Server Encryption: From Basics to Advanced. Data security is paramount in today’s digital landscape, and server-side encryption is a cornerstone of robust protection. This comprehensive guide delves into the intricacies of securing your server data, starting with fundamental concepts and progressing to advanced techniques. We’ll explore various encryption methods, key management strategies, implementation best practices, and future trends shaping this critical area of cybersecurity.
From understanding symmetric and asymmetric encryption to mastering key rotation and implementing encryption across different cloud platforms, we’ll equip you with the knowledge to safeguard your valuable information. We’ll also touch upon cutting-edge techniques like homomorphic encryption and quantum-resistant cryptography, providing a holistic view of the ever-evolving world of server-side data protection.
Introduction to Server Encryption
Server-side encryption is a crucial security measure protecting data stored on servers. It involves encrypting data before it’s written to storage, ensuring only authorized parties with the correct decryption keys can access it. This safeguards sensitive information from unauthorized access, even if the server itself is compromised. Understanding the fundamentals of server-side encryption is paramount for any organization handling sensitive data.Server encryption is the process of transforming readable data (plaintext) into an unreadable format (ciphertext) using cryptographic algorithms.
Understanding server encryption, from basic symmetric ciphers to the complexities of asymmetric key management, is crucial for robust data protection. To truly achieve bulletproof security, however, you need a holistic approach, as detailed in this excellent guide on Bulletproof Server Security with Cryptography. Mastering these advanced cryptographic techniques allows you to build a layered security model that effectively complements your server encryption strategy.
This prevents unauthorized access to the data even if the server is breached or the storage media is lost or stolen. The purpose is to maintain data confidentiality, integrity, and availability. Its effectiveness hinges on the strength of the encryption algorithm and the security of the encryption keys.
Types of Server Encryption
Server-side encryption primarily utilizes two types of encryption: symmetric and asymmetric. Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. Each approach has its strengths and weaknesses, making the choice dependent on the specific security requirements and context.
Comparison of Symmetric and Asymmetric Encryption
The following table compares symmetric and asymmetric encryption methods, highlighting key management considerations:
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Management | Requires secure key exchange; key distribution is a significant challenge. Vulnerable to key compromise if a single key is exposed. | More complex key management, but individual keys are less critical; compromise of one key doesn’t compromise the other. Public key distribution needs to be secured. |
| Speed | Generally faster than asymmetric encryption. | Significantly slower than symmetric encryption. |
| Algorithm Examples | AES (Advanced Encryption Standard), DES (Data Encryption Standard), 3DES (Triple DES) | RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography) |
| Use Cases | Ideal for encrypting large amounts of data where speed is crucial, such as database encryption. | Well-suited for secure key exchange, digital signatures, and encrypting smaller amounts of data where security is paramount, such as encrypting communication channels. |
Encryption Methods and Algorithms
Server-side encryption relies on robust cryptographic algorithms to protect sensitive data. Choosing the right algorithm depends on factors like security requirements, performance needs, and the type of data being protected. This section explores common encryption methods and their characteristics.
Symmetric and asymmetric encryption represent two fundamental approaches. Symmetric encryption uses the same key for both encryption and decryption, offering speed but posing key management challenges. Asymmetric encryption, conversely, utilizes separate keys for encryption (public key) and decryption (private key), simplifying key distribution but sacrificing speed.
AES Encryption
AES (Advanced Encryption Standard) is a widely used symmetric block cipher known for its speed and strong security. It operates on 128-bit, 192-bit, or 256-bit blocks of data, with the key size directly influencing the algorithm’s strength. Larger key sizes offer exponentially greater resistance to brute-force attacks. AES is a cornerstone of many security protocols, including HTTPS and TLS, protecting sensitive data in transit and at rest.
Its implementation in hardware accelerates encryption/decryption processes, making it suitable for high-throughput applications. Weaknesses in AES are largely theoretical and haven’t been practically exploited against well-implemented versions.
