Cryptography: The Server’s Secret Weapon. This phrase encapsulates the critical role cryptography plays in securing our digital world. From protecting sensitive data stored in databases to securing communications between servers and clients, cryptography forms the bedrock of modern server security. This exploration delves into the various encryption techniques, protocols, and key management practices that safeguard servers from cyber threats, offering a comprehensive overview of this essential technology.
We’ll examine symmetric and asymmetric encryption methods, comparing their strengths and weaknesses in practical applications. We’ll dissect secure communication protocols like TLS/SSL, exploring their functionality and potential vulnerabilities. Furthermore, we’ll discuss database security strategies, key management best practices, and the impact of cryptography on network performance. Finally, we’ll look towards the future, considering emerging trends and the challenges posed by advancements in quantum computing.
Introduction to Cryptography in Server Security
Cryptography is the cornerstone of modern server security, providing the essential mechanisms to protect data confidentiality, integrity, and authenticity. Without robust cryptographic techniques, servers would be vulnerable to a wide range of attacks, leading to data breaches, service disruptions, and significant financial losses. This section explores the fundamental role of cryptography in securing servers and details the various algorithms employed.Cryptography’s role in server security encompasses several key areas.
It protects data at rest (data stored on the server’s hard drives) and data in transit (data moving between the server and clients). It also authenticates users and servers, ensuring that only authorized individuals and systems can access sensitive information. By employing encryption, digital signatures, and other cryptographic primitives, servers can effectively mitigate the risks associated with unauthorized access, data modification, and denial-of-service attacks.
Symmetric-key Cryptography
Symmetric-key cryptography uses the same secret key for both encryption and decryption. This approach is generally faster than asymmetric cryptography, making it suitable for encrypting large volumes of data. Examples include the Advanced Encryption Standard (AES), a widely adopted and highly secure block cipher, and the ChaCha20 stream cipher, known for its performance and resistance against timing attacks. AES, for instance, is commonly used to encrypt data at rest on servers, while ChaCha20 might be preferred for encrypting data in transit due to its speed.
The choice of algorithm often depends on specific security requirements and performance considerations.
Asymmetric-key Cryptography
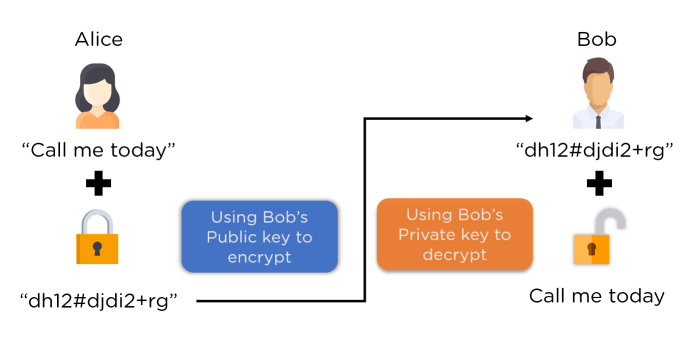
Asymmetric-key cryptography, also known as public-key cryptography, utilizes a pair of keys: a public key for encryption and a private key for decryption. This allows for secure communication without the need to share a secret key beforehand. The most prevalent example is RSA, which is widely used for secure communication protocols like HTTPS and for digital signatures. Elliptic Curve Cryptography (ECC) is another important asymmetric algorithm offering comparable security with smaller key sizes, making it particularly efficient for resource-constrained environments.
RSA is commonly used for secure key exchange and digital signatures in server-client communications, while ECC is increasingly favored for its efficiency in mobile and embedded systems.
Hashing Algorithms
Hashing algorithms produce a fixed-size string (the hash) from an input of any size. These are crucial for data integrity verification and password storage. They are designed to be one-way functions, meaning it’s computationally infeasible to reverse the process and obtain the original input from the hash. Popular examples include SHA-256 and SHA-3, which are used extensively in server security for verifying data integrity and generating message authentication codes (MACs).
