Cryptography for Server Admins: Practical Insights delves into the crucial role of cryptography in securing modern server environments. This guide provides a practical, hands-on approach, moving beyond theoretical concepts to equip server administrators with the skills to implement and manage robust security measures. We’ll explore symmetric and asymmetric encryption, hashing algorithms, digital certificates, and the cryptographic underpinnings of essential protocols like SSH and HTTPS.
This isn’t just theory; we’ll cover practical implementation, troubleshooting, and best practices for key management, ensuring you’re prepared to secure your servers effectively.
From understanding fundamental cryptographic principles to mastering the intricacies of key management and troubleshooting common issues, this comprehensive guide empowers server administrators to build a strong security posture. We’ll examine various algorithms, their strengths and weaknesses, and provide step-by-step instructions for implementing secure configurations in real-world scenarios. By the end, you’ll possess the knowledge and confidence to effectively leverage cryptography to protect your server infrastructure.
Introduction to Cryptography for Server Administration
Cryptography is the cornerstone of modern server security, providing the essential tools to protect sensitive data and ensure secure communication. For server administrators, understanding the fundamentals of cryptography is crucial for implementing and managing robust security measures. This section will explore key cryptographic concepts and their practical applications in server environments.
At its core, cryptography involves transforming readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic algorithm and a key. The reverse process, converting ciphertext back to plaintext, requires the correct key. The strength of a cryptographic system relies on the complexity of the algorithm and the secrecy of the key. Proper key management is paramount; a compromised key renders the entire system vulnerable.
Symmetric-key Cryptography
Symmetric-key cryptography uses the same key for both encryption and decryption. This approach is generally faster than asymmetric cryptography but requires a secure method for key exchange, as sharing the key securely is critical. Examples include AES (Advanced Encryption Standard), a widely used block cipher for encrypting data at rest and in transit, and DES (Data Encryption Standard), an older standard now largely superseded by AES due to its vulnerability to modern attacks.
AES, with its various key lengths (128, 192, and 256 bits), offers varying levels of security. The choice of key length depends on the sensitivity of the data and the desired security level.
Asymmetric-key Cryptography
Asymmetric-key cryptography, also known as public-key cryptography, utilizes two separate keys: a public key for encryption and a private key for decryption. The public key can be widely distributed, while the private key must be kept secret. This eliminates the need for secure key exchange, as the sender only needs access to the recipient’s public key. RSA (Rivest-Shamir-Adleman) is a prominent example, widely used for digital signatures and key exchange in SSL/TLS protocols.
ECC (Elliptic Curve Cryptography) is another significant asymmetric algorithm, offering comparable security with smaller key sizes, making it suitable for resource-constrained environments.
Hashing Algorithms
Hashing algorithms generate a fixed-size string (hash) from an input of any size. These hashes are one-way functions; it’s computationally infeasible to reverse the process and obtain the original input from the hash. Hashing is crucial for verifying data integrity and ensuring data hasn’t been tampered with. Examples include SHA-256 (Secure Hash Algorithm 256-bit) and SHA-3, widely used for password storage (salted and hashed) and digital signatures.
MD5, while historically popular, is now considered cryptographically broken and should be avoided.
Real-world Applications of Cryptography in Server Environments
Cryptography underpins numerous server security measures. SSL/TLS certificates, utilizing asymmetric cryptography, secure web traffic by encrypting communication between web servers and clients. SSH (Secure Shell), employing asymmetric and symmetric cryptography, enables secure remote access to servers. Database encryption, using symmetric or asymmetric methods, protects sensitive data stored in databases. File system encryption, often using symmetric algorithms, safeguards data stored on server file systems.
VPN (Virtual Private Network) connections, commonly utilizing IPsec (Internet Protocol Security), encrypt network traffic between servers and clients, ensuring secure communication over public networks. These are just a few examples demonstrating the widespread use of cryptography in securing server infrastructure.
Symmetric-key Cryptography
Symmetric-key cryptography relies on a single, secret key for both encryption and decryption. This shared secret must be securely distributed to all parties involved in communication. Its simplicity and speed make it a cornerstone of many secure systems, despite the challenges inherent in key management.Symmetric-key encryption involves transforming plaintext into ciphertext using an algorithm and the secret key.
Decryption reverses this process, using the same key to recover the original plaintext from the ciphertext. The security of the system entirely depends on the secrecy and strength of the key. Compromise of the key renders all communication vulnerable.
