Decoding Server Security with Cryptography unveils the critical role cryptography plays in safeguarding server infrastructure. This exploration delves into the core principles of server security, examining common threats and the various cryptographic techniques employed to mitigate them. From symmetric and asymmetric encryption to digital signatures and secure communication protocols like SSL/TLS, we’ll unravel the complexities of securing sensitive data and maintaining the integrity of online systems.
The journey will also cover key management strategies, secure implementation practices within server-side applications, and advanced cryptographic methods for enhanced protection.
We will navigate the landscape of different cryptographic algorithms, comparing their strengths and weaknesses in real-world scenarios. The discussion will extend beyond theoretical concepts, providing practical examples and actionable insights for developers and security professionals seeking to bolster their server security posture. This comprehensive guide aims to equip readers with the knowledge and understanding necessary to confidently navigate the challenges of securing their servers in today’s ever-evolving threat landscape.
Introduction to Server Security and Cryptography

Server security is paramount in today’s digital landscape. Protecting sensitive data and ensuring the availability and integrity of server resources requires a multi-layered approach, with cryptography playing a crucial role. Understanding the fundamental principles of server security and the application of cryptographic techniques is essential for building robust and resilient systems.
Fundamental Principles of Server Security
Server security relies on several core principles. Confidentiality ensures that only authorized individuals can access sensitive data. Integrity guarantees that data remains unaltered and trustworthy. Availability ensures that authorized users can access data and resources when needed. Authentication verifies the identity of users and systems attempting to access the server.
Authorization controls what actions authenticated users are permitted to perform. These principles, working in concert, form the bedrock of a secure server environment. Breaches in any of these areas can lead to significant consequences, ranging from data loss to financial penalties and reputational damage.
The Role of Cryptography in Securing Servers
Cryptography provides the technical mechanisms to implement the principles of server security. It uses mathematical algorithms to transform data, making it unintelligible to unauthorized parties (confidentiality). It also provides methods to verify data integrity and authenticity. For instance, digital signatures ensure data hasn’t been tampered with and can be verified as originating from a specific source. Encryption protects data in transit (e.g., using HTTPS) and at rest (e.g., encrypting databases).
Key management, a critical aspect of cryptography, governs the secure creation, storage, and distribution of cryptographic keys. Without robust key management, even the strongest cryptographic algorithms are vulnerable.
Common Server Security Threats
Servers face a constant barrage of threats. SQL injection attacks exploit vulnerabilities in database applications to gain unauthorized access to data. Cross-site scripting (XSS) attacks inject malicious scripts into websites, potentially stealing user data or hijacking sessions. Denial-of-service (DoS) attacks overwhelm servers with traffic, rendering them unavailable to legitimate users. Man-in-the-middle (MITM) attacks intercept communication between a server and a client, potentially stealing sensitive information.
Zero-day exploits leverage previously unknown vulnerabilities, requiring immediate patching and mitigation strategies. Regular security audits and vulnerability assessments are crucial for identifying and addressing potential weaknesses.
Comparison of Cryptographic Algorithms
The choice of cryptographic algorithm depends on the specific security requirements and the context of its application. Several factors influence this choice, including security strength, performance overhead, and key size. Below is a comparison of some commonly used algorithms:
| Algorithm | Type | Key Size (bits) | Use Cases |
|---|---|---|---|
| AES | Symmetric | 128, 192, 256 | Data encryption, disk encryption |
| RSA | Asymmetric | 1024, 2048, 4096 | Digital signatures, key exchange |
| ECC | Asymmetric | 256, 384, 521 | Digital signatures, key exchange (often preferred for resource-constrained environments) |
| SHA-256 | Hashing | 256 | Data integrity verification, password hashing |
Symmetric Encryption Techniques for Server Security: Decoding Server Security With Cryptography
Symmetric encryption is a cornerstone of server security, providing confidentiality for sensitive data stored and processed on servers. It relies on a single, secret key to both encrypt and decrypt information, making it a crucial tool for protecting data from unauthorized access. Understanding its mechanisms, strengths, and limitations is essential for implementing robust server security measures.Symmetric encryption operates by using a secret key to transform plaintext data into an unreadable ciphertext.
