The Art of Server Cryptography: Protecting Your Assets isn’t just about complex algorithms; it’s about safeguarding the very heart of your digital world. This journey delves into the crucial techniques and strategies needed to secure your server infrastructure from increasingly sophisticated cyber threats. We’ll explore everything from fundamental encryption concepts to advanced key management practices, equipping you with the knowledge to build a robust and resilient security posture.
Understanding server-side cryptography is paramount in today’s interconnected landscape. Data breaches can cripple businesses, leading to financial losses, reputational damage, and legal repercussions. This guide provides a practical, step-by-step approach to securing your servers, covering encryption methods, authentication protocols, secure coding practices, and incident response strategies. By the end, you’ll have a clear understanding of how to protect your valuable assets from malicious actors and ensure the integrity of your data.
Introduction to Server Cryptography
Server-side cryptography is the practice of using cryptographic techniques to protect data and resources stored on and transmitted to and from servers. It’s a critical component of securing any online system, ensuring confidentiality, integrity, and authenticity of information. Without robust server-side cryptography, sensitive data is vulnerable to a wide range of attacks, potentially leading to significant financial losses, reputational damage, and legal repercussions.The importance of securing server assets cannot be overstated.
Mastering the art of server cryptography is crucial for safeguarding your valuable digital assets. This involves implementing robust security measures, and understanding the nuances of encryption protocols is paramount. To delve deeper into advanced techniques, explore this comprehensive guide on Secure Your Server with Advanced Cryptographic Techniques for a stronger defense. Ultimately, effective server cryptography ensures the confidentiality and integrity of your data, protecting your business from potential breaches.
Servers often hold sensitive information such as user credentials, financial data, intellectual property, and customer details. A compromise of these assets can have far-reaching consequences, impacting not only the organization itself but also its customers and partners. Protecting server assets requires a multi-layered approach, with server-side cryptography forming a crucial cornerstone of this defense.
Types of Server-Side Attacks
Server-side attacks exploit vulnerabilities in servers and their applications to gain unauthorized access to data or resources. These attacks can range from simple attempts to guess passwords to sophisticated exploits leveraging zero-day vulnerabilities. Examples include SQL injection, where malicious code is injected into database queries to manipulate or extract data; cross-site scripting (XSS), which allows attackers to inject client-side scripts into web pages viewed by other users; and man-in-the-middle (MitM) attacks, where attackers intercept communication between a client and a server to eavesdrop or manipulate the data.
Denial-of-service (DoS) attacks flood servers with traffic, rendering them unavailable to legitimate users. Furthermore, sophisticated attacks may leverage vulnerabilities in server-side software or misconfigurations to gain unauthorized access and control.
Symmetric and Asymmetric Encryption Algorithms
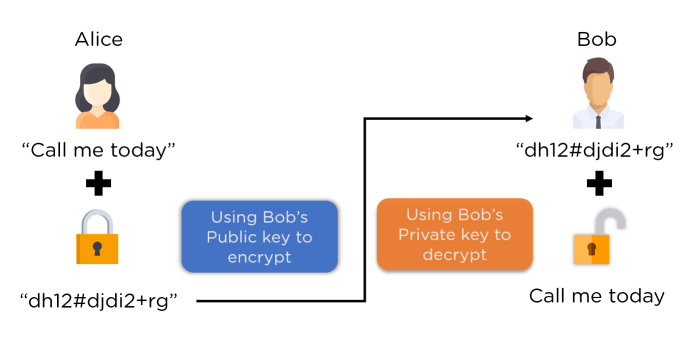
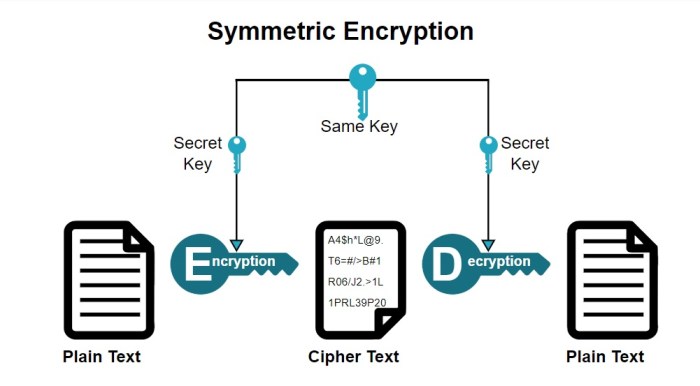
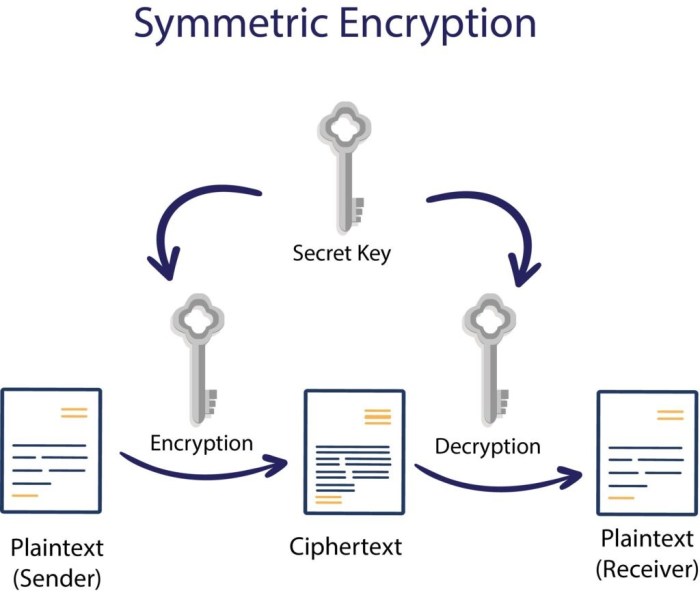
