Unlock Server Security with Cryptography: In today’s hyper-connected world, server security is paramount. Cyber threats are constantly evolving, demanding robust defenses. Cryptography, the art of secure communication, provides the essential tools to protect your valuable data and systems from unauthorized access and manipulation. This guide delves into the crucial role of cryptography in bolstering server security, exploring various techniques, protocols, and best practices to ensure a fortified digital infrastructure.
We’ll explore different encryption methods, from symmetric and asymmetric algorithms to the intricacies of secure protocols like TLS/SSL and SSH. Learn how to implement strong authentication mechanisms, manage cryptographic keys effectively, and understand the principles of data integrity using hashing algorithms. We’ll also touch upon advanced techniques and future trends in cryptography, equipping you with the knowledge to safeguard your servers against the ever-present threat of cyberattacks.
Introduction to Server Security and Cryptography
In today’s interconnected world, servers are the backbone of countless online services, from e-commerce platforms to critical infrastructure. The security of these servers is paramount, as a breach can lead to significant financial losses, reputational damage, and even legal repercussions. Protecting server data and ensuring the integrity of online services requires a robust security strategy, with cryptography playing a central role.Cryptography, the practice and study of techniques for secure communication in the presence of adversarial behavior, provides the essential tools to safeguard server data and communications.
It employs mathematical techniques to transform data into an unreadable format, protecting it from unauthorized access and manipulation. The effective implementation of cryptographic algorithms is crucial for mitigating a wide range of server security threats.
Common Server Security Threats
Servers face numerous threats, including unauthorized access, data breaches, denial-of-service attacks, and malware infections. Unauthorized access can occur through weak passwords, unpatched vulnerabilities, or exploited security flaws. Data breaches can result in the exposure of sensitive customer information, financial data, or intellectual property. Denial-of-service attacks overwhelm servers with traffic, rendering them inaccessible to legitimate users. Malware infections can compromise server functionality, steal data, or use the server to launch further attacks.
These threats highlight the critical need for robust security measures, including the strategic application of cryptography.
Cryptographic Algorithms
Various cryptographic algorithms are employed to enhance server security, each with its strengths and weaknesses. The choice of algorithm depends on the specific security requirements of the application. The following table compares three main types: symmetric, asymmetric, and hashing algorithms.
| Algorithm | Type | Use Case | Strengths/Weaknesses |
|---|---|---|---|
| AES (Advanced Encryption Standard) | Symmetric | Data encryption at rest and in transit | Strong encryption; relatively fast; vulnerable to key distribution challenges. |
| RSA (Rivest-Shamir-Adleman) | Asymmetric | Digital signatures, key exchange, encryption of smaller data sets | Provides strong authentication and confidentiality; computationally slower than symmetric algorithms. |
| SHA-256 (Secure Hash Algorithm 256-bit) | Hashing | Password storage, data integrity verification | Provides strong collision resistance; one-way function; does not provide confidentiality. |
Encryption Techniques for Server Security: Unlock Server Security With Cryptography
Server security relies heavily on robust encryption techniques to protect sensitive data both while it’s stored (data at rest) and while it’s being transmitted (data in transit). Choosing the right encryption method depends on the specific security needs and performance requirements of the system. This section explores various encryption techniques commonly used to safeguard server data.
Symmetric Encryption for Data at Rest and in Transit
Symmetric encryption utilizes a single, secret key to both encrypt and decrypt data. This approach is generally faster than asymmetric encryption, making it suitable for encrypting large volumes of data at rest, such as databases or backups. For data in transit, protocols like TLS/SSL leverage symmetric encryption to secure communication between a client and server after an initial key exchange using asymmetric cryptography.
Popular symmetric algorithms include AES (Advanced Encryption Standard) and ChaCha20, offering varying levels of security and performance based on key size and implementation. AES, for example, is widely adopted and considered highly secure with its 128-bit, 192-bit, and 256-bit key sizes. ChaCha20, on the other hand, is known for its performance advantages on certain hardware platforms. The choice between these, or others, depends on specific performance and security needs.