This ciphertext can then only be decrypted back into plaintext using the same secret key. The strength of the encryption relies entirely on the secrecy and length of this key. The encryption process itself involves a complex mathematical algorithm that scrambles the data in a way that’s computationally infeasible to reverse without the key.
Symmetric Encryption Algorithms
Several symmetric encryption algorithms are commonly used in server security, each with its own strengths and weaknesses. The choice of algorithm often depends on the specific security requirements, performance needs, and the size of the data being protected.
- Advanced Encryption Standard (AES): Widely considered the gold standard for symmetric encryption, AES is a block cipher that uses keys of 128, 192, or 256 bits. Its strength comes from its complex mathematical operations and the length of its keys, making it highly resistant to brute-force attacks. AES is used extensively in various applications, including securing HTTPS connections and encrypting data at rest.
- Data Encryption Standard (DES): An older algorithm, DES uses a 56-bit key and is now considered insecure due to its relatively short key length, making it vulnerable to brute-force attacks with modern computing power. It’s largely obsolete for securing sensitive data in modern server environments.
- Triple DES (3DES): This algorithm addresses some of DES’s weaknesses by applying the DES algorithm three times with either two or three different keys. While more secure than DES, 3DES is slower than AES and is also gradually being phased out in favor of AES.
Advantages and Disadvantages of Symmetric Encryption in Server Security
Symmetric encryption offers several advantages, but also has limitations that must be considered when implementing it in a server security strategy.
- Advantages: Speed and efficiency are key advantages. Symmetric encryption algorithms are generally faster than asymmetric encryption methods, making them suitable for encrypting large volumes of data. They are also relatively simple to implement.
- Disadvantages: Key distribution and management present a significant challenge. Securely sharing the secret key between communicating parties without compromising its confidentiality is crucial. The number of keys required increases exponentially with the number of parties involved, making key management complex in large networks. Additionally, compromise of the single key compromises all encrypted data.
Scenario: Protecting Server-Side Database with Symmetric Encryption
Imagine a financial institution storing sensitive customer data in a server-side database. To protect this data at rest, the institution could employ symmetric encryption. Before storing the data, a strong encryption algorithm like AES-256 is used to encrypt it using a securely generated and managed key. This key is stored separately, possibly using hardware security modules (HSMs) for enhanced protection.
When a legitimate user requests access to the data, the server decrypts it using the same key, ensuring only authorized personnel can access the sensitive information. The encrypted data remains unreadable even if the database itself is compromised, protecting the customer’s financial information.
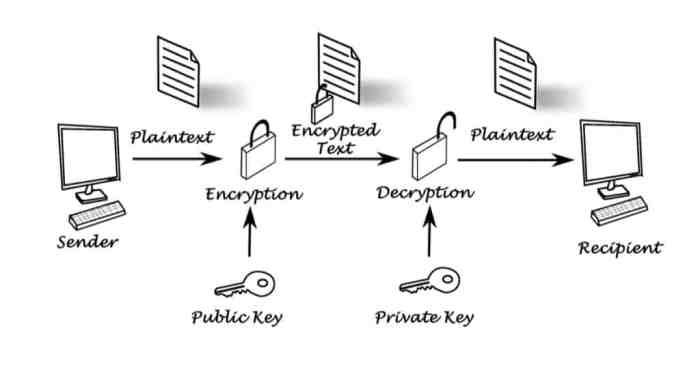
Asymmetric Encryption Techniques for Server Security
Asymmetric encryption, also known as public-key cryptography, forms a crucial cornerstone of modern server security. Unlike symmetric encryption, which relies on a single secret key shared between communicating parties, asymmetric encryption utilizes a pair of keys: a public key and a private key. This key pair enables secure communication even without prior key exchange, significantly enhancing security and scalability, especially in large-scale networks.
This section delves into the mechanics and applications of asymmetric encryption techniques in securing server communications.
Public-Key Cryptography Fundamentals
Public-key cryptography operates on the principle of a mathematically linked key pair. The public key can be freely distributed, while the private key must remain strictly confidential. Data encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. This asymmetry allows for secure key exchange and digital signatures, essential components of secure server infrastructure.