Symmetric and asymmetric encryption are fundamental concepts in cryptography. The choice between them depends on the specific security requirements and the context of their application. Understanding their differences is essential for effective server-side security implementation.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Management | Uses a single secret key for both encryption and decryption. Key exchange is a critical challenge. | Uses a pair of keys: a public key for encryption and a private key for decryption. Key exchange is simpler. |
| Speed | Generally faster than asymmetric encryption. | Significantly slower than symmetric encryption. |
| Key Size | Typically uses smaller key sizes (e.g., AES-256 uses a 256-bit key). | Typically uses larger key sizes (e.g., RSA-2048 uses a 2048-bit key). |
| Use Cases | Data encryption at rest and in transit (e.g., encrypting database backups, securing HTTPS connections using TLS). | Digital signatures, key exchange, secure communication in scenarios where key exchange is challenging (e.g., establishing a secure TLS connection using Diffie-Hellman). |
Encryption Techniques for Server Data
Securing server data is paramount in today’s digital landscape. Effective encryption techniques are crucial for protecting sensitive information from unauthorized access and breaches. This section details various encryption methods and best practices for their implementation, focusing on TLS/SSL and HTTPS, and offering guidance on algorithm selection.
TLS/SSL for Secure Communication
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols that provide secure communication over a network. They establish an encrypted link between a client (like a web browser) and a server, ensuring that data exchanged between them remains confidential and protected from eavesdropping. This is achieved through a process involving a handshake where the client and server authenticate each other and agree upon a cipher suite, defining the encryption algorithms and hashing functions to be used.
The chosen cipher suite determines the level of security and performance of the connection. Weak cipher suites can be vulnerable to attacks, highlighting the importance of regularly updating and choosing strong, modern cipher suites.
HTTPS Implementation for Web Servers
HTTPS (Hypertext Transfer Protocol Secure) is the secure version of HTTP, leveraging TLS/SSL to encrypt communication between web browsers and web servers. Implementing HTTPS involves obtaining an SSL/TLS certificate from a trusted Certificate Authority (CA). This certificate digitally binds the server’s identity to its public key, allowing clients to verify the server’s authenticity and ensuring that they are communicating with the intended server and not an imposter.
The certificate is then configured on the web server, enabling it to handle HTTPS requests. Proper configuration is vital; misconfigurations can lead to vulnerabilities, undermining the security provided by HTTPS. Regular updates to the server software and certificates are crucial for maintaining a strong security posture.
Choosing Appropriate Encryption Algorithms
Selecting the right encryption algorithm is crucial for effective data protection. Factors to consider include the security strength of the algorithm, its performance characteristics, and its compatibility with the server’s hardware and software. Symmetric encryption algorithms, like AES (Advanced Encryption Standard), are generally faster but require secure key exchange. Asymmetric encryption algorithms, such as RSA (Rivest-Shamir-Adleman), are slower but offer features like digital signatures and key exchange.
