Server Security Secrets Revealed: Cryptography Insights unveils the critical role of cryptography in safeguarding modern servers. This exploration delves into the intricacies of various encryption techniques, hashing algorithms, and digital signature methods, revealing how they protect against common cyber threats. We’ll dissect symmetric and asymmetric encryption, exploring the strengths and weaknesses of AES, DES, 3DES, RSA, and ECC. The journey continues with a deep dive into Public Key Infrastructure (PKI), SSL/TLS protocols, and strategies to mitigate vulnerabilities like SQL injection and cross-site scripting.
We’ll examine best practices for securing servers across different environments, from on-premise setups to cloud deployments. Furthermore, we’ll look ahead to advanced cryptographic techniques like homomorphic encryption and quantum-resistant cryptography, ensuring your server security remains robust in the face of evolving threats. This comprehensive guide provides actionable steps to fortify your server defenses and maintain data integrity.
Introduction to Server Security and Cryptography
Server security is paramount in today’s digital landscape, safeguarding sensitive data and ensuring the integrity of online services. Cryptography, the practice and study of techniques for secure communication in the presence of adversarial behavior, plays a critical role in achieving this. Without robust cryptographic methods, servers are vulnerable to a wide range of attacks, from data breaches to denial-of-service disruptions.
Understanding the fundamentals of cryptography and its application within server security is essential for building resilient and secure systems.Cryptography provides the essential building blocks for securing various aspects of server operations. It ensures confidentiality, integrity, and authenticity of data transmitted to and from the server, as well as the server’s own operational integrity. This is achieved through the use of sophisticated algorithms and protocols that transform data in ways that make it unintelligible to unauthorized parties.
The effectiveness of these measures directly impacts the overall security posture of the server and the applications it hosts.
Types of Cryptographic Algorithms Used for Server Protection
Several categories of cryptographic algorithms contribute to server security. Symmetric-key cryptography uses the same secret key for both encryption and decryption, offering speed and efficiency. Examples include Advanced Encryption Standard (AES) and Triple DES (3DES), frequently used for securing data at rest and in transit. Asymmetric-key cryptography, also known as public-key cryptography, employs a pair of keys – a public key for encryption and a private key for decryption.
This is crucial for tasks like secure communication (TLS/SSL) and digital signatures. RSA and ECC (Elliptic Curve Cryptography) are prominent examples. Hash functions, such as SHA-256 and SHA-3, generate a unique fingerprint of data, used for verifying data integrity and creating digital signatures. Finally, digital signature algorithms, like RSA and ECDSA, combine asymmetric cryptography and hash functions to provide authentication and non-repudiation.
The selection of appropriate algorithms depends on the specific security requirements and the trade-off between security strength and performance.
Common Server Security Vulnerabilities Related to Cryptography
Improper implementation of cryptographic algorithms is a major source of vulnerabilities. Weak or outdated algorithms, such as using outdated versions of SSL/TLS or employing insufficient key lengths, can be easily compromised by attackers with sufficient computational resources. For instance, the Heartbleed vulnerability exploited a flaw in OpenSSL’s implementation of the TLS protocol, allowing attackers to extract sensitive information from servers.
Another common issue is the use of hardcoded cryptographic keys within server applications. If an attacker gains access to the server, these keys can be easily extracted, compromising the entire system. Key management practices are also critical. Failure to properly generate, store, and rotate cryptographic keys can significantly weaken the server’s security. Furthermore, vulnerabilities in the implementation of cryptographic libraries or the application itself can introduce weaknesses, even if the underlying algorithms are strong.
Finally, the failure to properly validate user inputs before processing them can lead to vulnerabilities like injection attacks, which can be exploited to bypass security measures.