The strength of these systems relies on computationally hard problems, meaning that deriving the private key from the public key is practically infeasible with current computing power.
Examples of Asymmetric Encryption Algorithms
Several robust asymmetric encryption algorithms are widely employed in securing server communications. Two prominent examples are RSA and Elliptic Curve Cryptography (ECC).RSA (Rivest-Shamir-Adleman) is a widely used algorithm based on the mathematical difficulty of factoring large numbers. The algorithm involves generating two large prime numbers and using them to create the public and private keys. The security of RSA depends on the size of these prime numbers; larger numbers offer greater resistance to attacks.
For example, a 2048-bit RSA key is considered secure for most applications.ECC, on the other hand, relies on the algebraic structure of elliptic curves over finite fields. ECC offers comparable security to RSA but with significantly smaller key sizes. This makes ECC particularly attractive for resource-constrained environments, such as mobile devices and embedded systems, while still providing strong cryptographic protection for server communications.
A 256-bit ECC key offers similar security to a 3072-bit RSA key.
Comparison of Symmetric and Asymmetric Encryption
Symmetric and asymmetric encryption methods offer distinct advantages and disadvantages. Symmetric encryption, using a single secret key, is significantly faster than asymmetric encryption. However, the secure distribution of the secret key presents a challenge. Asymmetric encryption, with its public and private key pair, solves this key distribution problem but is computationally more expensive.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Management | Difficult; requires secure key exchange | Easier; public key can be openly distributed |
| Speed | Fast | Slow |
| Key Size | Relatively small | Relatively large |
| Scalability | Less scalable for large networks | More scalable |
| Use Cases | Data encryption in transit and at rest | Key exchange, digital signatures, authentication |
Use Cases for Asymmetric Encryption in Securing Server Communications
Asymmetric encryption plays a vital role in various aspects of server security. Its primary uses include:* Secure Key Exchange: Asymmetric encryption facilitates the secure exchange of symmetric keys. This is crucial because symmetric encryption is faster but requires a secure method to share the secret key initially. The public key is used to encrypt the symmetric key, which can then be safely transmitted.
The recipient uses their private key to decrypt and obtain the symmetric key for subsequent communication.* Digital Signatures: Asymmetric encryption enables the creation of digital signatures, verifying the authenticity and integrity of data. A server can digitally sign its responses, ensuring clients receive messages unaltered and originating from the legitimate server.* Authentication: Asymmetric encryption forms the basis of many authentication protocols.
For example, SSL/TLS (Secure Sockets Layer/Transport Layer Security), widely used to secure web traffic, utilizes asymmetric encryption for the initial handshake and key exchange, before switching to faster symmetric encryption for data transfer.* Secure Email: Asymmetric encryption ensures the confidentiality and integrity of email communications. Public keys are used to encrypt messages, ensuring only the recipient with the corresponding private key can decrypt and read them.
Digital Signatures and Authentication
Digital signatures are a crucial element of server security, providing a mechanism to verify the authenticity and integrity of data exchanged between servers and clients. They leverage cryptographic techniques to ensure that data hasn’t been tampered with and originates from a trusted source, significantly bolstering the security of server communications and transactions. This is particularly vital in scenarios where sensitive information is transmitted, such as financial transactions or user authentication.Digital signatures function similarly to handwritten signatures but offer significantly stronger security guarantees.
Unlike handwritten signatures, which are easily forged, digital signatures are computationally infeasible to replicate without the private key of the signer. This cryptographic strength forms the basis for trust and verification in various online applications.
Digital Signature Creation and Verification
Creating and verifying a digital signature involves a series of steps using asymmetric cryptography. The process relies on a pair of keys: a private key, known only to the signer, and a public key, which is widely distributed. The private key is used for signing, while the public key is used for verification.The creation process begins with the signer generating a cryptographic hash of the data to be signed.
This hash, a unique fingerprint of the data, is then encrypted using the signer’s private key. The resulting encrypted hash is the digital signature. The recipient then uses the signer’s public key to decrypt the signature and regenerate the hash of the received data. If the two hashes match, the signature is valid, confirming both the authenticity and integrity of the data.