Implementing symmetric encryption often involves using libraries or APIs provided by programming languages or operating systems.
Asymmetric Encryption for Authentication and Key Exchange
Asymmetric encryption employs a pair of keys: a public key, which can be freely distributed, and a private key, which must be kept secret. The public key is used to encrypt data, while only the corresponding private key can decrypt it. This characteristic is crucial for authentication. For example, a server can use its private key to digitally sign a message, and a client can verify the signature using the server’s public key, ensuring the message originates from the authentic server and hasn’t been tampered with.
Asymmetric encryption is also vital for key exchange in secure communication protocols. In TLS/SSL, for instance, the initial handshake involves the exchange of public keys to establish a shared secret key, which is then used for faster symmetric encryption of the subsequent communication. RSA and ECC are prominent examples of asymmetric encryption algorithms.
Comparison of RSA and ECC Algorithms
RSA and Elliptic Curve Cryptography (ECC) are both widely used asymmetric encryption algorithms, but they differ significantly in their underlying mathematical principles and performance characteristics. RSA relies on the difficulty of factoring large numbers, while ECC relies on the difficulty of solving the elliptic curve discrete logarithm problem. For equivalent security levels, ECC typically requires smaller key sizes than RSA, leading to faster encryption and decryption speeds and reduced computational overhead.
This makes ECC particularly attractive for resource-constrained devices and applications where performance is critical. However, RSA remains a widely deployed algorithm and benefits from extensive research and analysis, making it a mature and trusted option. The choice between RSA and ECC often involves a trade-off between security, performance, and implementation complexity.
Public Key Infrastructure (PKI) Scenario: Secure Client-Server Communication
Imagine an e-commerce website using PKI to secure communication between its server and client browsers. The website obtains a digital certificate from a trusted Certificate Authority (CA), which contains the website’s public key and other identifying information. The CA digitally signs this certificate, guaranteeing its authenticity. When a client attempts to connect to the website, the server presents its certificate.
The client’s browser verifies the certificate’s signature against the CA’s public key, ensuring the certificate is legitimate and hasn’t been tampered with. Once the certificate is validated, the client and server can use the website’s public key to securely exchange a symmetric session key, enabling fast and secure communication for the duration of the session. This process prevents eavesdropping and ensures the authenticity of the website.
This scenario showcases how PKI provides a framework for trust and secure communication in online environments.
Secure Protocols and Implementations
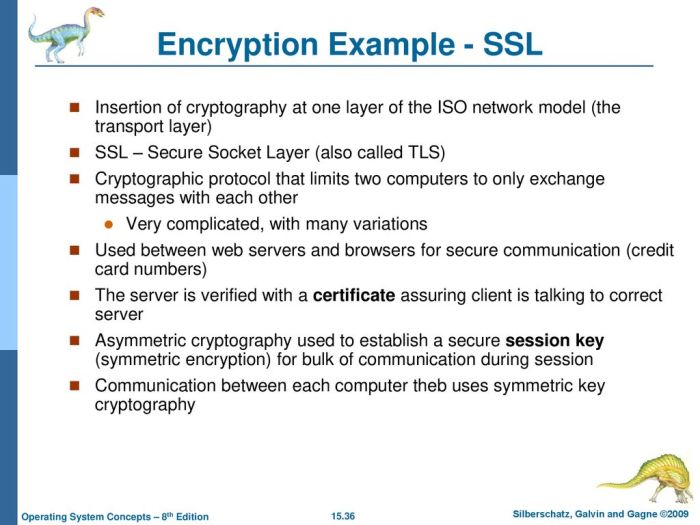
Secure protocols are crucial for establishing and maintaining secure communication channels between servers and clients. They leverage cryptographic algorithms to ensure confidentiality, integrity, and authentication, protecting sensitive data from unauthorized access and manipulation. This section examines two prominent secure protocols – TLS/SSL and SSH – detailing their underlying cryptographic mechanisms and practical implementation on web servers.
