Cryptography: The Key to Server Safety. In today’s interconnected world, server security is paramount. A single breach can expose sensitive data, cripple operations, and inflict significant financial damage. This comprehensive guide delves into the critical role cryptography plays in safeguarding server infrastructure, exploring various encryption techniques, key management strategies, and authentication protocols. We’ll examine both established methods and emerging technologies to provide a robust understanding of how to build a secure and resilient server environment.
From understanding fundamental vulnerabilities to implementing advanced cryptographic techniques, we’ll cover the essential elements needed to protect your servers from a range of threats. We’ll explore the practical applications of cryptography, including TLS/SSL protocols, digital certificates, and hashing algorithms, and delve into best practices for key management and secure coding. Ultimately, this guide aims to equip you with the knowledge and strategies to bolster your server security posture significantly.
Introduction to Server Security and Cryptography
Servers are the backbone of the modern internet, hosting websites, applications, and data crucial to businesses and individuals alike. Without adequate security measures, these servers are vulnerable to a wide range of attacks, leading to data breaches, financial losses, and reputational damage. Cryptography plays a vital role in mitigating these risks by providing secure communication channels and protecting sensitive information.
Server Vulnerabilities and the Role of Cryptography
Servers lacking robust security protocols face numerous threats. These include unauthorized access, data breaches through SQL injection or cross-site scripting (XSS), denial-of-service (DoS) attacks overwhelming server resources, and malware infections compromising system integrity. Cryptography provides a multi-layered defense against these threats. Encryption, for instance, transforms data into an unreadable format, protecting it even if intercepted. Digital signatures ensure data authenticity and integrity, verifying that data hasn’t been tampered with.
Authentication protocols, often incorporating cryptography, verify the identity of users and devices attempting to access the server. By combining various cryptographic techniques, server administrators can significantly reduce their attack surface and protect valuable data.
Examples of Server Attacks and Cryptographic Countermeasures, Cryptography: The Key to Server Safety
Consider a common scenario: a malicious actor attempting to steal user credentials from a web server. Without encryption, transmitted passwords could be easily intercepted during transit. However, using HTTPS (which relies on Transport Layer Security or TLS, a cryptographic protocol), the communication is encrypted, rendering intercepted data meaningless to the attacker. Similarly, SQL injection attacks attempt to exploit vulnerabilities in database queries.