RSA Encryption
RSA (Rivest–Shamir–Adleman) is a widely used asymmetric algorithm based on the mathematical difficulty of factoring large numbers. It’s commonly employed for key exchange and digital signatures, not typically for encrypting large amounts of data directly due to its comparatively slower speed. RSA’s security relies on the size of the modulus (the product of two large prime numbers). Key sizes typically range from 1024 bits to 4096 bits, with larger keys offering enhanced security.
The strength of RSA is directly tied to the computational infeasibility of factoring the modulus; however, advancements in quantum computing pose a potential long-term threat. RSA is crucial in securing online transactions and ensuring the authenticity of digital documents.
Key Sizes and Their Impact on Security
The key size directly impacts an encryption algorithm’s security. Larger key sizes increase the computational effort required to break the encryption, making brute-force attacks exponentially more difficult. For example, a 128-bit AES key offers sufficient security for most applications, while 256-bit AES provides even greater protection against future advances in computing power. Similarly, RSA keys of 2048 bits or more are generally considered secure for most applications today, though longer keys (4096 bits) are recommended for situations demanding the highest level of security and long-term protection.
Real-World Applications of Encryption Algorithms
Different encryption algorithms find applications in various contexts:
- AES: Securing data at rest in databases (e.g., using database encryption features), protecting data in transit using HTTPS/TLS in web browsers, encrypting files on disk.
- RSA: Securing HTTPS/TLS connections (for key exchange), digital signatures for software verification and email authentication, encrypting small amounts of sensitive data like passwords.
Server Encryption Process Flowchart
The following describes a typical server-side encryption process:
Imagine a flowchart with the following steps:
- Data Input: The plaintext data to be encrypted is received by the server.
- Key Generation/Retrieval: A suitable encryption key (symmetric or asymmetric) is generated or retrieved from a secure key management system.
- Encryption: The selected encryption algorithm encrypts the plaintext data using the key, producing ciphertext.
- Ciphertext Storage: The encrypted ciphertext is stored on the server’s storage system.
- Key Management: The encryption key is securely stored and managed, often using hardware security modules (HSMs) or other secure key management systems.
- Decryption (upon request): When authorized, the server retrieves the key and decrypts the ciphertext using the corresponding algorithm, recovering the original plaintext data.
Key Management and Security Practices
Robust key management is paramount to the effectiveness of server encryption. Without secure key handling, even the strongest encryption algorithms are vulnerable. This section details best practices for generating, storing, and managing encryption keys, identifies potential vulnerabilities, explains key rotation, and compares different key management systems.
Key Generation and Storage Best Practices
Secure key generation involves employing cryptographically secure pseudorandom number generators (CSPRNGs) to create keys of sufficient length. The length should align with the algorithm’s requirements and the desired security level. Keys should be stored in a hardware security module (HSM) whenever possible. HSMs provide a physically secure environment, protecting keys from unauthorized access even if the server itself is compromised.
If an HSM isn’t feasible, strong encryption should be used to protect keys at rest, using robust algorithms like AES-256 with a strong, independently managed key. Access to these keys should be strictly controlled and logged, adhering to the principle of least privilege.
Key Management Vulnerabilities, Server Encryption: From Basics to Advanced
Several vulnerabilities can compromise key management. Compromised key storage, whether through physical theft of HSMs or exploitation of software vulnerabilities, is a major risk. Weak key generation practices, such as using predictable or easily guessable keys, significantly weaken the security of the entire system. Insider threats, where authorized personnel misuse or steal keys, pose a significant internal risk.
Furthermore, insufficient key rotation increases the risk of long-term exposure if a key is compromised. Finally, lack of proper auditing and logging of key access makes it difficult to detect and respond to potential breaches.
Key Rotation and Its Importance
Key rotation is the process of periodically replacing encryption keys with new ones. This limits the impact of a potential key compromise; if a key is compromised, the attacker’s access is limited to the data encrypted with that specific key. The frequency of key rotation depends on the sensitivity of the data and the potential risks. For highly sensitive data, frequent rotation (e.g., daily or weekly) might be necessary.
The process should be automated to minimize the risk of human error and ensure consistency. Proper key rotation procedures include secure key generation, distribution, and decommissioning of old keys. It’s crucial to have a well-defined policy that Artikels the rotation schedule and procedures.