TLS/SSL and its Cryptographic Algorithms
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are widely used protocols for securing network connections, particularly in web browsing (HTTPS). They employ a layered approach to security, combining symmetric and asymmetric cryptography. The handshake process, detailed below, establishes a secure session. Key cryptographic algorithms commonly used within TLS/SSL include:
- Symmetric Encryption Algorithms: AES (Advanced Encryption Standard) is the most prevalent, offering strong confidentiality through its various key sizes (128, 192, and 256 bits). Other algorithms, though less common now, include 3DES (Triple DES) and ChaCha20.
- Asymmetric Encryption Algorithms: RSA (Rivest–Shamir–Adleman) and ECC (Elliptic Curve Cryptography) are used for key exchange and digital signatures. ECC is becoming increasingly popular due to its superior performance with comparable security levels to RSA for smaller key sizes.
- Hashing Algorithms: SHA-256 (Secure Hash Algorithm 256-bit) and SHA-384 are frequently used to ensure data integrity and generate message authentication codes (MACs).
TLS/SSL Handshake Process
The TLS/SSL handshake is a crucial phase establishing a secure connection. It involves a series of messages exchanged between the client and the server to negotiate security parameters and establish a shared secret key. The steps are broadly as follows:
- Client Hello: The client initiates the handshake by sending a message containing supported protocols, cipher suites (combinations of encryption, authentication, and hashing algorithms), and a random number (client random).
- Server Hello: The server responds with its chosen cipher suite (from those offered by the client), its own random number (server random), and its certificate.
- Certificate Verification: The client verifies the server’s certificate against a trusted Certificate Authority (CA). If the certificate is valid, the client proceeds; otherwise, the connection is terminated.
- Key Exchange: The client and server use the chosen cipher suite’s key exchange algorithm (e.g., RSA, Diffie-Hellman, or ECDHE) to generate a pre-master secret. This secret is then used to derive the session keys for symmetric encryption.
- Change Cipher Spec: Both client and server send a message indicating a switch to the negotiated encryption and authentication algorithms.
- Finished: Both sides send a “finished” message, encrypted using the newly established session keys, proving that the key exchange was successful and the connection is secure.
Configuring Secure Protocols on Apache
To enable HTTPS on an Apache web server, you’ll need an SSL/TLS certificate. Once obtained, configure Apache’s virtual host configuration file (typically located in `/etc/apache2/sites-available/` or a similar directory). Here’s a snippet demonstrating basic HTTPS configuration:
<VirtualHost
-:443>
ServerName example.com
ServerAdmin webmaster@example.com
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /etc/ssl/certs/example.com.crt
SSLCertificateKeyFile /etc/ssl/private/example.com.key
SSLCipherSuite HIGH:MEDIUM:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aTLSv1:!aTLSv1.1
</VirtualHost>
Remember to replace placeholders like `example.com`, certificate file paths, and cipher suite with your actual values. The `SSLCipherSuite` directive specifies the acceptable cipher suites, prioritizing strong and secure options.
Configuring Secure Protocols on Nginx
Nginx’s HTTPS configuration is similarly straightforward. The server block configuration file needs to be modified to include SSL/TLS settings. Below is a sample configuration snippet:
server
listen 443 ssl;
server_name example.com;
root /var/www/html;
ssl_certificate /etc/ssl/certs/example.com.crt;
ssl_certificate_key /etc/ssl/private/example.com.key;
ssl_protocols TLSv1.2 TLSv1.3; #Restrict to strong protocols
ssl_ciphers TLS13-AES-256-GCM-SHA384:TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-128-GCM-SHA256:TLS13-AES-128-CCM-8-SHA256:TLS13-AES-128-CCM-SHA256;
ssl_prefer_server_ciphers off;
Similar to Apache, remember to replace placeholders with your actual values.