Ensuring Data Integrity and Authenticity with Digital Signatures
Digital signatures guarantee data integrity by ensuring that any alteration to the data after signing will result in a mismatch between the original and regenerated hashes during verification. Even a minor change, like a single character alteration, will produce a completely different hash, invalidating the signature. This prevents unauthorized modifications and ensures that the received data is exactly as it was originally sent.Authenticity is guaranteed because only the holder of the private key can create a valid signature.
The successful verification using the public key confirms that the data originated from the entity possessing the corresponding private key. This prevents impersonation and ensures that the data source is trustworthy.
Implementing Digital Signatures for Server Authentication
Implementing digital signatures for server authentication involves a step-by-step process:
1. Key Generation
The server generates a pair of RSA or ECC keys (private and public). The private key must be securely stored, while the public key is made available to clients.
2. Data Preparation
The server prepares the data to be signed. This often involves creating a hash of relevant data like certificates, timestamps, and server details.
3. Signature Creation
The server uses its private key to digitally sign the prepared data hash, creating the digital signature.
4. Signature Transmission
Decoding server security with cryptography involves understanding various encryption techniques and their applications. For a deeper dive into the practical implementation of these methods, check out this comprehensive guide: Cryptography for Server Admins: A Comprehensive Overview. This resource will help you effectively secure your server infrastructure using cryptographic principles, ultimately strengthening your overall security posture.
The server transmits the signed data (including the digital signature) to the client.
5. Signature Verification
The client receives the data and uses the server’s public key to verify the digital signature. This involves decrypting the signature and comparing the regenerated hash with a hash of the received data.
6. Authentication
If the hashes match, the client authenticates the server, confirming the data’s authenticity and integrity. If they don’t match, the client rejects the data as potentially tampered with or originating from an unauthorized source.
Secure Communication Protocols (SSL/TLS)
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a cryptographic protocol designed to provide secure communication over a network, particularly the internet. It ensures data confidentiality, integrity, and authenticity between a client and a server. Understanding its architecture and handshake process is crucial for implementing robust server security.
SSL/TLS Architecture
SSL/TLS operates in a layered architecture. The core functionality resides in the SSL/TLS record protocol, which provides a reliable, secure transport for higher-level application protocols like HTTP (creating HTTPS). Below this sits the TLS handshake protocol, responsible for negotiating the security parameters of the connection. At the lowest level, the protocol relies on underlying transport protocols like TCP to handle data transmission.
The client and server each run a TLS implementation, negotiating security settings and managing encryption/decryption. The process involves several steps, culminating in a secure channel established between the two parties.
The SSL/TLS Handshake Process
The SSL/TLS handshake is a crucial phase establishing a secure connection. It involves a series of messages exchanged between the client and server to negotiate the cipher suite, authenticate the server, and establish a shared secret key. This process is complex but can be summarized in several key stages:
- Client Hello: The client initiates the handshake by sending a message containing its supported cipher suites, compression methods, and a randomly generated client random number.
- Server Hello: The server responds with a message selecting a cipher suite from the client’s list, a randomly generated server random number, and its certificate. The certificate contains the server’s public key and is digitally signed by a Certificate Authority (CA).
- Certificate Verification: The client verifies the server’s certificate, ensuring it’s valid and issued by a trusted CA. This step confirms the server’s identity.
- Server Key Exchange/Server Hello Done: The server sends its key exchange message, depending on the chosen cipher suite. This might include a Diffie-Hellman key exchange to establish a shared secret. The “Server Hello Done” message signals the completion of the server’s part of the handshake.
- Client Key Exchange: The client generates its pre-master secret and sends it to the server, encrypted using the server’s public key.
- Change Cipher Spec: Both client and server send a “Change Cipher Spec” message, indicating they will now use the newly established cipher suite for communication.
- Finished: Both client and server send a “Finished” message, which is encrypted using the shared secret. This message authenticates the connection and ensures both parties are using the same shared secret.