Symmetric-key Algorithm Comparison
Symmetric-key algorithms differ in their key sizes, block sizes, and computational speed. Choosing the right algorithm depends on the specific security requirements and performance constraints of the application. Larger key sizes generally offer greater security, but may impact performance. The block size refers to the amount of data processed at once; larger block sizes can improve efficiency.
| Algorithm | Key Size (bits) | Block Size (bits) | Speed |
|---|---|---|---|
| AES (Advanced Encryption Standard) | 128, 192, 256 | 128 | Fast |
| DES (Data Encryption Standard) | 56 | 64 | Slow |
| 3DES (Triple DES) | 112 or 168 | 64 | Slower than AES |
AES is widely considered the most secure and efficient symmetric-key algorithm for modern applications. DES, while historically significant, is now considered insecure due to its relatively short key size, making it vulnerable to brute-force attacks. 3DES, a more secure variant of DES, applies the DES algorithm three times, but its speed is significantly slower than AES. It’s often considered a transitional algorithm, gradually being replaced by AES.
Securing Server-to-Server Communication with Symmetric-key Cryptography, Cryptography for Server Admins: Practical Insights
Consider two servers, Server A and Server B, needing to exchange sensitive data securely. They could employ a pre-shared secret key, securely distributed through a trusted channel (e.g., out-of-band key exchange using a physical medium or a highly secure initial connection). Server A encrypts the data using the shared key and a chosen symmetric encryption algorithm (like AES).
Server B receives the encrypted data and decrypts it using the same shared key. This ensures only Server A and Server B can access the plaintext data, provided the key remains confidential. Regular key rotation is crucial to mitigate the risk of compromise. The use of a key management system would help streamline this process and enhance security.
Asymmetric-key Cryptography (Public-Key Cryptography)
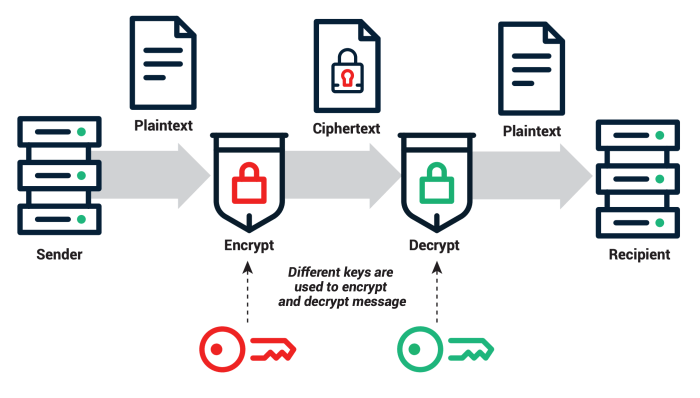
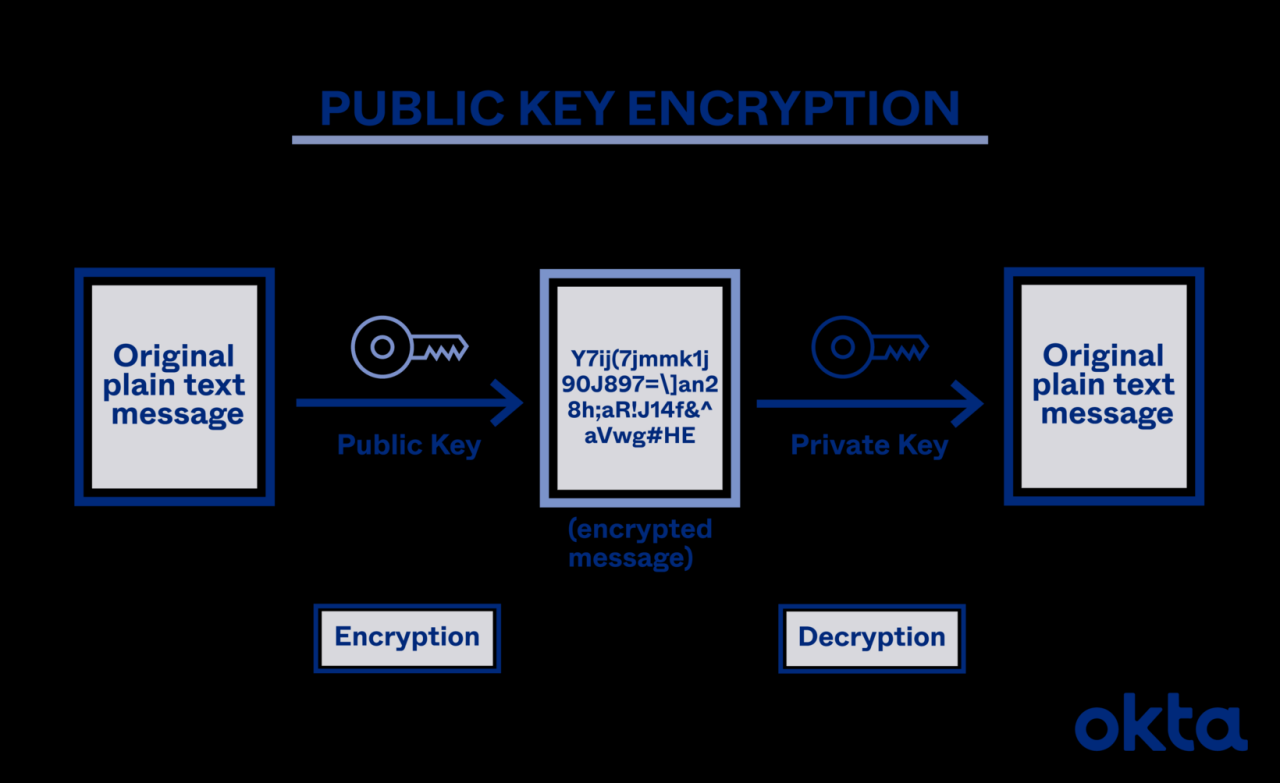
Asymmetric-key cryptography, also known as public-key cryptography, represents a fundamental shift from symmetric-key systems. Unlike symmetric encryption which relies on a single secret key shared between parties, asymmetric cryptography utilizes a pair of keys: a public key and a private key. This key pair is mathematically linked, allowing for secure communication and authentication in environments where secure key exchange is challenging or impossible.
Its application in server security is crucial for establishing trust and protecting sensitive data.Public-key cryptography operates on the principle of one-way functions. These are mathematical operations that are easy to compute in one direction but computationally infeasible to reverse without possessing specific information (the private key). This inherent asymmetry allows for the public key to be widely distributed without compromising the security of the private key.