For password storage, bcrypt and Argon2 are preferred over older algorithms like MD5 and SHA-1 due to their resistance against brute-force and rainbow table attacks.
Real-World Scenarios
Server-side cryptography is essential in numerous applications. HTTPS, the secure version of HTTP, uses asymmetric cryptography for secure key exchange and symmetric cryptography for encrypting the communication channel between the client’s web browser and the server. This protects sensitive data like credit card information and login credentials during online transactions. Email security protocols like S/MIME utilize digital signatures and encryption to ensure the authenticity and confidentiality of email messages.
Database encryption protects sensitive data stored in databases, safeguarding against unauthorized access even if the server is compromised. Virtual Private Networks (VPNs) rely on cryptography to create secure tunnels for data transmission, ensuring confidentiality and integrity when accessing corporate networks remotely.
Encryption Techniques for Server Data Protection
Server security relies heavily on robust encryption techniques to safeguard sensitive data from unauthorized access. Effective encryption protects data both in transit (while being transmitted over a network) and at rest (while stored on the server). Choosing the right encryption method depends on various factors, including the sensitivity of the data, performance requirements, and the computational resources available. This section will delve into the key encryption methods employed for server data protection.
Symmetric Encryption Methods
Symmetric encryption uses a single secret key to both encrypt and decrypt data. This approach is generally faster than asymmetric encryption, making it suitable for encrypting large volumes of data. However, secure key exchange presents a significant challenge. Popular symmetric encryption algorithms include AES, DES, and 3DES.
| Algorithm | Key Size (bits) | Block Size (bits) | Security Level |
|---|---|---|---|
| AES (Advanced Encryption Standard) | 128, 192, 256 | 128 | High; widely considered secure for most applications |
| DES (Data Encryption Standard) | 56 | 64 | Low; considered insecure due to its small key size and vulnerability to brute-force attacks. |
| 3DES (Triple DES) | 112 or 168 | 64 | Medium; offers improved security over DES but is slower than AES and is gradually being phased out. |
Asymmetric Encryption Methods, Cryptography: The Server’s Secret Weapon
Asymmetric encryption, also known as public-key cryptography, utilizes a pair of keys: a public key for encryption and a private key for decryption. The public key can be widely distributed, while the private key must be kept secret. This eliminates the need for secure key exchange inherent in symmetric encryption. RSA and Elliptic Curve Cryptography (ECC) are prominent examples.RSA Advantages:
- Widely adopted and well-understood.
- Mature technology with extensive research and analysis.
RSA Disadvantages:
- Computationally slower than symmetric encryption, especially for large data sets.
- Key sizes are typically larger than those used in symmetric encryption.
ECC Advantages:
- Provides comparable security to RSA with smaller key sizes, leading to faster encryption and decryption.
- More efficient in terms of computational resources and bandwidth.
ECC Disadvantages:
- Relatively newer compared to RSA, so its long-term security is still under ongoing evaluation.
- Implementation can be more complex than RSA.
Digital Signatures for Data Integrity and Authentication
Digital signatures provide both data integrity and authentication. They use asymmetric cryptography to ensure that data hasn’t been tampered with and to verify the sender’s identity. A digital signature is created by hashing the data and then encrypting the hash with the sender’s private key. The recipient can then verify the signature using the sender’s public key.
If the verification process is successful, it confirms that the data originated from the claimed sender and hasn’t been altered during transmission. This is crucial for server security, ensuring that software updates, configuration files, and other critical data are authentic and unaltered.
Secure Communication Protocols
Securing communication between servers and clients is paramount for maintaining data integrity and confidentiality. This necessitates the use of robust cryptographic protocols that establish secure channels for the transmission of sensitive information. The most widely used protocol for this purpose is Transport Layer Security (TLS), often referred to as its predecessor, Secure Sockets Layer (SSL). This section details the role of TLS/SSL, the process of establishing a secure connection, and potential vulnerabilities along with their mitigation strategies.TLS/SSL ensures secure communication by establishing an encrypted link between a client (e.g., a web browser) and a server (e.g., a web server).