Comparison of Key Management Systems
Several key management systems exist, each with its own strengths and weaknesses. These systems range from simple, self-managed solutions suitable for smaller organizations to complex, enterprise-grade systems. Centralized Key Management Systems (KMS) offer a single point of control and management for all encryption keys, providing better auditability and control. Distributed Key Management Systems offer higher resilience to single points of failure but can be more complex to manage.
Hardware Security Modules (HSMs) provide a highly secure environment for key storage and management, but they can be more expensive. Cloud-based KMS solutions offer scalability and convenience, but require careful consideration of data sovereignty and security implications. The choice of system depends on factors such as the organization’s size, security requirements, budget, and technical expertise.
Implementing Server Encryption: Server Encryption: From Basics To Advanced
Implementing server-side encryption involves integrating encryption algorithms into your server’s infrastructure to protect sensitive data at rest. This process requires careful planning and execution, considering various security factors and the specific needs of your application. Successful implementation enhances data security and compliance with regulations like GDPR and HIPAA.
Database Server-Side Encryption Implementation
Implementing server-side encryption for a database involves several key steps. First, you must choose an appropriate encryption algorithm and key management strategy. Next, you’ll configure the database system to utilize this encryption, typically through built-in features or extensions. Finally, you should regularly test and monitor the encryption process to ensure its ongoing effectiveness.
- Select Encryption Algorithm and Key Management: Choose a robust algorithm like AES-256 with a secure key management system. Consider factors like performance impact and compliance requirements.
- Configure Database System: Most modern database systems offer built-in encryption capabilities. This typically involves configuring encryption settings within the database management system (DBMS) interface, often specifying the encryption algorithm and key location.
- Encrypt Existing Data: Existing data will need to be encrypted. This process can be done offline or online, depending on the DBMS and the amount of data. Offline encryption involves exporting, encrypting, and re-importing the data. Online encryption is typically more complex but allows for continuous database availability.
- Test and Monitor: Regular testing and monitoring are critical. Verify that encryption is functioning correctly and that key management procedures are secure.
Encryption and Decryption Pseudocode Examples
The following pseudocode examples illustrate the basic encryption and decryption processes using a symmetric encryption algorithm. Remember that this is simplified and actual implementations will require more robust error handling and security considerations.
Encryption
function encryptData(data, key)
// Obtain encryption cipher using the chosen algorithm (e.g., AES) and key.
cipher = getCipher(algorithm, key);
// Encrypt the data using the cipher.
encryptedData = cipher.encrypt(data);
return encryptedData;
Decryption
function decryptData(encryptedData, key)
// Obtain decryption cipher using the chosen algorithm (e.g., AES) and key.
cipher = getCipher(algorithm, key);
// Decrypt the data using the cipher.
decryptedData = cipher.decrypt(encryptedData);
return decryptedData;
Security Considerations Checklist
Before implementing server-side encryption, a thorough security assessment is essential. This checklist highlights crucial areas to consider:
- Key Management: Implement a robust key management system using hardware security modules (HSMs) where appropriate. Keys should be securely stored, rotated regularly, and access strictly controlled.
- Algorithm Selection: Choose a strong, well-vetted encryption algorithm with sufficient key length (e.g., AES-256).
- Data at Rest and in Transit: Ensure both data at rest (on the server) and data in transit (between client and server) are encrypted.
- Access Control: Implement strict access controls to limit who can access encryption keys and encrypted data.
- Regular Audits and Monitoring: Regularly audit security logs and monitor the encryption system for any anomalies or potential vulnerabilities.
- Compliance: Ensure compliance with relevant industry regulations and standards (e.g., GDPR, HIPAA).