The public key is used for encryption and verification, while the private key is kept secret and used for decryption and signing. This eliminates the need for secure key exchange, a major vulnerability in symmetric-key systems.
RSA Algorithm in Server Security
The RSA algorithm is one of the most widely used public-key cryptosystems. It relies on the mathematical difficulty of factoring large numbers into their prime components. The algorithm generates a key pair based on two large prime numbers. The public key consists of the modulus (the product of the two primes) and a public exponent. The private key is derived from these primes and the public exponent.
RSA is used in server security for tasks such as secure shell (SSH) connections, encrypting data at rest, and securing web traffic using HTTPS. For instance, in HTTPS, the server’s public key is used to encrypt the initial communication, ensuring that only the server with the corresponding private key can decrypt and establish a secure session.
Elliptic Curve Cryptography (ECC) in Server Security
Elliptic Curve Cryptography (ECC) is another prominent public-key cryptosystem offering comparable security to RSA but with significantly smaller key sizes. This efficiency advantage makes ECC particularly attractive for resource-constrained devices and environments where bandwidth is limited, such as mobile applications and embedded systems often found in Internet of Things (IoT) deployments. ECC relies on the algebraic structure of elliptic curves over finite fields.
Similar to RSA, ECC generates a key pair, with the public key used for encryption and verification, and the private key for decryption and signing. ECC is increasingly adopted in server environments for securing communications and digital signatures, particularly in applications where key management and computational overhead are critical concerns. For example, many modern TLS implementations utilize ECC for key exchange and digital signatures, enhancing security and performance.
Public-Key Cryptography for Authentication and Digital Signatures
Public-key cryptography plays a vital role in server authentication and digital signatures. Server authentication ensures that a client is connecting to the legitimate server and not an imposter. This is typically achieved through the use of digital certificates, which bind a public key to the identity of the server. The certificate is digitally signed by a trusted Certificate Authority (CA), allowing clients to verify the server’s identity.
For example, HTTPS uses digital certificates to authenticate web servers, assuring users that they are communicating with the intended website and not a malicious actor. Digital signatures, on the other hand, provide authentication and data integrity. A server can digitally sign data using its private key, and clients can verify the signature using the server’s public key, ensuring both the authenticity and integrity of the data.
This is crucial for secure software distribution, code signing, and ensuring data hasn’t been tampered with during transit or storage. For example, software updates often include digital signatures to verify their authenticity and prevent malicious modifications.