This encryption prevents eavesdropping and tampering with data during transit. The protocol achieves this through a combination of symmetric and asymmetric encryption, digital certificates, and message authentication codes. It’s a critical component of modern internet security, underpinning many online services, from secure web browsing to online banking.
TLS/SSL’s Role in Securing Server-Client Communication
TLS/SSL operates at the transport layer of the network stack, providing confidentiality, integrity, and authentication. Confidentiality is ensured through the encryption of data transmitted between the client and server. Integrity is guaranteed through message authentication codes (MACs), which prevent unauthorized modification of data during transmission. Finally, authentication verifies the identity of the server to the client, preventing man-in-the-middle attacks where an attacker impersonates the legitimate server.
The use of digital certificates, issued by trusted Certificate Authorities (CAs), is crucial for this authentication process. A successful TLS/SSL handshake ensures that only the intended recipient can decrypt and read the exchanged data.
Establishing a Secure TLS/SSL Connection
The establishment of a secure TLS/SSL connection involves a complex handshake process. This process typically follows these steps:
- Client Hello: The client initiates the connection by sending a “Client Hello” message to the server. This message includes the client’s supported TLS versions, cipher suites (encryption algorithms), and a randomly generated number (client random).
- Server Hello: The server responds with a “Server Hello” message, selecting a cipher suite from those offered by the client and providing its own randomly generated number (server random). The server also sends its digital certificate, which contains its public key and other identifying information.
- Certificate Verification: The client verifies the server’s certificate, ensuring that it’s valid, hasn’t been revoked, and is issued by a trusted CA. This step is crucial for authenticating the server.
- Key Exchange: The client and server use a key exchange algorithm (e.g., Diffie-Hellman) to generate a shared secret key. This key is used for symmetric encryption of subsequent communication.
- Change Cipher Spec: Both client and server indicate that they will now use the newly generated shared secret key for encryption.
- Encrypted Communication: All subsequent communication between the client and server is encrypted using the shared secret key.
TLS/SSL Vulnerabilities and Mitigation Strategies
Despite its widespread use, TLS/SSL implementations can be vulnerable to various attacks. One significant vulnerability is the use of weak or outdated cipher suites. Another is the potential for implementation flaws in the server-side software. Heartbleed, for instance, was a critical vulnerability that allowed attackers to extract sensitive information from the server’s memory.To mitigate these vulnerabilities, several strategies can be employed:
- Regular Updates: Keeping server software and TLS libraries up-to-date is crucial to patch known vulnerabilities.
- Strong Cipher Suites: Using strong and modern cipher suites, such as those based on AES-256 with perfect forward secrecy (PFS), enhances security.
- Strict Certificate Validation: Implementing robust certificate validation procedures helps prevent man-in-the-middle attacks.
- Regular Security Audits: Conducting regular security audits and penetration testing helps identify and address potential vulnerabilities before they can be exploited.
- HTTP Strict Transport Security (HSTS): HSTS forces browsers to always use HTTPS, preventing downgrade attacks where a connection is downgraded to HTTP.
Database Security with Cryptography
Protecting sensitive data stored within server databases is paramount for any organization. The consequences of a data breach can be severe, ranging from financial losses and reputational damage to legal repercussions and loss of customer trust. Cryptography offers a robust solution to mitigate these risks by employing various encryption techniques to safeguard data at rest and in transit.Encryption, in the context of database security, transforms readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic key.
Only authorized individuals possessing the correct decryption key can access the original data. This prevents unauthorized access even if the database is compromised. The choice of encryption method and implementation significantly impacts the overall security posture.