The `ssl_protocols` and `ssl_ciphers` directives are crucial for selecting strong and up-to-date cryptographic algorithms. Always consult the latest security best practices and Nginx documentation for the most secure configurations.
Access Control and Authentication Mechanisms
Securing a server involves not only encrypting data but also controlling who can access it and what actions they can perform. Access control and authentication mechanisms are crucial components of a robust server security strategy, working together to verify user identity and restrict access based on predefined rules. These mechanisms are vital for preventing unauthorized access and maintaining data integrity.
Authentication methods verify the identity of a user or entity attempting to access the server. Authorization mechanisms, on the other hand, define what resources and actions a verified user is permitted to perform. The combination of robust authentication and finely-tuned authorization forms the bedrock of secure server operation.
Password-Based Authentication
Password-based authentication is the most common method, relying on users providing a username and password. The server then compares the provided credentials against a stored database of legitimate users. While simple to implement, this method is vulnerable to various attacks, including brute-force attacks and phishing. Strong password policies, regular password changes, and the use of password salting and hashing techniques are crucial to mitigate these risks.
Salting adds random data to the password before hashing, making it more resistant to rainbow table attacks. Hashing converts the password into a one-way function, making it computationally infeasible to reverse engineer the original password.
Multi-Factor Authentication (MFA)
Multi-factor authentication enhances security by requiring users to provide multiple forms of authentication. Common factors include something the user knows (password), something the user has (security token or smartphone), and something the user is (biometric data). MFA significantly reduces the risk of unauthorized access, even if one factor is compromised. For example, even if a password is stolen, an attacker would still need access to the user’s physical security token or biometric data to gain access.
This layered approach makes MFA a highly effective security measure.
Biometric Authentication
Biometric authentication uses unique biological characteristics to verify user identity. Examples include fingerprint scanning, facial recognition, and iris scanning. Biometric authentication is generally considered more secure than password-based methods because it’s difficult to replicate biological traits. However, biometric systems can be vulnerable to spoofing attacks, and data privacy concerns need careful consideration. For instance, a high-resolution photograph might be used to spoof facial recognition systems.
Digital Signatures and Server Software/Data Authenticity
Digital signatures employ cryptography to verify the authenticity and integrity of server software and data. A digital signature is created using a private key and can be verified using the corresponding public key. This ensures that the software or data has not been tampered with and originates from a trusted source. The integrity of the digital signature itself is crucial, and reliance on a trusted Certificate Authority (CA) for public key distribution is paramount.
If a malicious actor were to compromise the CA, the validity of digital signatures would be severely compromised.
Authorization Mechanisms
Authorization mechanisms define what actions authenticated users are permitted to perform. These mechanisms are implemented to enforce the principle of least privilege, granting users only the necessary access to perform their tasks.
Role-Based Access Control (RBAC)
Role-based access control assigns users to roles, each with predefined permissions. This simplifies access management, especially in large organizations with many users and resources. For instance, a “database administrator” role might have full access to a database, while a “data analyst” role would have read-only access. This method is efficient for managing access across a large number of users and resources.
Attribute-Based Access Control (ABAC)
Attribute-based access control grants access based on attributes of the user, the resource, and the environment. This provides fine-grained control and adaptability to changing security requirements. For example, access to a sensitive document might be granted only to employees located within a specific geographic region during business hours. ABAC offers greater flexibility than RBAC but can be more complex to implement.
Comparison of Access Control Methods
The choice of access control method depends on the specific security requirements and the complexity of the system. A comparison of strengths and weaknesses is provided below:
- Password-Based Authentication:
- Strengths: Simple to implement and understand.
- Weaknesses: Vulnerable to various attacks, including brute-force and phishing.
- Multi-Factor Authentication:
- Strengths: Significantly enhances security by requiring multiple factors.