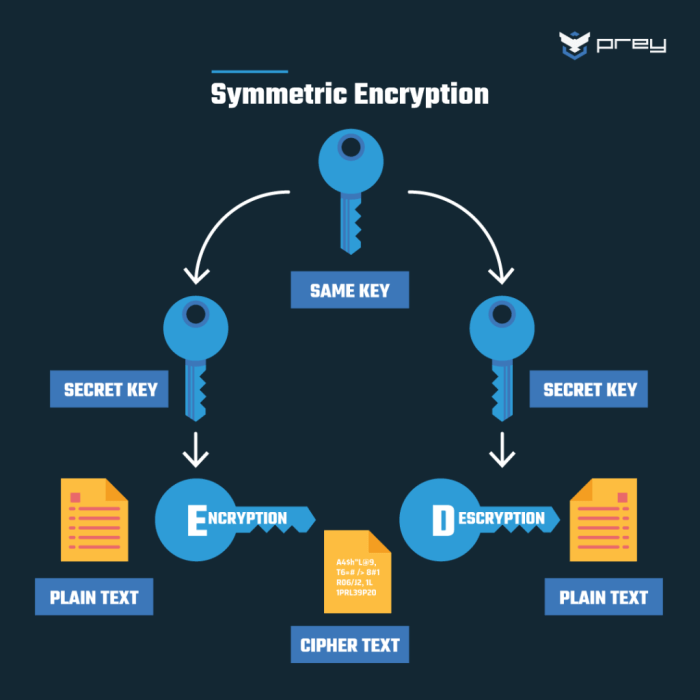
Symmetric Encryption Techniques
Symmetric encryption employs a single, secret key for both encryption and decryption. Its speed and efficiency make it ideal for securing large amounts of data, particularly in server-to-server communication where performance is critical. However, secure key exchange presents a significant challenge. This section will explore three prominent symmetric encryption algorithms: AES, DES, and 3DES, comparing their strengths and weaknesses and illustrating their application in a practical scenario.
Comparison of AES, DES, and 3DES
AES (Advanced Encryption Standard), DES (Data Encryption Standard), and 3DES (Triple DES) represent different generations of symmetric encryption algorithms. AES, the current standard, offers significantly improved security compared to its predecessors. DES, while historically important, is now considered insecure due to its relatively short key length. 3DES, a modification of DES, attempts to address this weakness but suffers from performance limitations.
| Feature | AES | DES | 3DES |
|---|---|---|---|
| Key Size | 128, 192, or 256 bits | 56 bits | 112 or 168 bits (using three 56-bit keys) |
| Block Size | 128 bits | 64 bits | 64 bits |
| Rounds | 10-14 rounds (depending on key size) | 16 rounds | 3 sets of DES operations (effectively 48 rounds) |
| Security | High, considered secure against current attacks | Low, vulnerable to brute-force attacks | Medium, more secure than DES but slower than AES |
| Performance | Fast | Fast (relatively) | Slow |
Strengths and Weaknesses of Symmetric Encryption Methods
The strengths and weaknesses of each algorithm are directly related to their key size, block size, and the number of rounds in their operation. A larger key size and more rounds generally provide stronger security against brute-force and other cryptanalytic attacks.
- AES Strengths: High security, fast performance, widely supported.
- AES Weaknesses: Requires secure key exchange mechanisms.
- DES Strengths: Relatively simple to implement (historically).
- DES Weaknesses: Extremely vulnerable to brute-force attacks due to its short key size.
- 3DES Strengths: More secure than DES, widely implemented.
- 3DES Weaknesses: Significantly slower than AES, considered less efficient than AES.
Scenario: Server-to-Server Communication using Symmetric Encryption
Imagine two servers, Server A and Server B, needing to exchange sensitive financial data. They could use AES-256 to encrypt the data. First, they would establish a shared secret key using a secure key exchange protocol like Diffie-Hellman. Server A encrypts the data using the shared secret key and AES-256. The encrypted data is then transmitted to Server B.
Server B decrypts the data using the same shared secret key and AES-256, retrieving the original financial information. This ensures confidentiality during transmission, as only servers possessing the shared key can decrypt the data. The choice of AES-256 offers strong protection against unauthorized access. This scenario highlights the importance of both the encryption algorithm (AES) and a secure key exchange method for the overall security of the communication.