Hybrid approaches, combining symmetric and asymmetric encryption, are often employed to leverage the strengths of both. Staying informed about the latest cryptographic research and algorithm recommendations from reputable organizations like NIST (National Institute of Standards and Technology) is essential for making informed decisions.
Hypothetical Encryption Scenario: Success and Failure
Consider a scenario where a bank’s server uses AES-256 encryption with a robust key management system to protect customer data. In a successful scenario, a customer’s transaction data is encrypted before being stored on the server. Only the server, possessing the correct decryption key, can access and decrypt this data. Any attempt to intercept the data during transmission or access it from the server without the key will result in an unreadable ciphertext.
In contrast, a failure scenario could involve a weak encryption algorithm (like DES), a compromised key, or a flawed implementation. This could allow a malicious actor to decrypt the data, potentially leading to a data breach with severe consequences, exposing sensitive customer information like account numbers and transaction details. This underscores the importance of utilizing strong encryption and secure key management practices.
Key Management and Security: The Art Of Server Cryptography: Protecting Your Assets
Robust key management is paramount for the effectiveness of server cryptography. Without secure key handling, even the strongest encryption algorithms are vulnerable. Compromised keys render encrypted data readily accessible to attackers, negating the security measures put in place. This section details best practices for generating, storing, and managing cryptographic keys to ensure the ongoing confidentiality, integrity, and availability of your server’s data.
Key Generation Methods
Secure key generation is the foundation of strong cryptography. Weakly generated keys are easily cracked, rendering the encryption useless. Keys should be generated using cryptographically secure pseudo-random number generators (CSPRNGs) that produce unpredictable and statistically random outputs. These generators leverage sources of entropy, such as system noise and hardware-specific random number generators, to avoid predictable patterns in the key material.
Algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) require keys of specific lengths (e.g., 256-bit AES keys, 2048-bit RSA keys) to provide adequate security against current computational power. The key length directly impacts the computational complexity required to break the encryption. Improperly generated keys can be significantly weaker than intended, leading to vulnerabilities.
Key Storage and Protection
Once generated, keys must be stored securely to prevent unauthorized access. Storing keys directly in server files is highly discouraged due to the risk of exposure through malware, operating system vulnerabilities, or unauthorized access to the server. Instead, specialized methods are needed. These include hardware security modules (HSMs), which offer a physically secure environment for key storage and management, or encrypted key vaults managed by dedicated key management systems (KMS).
These systems typically utilize robust encryption techniques and access controls to restrict key access to authorized personnel and processes. The selection of the storage method depends on the sensitivity of the data and the security requirements of the application. A well-designed system will include version control and audit trails to track key usage and changes.
Key Rotation Practices
Regular key rotation is a crucial security practice. Even with secure storage, keys can be compromised over time through unforeseen vulnerabilities or insider threats. Rotating keys periodically minimizes the potential impact of a compromised key, limiting the timeframe during which sensitive data remains vulnerable. A robust key rotation schedule should be established, based on risk assessment and industry best practices.
The frequency of rotation may vary depending on the sensitivity of the data and the threat landscape, ranging from daily to annually. Automated key rotation mechanisms are recommended to streamline the process and minimize human error. During rotation, the old key should be securely destroyed, ensuring it cannot be recovered.
Hardware Security Modules (HSMs) vs. Software-Based Key Management
Hardware security modules (HSMs) provide a dedicated, tamper-resistant hardware device for key generation, storage, and cryptographic operations. They offer significantly enhanced security compared to software-based solutions, as keys are protected even if the host system is compromised. HSMs often include features like secure boot, tamper detection, and physical security measures to prevent unauthorized access. However, HSMs are typically more expensive and complex to implement than software-based key management systems.
Software-based solutions rely on software libraries and encryption techniques to manage keys, offering greater flexibility and potentially lower costs. However, they are more susceptible to software vulnerabilities and require robust security measures to protect the system from attacks. The choice between HSMs and software-based solutions depends on the security requirements, budget, and technical expertise available.
Implementing a Secure Key Management System: A Step-by-Step Guide
Implementing a secure key management system involves several key steps. First, a thorough risk assessment must be conducted to identify potential threats and vulnerabilities. This assessment informs the design and implementation of the key management system, ensuring that it adequately addresses the specific risks faced. Second, a suitable key management solution must be selected, considering factors such as scalability, security features, and integration with existing systems.