Input validation and parameterized queries can mitigate this risk, but even if an attacker manages to inject malicious code, encrypting the database itself can limit the damage. A denial-of-service attack might flood a server with requests, making it unavailable to legitimate users. While cryptography doesn’t directly prevent DoS attacks, it can help in mitigating their impact by enabling faster authentication and secure communication channels, improving the server’s overall resilience.
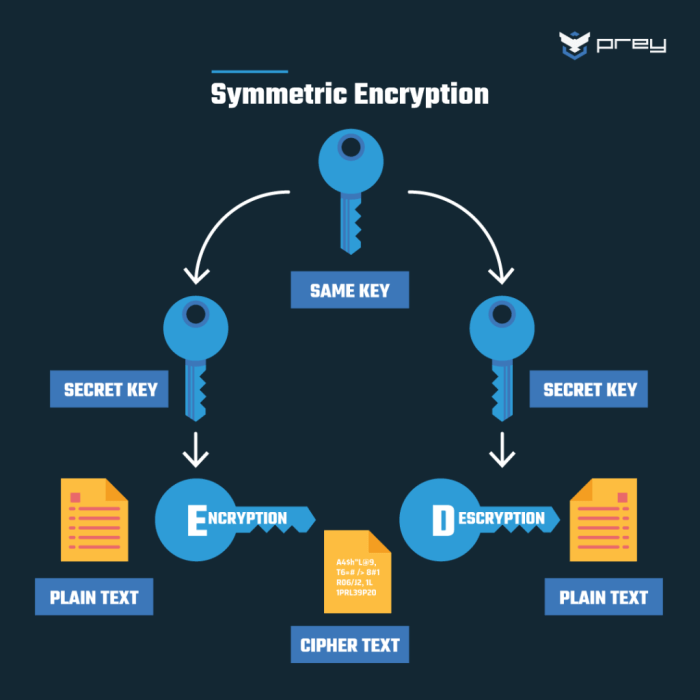
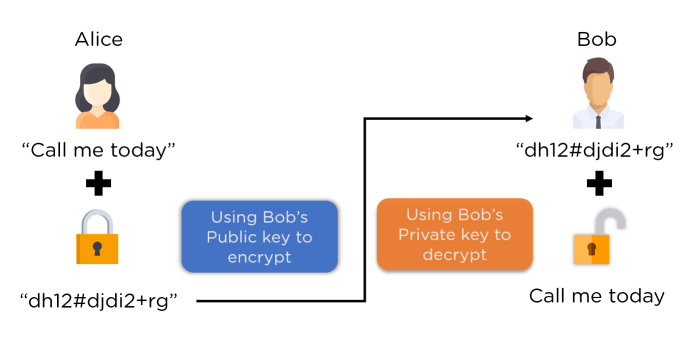
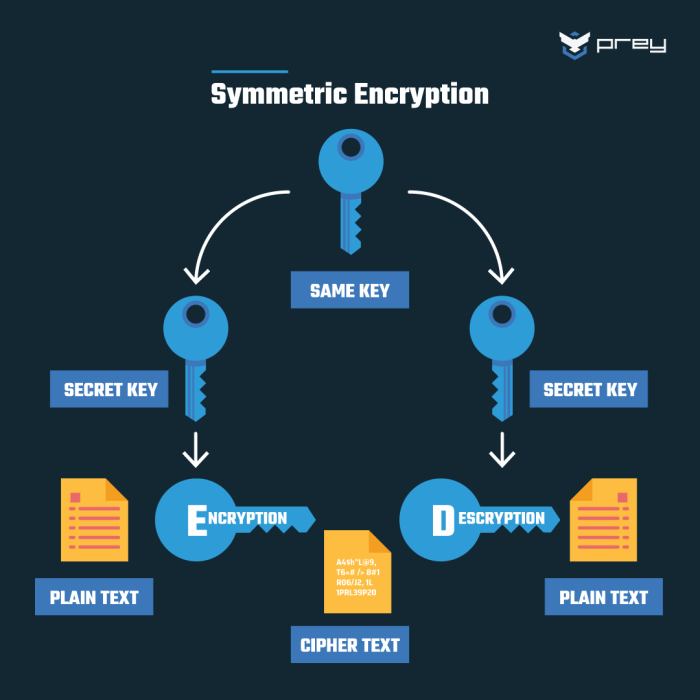
Comparison of Symmetric and Asymmetric Encryption Algorithms
Symmetric and asymmetric encryption are fundamental cryptographic techniques used in server security. They differ significantly in how they handle encryption and decryption keys.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Management | Uses a single secret key for both encryption and decryption. | Uses a pair of keys: a public key for encryption and a private key for decryption. |
| Speed | Generally faster than asymmetric encryption. | Significantly slower than symmetric encryption. |
| Scalability | Key distribution can be challenging with a large number of users. | Better scalability for large networks due to public key distribution. |
| Algorithms | AES, DES, 3DES | RSA, ECC, DSA |
Encryption Techniques in Server Security
Robust encryption is the cornerstone of modern server security, safeguarding sensitive data from unauthorized access and ensuring the integrity of online transactions. This section delves into the crucial encryption techniques employed to protect servers and the data they manage. We will examine the implementation of TLS/SSL, the role of digital certificates, various hashing algorithms for password security, and illustrate the impact of strong encryption through a hypothetical breach scenario.
TLS/SSL Protocol Implementation for Secure Communication
The Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), protocols are fundamental for establishing secure communication channels between clients and servers. TLS/SSL uses a combination of symmetric and asymmetric encryption to achieve confidentiality, integrity, and authentication. The handshake process begins with the negotiation of a cipher suite, determining the encryption algorithms and hashing functions to be used.
The server presents its digital certificate, verifying its identity, and a shared secret key is established. All subsequent communication is then encrypted using this symmetric key, ensuring that only the communicating parties can decipher the exchanged data. The use of forward secrecy, where the session key is ephemeral and not reusable, further enhances security by limiting the impact of potential key compromises.
Digital Certificates for Server Authentication
Digital certificates are crucial for verifying the identity of servers. Issued by trusted Certificate Authorities (CAs), these certificates contain the server’s public key, its domain name, and other identifying information. When a client connects to a server, the server presents its certificate. The client’s browser (or other client software) then verifies the certificate’s authenticity by checking its signature against the CA’s public key.