Asymmetric Encryption and Digital Signatures
Asymmetric encryption, unlike its symmetric counterpart, utilizes two separate keys: a public key for encryption and a private key for decryption. This fundamental difference enables secure key exchange and the creation of digital signatures, crucial elements for robust server security. This section delves into the mechanics of asymmetric encryption, focusing on RSA and Elliptic Curve Cryptography (ECC), and explores the benefits of digital signatures in server authentication and data integrity.Asymmetric encryption is based on the principle of a one-way function, mathematically difficult to reverse without the appropriate key.
This allows for the secure transmission of sensitive information, even over insecure channels, because only the holder of the private key can decrypt the message. This system forms the bedrock of many secure online interactions, including HTTPS and secure email.
RSA Algorithm for Key Exchange and Digital Signatures
The RSA algorithm, named after its inventors Rivest, Shamir, and Adleman, is a widely used asymmetric encryption algorithm. It relies on the computational difficulty of factoring large numbers into their prime components. For key exchange, one party shares their public key, allowing the other party to encrypt a message using this key. Only the recipient, possessing the corresponding private key, can decrypt the message.
For digital signatures, the sender uses their private key to create a signature, which can then be verified by anyone using the sender’s public key. This ensures both authenticity and integrity of the message. The security of RSA is directly tied to the size of the keys; larger keys offer greater resistance to attacks. However, the computational cost increases significantly with key size.
Elliptic Curve Cryptography (ECC) for Key Exchange and Digital Signatures
Elliptic Curve Cryptography (ECC) offers a more efficient alternative to RSA. ECC relies on the algebraic structure of elliptic curves over finite fields. For the same level of security, ECC uses significantly smaller key sizes compared to RSA, leading to faster encryption and decryption processes and reduced computational overhead. This makes ECC particularly suitable for resource-constrained environments like mobile devices and embedded systems.
Like RSA, ECC can be used for both key exchange and digital signatures, providing similar security guarantees with enhanced performance.
Benefits of Digital Signatures for Server Authentication and Data Integrity
Digital signatures provide crucial security benefits for servers. Server authentication ensures that a client is communicating with the intended server, preventing man-in-the-middle attacks. Data integrity guarantees that the data received has not been tampered with during transmission. Digital signatures achieve this by cryptographically linking a message to the identity of the sender. Any alteration to the message invalidates the signature, alerting the recipient to potential tampering.
This significantly enhances the trustworthiness of server-client communication.
Comparison of RSA and ECC
| Algorithm | Key Size | Computational Cost | Security Level |
|---|---|---|---|
| RSA | 2048 bits or higher for high security | High, especially for larger key sizes | Equivalent to ECC with smaller key size |
| ECC | 256 bits or higher for comparable security to 2048-bit RSA | Lower than RSA for equivalent security levels | Comparable to RSA with smaller key size |
Hashing Algorithms and their Applications
Hashing algorithms are fundamental to modern server security, providing crucial functionalities for password storage and data integrity verification. These algorithms transform data of arbitrary size into a fixed-size string of characters, known as a hash. The key characteristic of a secure hashing algorithm is its one-way nature: it’s computationally infeasible to reverse the process and obtain the original data from its hash.
This property makes them invaluable for security applications where protecting data confidentiality and integrity is paramount.Hashing algorithms like SHA-256 and SHA-3 offer distinct advantages in terms of security and performance. Understanding their properties and applications is essential for implementing robust security measures.
Secure Hashing Algorithm Properties
Secure hashing algorithms, such as SHA-256 and SHA-3, possess several crucial properties. These properties ensure their effectiveness in various security applications. A strong hashing algorithm should exhibit collision resistance, meaning it’s extremely difficult to find two different inputs that produce the same hash value. It should also demonstrate pre-image resistance, making it computationally infeasible to determine the original input from its hash.
Finally, second pre-image resistance ensures that given an input and its hash, finding a different input with the same hash is practically impossible. SHA-256 and SHA-3 are designed to meet these requirements, offering varying levels of security depending on the specific needs of the application. SHA-3, for example, is designed with a different underlying structure than SHA-256, providing enhanced resistance against potential future attacks.
Password Storage and Hashing
Storing passwords directly in a database presents a significant security risk. If the database is compromised, all passwords are exposed. Hashing offers a solution. Instead of storing passwords in plain text, we store their hashes. When a user attempts to log in, the entered password is hashed, and the resulting hash is compared to the stored hash.