Transparent Encryption
Transparent encryption is a method where encryption and decryption happen automatically, without requiring modifications to the application accessing the database. This is often achieved through database-level encryption, where the database management system (DBMS) handles the encryption and decryption processes. The application remains unaware of the encryption layer, simplifying integration and reducing the burden on developers. However, transparent encryption can sometimes introduce performance overhead, and the security relies heavily on the security of the DBMS itself.
For example, a database using transparent encryption might leverage a feature built into its core, like always-on encryption for certain columns, automatically encrypting data as it is written and decrypting it as it is read.
Application-Level Encryption
Application-level encryption, conversely, involves encrypting data within the application logic before it’s stored in the database. This offers greater control over the encryption process and allows for more granular control over which data is encrypted. Developers have more flexibility in choosing encryption algorithms and key management strategies. However, this approach requires more development effort and careful implementation to avoid introducing vulnerabilities.
A common example is encrypting sensitive fields like credit card numbers within the application before storing them in a database column, with the decryption occurring only within the application’s secure environment during authorized access.
Hypothetical Database Security Architecture
A robust database security architecture incorporates multiple layers of protection. Consider a hypothetical e-commerce platform. Sensitive customer data, such as addresses and payment information, is stored in a relational database. The architecture would include:
- Transparent Encryption at the Database Level: All tables containing sensitive data are encrypted using always-on encryption provided by the DBMS. This provides a baseline level of protection.
- Application-Level Encryption for Specific Fields: Credit card numbers are encrypted using a strong, industry-standard algorithm (e.g., AES-256) within the application before storage. This adds an extra layer of security, even if the database itself is compromised.
- Access Control Mechanisms: Role-based access control (RBAC) is implemented, restricting access to sensitive data based on user roles and permissions. Only authorized personnel, such as database administrators and customer service representatives with appropriate permissions, can access this data. This controls who can even
-attempt* to access the data, encrypted or not. - Regular Security Audits and Penetration Testing: Regular security audits and penetration testing are conducted to identify and address potential vulnerabilities. This ensures the system’s security posture remains strong over time.
- Key Management System: A secure key management system is implemented to manage and protect the encryption keys. This system should include secure key generation, storage, rotation, and access control mechanisms. Compromise of the keys would negate the security provided by encryption.
This multi-layered approach provides a comprehensive security strategy, combining the strengths of transparent and application-level encryption with robust access control mechanisms and regular security assessments. The specific implementation details will depend on the sensitivity of the data, the organization’s security requirements, and the capabilities of the chosen DBMS.
Key Management and Security: Cryptography: The Server’s Secret Weapon
Robust key management is paramount for the effectiveness of any cryptographic system. A compromised key renders even the strongest encryption algorithm vulnerable. This section details best practices for generating, storing, and managing cryptographic keys to ensure the continued security of server data and communications.Secure key management involves a multifaceted approach encompassing key generation, storage, rotation, and the utilization of specialized hardware.
Neglecting any of these aspects can significantly weaken the overall security posture.
Key Generation Best Practices
Strong cryptographic keys must be generated using cryptographically secure pseudo-random number generators (CSPRNGs). These generators produce sequences of numbers that are statistically indistinguishable from truly random numbers, a crucial characteristic for preventing predictability and subsequent compromise. Operating systems typically provide CSPRNGs; however, it’s vital to ensure that these are properly seeded and regularly tested for randomness. Avoid using simple algorithms or predictable sources for key generation.
The length of the key should also align with the strength required by the chosen cryptographic algorithm; longer keys generally offer greater resistance against brute-force attacks. For example, a 2048-bit RSA key is generally considered secure for the foreseeable future, while shorter keys are susceptible to advances in computing power.
Secure Key Storage
Storing cryptographic keys securely is as critical as their generation. Keys should never be stored in plain text within configuration files or databases. Instead, they should be encrypted using a separate, well-protected key, often referred to as a key encryption key (KEK). This KEK should be stored separately and protected with strong access controls. Consider using dedicated key management systems that offer features like access control lists (ACLs), auditing capabilities, and robust encryption mechanisms.