This process confirms that the server is indeed who it claims to be, preventing man-in-the-middle attacks where an attacker impersonates the legitimate server. The use of extended validation (EV) certificates further strengthens authentication by providing a higher level of assurance regarding the server’s identity.
Comparison of Hashing Algorithms for Password Storage
Storing passwords directly in a database is a significant security risk. Instead, hashing algorithms are used to generate one-way functions, transforming passwords into unique, fixed-length strings. Even if the database is compromised, the original passwords remain protected. Different hashing algorithms offer varying levels of security. Older algorithms like MD5 and SHA-1 are now considered insecure due to vulnerabilities to collision attacks.
More robust algorithms like bcrypt, scrypt, and Argon2 are preferred, as they are computationally expensive, making brute-force attacks significantly more difficult. These algorithms often incorporate a salt (a random string added to the password before hashing), further enhancing security and making it impossible to reuse the same hash for different passwords, even if the same password is used on multiple systems.
Hypothetical Server Breach Scenario and Encryption’s Preventative Role
Imagine an e-commerce website storing customer credit card information in a database. If the database lacks strong encryption and is compromised, the attacker gains access to sensitive data, potentially leading to identity theft and significant financial losses for both the customers and the business. However, if the credit card numbers were encrypted using a robust algorithm like AES-256 before storage, even if the database is breached, the attacker would only obtain encrypted data, rendering it useless without the decryption key.
Furthermore, if TLS/SSL was implemented for all communication channels, the transmission of sensitive data between the client and the server would also be protected from eavesdropping. The use of strong password hashing would also prevent unauthorized access to the database itself, even if an attacker obtained user credentials through phishing or other means. This scenario highlights how strong encryption at various layers—data at rest, data in transit, and authentication—can significantly mitigate the impact of a server breach.
Key Management and Distribution
Secure key management is paramount to the effectiveness of any cryptographic system protecting server infrastructure. A compromised key renders even the strongest encryption algorithms useless, leaving sensitive data vulnerable. This section details best practices for key generation, storage, and distribution, along with an examination of key exchange protocols.
Best Practices for Key Generation, Storage, and Management
Strong cryptographic keys are the foundation of secure server operations. Key generation should leverage cryptographically secure pseudorandom number generators (CSPRNGs) to ensure unpredictability. Keys should be of sufficient length to resist brute-force attacks; for example, 2048-bit RSA keys are generally considered secure at this time, though this is subject to ongoing research and advancements in computing power.
Storing keys securely requires a multi-layered approach. Keys should never be stored in plain text. Instead, they should be encrypted using a strong key encryption key (KEK) and stored in a hardware security module (HSM) or a dedicated, highly secured, and regularly audited key management system. Regular key rotation, replacing keys at predetermined intervals, adds another layer of protection, limiting the impact of a potential compromise.
Access control mechanisms should strictly limit access to keys based on the principle of least privilege.
Challenges of Key Distribution in Distributed Environments
Distributing keys securely across a distributed environment presents significant challenges. The primary concern is ensuring that keys are delivered to the intended recipients without interception or modification by unauthorized parties. Network vulnerabilities, compromised systems, and insider threats all pose risks. The scale and complexity of distributed systems also increase the difficulty of managing and auditing key distribution processes.
Furthermore, ensuring key consistency across multiple systems is crucial for maintaining the integrity of cryptographic operations. Failure to address these challenges can lead to significant security breaches.
Key Exchange Protocols
Several key exchange protocols address the challenges of secure key distribution. The Diffie-Hellman key exchange (DH) is a widely used protocol that allows two parties to establish a shared secret key over an insecure channel. It relies on the mathematical properties of modular arithmetic to achieve this. However, DH is vulnerable to man-in-the-middle attacks if not properly implemented with authentication mechanisms, such as those provided by digital certificates and public key infrastructure (PKI).
Elliptic Curve Diffie-Hellman (ECDH) is a variant that offers improved efficiency and security with smaller key sizes compared to traditional DH. The Transport Layer Security (TLS) protocol, used extensively for secure web communication, leverages key exchange protocols to establish secure connections. Each protocol has strengths and weaknesses related to computational overhead, security against various attacks, and implementation complexity.