A match indicates a successful login. However, simply hashing passwords is insufficient. A sophisticated attacker could create a rainbow table—a pre-computed table of hashes—to crack passwords.
Secure Password Hashing Scheme Implementation
To mitigate the risks associated with simple password hashing, a secure scheme incorporates salting and key stretching. Salting involves adding a random string (the salt) to the password before hashing. This ensures that the same password produces different hashes even if the same hashing algorithm is used. Key stretching techniques, such as PBKDF2 (Password-Based Key Derivation Function 2), apply the hashing algorithm iteratively, increasing the computational cost for attackers attempting to crack passwords.
This makes brute-force and rainbow table attacks significantly more difficult.Here’s a conceptual example of a secure password hashing scheme using SHA-256, salting, and PBKDF2:
- Generate a random salt.
- Concatenate the salt with the password.
- Apply PBKDF2 with SHA-256, using a high iteration count (e.g., 100,000 iterations).
- Store both the salt and the resulting hash in the database.
- During login, repeat steps 1-3 and compare the generated hash with the stored hash.
This approach significantly enhances password security, making it much harder for attackers to compromise user accounts. The use of a high iteration count in PBKDF2 dramatically increases the computational effort required to crack passwords, effectively protecting against brute-force attacks. The salt ensures that even if the same password is used across multiple systems, the resulting hashes will be different.
Data Integrity Verification using Hashing
Hashing also plays a critical role in verifying data integrity. By generating a hash of a file or data set, we can ensure that the data hasn’t been tampered with. If the hash of the original data matches the hash of the received data, it indicates that the data is intact. This technique is frequently used in software distribution, where hashes are provided to verify the authenticity and integrity of downloaded files.
Any alteration to the file will result in a different hash, immediately alerting the user to potential corruption or malicious modification. This simple yet powerful mechanism provides a crucial layer of security against data manipulation and ensures data trustworthiness.
Public Key Infrastructure (PKI) and Certificate Management: Server Security Secrets Revealed: Cryptography Insights
Public Key Infrastructure (PKI) is a system that uses digital certificates to verify the authenticity and integrity of online communications. It’s crucial for securing server communication, enabling secure transactions and protecting sensitive data exchanged between servers and clients. Understanding PKI’s components and the process of certificate management is paramount for robust server security.PKI Components and Their Roles in Securing Server Communication
PKI System Components and Their Roles
A PKI system comprises several key components working in concert to establish trust and secure communication. These components include:
- Certificate Authority (CA): The CA is the trusted third party responsible for issuing and managing digital certificates. It verifies the identity of the certificate applicant and guarantees the authenticity of the public key bound to the certificate. Think of a CA as a digital notary public.
- Registration Authority (RA): RAs act as intermediaries between the CA and certificate applicants. They often handle the verification process, reducing the workload on the CA. Not all PKI systems utilize RAs.
- Certificate Repository: This is a central database storing issued certificates, allowing users and systems to verify the authenticity of certificates before establishing a connection.
- Certificate Revocation List (CRL): A CRL lists certificates that have been revoked due to compromise or other reasons. This mechanism ensures that outdated or compromised certificates are not trusted.
- Digital Certificates: These are electronic documents that bind a public key to an entity’s identity. They contain information such as the subject’s name, public key, validity period, and the CA’s digital signature.
These components work together to create a chain of trust. A client can verify the authenticity of a server’s certificate by tracing it back to a trusted CA.
Obtaining and Managing SSL/TLS Certificates for Servers
The process of obtaining and managing SSL/TLS certificates involves several steps, beginning with a Certificate Signing Request (CSR) generation.
- Generate a CSR: This request contains the server’s public key and other identifying information. The CSR is generated using OpenSSL or similar tools.
- Submit the CSR to a CA: The CSR is submitted to a CA (or RA) for verification. This often involves providing proof of domain ownership.
- CA Verification: The CA verifies the information provided in the CSR. This process may involve email verification, DNS record checks, or other methods.
- Certificate Issuance: Once verification is complete, the CA issues a digital certificate containing the server’s public key and other relevant information.