Digital Certificates and Public Key Infrastructure (PKI)
Digital certificates are the cornerstone of secure server communication in today’s internet landscape. They provide a mechanism to verify the identity of a server and ensure that communication with it is indeed taking place with the intended party, preventing man-in-the-middle attacks and other forms of digital impersonation. This verification process relies heavily on the Public Key Infrastructure (PKI), a complex system of interconnected components working together to establish trust and authenticity.Digital certificates act as digital identities, binding a public key to an entity’s details, such as a domain name or organization.
This binding is cryptographically secured, ensuring that only the legitimate owner can possess the corresponding private key. When a client connects to a server, the server presents its digital certificate. The client’s system then verifies the certificate’s authenticity, ensuring that the server is who it claims to be before proceeding with the secure communication. This verification process is crucial for establishing secure HTTPS connections and other secure interactions.
Digital Certificate Components
A digital certificate contains several key pieces of information crucial for its verification. These components work together to establish trust and prevent forgery. Missing or incorrect information renders the certificate invalid. The certificate’s integrity is checked through a digital signature, usually from a trusted Certificate Authority (CA).
- Subject: This field identifies the entity to which the certificate belongs (e.g., a website’s domain name or an organization’s name).
- Issuer: This field identifies the Certificate Authority (CA) that issued the certificate. The CA’s trustworthiness is essential for the validity of the certificate.
- Public Key: The server’s public key is included, allowing clients to encrypt data for secure communication.
- Validity Period: Specifies the start and end dates during which the certificate is valid.
- Serial Number: A unique identifier for the certificate within the CA’s system.
- Digital Signature: A cryptographic signature from the issuing CA, verifying the certificate’s authenticity and integrity.
Public Key Infrastructure (PKI) Components
PKI is a complex system involving multiple interacting components, each playing a vital role in establishing and maintaining trust. The proper functioning of all these components is essential for a secure and reliable PKI. A malfunction in any part can compromise the entire system.
- Certificate Authority (CA): A trusted third-party entity responsible for issuing and managing digital certificates. CAs verify the identity of certificate applicants before issuing certificates.
- Registration Authority (RA): An intermediary that assists in the verification process, often handling identity verification on behalf of the CA. This reduces the workload on the CA.
- Certificate Repository: A database or directory containing information about issued certificates, allowing clients to access and verify certificates.
- Certificate Revocation List (CRL): A list of certificates that have been revoked due to compromise or other reasons. Clients consult the CRL to ensure that the certificate is still valid.
- Online Certificate Status Protocol (OCSP): An online service that provides real-time verification of certificate validity, offering a more efficient alternative to CRLs.
Verifying a Digital Certificate with OpenSSL
OpenSSL is a powerful command-line tool that allows for the verification of digital certificates. To verify a certificate, you need the certificate file (often found in a `.pem` or `.crt` format) and the CA certificate that issued it. The following example demonstrates the process:openssl verify -CAfile /path/to/ca.crt /path/to/server.crtThis command verifies `/path/to/server.crt` using the CA certificate specified in `/path/to/ca.crt`.
A successful verification will output a message indicating that the certificate is valid. Failure will result in an error message detailing the reason for the failure. Note that `/path/to/ca.crt` should contain the certificate of the CA that issued the server certificate. Incorrectly specifying the CA certificate will lead to verification failure, even if the server certificate itself is valid.
Hashing Algorithms and their Use in Server Security
Hashing algorithms are fundamental to server security, providing crucial mechanisms for password storage and data integrity verification. These algorithms transform data of any size into a fixed-size string of characters, known as a hash. The key characteristic is that even a tiny change in the input data results in a significantly different hash, making them invaluable for detecting tampering and ensuring data authenticity.
Understanding the strengths and weaknesses of various hashing algorithms is critical for selecting the appropriate method for specific security needs.Hashing algorithms are one-way functions; it’s computationally infeasible to reverse the process and obtain the original data from the hash. This characteristic is essential for protecting sensitive information like passwords. Instead of storing passwords directly, systems store their hash values.
When a user logs in, the system hashes the entered password and compares it to the stored hash. A match confirms the correct password without ever revealing the actual password in plain text.
Types of Hashing Algorithms
Several hashing algorithms exist, each with varying levels of security and performance characteristics. Three prominent examples are MD5, SHA-1, and SHA-256. These algorithms differ in their internal processes and the length of the hash they produce, directly impacting their collision resistance – the likelihood of two different inputs producing the same hash.