The choice of protocol depends on the specific security requirements and the constraints of the environment.
Implementing Secure Key Management in Server Infrastructure: A Step-by-Step Guide
Implementing robust key management involves several key steps:
- Inventory and Assessment: Identify all cryptographic keys used within the server infrastructure, their purpose, and their current management practices.
- Key Generation Policy: Define a clear policy outlining the requirements for key generation, including key length, algorithms, and random number generation methods.
- Key Storage and Protection: Select a secure key storage solution, such as an HSM or a dedicated key management system. Implement strict access control measures.
- Key Rotation Policy: Establish a schedule for regular key rotation, balancing security needs with operational efficiency.
- Key Distribution Mechanisms: Implement secure key distribution mechanisms, using protocols like ECDH or relying on secure channels provided by TLS.
- Auditing and Monitoring: Implement logging and monitoring capabilities to track key usage, access attempts, and any security events related to key management.
- Incident Response Plan: Develop a plan for responding to incidents involving key compromise or suspected security breaches.
Following these steps creates a structured and secure approach to managing cryptographic keys within a server environment, minimizing the risks associated with key compromise and ensuring the ongoing confidentiality, integrity, and availability of sensitive data.
Authentication and Authorization Mechanisms
Server security relies heavily on robust authentication and authorization mechanisms to control access to sensitive resources. These mechanisms ensure that only legitimate users and processes can interact with the server and its data, preventing unauthorized access and potential breaches. This section will explore the key components of these mechanisms, including digital signatures, multi-factor authentication, and access control lists.
Digital Signatures and Data Integrity
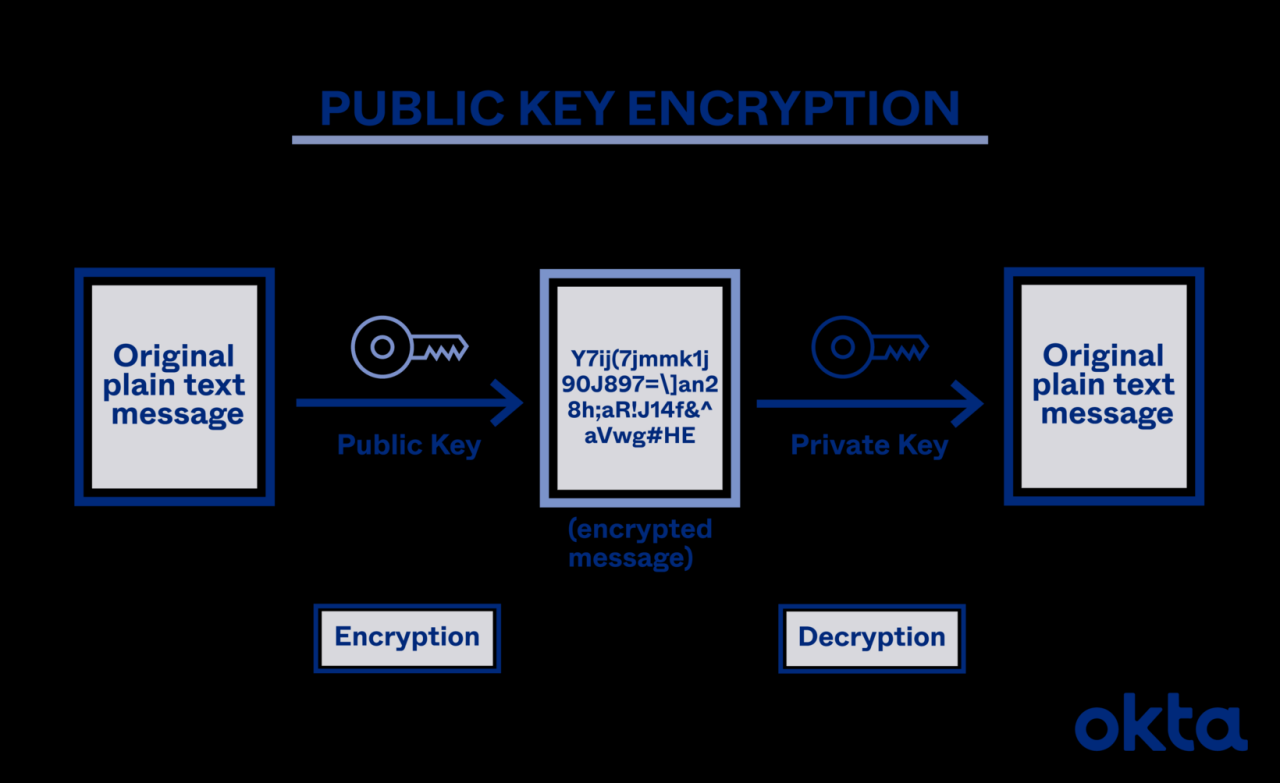
Digital signatures leverage cryptography to verify the authenticity and integrity of data. They provide assurance that a message or document hasn’t been tampered with and originated from a claimed source. This is achieved through the use of asymmetric cryptography, where a private key is used to sign the data, and a corresponding public key is used to verify the signature.
