data stored and transmitted by servers, potentially leading to large-scale data breaches and system failures.
For example, Shor’s algorithm, a quantum algorithm, can factor large numbers exponentially faster than the best known classical algorithms, effectively breaking RSA encryption. This necessitates a proactive approach to mitigating the risks associated with quantum computing.
Post-Quantum Cryptography and Its Implications for Server Protection
Post-quantum cryptography (PQC) focuses on developing cryptographic algorithms that are resistant to attacks from both classical and quantum computers. Several promising PQC candidates are currently under evaluation by standardization bodies, including lattice-based, code-based, and multivariate cryptography. The transition to PQC requires a phased approach, involving algorithm selection, key management updates, and the integration of new cryptographic libraries into server software.
This transition will not be immediate and will require significant investment in research, development, and infrastructure upgrades. However, the long-term implications are crucial for maintaining the security and integrity of server systems in a post-quantum world. Successful implementation of PQC will be essential to safeguarding sensitive data and preventing widespread disruptions.
Ending Remarks
Securing your servers in the face of escalating cyber threats demands a multi-pronged, proactive approach. This guide has highlighted the crucial role of cryptography in achieving robust server protection. By implementing the encryption techniques, authentication mechanisms, key management practices, and security audits discussed, you can significantly strengthen your defenses against various attacks. Remember that server security is an ongoing process requiring vigilance and adaptation to emerging threats.
Staying informed about the latest advancements in cryptographic techniques and security best practices is vital for maintaining a secure and resilient server infrastructure.
FAQ Resource
What are the common types of cryptographic attacks?
Common attacks include brute-force attacks, man-in-the-middle attacks, and chosen-plaintext attacks. Understanding these helps in choosing appropriate countermeasures.
How often should I conduct security audits?
Regular security audits, ideally quarterly or semi-annually, are crucial for identifying and addressing vulnerabilities before they can be exploited.
What is the role of a Web Application Firewall (WAF)?
A WAF acts as a security layer for web applications, filtering malicious traffic and protecting against common web application vulnerabilities.
How can I choose the right encryption algorithm?
Algorithm selection depends on your specific security needs and the sensitivity of your data. Consider factors like key length, performance, and the algorithm’s resistance to known attacks.