- Weaknesses: Can be more inconvenient for users.
- Biometric Authentication:
- Strengths: Difficult to replicate biological traits.
- Weaknesses: Vulnerable to spoofing attacks, privacy concerns.
- Role-Based Access Control (RBAC):
- Strengths: Simplifies access management, efficient for large organizations.
- Weaknesses: Can be inflexible for complex scenarios.
- Attribute-Based Access Control (ABAC):
- Strengths: Provides fine-grained control and adaptability.
- Weaknesses: More complex to implement and manage.
Data Integrity and Hashing Algorithms
Data integrity, in the context of server security, refers to the assurance that data remains unaltered and trustworthy throughout its lifecycle. Maintaining data integrity is crucial because compromised data can lead to incorrect decisions, security breaches, and significant financial losses. Hashing algorithms play a vital role in achieving this by providing a mechanism to detect any unauthorized modifications.
Data integrity is paramount for ensuring the reliability and trustworthiness of information stored and processed on servers. Without it, attackers could manipulate data, leading to inaccurate reporting, flawed analyses, and compromised operational decisions. The consequences of data breaches stemming from compromised integrity can be severe, ranging from reputational damage to legal repercussions and financial penalties. Therefore, robust mechanisms for verifying data integrity are essential for maintaining a secure server environment.
Hashing Algorithms: MD5, SHA-256, and SHA-3
Hashing algorithms are cryptographic functions that take an input (data of any size) and produce a fixed-size string of characters, known as a hash or message digest. This hash acts as a fingerprint of the data. Even a tiny change in the input data results in a drastically different hash value. This property is fundamental to verifying data integrity.
Three prominent hashing algorithms are MD5, SHA-256, and SHA-3.
MD5
MD5 (Message Digest Algorithm 5) is a widely known but now considered cryptographically broken hashing algorithm. While it was once popular due to its speed, significant vulnerabilities have been discovered, making it unsuitable for security-sensitive applications requiring strong collision resistance. Collisions (where different inputs produce the same hash) are easily found, rendering MD5 ineffective for verifying data integrity in situations where malicious actors might attempt to forge data.
SHA-256, Unlock Server Security with Cryptography
SHA-256 (Secure Hash Algorithm 256-bit) is a member of the SHA-2 family of algorithms. It produces a 256-bit hash value and is significantly more secure than MD5. SHA-256 is widely used in various security applications, including digital signatures and password hashing (often with salting and key derivation functions). Its resistance to collisions is considerably higher than MD5, making it a more reliable choice for ensuring data integrity.
SHA-3
SHA-3 (Secure Hash Algorithm 3) is a more recent hashing algorithm designed to be distinct from the SHA-2 family. It offers a different cryptographic approach and is considered to be a strong alternative to SHA-2. SHA-3 boasts improved security properties and is designed to resist attacks that might be effective against SHA-2 in the future. While SHA-256 remains widely used, SHA-3 offers a robust and future-proof option for ensuring data integrity.
Comparison of Hashing Algorithms
The following table summarizes the key differences and security properties of MD5, SHA-256, and SHA-3:
| Algorithm | Hash Size | Security Status | Collision Resistance |
|---|---|---|---|
| MD5 | 128 bits | Cryptographically broken | Weak |
| SHA-256 | 256 bits | Secure (currently) | Strong |
| SHA-3 | Variable (224-512 bits) | Secure | Strong |
Illustrating Data Integrity with Hashing
Imagine a file containing sensitive data. Before storing the file, a hashing algorithm (e.g., SHA-256) is applied to it, generating a unique hash value. This hash is then stored separately.
Later, when retrieving the file, the same hashing algorithm is applied again. If the newly generated hash matches the stored hash, it confirms that the file has not been tampered with. If the hashes differ, it indicates that the file has been altered.
“`
Original File: “This is my secret data.”
SHA-256 Hash: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
Modified File: “This is my SECRET data.”