- Install the Certificate: The issued certificate is installed on the server. This typically involves placing the certificate file in a specific directory and configuring the web server to use it.
- Certificate Renewal: Certificates have a limited validity period (often one or two years). They must be renewed before they expire to avoid service disruptions.
Proper certificate management involves monitoring expiration dates and renewing certificates proactively to maintain continuous secure communication.
Implementing Certificate Pinning to Prevent Man-in-the-Middle Attacks
Certificate pinning is a security mechanism that mitigates the risk of man-in-the-middle (MITM) attacks. It works by hardcoding the expected certificate’s public key or its fingerprint into the client application.
- Identify the Certificate Fingerprint: Obtain the SHA-256 or SHA-1 fingerprint of the server’s certificate. This can be done using OpenSSL or other tools.
- Embed the Fingerprint in the Client Application: The fingerprint is embedded into the client-side code (e.g., mobile app, web browser extension).
- Client-Side Verification: Before establishing a connection, the client application verifies the server’s certificate against the pinned fingerprint. If they don’t match, the connection is rejected.
- Update Pinned Fingerprints: When a certificate is renewed, the pinned fingerprint must be updated in the client application. Failure to do so will result in connection failures.
Certificate pinning provides an extra layer of security by preventing attackers from using fraudulent certificates to intercept communication, even if they compromise the CA. However, it requires careful management to avoid breaking legitimate connections during certificate renewals. For instance, if a pinned certificate expires and is not updated in the client application, the application will fail to connect to the server.
Secure Socket Layer (SSL) and Transport Layer Security (TLS)
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols designed to provide secure communication over a network, primarily the internet. While often used interchangeably, they represent distinct but closely related technologies, with TLS being the successor to SSL. Understanding their differences and functionalities is crucial for implementing robust server security.SSL and TLS both operate by establishing an encrypted link between a client (like a web browser) and a server.
This link ensures that data exchanged between the two remains confidential and protected from eavesdropping or tampering. The protocols achieve this through a handshake process that establishes a shared secret key, enabling symmetric encryption for the subsequent data transfer. However, key differences exist in their versions and security features.
SSL and TLS Protocol Versions and Differences
SSL versions 2.0 and 3.0, while historically significant, are now considered insecure and deprecated due to numerous vulnerabilities. TLS, starting with version 1.0, addressed many of these weaknesses and introduced significant improvements in security and performance. TLS 1.0, 1.1, and 1.2, while better than SSL, also have known vulnerabilities and are being phased out in favor of TLS 1.3.
TLS 1.3 represents a significant advancement, featuring improved performance, enhanced security, and streamlined handshake procedures. Key differences include stronger cipher suites, forward secrecy, and removal of insecure features. The transition to TLS 1.3 is essential for maintaining a high level of security. For example, TLS 1.3 offers perfect forward secrecy (PFS), meaning that even if a long-term key is compromised, past communications remain secure.
Older protocols lacked this crucial security feature.
TLS Ensuring Secure Communication, Server Security Secrets Revealed: Cryptography Insights
TLS ensures secure communication through a multi-step process. First, a client initiates a connection to a server. The server then presents its digital certificate, which contains the server’s public key and other identifying information. The client verifies the certificate’s authenticity through a trusted Certificate Authority (CA). Once verified, the client and server negotiate a cipher suite—a set of cryptographic algorithms to be used for encryption and authentication.
This involves a key exchange, typically using Diffie-Hellman or Elliptic Curve Diffie-Hellman, which establishes a shared secret key. This shared key is then used to encrypt all subsequent communication using a symmetric encryption algorithm. This process guarantees confidentiality, integrity, and authentication. For instance, a user accessing their online banking platform benefits from TLS, as their login credentials and transaction details are encrypted, protecting them from interception by malicious actors.
Best Practices for Configuring and Maintaining Secure TLS Connections
Maintaining secure TLS connections requires diligent configuration and ongoing maintenance. This involves selecting strong cipher suites that support modern cryptographic algorithms and avoiding deprecated or vulnerable ones. Regularly updating server software and certificates is vital to patch security vulnerabilities and maintain compatibility. Implementing HTTPS Strict Transport Security (HSTS) forces browsers to always use HTTPS, preventing downgrade attacks.