Additionally, physical security of servers housing key storage systems is paramount.
Key Rotation and Implementation
Regular key rotation is a crucial security measure to mitigate the impact of potential key compromises. If a key is compromised, the damage is limited to the period it was in use. A well-defined key rotation policy should be implemented, specifying the frequency of key changes (e.g., every 90 days, annually, or based on specific events). Automated key rotation processes should be employed to minimize the risk of human error.
The old key should be securely deleted after the new key is successfully implemented and verified. Careful planning and testing are essential before implementing any key rotation scheme to avoid service disruptions.
Hardware Security Modules (HSMs)
Hardware Security Modules (HSMs) provide a dedicated, physically secure environment for generating, storing, and managing cryptographic keys. These devices offer tamper-resistance and various security features that significantly enhance key protection. HSMs handle cryptographic operations within a trusted execution environment, preventing unauthorized access or manipulation of keys, even if the server itself is compromised. They are commonly used in high-security environments, such as financial institutions and government agencies, where the protection of cryptographic keys is paramount.
The use of HSMs adds a significant layer of security, reducing the risk of key exposure or theft.
Cryptography and Network Security on Servers
Server-side cryptography, while crucial for data protection, operates within a broader network security context. Firewalls, intrusion detection systems (IDS), and other network security mechanisms play vital roles in protecting cryptographic keys and ensuring the integrity of encrypted communications. Understanding the interplay between these elements is critical for building robust and secure server infrastructure.
Firewall and Intrusion Detection System Interaction with Server-Side Cryptography
Firewalls act as the first line of defense, filtering network traffic based on predefined rules. They prevent unauthorized access attempts to the server, thus indirectly protecting cryptographic keys and sensitive data stored on the server. Intrusion detection systems monitor network traffic and server activity for malicious patterns. While IDS doesn’t directly interact with cryptographic algorithms, it can detect suspicious activity, such as unusually high encryption/decryption rates or attempts to exploit known vulnerabilities in cryptographic implementations, triggering alerts that allow for timely intervention.
A well-configured firewall can restrict access to ports used for cryptographic protocols (e.g., HTTPS on port 443), preventing unauthorized attempts to initiate encrypted connections. IDS, in conjunction with log analysis, can help identify potential attacks targeting cryptographic keys or exploiting weaknesses in cryptographic systems. For instance, a sudden surge in failed login attempts, combined with unusual network activity targeting the server’s encryption services, might indicate a brute-force attack against cryptographic keys.
Impact of Cryptography on Network Performance
Implementing cryptography inevitably introduces overhead. Encryption and decryption processes consume CPU cycles and network bandwidth. The performance impact varies depending on the chosen algorithm, key size, and hardware capabilities. Symmetric encryption algorithms, generally faster than asymmetric ones, are suitable for encrypting large volumes of data, but require secure key exchange mechanisms. Asymmetric algorithms, while slower, are essential for key exchange and digital signatures.
Using strong encryption with larger key sizes enhances security but increases processing time. For example, AES-256 is more secure than AES-128 but requires significantly more computational resources. Network performance degradation can be mitigated by optimizing cryptographic implementations, employing hardware acceleration (e.g., specialized cryptographic processors), and carefully selecting appropriate algorithms for specific use cases. Load balancing and efficient caching strategies can also help to minimize the performance impact of cryptography on high-traffic servers.
A real-world example is the use of hardware-accelerated TLS/SSL encryption in web servers to handle high volumes of encrypted traffic without significant performance bottlenecks.
Secure Server-to-Server Communication Using Cryptography: A Step-by-Step Guide
Secure server-to-server communication requires a robust cryptographic framework. The following steps Artikel a common approach:
- Key Exchange: Establish a secure channel for exchanging cryptographic keys. This typically involves using an asymmetric algorithm like RSA or ECC to exchange a symmetric key. The Diffie-Hellman key exchange is a common method for establishing a shared secret key over an insecure channel.