Comparison of Hashing Algorithms: Security Strengths and Weaknesses
| Algorithm | Hash Length | Security Status | Strengths | Weaknesses |
|---|---|---|---|---|
| MD5 (Message Digest Algorithm 5) | 128 bits | Cryptographically broken | Fast computation | Highly susceptible to collision attacks; should not be used for security-sensitive applications. |
| SHA-1 (Secure Hash Algorithm 1) | 160 bits | Cryptographically broken | Widely used in the past | Vulnerable to collision attacks; deprecated for security-critical applications. |
| SHA-256 (Secure Hash Algorithm 256-bit) | 256 bits | Currently secure | Strong collision resistance; widely used and recommended | Slower computation than MD5 and SHA-1; potential future vulnerabilities remain a possibility, though unlikely in the near future given the hash length. |
Password Storage Using Hashing
A common application of hashing in server security is password storage. Instead of storing passwords in plain text, which would be catastrophic if a database were compromised, a strong hashing algorithm like SHA-256 is used. When a user creates an account, their password is hashed, and only the hash is stored in the database. During login, the entered password is hashed and compared to the stored hash.
If they match, the user is authenticated. To further enhance security, salting (adding a random string to the password before hashing) and peppering (using a secret key in addition to the salt) are often employed to protect against rainbow table attacks and other forms of password cracking.
Data Integrity Verification Using Hashing
Hashing is also vital for verifying data integrity. A hash of a file can be generated and stored separately. Later, if the file is suspected to have been altered, a new hash is calculated and compared to the stored one. Any discrepancy indicates that the file has been tampered with. This technique is frequently used for software distribution, ensuring that downloaded files haven’t been modified during transfer.
For example, many software download sites provide checksums (hashes) alongside their downloads, allowing users to verify the integrity of the downloaded files. This prevents malicious actors from distributing modified versions of software that might contain malware.
Secure Shell (SSH) and its Cryptographic Foundations
Secure Shell (SSH) is a cryptographic network protocol that provides secure remote login and other secure network services over an unsecured network. Its strength lies in its robust implementation of various cryptographic techniques, ensuring confidentiality, integrity, and authentication during remote access. This section details the cryptographic protocols underlying SSH and provides a practical guide to configuring it securely.SSH utilizes a combination of asymmetric and symmetric cryptography to achieve secure communication.
Asymmetric cryptography is employed for key exchange and authentication, while symmetric cryptography handles the encryption and decryption of the actual data stream during the session. This layered approach ensures both secure authentication and efficient data transfer.
SSH Authentication Methods
SSH offers several authentication methods, each leveraging different cryptographic principles. The most common methods are password authentication, public-key authentication, and keyboard-interactive authentication. Password authentication, while convenient, is generally considered less secure due to its susceptibility to brute-force attacks. Public-key authentication, on the other hand, offers a significantly stronger security posture.
Public-Key Authentication in SSH
Public-key authentication relies on the principles of asymmetric cryptography. The user generates a key pair: a private key (kept secret) and a public key (freely distributed). The public key is added to the authorized_keys file on the server. When a user attempts to connect, the server uses the public key to verify the authenticity of the client. Once authenticated, a secure session is established using symmetric encryption.
This eliminates the need to transmit passwords over the network, mitigating the risk of interception.
Symmetric-Key Encryption in SSH
Once authenticated, SSH employs symmetric-key cryptography to encrypt the data exchanged between the client and the server. This involves the creation of a session key, a secret key known only to the client and the server. This session key is used to encrypt and decrypt all subsequent data during the SSH session. The choice of cipher suite dictates the specific symmetric encryption algorithm used (e.g., AES-256-GCM, ChaCha20-poly1305).
Stronger ciphers provide greater security against eavesdropping and attacks.
Configuring SSH with Strong Cryptographic Settings on a Linux Server
A step-by-step guide to configuring SSH with robust cryptographic settings on a Linux server is crucial for maintaining secure remote access. The following steps ensure a high level of security:
- Disable Password Authentication: This is the most critical step. By disabling password authentication, you eliminate a significant vulnerability. Edit the `/etc/ssh/sshd_config` file and set `PasswordAuthentication no`.
- Enable Public Key Authentication: Ensure that `PubkeyAuthentication yes` is enabled in `/etc/ssh/sshd_config`.
- Restrict SSH Access by IP Address: Limit SSH access to specific IP addresses or networks to further reduce the attack surface. Configure `AllowUsers` or `AllowGroups` and `DenyUsers` or `DenyGroups` directives in `/etc/ssh/sshd_config` to control access. For example, `AllowUsers user1@192.168.1.100`.
- Specify Strong Ciphers and MACs: Choose strong encryption algorithms and message authentication codes (MACs) in `/etc/ssh/sshd_config`. For example, `Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com` and `MACs hmac-sha2-512,hmac-sha2-256`.