The digital signature algorithm creates a unique hash of the data, which is then encrypted using the sender’s private key. The recipient uses the sender’s public key to decrypt the hash and compare it to a newly computed hash of the received data. A match confirms both the authenticity (the data originated from the claimed sender) and the integrity (the data hasn’t been altered).
This is crucial for secure communication and data exchange on servers. For example, software updates often employ digital signatures to ensure that downloaded files are legitimate and haven’t been modified maliciously.
Multi-Factor Authentication (MFA) Methods for Server Access
Multi-factor authentication enhances server security by requiring multiple forms of authentication to verify a user’s identity. This significantly reduces the risk of unauthorized access, even if one authentication factor is compromised. Common MFA methods for server access include:
- Something you know: This typically involves a password or PIN.
- Something you have: This could be a security token, a smartphone with an authentication app (like Google Authenticator or Authy), or a smart card.
- Something you are: This refers to biometric authentication, such as fingerprint scanning or facial recognition.
- Somewhere you are: This involves verifying the user’s location using GPS or IP address.
A robust MFA implementation might combine a password (something you know) with a time-based one-time password (TOTP) generated by an authentication app on a smartphone (something you have). This ensures that even if someone obtains the password, they still need access to the authorized device to gain access.
Access Control Lists (ACLs) and Resource Restriction
Access Control Lists (ACLs) are crucial for implementing granular access control on servers. ACLs define which users or groups have permission to access specific files, directories, or other resources on the server. Permissions can be set to allow or deny various actions, such as reading, writing, executing, or deleting. For example, a web server might use ACLs to restrict access to sensitive configuration files, preventing unauthorized modification.
ACLs are often implemented at the operating system level or through dedicated access control mechanisms provided by the server software. Effective ACL management ensures that only authorized users and processes have the necessary permissions to interact with critical server components.
Authentication and Authorization Process Flowchart
The following describes a typical authentication and authorization process:The flowchart would visually represent the following steps:
1. User attempts to access a resource
The user initiates a request to access a server resource (e.g., a file, a database).
2. Authentication
The server verifies the user’s identity using a chosen authentication method (e.g., password, MFA).
3. Authorization
If authentication is successful, the server checks the user’s permissions using an ACL or similar mechanism to determine if the user is authorized to access the requested resource.
4. Access Granted/Denied
Based on the authorization check, the server either grants or denies access to the resource.
5. Resource Access/Error Message
Cryptography: The Key to Server Safety, is paramount in today’s digital landscape. Understanding how various cryptographic techniques protect sensitive data is crucial, and a deep dive into the subject reveals the multifaceted nature of server security. For a comprehensive look at the practical applications, check out this excellent resource on How Cryptography Powers Server Security to further solidify your understanding of how cryptography ensures server safety and data integrity.
Ultimately, robust cryptography remains the cornerstone of a secure server environment.
If access is granted, the user can access the resource; otherwise, an appropriate error message is returned.
Advanced Cryptographic Techniques for Server Protection
Protecting server infrastructure in today’s digital landscape necessitates employing advanced cryptographic techniques beyond basic encryption. These methods offer enhanced security against increasingly sophisticated threats, including those leveraging quantum computing. This section delves into several crucial advanced techniques and their practical applications in server security.
Homomorphic Encryption for Secure Cloud Data Processing
Homomorphic encryption allows computations to be performed on encrypted data without decryption. This is particularly valuable for cloud computing, where sensitive data needs to be processed by third-party servers. The core principle involves creating an encryption scheme where operations performed on ciphertexts produce ciphertexts that correspond to the results of the same operations performed on the plaintexts. For example, adding two encrypted numbers results in a ciphertext representing the sum of the original numbers, all without ever revealing the actual numbers themselves.