SHA-256 Hash: 292148573a2e8632285945912c02342c50c5a663187448162048b1c2e0951325
Hashes do not match; data integrity compromised.
“`
Key Management and Security Best Practices
Secure key management is paramount to the effectiveness of any cryptographic system protecting server security. Without robust key management practices, even the strongest encryption algorithms are vulnerable to compromise, rendering the entire security infrastructure ineffective. This section details the critical aspects of secure key management and Artikels best practices to mitigate risks.
Risks Associated with Poor Key Management
Neglecting key management practices exposes servers to a multitude of threats. Compromised keys can lead to unauthorized access, data breaches, and significant financial losses. Specifically, weak key generation methods, insecure storage, and inadequate distribution protocols increase the likelihood of successful attacks. For example, a poorly generated key might be easily guessed through brute-force attacks, while insecure storage allows attackers to steal keys directly, leading to complete system compromise.
The lack of proper key rotation increases the impact of a successful attack, potentially leaving the system vulnerable for extended periods.
Best Practices for Key Generation, Storage, and Distribution
Generating strong cryptographic keys requires adherence to specific guidelines. Keys should be generated using cryptographically secure random number generators (CSPRNGs) to prevent predictability. The key length must be appropriate for the chosen algorithm and the level of security required; longer keys generally offer greater resistance to brute-force attacks. For example, AES-256 requires a 256-bit key, providing significantly stronger security than AES-128 with its 128-bit key.
Secure key storage involves protecting keys from unauthorized access. Hardware security modules (HSMs) provide a highly secure environment for key storage and management. HSMs are tamper-resistant devices that isolate keys from the main system, minimizing the risk of compromise. Alternatively, keys can be stored in encrypted files on secure servers, employing strong encryption algorithms and access control mechanisms.
Regular backups of keys are crucial for disaster recovery, but these backups must also be securely stored and protected.
Key distribution requires secure channels to prevent interception. Key exchange protocols, such as Diffie-Hellman, allow two parties to establish a shared secret key over an insecure channel. Secure communication protocols like TLS/SSL ensure secure transmission of keys during distribution. Employing secure methods for key distribution is essential to prevent man-in-the-middle attacks.
Examples of Key Management Systems
Several key management systems (KMS) are available, offering varying levels of functionality and security. Cloud-based KMS solutions, such as those provided by AWS, Azure, and Google Cloud, offer centralized key management, access control, and auditing capabilities. These systems often integrate with other security services, simplifying key management for large-scale deployments. Open-source KMS solutions provide more flexibility and customization but require more technical expertise to manage effectively.
A well-known example is HashiCorp Vault, a popular choice for managing secrets and keys in a distributed environment. The selection of a KMS should align with the specific security requirements and the organization’s technical capabilities.
Advanced Cryptographic Techniques
Beyond the foundational cryptographic methods, more sophisticated techniques offer enhanced security for server environments. These advanced approaches address complex threats and provide a higher level of protection for sensitive data. Understanding these techniques is crucial for implementing robust server security strategies. This section will explore several key advanced cryptographic techniques and their applications, alongside the challenges inherent in their implementation.
Homomorphic Encryption and its Applications
Homomorphic encryption allows computations to be performed on encrypted data without first decrypting it. This groundbreaking technique enables secure cloud computing and data analysis. Imagine a scenario where a financial institution needs to process sensitive customer data held in an encrypted format on a third-party cloud server. With homomorphic encryption, the cloud server can perform calculations (such as calculating the average balance) on the encrypted data without ever accessing the decrypted information, thereby maintaining confidentiality.
Different types of homomorphic encryption exist, including partially homomorphic encryption (allowing only specific operations, such as addition or multiplication), somewhat homomorphic encryption (allowing a limited number of operations before decryption is needed), and fully homomorphic encryption (allowing any computation). The practicality of fully homomorphic encryption is still under development, but partially and somewhat homomorphic schemes are finding increasing use in various applications.