- Enable SSH Key-Based Authentication: Generate an SSH key pair (public and private keys) using the `ssh-keygen` command. Copy the public key to the `~/.ssh/authorized_keys` file on the server. This allows authentication without passwords.
- Regularly Update SSH: Keep your SSH server software updated to benefit from the latest security patches and improvements.
- Restart SSH Service: After making changes to `/etc/ssh/sshd_config`, restart the SSH service using `sudo systemctl restart ssh`.
HTTPS and TLS/SSL

HTTPS (Hypertext Transfer Protocol Secure) is the cornerstone of secure web communication, leveraging the TLS/SSL (Transport Layer Security/Secure Sockets Layer) protocol to encrypt data exchanged between a client (typically a web browser) and a server. This encryption ensures confidentiality, integrity, and authentication, protecting sensitive information like passwords, credit card details, and personal data from eavesdropping and tampering.HTTPS achieves its security through a combination of cryptographic mechanisms, primarily symmetric and asymmetric encryption, digital certificates, and hashing algorithms.
The process involves a complex handshake between the client and server to establish a secure connection before any data transmission occurs. This handshake negotiates the cryptographic algorithms and parameters to be used for the session.
The Cryptographic Mechanisms of HTTPS
HTTPS relies on a layered approach to security. Initially, an asymmetric encryption algorithm, typically RSA or ECC (Elliptic Curve Cryptography), is used to exchange a symmetric key. This symmetric key, much faster to encrypt and decrypt large amounts of data than asymmetric keys, is then used to encrypt all subsequent communication during the session. Digital certificates, issued by trusted Certificate Authorities (CAs), are crucial for verifying the server’s identity and ensuring that the communication is indeed with the intended recipient.
Hashing algorithms, like SHA-256 or SHA-3, are employed to ensure data integrity, verifying that the data hasn’t been altered during transmission. The specific algorithms used are negotiated during the TLS/SSL handshake.
Certificate Pinning and its Server-Side Implementation
Certificate pinning is a security mechanism that enhances the trust relationship between a client and a server by explicitly defining which certificates the client is allowed to accept. This mitigates the risk of man-in-the-middle (MITM) attacks, where an attacker might present a fraudulent certificate to intercept communication. In server-side applications, certificate pinning is implemented by embedding the expected certificate’s public key or its fingerprint (a cryptographic hash of the certificate) within the application’s code.
The client then verifies the server’s certificate against the pinned values before establishing a connection. If a mismatch occurs, the connection is refused, preventing communication with a potentially malicious server. This approach requires careful management of pinned certificates, especially when certificates need to be renewed. Incorrect implementation can lead to application failures.
The TLS/SSL Handshake Process
The TLS/SSL handshake is a crucial step in establishing a secure connection. Imagine it as a multi-stage dialogue between the client and server:
1. Client Hello
The client initiates the connection by sending a “Client Hello” message, indicating the supported TLS/SSL version, cipher suites (combinations of encryption algorithms and hashing algorithms), and other parameters.
2. Server Hello
The server responds with a “Server Hello” message, selecting a cipher suite from those offered by the client, and sending its digital certificate.
3. Certificate Verification
The client verifies the server’s certificate against a trusted root CA certificate, ensuring the server’s identity.
4. Key Exchange
The client and server use the chosen cipher suite’s key exchange algorithm (e.g., RSA, Diffie-Hellman) to securely negotiate a symmetric session key.
5. Change Cipher Spec
Both client and server signal a change to encrypted communication.
6. Finished
Both sides send a “Finished” message, encrypted with the newly established session key, confirming the successful establishment of the secure connection. This message also verifies the integrity of the handshake process.Following this handshake, all subsequent communication is encrypted using the agreed-upon symmetric key, ensuring confidentiality and integrity of the data exchanged. The entire process is highly complex, involving multiple cryptographic operations and negotiations, but the end result is a secure channel for transmitting sensitive information.
Secure Data Storage and Encryption at Rest
Protecting data stored on servers is paramount for maintaining confidentiality and complying with data protection regulations. Encryption at rest, the process of encrypting data while it’s stored on a server’s hard drives or other storage media, is a crucial security measure. This prevents unauthorized access even if the physical storage device is compromised. Various methods and techniques exist, each with its strengths and weaknesses depending on the specific context and sensitivity of the data.Data encryption at rest utilizes cryptographic algorithms to transform readable data (plaintext) into an unreadable format (ciphertext).
Only authorized parties possessing the decryption key can revert the ciphertext back to its original form. The choice of encryption method depends heavily on factors such as performance requirements, security needs, and the type of storage (databases, file systems). Strong encryption, combined with robust access controls, forms a multi-layered approach to safeguarding sensitive data.