Furthermore, employing certificate pinning helps prevent man-in-the-middle attacks by restricting the trusted certificates for a specific domain. Regularly auditing TLS configurations and penetration testing are essential to identify and address potential weaknesses. For example, a company might implement a policy mandating the use of TLS 1.3 and only strong cipher suites, alongside regular security audits and penetration tests to ensure the security of their web applications.
Server Security Secrets Revealed: Cryptography Insights dives deep into the essential role of encryption in protecting sensitive data. Understanding how these mechanisms function is crucial, and to get a foundational grasp on this, check out this excellent resource on How Cryptography Powers Server Security. This understanding forms the bedrock of advanced server security strategies detailed in Server Security Secrets Revealed: Cryptography Insights.
Protecting Against Common Server Attacks
Server security extends beyond robust cryptography; it necessitates a proactive defense against common attack vectors. Ignoring these vulnerabilities leaves even the most cryptographically secure systems exposed. This section details common threats and mitigation strategies, emphasizing the role of cryptography in bolstering overall server protection.
Three prevalent attack types—SQL injection, cross-site scripting (XSS), and denial-of-service (DoS)—pose significant risks to server integrity and availability. Understanding their mechanisms and implementing effective countermeasures is crucial for maintaining a secure server environment.
SQL Injection Prevention
SQL injection attacks exploit vulnerabilities in database interactions. Attackers inject malicious SQL code into input fields, manipulating database queries to gain unauthorized access or modify data. Cryptographic techniques aren’t directly used to prevent SQL injection itself, but secure coding practices and input validation are paramount. These practices prevent malicious code from reaching the database. For example, parameterized queries, which treat user inputs as data rather than executable code, are a crucial defense.
This prevents the injection of malicious SQL commands. Furthermore, using an ORM (Object-Relational Mapper) can significantly reduce the risk by abstracting direct database interactions. Robust input validation, including escaping special characters and using whitelisting techniques to restrict allowed input, further reinforces security.
Cross-Site Scripting (XSS) Mitigation
Cross-site scripting (XSS) attacks involve injecting malicious scripts into websites viewed by other users. These scripts can steal cookies, session tokens, or other sensitive information. Output encoding and escaping are essential in mitigating XSS vulnerabilities. By converting special characters into their HTML entities, the server prevents the browser from interpreting the malicious script as executable code. Content Security Policy (CSP) headers provide an additional layer of defense by defining which sources the browser is allowed to load resources from, restricting the execution of untrusted scripts.
Regular security audits and penetration testing help identify and address potential XSS vulnerabilities before they can be exploited.
Denial-of-Service (DoS) Attack Countermeasures
Denial-of-service (DoS) attacks aim to overwhelm a server with traffic, making it unavailable to legitimate users. While cryptography doesn’t directly prevent DoS attacks, it plays a crucial role in authentication and authorization. Strong authentication mechanisms, such as multi-factor authentication, make it more difficult for attackers to flood the server with requests. Rate limiting, which restricts the number of requests from a single IP address within a specific time frame, is a common mitigation technique.
Distributed Denial-of-Service (DDoS) attacks require more sophisticated solutions, such as using a Content Delivery Network (CDN) to distribute traffic across multiple servers and employing DDoS mitigation services that filter malicious traffic.
Implementing a Multi-Layered Security Approach
A comprehensive server security strategy requires a multi-layered approach. This includes:
A layered approach combines various security measures to create a robust defense. No single solution guarantees complete protection; instead, multiple layers work together to minimize vulnerabilities.
- Network Security: Firewalls, intrusion detection/prevention systems (IDS/IPS), and virtual private networks (VPNs) control network access and monitor for malicious activity.
- Server Hardening: Regularly updating the operating system and applications, disabling unnecessary services, and using strong passwords are essential for minimizing vulnerabilities.
- Application Security: Secure coding practices, input validation, and output encoding protect against vulnerabilities like SQL injection and XSS.
- Data Security: Encryption at rest and in transit protects sensitive data from unauthorized access. Regular backups and disaster recovery planning ensure business continuity.