This technology is still under active development, with various schemes offering different functionalities and levels of efficiency. Fully homomorphic encryption (FHE), which supports all possible computations, is particularly complex and computationally expensive. Partially homomorphic encryption schemes, on the other hand, are more practical and efficient, supporting specific operations like addition or multiplication. The adoption of homomorphic encryption depends on the specific application and the trade-off between security and performance.
For instance, its use in secure medical data analysis or financial modeling is actively being explored, where the need for confidentiality outweighs the computational overhead.
Zero-Knowledge Proofs in Server Security
Zero-knowledge proofs (ZKPs) allow one party (the prover) to demonstrate the truth of a statement to another party (the verifier) without revealing any information beyond the statement’s validity. This is achieved through interactive protocols where the prover convinces the verifier without divulging the underlying data. A classic example is the “Peggy and Victor” protocol, demonstrating knowledge of a graph’s Hamiltonian cycle without revealing the cycle itself.
In server security, ZKPs can be used for authentication, proving identity without revealing passwords or other sensitive credentials. They can also be applied to verifiable computations, where a client can verify the correctness of a computation performed by a server without needing to access the server’s internal data or algorithms. The growing interest in blockchain technology and decentralized systems further fuels the development and application of ZKPs, enhancing privacy and security in various server-based applications.
Quantum-Resistant Cryptography
Quantum computing poses a significant threat to currently used public-key cryptography, as Shor’s algorithm can efficiently factor large numbers and compute discrete logarithms, breaking widely used algorithms like RSA and ECC. Quantum-resistant cryptography (also known as post-quantum cryptography) focuses on developing cryptographic algorithms that are secure against both classical and quantum computers. These algorithms are based on mathematical problems believed to be hard even for quantum computers.
Several promising candidates include lattice-based cryptography, code-based cryptography, multivariate cryptography, and hash-based cryptography. Standardization efforts are underway to select and implement these algorithms, ensuring a smooth transition to a post-quantum secure world. The adoption of quantum-resistant cryptography is crucial for protecting long-term data confidentiality and the integrity of server communications. Government agencies and major technology companies are actively investing in research and development in this area to prepare for the potential threat of quantum computers.
Implementation of Elliptic Curve Cryptography (ECC) in a Simplified Server Environment
Elliptic curve cryptography (ECC) is a public-key cryptosystem offering strong security with relatively shorter key lengths compared to RSA. Consider a simplified server environment where a client needs to securely connect to the server. The server can generate an ECC key pair (public key and private key). The public key is made available to clients, while the private key remains securely stored on the server.
When a client connects, it uses the server’s public key to encrypt a symmetric session key. The server, using its private key, decrypts this session key. Both the client and server then use this symmetric session key to encrypt and decrypt their subsequent communication using a faster and more efficient symmetric encryption algorithm, like AES. This hybrid approach combines the security of ECC for key exchange with the efficiency of symmetric encryption for ongoing data transfer.
The specific implementation would involve using a cryptographic library, such as OpenSSL or libsodium, to handle the key generation, encryption, and decryption processes. This example showcases how ECC can provide a robust foundation for secure communication in a server environment.
Practical Implementation and Best Practices: Cryptography: The Key To Server Safety

Successfully implementing strong cryptography requires more than just selecting the right algorithms. It demands a holistic approach encompassing secure server configurations, robust coding practices, and a proactive security posture. This section details practical steps and best practices for achieving a truly secure server environment.
Securing Server Configurations and Hardening the Operating System
Operating system hardening and secure server configurations form the bedrock of server security. A compromised operating system is a gateway to the entire server infrastructure. Vulnerabilities in the OS or misconfigurations can significantly weaken even the strongest cryptographic implementations. Therefore, minimizing the attack surface is paramount.
- Regular Updates and Patching: Promptly apply all security updates and patches released by the operating system vendor. This mitigates known vulnerabilities exploited by attackers. Automate this process wherever possible.
- Principle of Least Privilege: Grant only the necessary permissions and access rights to users and processes. Avoid running services as root or administrator unless absolutely essential.