- Symmetric Encryption: Use a strong symmetric encryption algorithm like AES to encrypt data exchanged between the servers. AES-256 is currently considered a highly secure option.
- Message Authentication Code (MAC): Generate a MAC using a cryptographic hash function (e.g., HMAC-SHA256) to ensure data integrity and authenticity. This verifies that the data hasn’t been tampered with during transmission.
- Digital Signatures (Optional): For non-repudiation and stronger authentication, digital signatures using asymmetric cryptography can be employed. This allows verification of the sender’s identity and ensures the message hasn’t been altered.
- Secure Transport Layer: Implement a secure transport layer protocol like TLS/SSL to encapsulate the encrypted data and provide secure communication over the network. TLS/SSL handles key exchange, encryption, and authentication, simplifying the implementation of secure server-to-server communication.
- Regular Key Rotation: Implement a key rotation policy to periodically change cryptographic keys. This minimizes the impact of potential key compromises.
Implementing these steps ensures that data exchanged between servers remains confidential, authentic, and tamper-proof. Failure to follow these steps can lead to vulnerabilities and potential data breaches. For instance, using weak encryption algorithms or failing to implement proper key management practices can leave the communication channel susceptible to eavesdropping or data manipulation.
Addressing Cryptographic Vulnerabilities
Cryptographic implementations, while crucial for server security, are susceptible to various vulnerabilities that can compromise sensitive data. These vulnerabilities often stem from flawed algorithm choices, improper key management, or insecure implementation practices. Understanding these weaknesses and implementing robust mitigation strategies is paramount for maintaining the integrity and confidentiality of server resources.
Weaknesses in cryptographic systems can lead to devastating consequences, ranging from data breaches and financial losses to reputational damage and legal repercussions. A comprehensive understanding of these vulnerabilities and their exploitation methods is therefore essential for building secure and resilient server infrastructures.
Common Cryptographic Vulnerabilities
Several common vulnerabilities plague cryptographic implementations. These include the use of outdated or weak algorithms, inadequate key management practices, improper implementation of cryptographic protocols, and side-channel attacks. Addressing these issues requires a multi-faceted approach encompassing algorithm selection, key management practices, secure coding, and regular security audits.
Examples of Exploitable Weaknesses
One example is the use of the Data Encryption Standard (DES), now considered obsolete due to its relatively short key length, making it vulnerable to brute-force attacks. Another example is the exploitation of vulnerabilities in the implementation of cryptographic libraries, such as buffer overflows or insecure random number generators. These flaws can lead to attacks like padding oracle attacks, which allow attackers to decrypt ciphertext without knowing the decryption key.
Poor key management, such as the reuse of keys across multiple systems or insufficient key rotation, also significantly increases the risk of compromise. Furthermore, side-channel attacks, which exploit information leaked through power consumption or timing variations, can reveal sensitive cryptographic information.
Methods for Detecting and Mitigating Vulnerabilities
Detecting cryptographic vulnerabilities requires a combination of automated tools and manual code reviews. Static and dynamic code analysis tools can identify potential weaknesses in cryptographic implementations. Penetration testing, simulating real-world attacks, helps identify exploitable vulnerabilities. Regular security audits and vulnerability scanning are crucial for proactively identifying and addressing potential weaknesses. Mitigation strategies involve using strong, up-to-date cryptographic algorithms, implementing robust key management practices, employing secure coding techniques, and regularly patching vulnerabilities.
The use of hardware security modules (HSMs) can further enhance security by protecting cryptographic keys and operations from unauthorized access. Finally, rigorous testing and validation of cryptographic implementations are essential to ensure their effectiveness and resilience against attacks.
The Future of Cryptography in Server Security
The landscape of server security is constantly evolving, driven by advancements in computing power and the persistent threat of cyberattacks. Cryptography, the cornerstone of secure server operations, is no exception. Emerging trends and technological leaps promise to reshape how we protect sensitive data, demanding a proactive approach to anticipating and adapting to these changes. The future of server security hinges on the continuous evolution and implementation of robust cryptographic techniques.