- Monitoring and Logging: Regularly monitoring server logs for suspicious activity allows for prompt identification and response to security incidents. Intrusion detection systems provide automated alerts for potential threats.
Advanced Cryptographic Techniques
Beyond the foundational cryptographic methods, several advanced techniques offer enhanced security and address emerging threats in server environments. These techniques are crucial for safeguarding sensitive data and ensuring the integrity of server communications in increasingly complex digital landscapes. This section explores three key areas: elliptic curve cryptography, homomorphic encryption, and quantum-resistant cryptography.
Elliptic Curve Cryptography (ECC) Applications in Server Security
Elliptic curve cryptography leverages the mathematical properties of elliptic curves to provide comparable security to RSA and other traditional methods, but with significantly smaller key sizes. This efficiency translates to faster encryption and decryption processes, reduced bandwidth consumption, and lower computational overhead, making it particularly suitable for resource-constrained environments like mobile devices and embedded systems, as well as high-volume server operations.
ECC is widely used in securing TLS/SSL connections, protecting data in transit, and enabling secure authentication protocols. For instance, many modern web browsers and servers now support ECC-based TLS certificates, providing a more efficient and secure method of establishing encrypted connections compared to RSA-based certificates. The smaller key sizes also contribute to faster digital signature generation and verification, crucial for secure server-client interactions and authentication processes.
Homomorphic Encryption and its Potential Uses
Homomorphic encryption allows computations to be performed on encrypted data without first decrypting it. This groundbreaking technique opens possibilities for secure cloud computing, allowing sensitive data to be processed and analyzed remotely without compromising confidentiality. Several types of homomorphic encryption exist, each with varying capabilities. Fully homomorphic encryption (FHE) allows for arbitrary computations on encrypted data, while partially homomorphic encryption (PHE) supports only specific operations.
For example, a partially homomorphic scheme might allow for addition and multiplication operations on encrypted numbers but not more complex operations. The practical applications of homomorphic encryption are still developing, but potential uses in server security include secure data analysis, privacy-preserving machine learning on encrypted datasets, and secure multi-party computation where multiple parties can collaboratively compute a function on their private inputs without revealing their individual data.
Quantum-Resistant Cryptography and Future Server Infrastructure
The advent of quantum computing poses a significant threat to current cryptographic systems, as quantum algorithms can potentially break widely used algorithms like RSA and ECC. Quantum-resistant cryptography (also known as post-quantum cryptography) aims to develop cryptographic algorithms that are resistant to attacks from both classical and quantum computers. Several promising candidates are currently under development and evaluation by standardization bodies like NIST (National Institute of Standards and Technology).
These algorithms are based on various mathematical problems believed to be hard even for quantum computers, such as lattice-based cryptography, code-based cryptography, and multivariate cryptography. The transition to quantum-resistant cryptography is a crucial step in securing future server infrastructure and ensuring long-term data confidentiality. Organizations are already beginning to plan for this transition, evaluating different post-quantum algorithms and considering the implications for their existing systems and security protocols.
A gradual migration strategy, incorporating both existing and quantum-resistant algorithms, is likely to be adopted to minimize disruption and ensure a secure transition.
Server Security Best Practices
Implementing robust server security requires a multi-layered approach encompassing hardware, software, and operational practices. Effective cryptographic techniques are fundamental to this approach, forming the bedrock of secure communication and data protection. This section details essential best practices and their implementation across various server environments.
A holistic server security strategy involves a combination of preventative measures, proactive monitoring, and rapid response capabilities. Failing to address any single aspect weakens the overall security posture, increasing vulnerability to attacks.
Server Hardening and Configuration
Server hardening involves minimizing the attack surface by disabling unnecessary services, applying the principle of least privilege, and regularly updating software. This includes disabling or removing unnecessary ports, accounts, and services. In cloud environments, this might involve configuring appropriate security groups in AWS, Azure, or GCP to restrict inbound and outbound traffic only to essential ports and IP addresses.