- Firewall Configuration: Implement and configure a robust firewall to restrict network access to only necessary ports and services. Block all unnecessary inbound and outbound traffic.
- Disable Unnecessary Services: Disable any services or daemons not explicitly required for the server’s functionality. This reduces the potential attack surface.
- Secure Shell (SSH) Configuration: Use strong SSH keys and disable password authentication. Limit login attempts to prevent brute-force attacks. Regularly audit SSH logs for suspicious activity.
- Regular Security Audits: Conduct periodic security audits to identify and address misconfigurations or vulnerabilities in the server’s operating system and applications.
Secure Coding Practices to Prevent Cryptographic Vulnerabilities
Secure coding practices are crucial to prevent the introduction of cryptographic vulnerabilities in server-side applications. Even the strongest cryptographic algorithms are ineffective if implemented poorly.
- Input Validation and Sanitization: Always validate and sanitize all user inputs before using them in cryptographic operations. This prevents injection attacks, such as SQL injection or cross-site scripting (XSS), that could compromise the security of cryptographic keys or data.
- Proper Key Management: Implement robust key management practices, including secure key generation, storage, and rotation. Avoid hardcoding keys directly into the application code.
- Use Approved Cryptographic Libraries: Utilize well-vetted and regularly updated cryptographic libraries provided by reputable sources. Avoid implementing custom cryptographic algorithms unless absolutely necessary and possessing extensive cryptographic expertise.
- Avoid Weak Cryptographic Algorithms: Do not use outdated or insecure cryptographic algorithms like MD5 or DES. Employ strong, modern algorithms such as AES-256, RSA with sufficiently large key sizes, and SHA-256 or SHA-3.
- Secure Random Number Generation: Use cryptographically secure random number generators (CSPRNGs) for generating keys and other cryptographic parameters. Avoid using pseudo-random number generators (PRNGs) which are predictable and easily compromised.
Importance of Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying and mitigating vulnerabilities before attackers can exploit them. These proactive measures help ensure that the server infrastructure remains secure and resilient against cyber threats.Security audits involve systematic reviews of server configurations, security policies, and application code to identify potential weaknesses. Penetration testing simulates real-world attacks to assess the effectiveness of security controls and identify exploitable vulnerabilities.
A combination of both approaches offers a comprehensive security assessment. Regular, scheduled penetration testing, at least annually, is recommended, with more frequent testing for critical systems. The frequency should also depend on the level of risk associated with the system.
Checklist for Implementing Strong Cryptography Across a Server Infrastructure
Implementing strong cryptography across a server infrastructure is a multi-faceted process. This checklist provides a structured approach to ensure comprehensive security.
- Inventory and Assessment: Identify all servers and applications within the infrastructure that require cryptographic protection.
- Policy Development: Establish clear security policies and procedures for key management, cryptographic algorithm selection, and incident response.
- Cryptography Selection: Choose appropriate cryptographic algorithms based on security requirements and performance considerations.
- Key Management Implementation: Implement a robust key management system for secure key generation, storage, rotation, and access control.
- Secure Coding Practices: Enforce secure coding practices to prevent the introduction of cryptographic vulnerabilities in applications.
- Configuration Hardening: Harden operating systems and applications by disabling unnecessary services, restricting network access, and applying security updates.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify and mitigate vulnerabilities.
- Monitoring and Logging: Implement comprehensive monitoring and logging to detect and respond to security incidents.
- Incident Response Plan: Develop and regularly test an incident response plan to effectively handle security breaches.
- Employee Training: Provide security awareness training to employees to educate them about best practices and potential threats.
Future Trends in Server Security and Cryptography
The landscape of server security is constantly evolving, driven by increasingly sophisticated cyber threats and the rapid advancement of technology. Cryptography, the cornerstone of server protection, is adapting and innovating to meet these challenges, leveraging new techniques and integrating with emerging technologies to ensure the continued integrity and confidentiality of data. This section explores key future trends shaping the evolution of server security and the pivotal role cryptography will play.
Emerging threats are becoming more complex and persistent, requiring a proactive and adaptable approach to security. Quantum computing, for instance, poses a significant threat to current cryptographic algorithms, necessitating the development and deployment of post-quantum cryptography. Furthermore, the increasing sophistication of AI-powered attacks necessitates the development of more robust and intelligent defense mechanisms.