Server-Side Encryption Configuration Across Cloud Platforms
Different cloud providers offer various methods for implementing server-side encryption. The following table compares the options available on AWS, Azure, and GCP.
| Feature | AWS | Azure | GCP |
|---|---|---|---|
| Database Encryption | AWS Database Encryption with AWS KMS | Azure Key Vault with Always Encrypted | Cloud SQL Encryption with Cloud KMS |
| Storage Encryption | Amazon S3 Server-Side Encryption (SSE) | Azure Blob Storage Server-Side Encryption | Google Cloud Storage Server-Side Encryption |
| Key Management | AWS KMS | Azure Key Vault | Cloud KMS |
| Integration with other services | Seamless integration with other AWS services | Tight integration within the Azure ecosystem | Strong integration with other GCP services |
Advanced Encryption Techniques
Beyond the fundamental encryption methods, several advanced techniques offer enhanced security and functionality for server data protection. These techniques address specific challenges and cater to diverse data types, ensuring robust protection against evolving threats. This section delves into some of the most prominent advanced encryption methods and their practical applications.
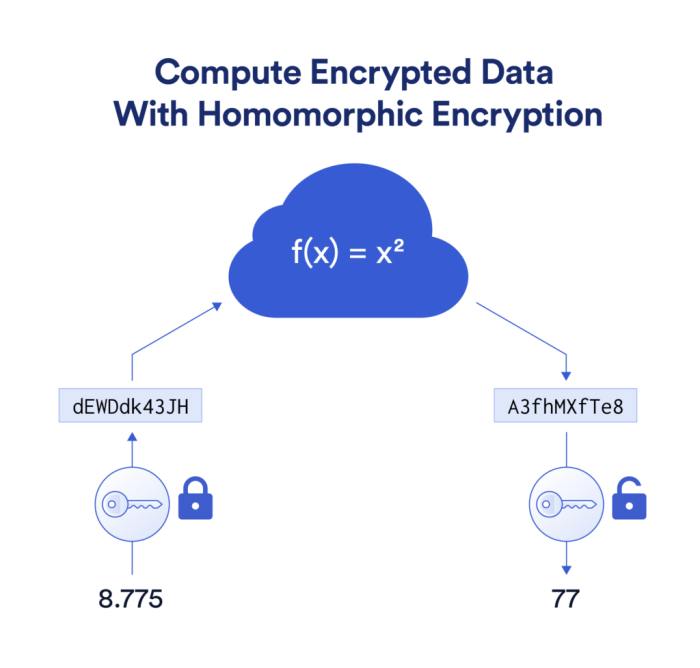
Homomorphic Encryption and its Applications
Homomorphic encryption allows computations to be performed on encrypted data without decryption. This groundbreaking approach enables processing sensitive information while maintaining its confidentiality. Imagine a scenario where a financial institution needs to analyze aggregated data from multiple encrypted customer records without compromising individual privacy. Homomorphic encryption facilitates this by allowing computations on the encrypted data, yielding an encrypted result that can be decrypted only by the authorized party.
Several types of homomorphic encryption exist, including partially homomorphic, somewhat homomorphic, and fully homomorphic encryption, each offering varying levels of computational capabilities. The practical applications extend beyond financial services, encompassing cloud computing, secure multi-party computation, and privacy-preserving machine learning.
Digital Signatures in Securing Server Data
Digital signatures provide authentication and integrity verification for server data. Unlike symmetric or asymmetric encryption, which primarily focuses on confidentiality, digital signatures ensure data authenticity and prevent tampering. A digital signature uses a private key to create a unique “signature” for a data set. This signature can then be verified using the corresponding public key, confirming the data’s origin and integrity.
This is crucial for preventing unauthorized modifications or fraudulent claims. For instance, a server hosting critical software updates could use digital signatures to guarantee the authenticity of the updates, preventing malicious actors from distributing altered versions. The widespread adoption of digital signatures is largely due to their effectiveness in ensuring data integrity within various security protocols and systems.
Advanced Encryption Techniques for Specific Data Types
Different data types require tailored encryption approaches due to their unique characteristics and security sensitivities. Multimedia data, such as images and videos, often benefit from techniques like AES (Advanced Encryption Standard) in combination with lossless compression algorithms to balance security and storage efficiency. For sensitive personal information (SPI), such as medical records or financial transactions, more robust methods like homomorphic encryption or multi-party computation might be necessary to ensure privacy while enabling data analysis.
The selection of the optimal technique hinges on several factors, including data sensitivity, computational resources, and regulatory compliance requirements. A careful assessment of these factors is crucial in selecting the most appropriate encryption method.