On-premise, this involves using firewalls and carefully configuring access control lists (ACLs). Regular patching and updates are crucial to mitigate known vulnerabilities, ensuring the server operates with the latest security fixes. For example, promptly applying patches for known vulnerabilities in the operating system and applications is critical to preventing exploitation.
Secure Key Management
Secure key management is paramount. This involves the secure generation, storage, rotation, and destruction of cryptographic keys. Keys should be generated using strong, cryptographically secure random number generators (CSPRNGs). They should be stored securely, ideally using hardware security modules (HSMs) for enhanced protection against unauthorized access. Regular key rotation minimizes the impact of a compromised key, limiting the window of vulnerability.
Key destruction should follow established procedures to ensure complete and irreversible deletion. Cloud providers offer key management services (KMS) that simplify key management processes, such as AWS KMS, Azure Key Vault, and Google Cloud KMS. On-premise solutions might involve dedicated hardware security modules or robust software-based key management systems.
Regular Security Audits and Vulnerability Scanning
Regular security audits and vulnerability scans are essential for identifying and mitigating potential security weaknesses. Automated vulnerability scanners can identify known vulnerabilities in software and configurations. Penetration testing, simulating real-world attacks, can further assess the server’s resilience. Regular security audits by independent security professionals provide a comprehensive evaluation of the server’s security posture, identifying potential weaknesses that automated scans might miss.
For instance, a recent audit of a financial institution’s servers revealed a misconfiguration in their web application firewall, potentially exposing sensitive customer data. This highlights the critical importance of regular audits, which are often a regulatory requirement. These audits can be conducted on-premise or remotely, depending on the environment. Cloud providers offer various security tools and services that integrate with their platforms, facilitating vulnerability scanning and automated patching.
Data Encryption at Rest and in Transit
Encrypting data both at rest and in transit is crucial for protecting sensitive information. Data encryption at rest protects data stored on the server’s hard drives or in cloud storage. This can be achieved using full-disk encryption (FDE) or file-level encryption. Data encryption in transit protects data while it’s being transmitted over a network. This is typically achieved using TLS/SSL encryption for web traffic and VPNs for remote access.
For example, encrypting databases using strong encryption algorithms like AES-256 protects sensitive data even if the database server is compromised. Similarly, using HTTPS for all web traffic ensures that communication between the server and clients remains confidential. Cloud providers offer various encryption options, often integrated with their storage and networking services. On-premise, this would require careful configuration of encryption protocols and the selection of appropriate encryption algorithms.
Access Control and Authentication
Implementing strong access control measures is critical. This involves using strong passwords or multi-factor authentication (MFA) to restrict access to the server. Principle of least privilege should be applied, granting users only the necessary permissions to perform their tasks. Regularly review and update user permissions to ensure they remain appropriate. Using role-based access control (RBAC) can streamline permission management and improve security.
For instance, an employee should only have access to the data they need for their job, not all server resources. This limits the potential damage from a compromised account. Cloud providers offer robust identity and access management (IAM) services to manage user access. On-premise, this would require careful configuration of user accounts and access control lists.
End of Discussion
Securing your servers effectively requires a multi-layered approach that leverages the power of cryptography. From understanding the nuances of symmetric and asymmetric encryption to implementing robust PKI and TLS configurations, this exploration of Server Security Secrets Revealed: Cryptography Insights provides a solid foundation for building resilient server infrastructure. By staying informed about evolving threats and adopting best practices, you can proactively mitigate risks and protect your valuable data.
Remember that continuous monitoring, regular security audits, and staying updated on the latest cryptographic advancements are crucial for maintaining optimal server security in the ever-changing landscape of cybersecurity.
FAQ Explained
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption.
How often should SSL certificates be renewed?
SSL certificates typically have a validity period of 1 to 2 years. Renew them before they expire to avoid service interruptions.
What is certificate pinning, and why is it important?
Certificate pinning involves hardcoding the expected SSL certificate’s public key into the application. This prevents man-in-the-middle attacks by ensuring that only the trusted certificate is accepted.
What are some examples of quantum-resistant cryptographic algorithms?
Examples include lattice-based cryptography, code-based cryptography, and multivariate cryptography. These algorithms are designed to withstand attacks from quantum computers.