Unlocking server security relies heavily on robust cryptographic techniques. To truly master these methods and bolster your defenses, delve into the comprehensive guide, Server Security Secrets: Cryptography Mastery , which provides in-depth strategies for implementing effective encryption. By understanding these advanced concepts, you can significantly enhance your server’s resilience against cyber threats and ensure data confidentiality.
Digital Rights Management (DRM) for Protecting Sensitive Data
Digital Rights Management (DRM) is a suite of technologies designed to control access to digital content. It employs various cryptographic techniques to restrict copying, distribution, and usage of copyrighted material. DRM mechanisms often involve encryption of the digital content, coupled with access control measures enforced by digital signatures and keys. A common example is the protection of streaming media services, where DRM prevents unauthorized copying and redistribution of video or audio content.
However, DRM systems are often criticized for being overly restrictive, hindering legitimate uses and creating a frustrating user experience. The balance between effective protection and user accessibility remains a significant challenge in DRM implementation.
Challenges and Limitations of Implementing Advanced Cryptographic Techniques
Implementing advanced cryptographic techniques presents significant challenges. The computational overhead associated with homomorphic encryption, for example, can be substantial, impacting performance and requiring specialized hardware. Furthermore, the complexity of these techniques demands a high level of expertise in both cryptography and software engineering. The selection and proper configuration of cryptographic algorithms are critical; improper implementation can introduce vulnerabilities, undermining the very security they are intended to provide.
Moreover, the ongoing evolution of cryptographic attacks necessitates continuous monitoring and updates to maintain effective protection. The key management aspect becomes even more critical, demanding robust and secure key generation, storage, and rotation processes. Finally, legal and regulatory compliance needs careful consideration, as the use of some cryptographic techniques might be restricted in certain jurisdictions.
Future Trends in Cryptography for Server Security
The field of cryptography is constantly evolving to counter emerging threats. Several key trends are shaping the future of server security:
- Post-Quantum Cryptography: The development of quantum computing poses a significant threat to existing cryptographic algorithms. Post-quantum cryptography focuses on creating algorithms resistant to attacks from quantum computers.
- Lattice-based Cryptography: This promising area is gaining traction due to its potential for resisting both classical and quantum attacks. Lattice-based cryptography offers various cryptographic primitives, including encryption, digital signatures, and key exchange.
- Homomorphic Encryption Advancements: Research continues to improve the efficiency and practicality of homomorphic encryption, making it increasingly viable for real-world applications.
- Blockchain Integration: Blockchain technology, with its inherent security features, can be integrated with cryptographic techniques to enhance the security and transparency of server systems.
- AI-driven Cryptography: Artificial intelligence and machine learning are being applied to enhance the detection of cryptographic weaknesses and improve the design of new algorithms.
Wrap-Up
Securing your servers against modern threats requires a multi-layered approach, and cryptography forms the bedrock of this defense. By understanding and implementing the techniques discussed – from choosing appropriate encryption algorithms and secure protocols to mastering key management and employing robust authentication methods – you can significantly enhance your server’s security posture. Staying informed about emerging threats and evolving cryptographic techniques is crucial for maintaining a resilient and protected digital environment.
Remember, proactive security is the best defense against cyberattacks.
Top FAQs
What are the risks of weak encryption?
Weak encryption leaves your data vulnerable to unauthorized access, data breaches, and potential financial losses. It can also compromise user trust and damage your reputation.
How often should cryptographic keys be rotated?
Key rotation frequency depends on the sensitivity of the data and the threat landscape. Regular rotation, often based on time-based schedules or event-driven triggers, is crucial to mitigate risks associated with key compromise.
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption.
How can I detect if my server has been compromised?
Regular security audits, intrusion detection systems, and monitoring system logs for unusual activity are essential for detecting potential compromises. Look for unauthorized access attempts, unusual network traffic, and file modifications.