SSL/TLS Cipher Suites, Decoding Server Security with Cryptography
Cipher suites define the combination of cryptographic algorithms used for encryption, authentication, and key exchange in SSL/TLS. They specify the key exchange algorithm (e.g., RSA, Diffie-Hellman), the bulk encryption algorithm (e.g., AES, ChaCha20), the message authentication code (MAC) algorithm (e.g., HMAC-SHA256), and the pseudorandom function (PRF) algorithm. Choosing a strong cipher suite is crucial for security. Examples of commonly used cipher suites include TLS_AES_256_GCM_SHA384 and TLS_CHACHA20_POLY1305_SHA256.
The selection process during the handshake prioritizes the strongest mutually supported cipher suite between the client and the server. Older and less secure cipher suites should be disabled to prevent vulnerabilities.
Visual Representation of the SSL/TLS Handshake
Imagine a flowchart. The process begins with the client (left side) initiating a connection. An arrow points to the server (right side). The client sends a “Client Hello” message (box 1), containing its preferences. The server responds with a “Server Hello” (box 2), including its certificate.
A verification step (box 3) follows where the client checks the certificate’s validity. Next, a key exchange (box 4) happens, usually using Diffie-Hellman, establishing a shared secret. Both client and server then send “Change Cipher Spec” messages (box 5), switching to the encrypted channel. Finally, both send “Finished” messages (box 6), confirming the secure connection is established.
Each box represents a message exchange, and the arrows indicate the direction of communication. The entire process is a series of carefully choreographed message exchanges, resulting in a secure, authenticated communication channel.
Key Management and Distribution
Effective key management is paramount to the overall security of a server environment. Without robust strategies for key generation, storage, distribution, and revocation, even the strongest cryptographic algorithms are vulnerable. Compromised keys can lead to data breaches, unauthorized access, and significant financial losses. This section will explore the challenges inherent in key management and detail best practices for mitigating these risks.
Challenges of Key Management in Server Security
Key management presents a multifaceted challenge. The sheer number of keys required in a complex server environment, coupled with the need for secure storage and efficient distribution, creates significant logistical and security hurdles. Maintaining key confidentiality, integrity, and availability across the lifecycle of each key requires meticulous planning and implementation. Furthermore, the need for regular key rotation to mitigate the risk of long-term compromise adds to the complexity.
A single point of failure in the key management system can have catastrophic consequences, compromising the entire security infrastructure. The legal and regulatory requirements surrounding key management, particularly for sensitive data, add another layer of complexity that organizations must navigate.
Best Practices for Secure Key Storage and Distribution
Secure key storage relies on a combination of hardware and software solutions. Hardware security modules (HSMs) offer a robust solution, providing tamper-resistant environments for key generation, storage, and cryptographic operations. Software solutions, while less secure than HSMs, can be used in conjunction with strong access controls and encryption to protect keys. Key distribution should leverage secure channels, such as encrypted connections (e.g., TLS), to prevent interception.
The use of key distribution centers (KDCs) or other trusted third parties can simplify the process while maintaining security. Regular key rotation, with a defined schedule and automated processes, minimizes the window of vulnerability in case of a compromise. A comprehensive audit trail, tracking all key access and management events, is essential for accountability and incident response.
Key Management Systems
Various key management systems (KMS) exist, each with its strengths and weaknesses. Centralized KMSs provide a single point of control over all keys, simplifying management but increasing the risk associated with a single point of failure. Decentralized systems distribute key management responsibilities, enhancing resilience but increasing complexity. Cloud-based KMSs offer scalability and ease of management but introduce reliance on a third-party provider.
Hierarchical KMSs establish a hierarchy of keys, where higher-level keys control lower-level keys, offering a granular control mechanism. The choice of KMS depends on the specific needs and risk tolerance of the organization.
Secure Key Management Strategy for a Hypothetical Server Environment
Consider a hypothetical e-commerce platform with sensitive customer data. A secure key management strategy would involve:
- Employing HSMs for storing cryptographic keys used for encryption and signing.
- Implementing a centralized KMS with robust access controls and audit logging.
- Using a hierarchical key structure to manage keys for different services and data types.
- Establishing a strict key rotation policy, with automated key generation and replacement.