Summary of Advanced Encryption Techniques and Use Cases
| Technique | Description | Use Cases |
|---|---|---|
| Homomorphic Encryption | Allows computations on encrypted data without decryption. | Cloud computing, secure multi-party computation, privacy-preserving machine learning, financial data analysis. |
| Digital Signatures | Provides authentication and integrity verification. | Software updates, secure document exchange, transaction verification. |
| AES (Advanced Encryption Standard) | A symmetric block cipher widely used for data encryption. | Data at rest, data in transit, multimedia encryption. |
| Elliptic Curve Cryptography (ECC) | Asymmetric cryptography offering strong security with smaller key sizes. | Secure communication, digital signatures, key exchange. |
| Multi-Party Computation (MPC) | Allows multiple parties to jointly compute a function over their private inputs without revealing anything beyond the output. | Privacy-preserving data analysis, secure voting systems. |
Security Considerations and Best Practices
Server-side encryption, while offering robust data protection, is not foolproof. A comprehensive security strategy requires understanding potential vulnerabilities and implementing proactive mitigation techniques. This section details common threats, effective countermeasures, and best practices for maintaining a secure encrypted environment.
Common Vulnerabilities and Attack Vectors
Successful server encryption relies on the strength of its implementation and the security of its supporting infrastructure. Weaknesses in any component can compromise the overall security. Neglecting security best practices can expose sensitive data to various attack vectors. These vulnerabilities can range from simple misconfigurations to sophisticated exploits targeting cryptographic weaknesses.
Mitigation Strategies for Server Encryption Vulnerabilities
Addressing vulnerabilities requires a multi-layered approach combining technical solutions and robust security policies. This includes regularly updating encryption libraries and operating systems, employing strong key management practices, and implementing access control mechanisms to restrict unauthorized access to encrypted data and cryptographic keys. Regular security audits and penetration testing are also crucial for identifying and rectifying vulnerabilities before they can be exploited.
Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying vulnerabilities in server encryption implementations. Audits involve systematic reviews of security controls, configurations, and processes to ensure compliance with security policies and best practices. Penetration testing simulates real-world attacks to uncover weaknesses in the system’s defenses. These processes should be conducted by experienced security professionals, ideally using a combination of automated tools and manual analysis.
A well-defined schedule for these activities, coupled with thorough documentation of findings and remediation efforts, is crucial. For instance, a financial institution might schedule a penetration test every six months, while a smaller company might opt for an annual assessment.
Comprehensive Security Policy for Server-Side Encryption
A comprehensive security policy should Artikel all aspects of server-side encryption, from key management to incident response. This policy should clearly define roles and responsibilities, data classification schemes, encryption algorithms and key lengths, and procedures for key rotation and revocation. The policy should also detail incident response plans, including procedures for identifying, containing, and remediating security breaches. Regular review and updates of the policy are crucial to adapt to evolving threats and technological advancements.
A well-defined policy helps maintain a consistent and secure approach to server-side encryption, reducing the risk of vulnerabilities and data breaches. Consideration should be given to regulatory compliance, such as GDPR or HIPAA, depending on the nature of the data being protected. For example, a policy might mandate the use of AES-256 encryption with a key rotation schedule of every 90 days and a detailed incident response plan outlining communication protocols and escalation procedures.
Future Trends in Server Encryption
The landscape of server encryption is constantly evolving, driven by advancements in cryptography, the increasing volume and sensitivity of data, and the tightening regulatory environment. Understanding these emerging trends is crucial for organizations seeking to maintain robust data security in the years to come. This section explores key future directions in server encryption, highlighting both the opportunities and challenges they present.
Emerging technologies are significantly influencing the future of server encryption. The most impactful of these is the development of quantum-resistant cryptography. As quantum computing technology matures, existing encryption algorithms, including widely used RSA and ECC, will become vulnerable to attacks. This necessitates the development and implementation of algorithms that can withstand attacks from both classical and quantum computers.
The transition to these new algorithms represents a major undertaking, requiring careful planning and substantial investment.