Database Encryption Techniques
Databases often contain highly sensitive information, necessitating strong encryption methods. Full disk encryption, while providing overall protection, might not be sufficient for granular control over database access. Therefore, database-specific encryption techniques are often employed. These include transparent data encryption (TDE), where the database management system (DBMS) handles the encryption and decryption processes without requiring application-level changes, and column-level or row-level encryption, offering more granular control over which data elements are encrypted.
Securing server infrastructure requires a deep understanding of cryptography; server admins need practical knowledge of encryption, hashing, and digital signatures. Effective communication of this crucial knowledge is vital, and learning how to boost your content’s reach, as outlined in this excellent guide on content creation, 17 Trik Memukau Content Creation: View Melonjak 200% , can significantly improve the dissemination of this vital information to a wider audience.
Ultimately, robust server security depends on both strong cryptographic practices and effective communication strategies.
Another approach involves encrypting the entire database file, similar to file system encryption, but tailored to the database’s structure. The choice between these depends on the specific DBMS, performance considerations, and security requirements. For example, a financial institution might opt for row-level encryption for customer transaction data, while a less sensitive application might utilize TDE for overall database protection.
File System Encryption Techniques
File system encryption protects data stored within a file system. Operating systems often provide built-in tools for this purpose, such as BitLocker (Windows) and FileVault (macOS). These tools typically encrypt the entire partition or drive, rendering the data inaccessible without the decryption key. Third-party tools offer similar functionalities, sometimes with additional features like key management and remote access capabilities.
The encryption method used (e.g., AES-256) is a crucial factor influencing the security level. A well-designed file system encryption strategy ensures that even if a server is physically stolen or compromised, the data remains protected. Consider, for instance, a medical facility storing patient records; robust file system encryption is essential to comply with HIPAA regulations.
Implementing Disk Encryption on a Server
Implementing disk encryption involves several steps. First, select an appropriate encryption method and tool, considering factors like performance overhead and compatibility with the server’s operating system and applications. Then, create a strong encryption key, ideally stored securely using a hardware security module (HSM) or a key management system (KMS) to prevent unauthorized access. The encryption process itself involves encrypting the entire hard drive or specific partitions containing sensitive data.
Post-encryption, verify the functionality of the system and establish a secure key recovery process in case of key loss or corruption. Regular backups of the encryption keys are crucial, but these should be stored securely, separate from the server itself. For instance, a server hosting e-commerce transactions should implement disk encryption using a robust method like AES-256, coupled with a secure key management system to protect customer payment information.
Key Management and Best Practices
Secure key management is paramount for the integrity and confidentiality of any system relying on cryptography. Neglecting proper key management renders even the strongest cryptographic algorithms vulnerable, potentially exposing sensitive data to unauthorized access or manipulation. This section details the critical aspects of key management and best practices to mitigate these risks.The risks associated with insecure key handling are significant and far-reaching.
Compromised keys can lead to data breaches, unauthorized access to systems, disruption of services, and reputational damage. Furthermore, the cost of recovering from a key compromise, including legal fees, remediation efforts, and potential fines, can be substantial. Poor key management practices can also result in regulatory non-compliance, exposing organizations to further penalties.
Key Generation Best Practices
Strong cryptographic keys should be generated using cryptographically secure pseudorandom number generators (CSPRNGs). These generators produce sequences of numbers that are statistically indistinguishable from truly random sequences, a crucial factor in preventing predictable key generation. The key length should be appropriate for the chosen algorithm and the security level required. For example, AES-256 requires a 256-bit key, offering significantly stronger protection than AES-128 with its 128-bit key.
The process of key generation should be automated whenever possible to minimize human error and ensure consistency. Furthermore, keys should never be generated based on easily guessable information, such as passwords or readily available data.
Key Storage and Protection
Secure storage of cryptographic keys is critical. Keys should be stored in hardware security modules (HSMs) whenever feasible. HSMs are specialized hardware devices designed to protect cryptographic keys and perform cryptographic operations securely. They offer tamper-resistance and provide a high level of assurance against unauthorized access. Alternatively, if HSMs are not available, keys should be encrypted using a strong encryption algorithm and stored in a secure, isolated environment, ideally with access control mechanisms limiting who can access them.
Access to these keys should be strictly limited to authorized personnel using strong authentication methods. The use of key management systems (KMS) can automate and streamline the key lifecycle management processes, including generation, storage, rotation, and revocation.