- Leveraging TLS for secure communication during key distribution and other sensitive operations.
- Implementing regular security assessments and penetration testing to identify and address vulnerabilities.
This strategy combines hardware and software security measures, centralizes management for efficiency, and incorporates a hierarchical structure for granular control and resilience. The automated key rotation minimizes risk, and the comprehensive audit trail aids in incident response and compliance. Regular security assessments are crucial for ongoing maintenance and protection.
Implementing Cryptography in Server-Side Applications
Integrating cryptography into server-side applications is crucial for securing sensitive data and ensuring the integrity of online services. This involves selecting appropriate cryptographic algorithms, implementing them securely within the application’s codebase, and managing cryptographic keys effectively. Failure to do so can lead to significant security vulnerabilities and data breaches.
This section details the practical aspects of integrating cryptographic libraries, highlights crucial security considerations, and Artikels common vulnerabilities to avoid. It also provides best practices for robust cryptographic implementation in server-side environments.
Integrating Cryptographic Libraries
Integrating cryptographic libraries involves selecting a suitable library for your programming language and incorporating its functions into your server-side code. Popular choices include OpenSSL (C), Bouncy Castle (Java), and cryptography (Python). These libraries provide functions for various cryptographic operations, such as encryption, decryption, hashing, and digital signature generation and verification. For example, in Python, using the cryptography library, symmetric encryption with AES could be implemented as follows:
from cryptography.fernet import Fernet
# Generate a key
key = Fernet.generate_key()
f = Fernet(key)
# Encrypt data
message = b"This is a secret message"
encrypted_message = f.encrypt(message)
# Decrypt data
decrypted_message = f.decrypt(encrypted_message)
Remember to securely store and manage the generated key; this example is for illustrative purposes only and lacks robust key management.
Security Considerations in Cryptographic Implementation
Several critical security considerations must be addressed when implementing cryptography in server-side applications. These include choosing strong and up-to-date algorithms, properly handling keys, and validating all inputs to prevent vulnerabilities like padding oracle attacks. The choice of algorithm should be based on security requirements, performance needs, and the length of the key used. Key management is paramount; weak key management practices can easily negate the security benefits of strong cryptographic algorithms.
Input validation is crucial to prevent attackers from manipulating inputs to trigger vulnerabilities. Finally, regular security audits and updates are essential to maintain the security posture of the system.
Common Cryptographic Implementation Vulnerabilities
Improper cryptographic implementation can lead to several vulnerabilities. These include:
- Weak or outdated algorithms: Using algorithms known to be vulnerable to attacks renders the system susceptible to compromise.
- Improper key management: Poor key generation, storage, and rotation practices can expose keys to attackers, leading to data breaches.
- Padding oracle attacks: These attacks exploit vulnerabilities in how padding is handled during encryption and decryption.
- Side-channel attacks: These attacks exploit information leaked during cryptographic operations, such as timing or power consumption variations.
- Implementation bugs: Errors in the code implementing cryptographic algorithms can introduce vulnerabilities that attackers can exploit.
Best Practices for Secure Cryptographic Implementation
Implementing cryptography securely requires careful attention to detail. The following best practices should be followed:
- Use strong and up-to-date algorithms: Stay informed about algorithm recommendations from reputable sources like NIST.
- Employ robust key management practices: Use secure key generation, storage, and rotation methods. Consider using hardware security modules (HSMs).
- Validate all inputs rigorously: Prevent attackers from manipulating inputs to trigger vulnerabilities.
- Use established libraries and frameworks: Leverage well-vetted libraries to reduce the risk of implementation errors.
- Regularly update and patch your systems: Stay current with security updates to address known vulnerabilities.
- Perform regular security audits: Conduct periodic assessments to identify and mitigate potential weaknesses.
- Follow secure coding practices: Implement secure coding principles to prevent common vulnerabilities.
Advanced Cryptographic Techniques for Server Security
Beyond the foundational cryptographic techniques, several advanced methods significantly bolster server security. These techniques offer enhanced protection against sophisticated attacks and ensure data integrity and confidentiality at a higher level. This section will explore key advanced cryptographic methods and their applications in securing server environments.