The increasing sophistication of cyber threats necessitates a proactive approach to server security. Traditional cryptographic methods, while effective, face potential vulnerabilities in the face of emerging technologies, particularly quantum computing. Therefore, a forward-looking strategy must encompass the adoption of cutting-edge cryptographic techniques and a robust approach to risk management. This involves not only updating existing systems but also anticipating and preparing for future challenges.
Post-Quantum Cryptography
Post-quantum cryptography (PQC) represents a crucial area of development in server security. Current widely-used encryption algorithms, such as RSA and ECC, are vulnerable to attacks from sufficiently powerful quantum computers. PQC algorithms are designed to resist attacks from both classical and quantum computers. The National Institute of Standards and Technology (NIST) has been leading the effort to standardize PQC algorithms, and several candidates are currently undergoing evaluation.
Adoption of these standards will be a critical step in ensuring long-term server security in a post-quantum world. For example, the transition to PQC will involve replacing existing cryptographic libraries and updating protocols, a process requiring careful planning and implementation to minimize disruption and ensure seamless integration.
Predictions for the Future of Server Security
The future of server security will likely see a greater emphasis on hybrid cryptographic approaches, combining different algorithms to create layered security. This will enhance resilience against a wider range of attacks, including those leveraging both classical and quantum computing power. We can also anticipate an increase in the use of homomorphic encryption, which allows computations to be performed on encrypted data without decryption, enabling secure data processing in cloud environments.
Furthermore, advancements in machine learning and artificial intelligence will play a larger role in threat detection and response, enhancing the overall security posture of servers. For instance, AI-powered systems can analyze network traffic patterns to identify anomalies indicative of malicious activity, triggering automated responses to mitigate threats in real-time.
The Impact of Quantum Computing on Current Cryptographic Methods
Advancements in quantum computing pose a significant threat to current cryptographic methods. Quantum computers, with their ability to perform certain computations exponentially faster than classical computers, can break widely used public-key cryptosystems like RSA and ECC. This means that data encrypted using these algorithms could be vulnerable to decryption by sufficiently powerful quantum computers. The timeline for when this threat will become a reality is uncertain, but the potential impact is significant, making the transition to post-quantum cryptography a matter of urgency for organizations handling sensitive data.
Consider, for example, the implications for financial transactions, healthcare records, and national security data, all of which rely heavily on robust encryption. The potential for widespread data breaches necessitates a proactive approach to mitigating this risk.
Cryptography: The Server’s Secret Weapon, is paramount for data protection. Understanding robust encryption methods is crucial, and to delve deeper into practical applications, check out this excellent guide on Crypto Strategies for Unbeatable Server Security. Ultimately, mastering cryptography ensures your server remains a secure fortress against cyber threats, safeguarding sensitive information effectively.
Final Thoughts
In conclusion, cryptography is not merely a technical detail but the very lifeblood of secure server operations. Understanding its intricacies—from choosing the right encryption algorithms to implementing robust key management strategies—is paramount for safeguarding sensitive data and maintaining the integrity of online systems. By proactively addressing vulnerabilities and staying informed about emerging threats, organizations can leverage the power of cryptography to build resilient and secure server infrastructures for the future.
Detailed FAQs
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys—a public key for encryption and a private key for decryption.
How does a Hardware Security Module (HSM) enhance key protection?
HSMs are physical devices that securely store and manage cryptographic keys, offering enhanced protection against theft or unauthorized access compared to software-based solutions.
What are some common vulnerabilities in cryptographic implementations?
Common vulnerabilities include weak key generation, improper key management, vulnerabilities in cryptographic algorithms themselves, and insecure implementation of protocols.
What is post-quantum cryptography?
Post-quantum cryptography refers to cryptographic algorithms that are designed to be resistant to attacks from both classical and quantum computers.