Emerging Threats and Cryptographic Countermeasures
The rise of quantum computing presents a significant challenge to widely used public-key cryptography algorithms like RSA and ECC. These algorithms rely on mathematical problems that are computationally infeasible for classical computers to solve, but quantum computers could potentially break them efficiently. This necessitates the development and standardization of post-quantum cryptography (PQC) algorithms, which are designed to be resistant to attacks from both classical and quantum computers.
Examples of promising PQC algorithms include lattice-based cryptography, code-based cryptography, and multivariate cryptography. The National Institute of Standards and Technology (NIST) is leading the effort to standardize PQC algorithms, and the transition to these new algorithms will be a critical step in maintaining server security in the quantum era. Beyond quantum computing, advanced persistent threats (APTs) and sophisticated zero-day exploits continue to pose significant risks, demanding constant vigilance and the rapid deployment of patches and security updates.
Blockchain Technology’s Impact on Server Security
Blockchain technology, with its decentralized and immutable ledger, offers potential benefits for enhancing server security and data management. By distributing trust and eliminating single points of failure, blockchain can improve data integrity and resilience against attacks. For example, a blockchain-based system could be used to record and verify server logs, making it more difficult to tamper with or falsify audit trails.
Furthermore, blockchain’s cryptographic foundation provides a secure mechanism for managing digital identities and access control, reducing the risk of unauthorized access. However, the scalability and performance limitations of some blockchain implementations need to be addressed before widespread adoption in server security becomes feasible. The energy consumption associated with some blockchain networks also remains a concern.
Artificial Intelligence and Machine Learning in Server Security
Artificial intelligence (AI) and machine learning (ML) are rapidly transforming server security. These technologies can be used to analyze large datasets of security logs and network traffic to identify patterns and anomalies indicative of malicious activity. AI-powered intrusion detection systems (IDS) can detect and respond to threats in real-time, significantly reducing the time it takes to contain security breaches.
Furthermore, ML algorithms can be used to predict potential vulnerabilities and proactively address them before they can be exploited. For example, ML models can be trained to identify suspicious login attempts or unusual network traffic patterns, allowing security teams to take preventative action. However, the accuracy and reliability of AI and ML models depend heavily on the quality and quantity of training data, and adversarial attacks can potentially compromise their effectiveness.
A Vision for the Future of Server Security
The future of server security hinges on a multifaceted approach that combines advanced cryptographic techniques, robust security protocols, and the intelligent application of AI and ML. A key aspect will be the seamless integration of post-quantum cryptography to mitigate the threat posed by quantum computers. Blockchain technology offers promising avenues for enhancing data integrity and trust, but its scalability and energy consumption need to be addressed.
AI and ML will play an increasingly important role in threat detection and response, but their limitations must be carefully considered. Ultimately, a layered security approach that incorporates these technologies and fosters collaboration between security professionals and researchers will be crucial in safeguarding servers against the evolving cyber threats of the future. The continuous development and refinement of cryptographic algorithms and protocols will remain the bedrock of robust server security.
Conclusion
Securing your server infrastructure requires a multifaceted approach, and cryptography forms the cornerstone of a robust defense. By understanding and implementing the techniques and best practices Artikeld in this guide, you can significantly reduce your vulnerability to attacks and protect your valuable data. Remember, continuous vigilance and adaptation are crucial in the ever-evolving landscape of cybersecurity. Staying informed about emerging threats and advancements in cryptography is vital to maintaining a high level of server security.
Commonly Asked Questions
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, offering speed but requiring secure key exchange. Asymmetric encryption uses separate keys (public and private), simplifying key distribution but being slower.
How often should I update my server’s cryptographic keys?
Key update frequency depends on the sensitivity of the data and the risk profile. Regular updates, at least annually, are recommended, with more frequent updates for high-risk systems.
What are some common vulnerabilities in server-side applications that cryptography can address?
Common vulnerabilities include SQL injection, cross-site scripting (XSS), and insecure direct object references. Proper input validation and parameterized queries, combined with robust authentication and authorization, can mitigate these risks.
What is quantum-resistant cryptography and why is it important?
Quantum-resistant cryptography refers to algorithms designed to withstand attacks from quantum computers. As quantum computing advances, existing encryption methods could become vulnerable, making quantum-resistant cryptography a crucial area of research and development.