Quantum-Resistant Cryptography
The development and standardization of quantum-resistant cryptographic algorithms is paramount. National Institute of Standards and Technology (NIST) has been leading the effort to identify and standardize suitable algorithms. The selected algorithms, including CRYSTALS-Kyber, CRYSTALS-Dilithium, FALCON, SPHINCS+, and others, offer different security properties and performance characteristics. Implementing these algorithms will require significant changes to existing infrastructure and applications, necessitating a phased approach to minimize disruption and ensure compatibility.
The transition will also involve updating hardware and software to support the new algorithms’ computational requirements. For instance, migrating a large-scale enterprise system might require significant testing and validation to ensure seamless integration and continued operational efficiency.
Challenges and Opportunities in Server Encryption
The future of server encryption presents both challenges and opportunities. One major challenge is the complexity of managing encryption keys across distributed systems, especially in cloud environments. This complexity increases with the adoption of more sophisticated encryption techniques, such as homomorphic encryption, which allows computations to be performed on encrypted data without decryption. Opportunities arise from the development of more efficient and flexible encryption solutions, including advancements in hardware-based encryption and the integration of encryption into the underlying infrastructure of data centers and cloud platforms.
This could lead to improved performance and reduced overhead, making strong encryption more accessible and practical for a wider range of applications. For example, the development of specialized hardware accelerators for quantum-resistant algorithms could significantly improve their performance, making them more viable for deployment in high-throughput systems.
Impact of Evolving Data Privacy Regulations
Evolving data privacy regulations, such as GDPR and CCPA, are significantly impacting server encryption practices. These regulations mandate strong encryption for sensitive data, both in transit and at rest. Compliance requires organizations to implement robust encryption strategies and maintain detailed records of their encryption practices. Failure to comply can result in significant financial penalties and reputational damage. The increasing complexity of these regulations necessitates a proactive approach to compliance, including regular audits and assessments to ensure ongoing adherence to evolving requirements.
For instance, organizations need to adapt their encryption strategies to accommodate changes in regulatory requirements, such as new data categories requiring encryption or stricter key management practices.
A Hypothetical Future Scenario
In 2035, server encryption is seamlessly integrated into all aspects of data management. Quantum-resistant algorithms are the standard, and automated key management systems ensure efficient and secure key rotation. Homomorphic encryption is widely adopted, allowing for secure data analysis and processing without decryption, greatly enhancing privacy and security in collaborative research and data analytics projects. The implementation of advanced threat detection systems leverages machine learning to identify and mitigate potential vulnerabilities in real-time, continuously adapting to evolving threats.
This sophisticated, automated system ensures that data remains secure even in the face of increasingly sophisticated attacks, both classical and quantum. This integrated approach reduces the administrative burden on organizations, allowing them to focus on their core business activities while maintaining the highest level of data security.
Conclusion
Securing your server data is an ongoing process, requiring vigilance and adaptation to evolving threats. By understanding the fundamentals of server encryption and staying abreast of advanced techniques, you can significantly reduce your risk profile. This guide has provided a solid foundation, empowering you to build a robust and resilient security posture. Remember, proactive security measures are not just best practices; they are essential for maintaining data integrity and protecting your organization’s valuable assets in the face of increasingly sophisticated cyberattacks.
FAQ Explained
What are the potential legal ramifications of failing to adequately encrypt server data?
Failure to comply with data privacy regulations like GDPR or CCPA can result in hefty fines, legal action, and reputational damage. The specific penalties vary depending on the jurisdiction and the severity of the breach.
How often should encryption keys be rotated?
Key rotation frequency depends on several factors, including the sensitivity of the data and the threat landscape. Best practices suggest regular rotations, at least annually, or even more frequently for highly sensitive data.
Can server encryption protect against all types of attacks?
While server encryption significantly reduces the risk of data breaches, it’s not a foolproof solution. Other security measures, such as access controls, intrusion detection systems, and regular security audits, are crucial for comprehensive protection.
What is the role of hardware security modules (HSMs) in key management?
HSMs provide a secure hardware environment for generating, storing, and managing cryptographic keys. They offer enhanced protection against physical and software-based attacks, strengthening overall key management security.