Hashing Algorithms for Password Storage
Secure password storage is paramount. Instead of storing passwords in plain text, which is highly vulnerable, hashing algorithms are employed. These algorithms generate a one-way function, transforming a password into a fixed-size string of characters (a hash). Even if the hash is compromised, reversing it to obtain the original password is computationally infeasible. SHA-256 and SHA-3 are prominent examples.
SHA-256 (Secure Hash Algorithm 256-bit) is a widely used hashing algorithm, providing a 256-bit hash value. SHA-3 (Secure Hash Algorithm 3), a more recent standard, offers improved security properties and resistance to certain types of attacks. The use of salt (a random string added to the password before hashing) further enhances security by preventing rainbow table attacks, which pre-compute hashes for common passwords.
The combination of strong hashing algorithms and salting is crucial for robust password protection.
Message Authentication Codes (MACs)
Message Authentication Codes (MACs) provide both data integrity and authentication. A MAC is a cryptographic checksum generated using a secret key. This key is shared between the sender and receiver. The sender computes a MAC for the message and sends it along with the message itself. The receiver independently computes the MAC using the same key and compares it to the received MAC.
If they match, it confirms that the message has not been tampered with and originated from an authorized source. HMAC (Hash-based Message Authentication Code) is a widely used MAC algorithm that leverages cryptographic hash functions like SHA-256 or SHA-3. MACs are vital for ensuring the authenticity and integrity of data transmitted between servers and clients.
Digital Certificates in Server Authentication
Digital certificates play a crucial role in server authentication, establishing trust between a server and a client. A digital certificate is an electronic document that binds a public key to an identity (e.g., a website’s domain name). It’s issued by a trusted Certificate Authority (CA), verifying the server’s identity. Clients can use the certificate to verify the server’s authenticity before establishing a secure connection.
The certificate contains the server’s public key, allowing clients to encrypt data for secure communication. This process prevents man-in-the-middle attacks, where an attacker intercepts the communication and impersonates the server. The use of digital certificates ensures that clients connect to the legitimate server.
Securing Server-Side Databases
Securing server-side databases requires a multi-layered approach. This includes employing strong passwords or other authentication mechanisms for database access, regularly updating database software and patching vulnerabilities, implementing access control mechanisms (e.g., role-based access control) to restrict access to sensitive data, and encrypting data both at rest (on the storage device) and in transit (when transferred over a network). Database encryption techniques, such as transparent data encryption (TDE), encrypt the entire database, offering robust protection against unauthorized access even if the storage device is compromised.
Regular database backups are also essential to ensure data recovery in case of unforeseen incidents. Furthermore, implementing intrusion detection and prevention systems helps monitor and respond to suspicious database activities.
End of Discussion
Securing servers effectively requires a multi-layered approach leveraging the power of cryptography. This exploration of Decoding Server Security with Cryptography has highlighted the crucial role of various encryption techniques, digital signatures, and secure communication protocols in achieving robust protection. By understanding the intricacies of symmetric and asymmetric encryption, implementing secure key management practices, and adopting best practices for cryptographic implementation, organizations can significantly reduce their vulnerability to cyber threats.
The ongoing evolution of cryptographic techniques necessitates a commitment to continuous learning and adaptation to stay ahead of emerging security challenges. This comprehensive understanding empowers individuals and organizations to build a more resilient and secure digital infrastructure.
FAQ Overview
What are some common vulnerabilities related to weak cryptography?
Weak or outdated encryption algorithms, improper key management, insecure implementation of cryptographic libraries, and lack of regular security updates are all common vulnerabilities.
How often should SSL/TLS certificates be renewed?
SSL/TLS certificates should be renewed before their expiration date, typically every 1-2 years, to maintain secure connections.
What is the difference between a digital signature and a digital certificate?
A digital signature verifies the authenticity and integrity of data, while a digital certificate verifies the identity of the entity (e.g., website) possessing the digital signature.
How can I choose the right cryptographic algorithm for my application?
The choice depends on the specific security requirements, performance considerations, and the sensitivity of the data being protected. Consult security best practices and consider factors like key size and algorithm strength.