Key Rotation and Revocation
Regular key rotation is a crucial security practice. Keys should be rotated at defined intervals based on risk assessment and regulatory requirements. This limits the potential damage from a key compromise, as a compromised key will only be valid for a limited time. A key revocation mechanism should be in place to immediately invalidate compromised keys, preventing their further use.
This mechanism should be robust and reliable, ensuring that all systems and applications using the compromised key are notified and updated accordingly. Proper logging and auditing of key rotation and revocation activities are also essential to maintain accountability and traceability.
Practical Implementation and Troubleshooting
Implementing robust cryptography in server applications requires careful planning and execution. This section details practical steps for database encryption and addresses common challenges encountered during implementation and ongoing maintenance. Effective monitoring and logging are crucial for security auditing and incident response.
Successful cryptographic implementation hinges on understanding the specific needs of the application and selecting appropriate algorithms and key management strategies. Failure to address these aspects can lead to vulnerabilities and compromise the security of sensitive data. This section provides guidance to mitigate these risks.
Database Encryption Implementation
Implementing encryption for a database involves several steps. First, choose an encryption method appropriate for the database system and data sensitivity. Common options include Transparent Data Encryption (TDE) offered by many database systems, or application-level encryption using libraries that handle encryption and decryption.
For TDE, the process usually involves enabling the feature within the database management system’s configuration. This typically requires specifying a master encryption key (MEK) which is then used to encrypt the database encryption keys. The MEK itself should be securely stored, often using a hardware security module (HSM).
Application-level encryption requires integrating encryption libraries into the application code. This involves encrypting data before it’s written to the database and decrypting it upon retrieval. This approach offers more granular control but requires more development effort and careful consideration of performance implications.
Common Challenges and Troubleshooting
Several challenges can arise during cryptographic implementation. Key management is paramount; losing or compromising encryption keys renders data inaccessible or vulnerable. Performance overhead is another concern, especially with resource-intensive encryption algorithms. Incompatibility between different cryptographic libraries or versions can also lead to issues.
Troubleshooting often involves reviewing logs for error messages, checking key management procedures, and verifying the correct configuration of encryption settings. Testing the implementation thoroughly with realistic data volumes and usage patterns is essential to identify potential bottlenecks and vulnerabilities before deployment to production.
Monitoring and Logging Cryptographic Operations
Monitoring and logging cryptographic activities are essential for security auditing and incident response. Logs should record key events, such as key generation, key rotation, encryption/decryption operations, and any access attempts to cryptographic keys or encrypted data.
This information is crucial for detecting anomalies, identifying potential security breaches, and complying with regulatory requirements. Centralized log management systems are recommended for efficient analysis and correlation of security events. Regularly reviewing these logs helps maintain a comprehensive audit trail and ensures the integrity of the cryptographic infrastructure.
Example: Encrypting a MySQL Database with TDE
MySQL offers TDE using the `innodb_encryption` plugin. Enabling it requires setting the `innodb_encryption_type` variable to a suitable encryption algorithm (e.g., AES-256) and providing a master key. The master key can be managed using a dedicated key management system or stored securely within the database server’s operating system. Detailed instructions are available in the MySQL documentation. Failure to properly configure and manage the master key can lead to data loss or exposure.
Regular key rotation is recommended to mitigate this risk.
Epilogue: Cryptography For Server Admins: Practical Insights
Securing your server infrastructure requires a deep understanding of cryptography. This guide has provided a practical overview of essential cryptographic concepts and their application in server administration. By mastering the techniques and best practices discussed—from implementing robust encryption methods to securely managing cryptographic keys—you can significantly enhance the security of your systems and protect sensitive data. Remember, ongoing vigilance and adaptation to evolving threats are key to maintaining a strong security posture in the ever-changing landscape of cybersecurity.
Commonly Asked Questions
What are the common vulnerabilities related to cryptography implementation on servers?
Common vulnerabilities include weak or easily guessable passwords, insecure key management practices (e.g., storing keys unencrypted), outdated cryptographic algorithms, and misconfigurations of security protocols like SSH and HTTPS.
How often should cryptographic keys be rotated?
The frequency of key rotation depends on the sensitivity of the data and the specific security requirements. Best practices often recommend rotating keys at least annually, or more frequently if a security breach is suspected.
What are some open-source tools for managing cryptographic keys?
Several open-source tools can assist with key management, including GnuPG (for encryption and digital signatures) and OpenSSL (for various cryptographic operations).
How can I detect if a server’s cryptographic implementation is compromised?
Regular security audits, intrusion detection systems, and monitoring logs for suspicious activity can help detect compromises. Unexpected performance drops or unusual network traffic might also indicate a problem.