This might involve selecting an HSM, a cloud-based KMS, or a custom-built system. Third, clear key generation, storage, and rotation policies must be established and documented. These policies should Artikel the procedures for generating, storing, and rotating keys, including the frequency of rotation and the methods used for secure key destruction. Fourth, access controls must be implemented to restrict access to keys based on the principle of least privilege.
Only authorized personnel and processes should have access to keys. Finally, regular audits and security assessments are essential to ensure the ongoing security and effectiveness of the key management system. These audits help identify weaknesses and potential vulnerabilities, allowing for proactive mitigation measures.
Protecting Data at Rest and in Transit
Data security is paramount in server environments. Protecting data both while it’s stored (at rest) and while it’s being transmitted (in transit) requires a multi-layered approach encompassing robust encryption techniques and secure infrastructure. Failure to adequately protect data can lead to significant financial losses, reputational damage, and legal repercussions.Data encryption is the cornerstone of this protection. It transforms readable data (plaintext) into an unreadable format (ciphertext) using cryptographic algorithms and keys.
Only those possessing the correct decryption key can restore the data to its original form. The choice of encryption algorithm and key management practices are crucial for effective data protection.
Disk Encryption
Disk encryption protects all data stored on a server’s hard drive or solid-state drive (SSD). Full-disk encryption (FDE) solutions encrypt the entire disk, rendering the data inaccessible without the decryption key. This is particularly important for servers containing sensitive information, as even unauthorized physical access to the server won’t compromise the data. Examples of FDE solutions include BitLocker (Windows) and FileVault (macOS).
These systems typically use AES (Advanced Encryption Standard) with a strong key length, such as 256-bit. The key is often stored securely within the hardware or through a Trusted Platform Module (TPM). Proper key management is vital; loss of the key renders the data unrecoverable.
File-Level Encryption
File-level encryption focuses on securing individual files or folders. This approach is suitable when only specific data requires strong protection, or when granular control over access is needed. It allows for selective encryption, meaning that only sensitive files are protected, while less sensitive data remains unencrypted. Software solutions and file encryption tools offer various algorithms and key management options.
Examples include VeraCrypt and 7-Zip with AES encryption. This method provides flexibility but requires careful management of individual encryption keys for each file or folder.
Securing Data in Transit
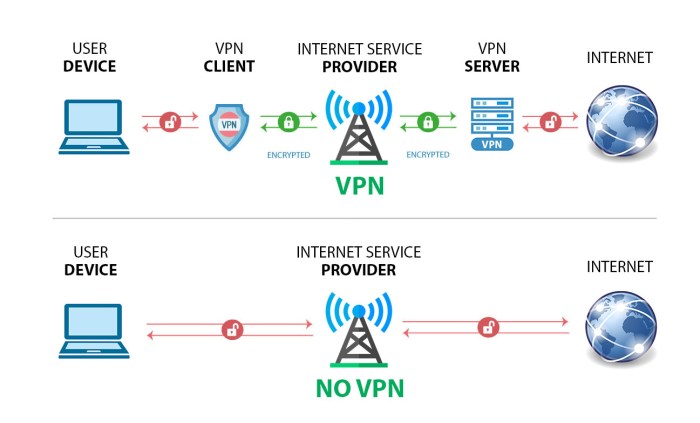
Securing data during transmission, whether between servers or between a server and a client, is equally critical. This primarily involves using Transport Layer Security (TLS) or Secure Sockets Layer (SSL) protocols. These protocols establish an encrypted connection between communicating parties, preventing eavesdropping and tampering with data in transit. HTTPS, a secure version of HTTP, utilizes TLS to protect web traffic.
Virtual Private Networks (VPNs) create secure tunnels for data transmission across untrusted networks, like public Wi-Fi, further enhancing security. Implementation involves configuring servers to use appropriate TLS/SSL certificates and protocols, ensuring strong cipher suites are utilized, and regularly updating the software to address known vulnerabilities.
Security Measures for Different Data Types
The importance of tailored security measures based on the sensitivity of data cannot be overstated. Different data types necessitate different levels of protection.
The following Artikels security measures for various data types:
- Databases: Database encryption, both at rest (using database-level encryption features or disk encryption) and in transit (using TLS/SSL for database connections), is essential. Access control mechanisms, such as user roles and permissions, are crucial for limiting access to authorized personnel. Regular database backups and vulnerability scanning are also important.
- Configuration Files: Configuration files containing sensitive information (e.g., API keys, database credentials) should be encrypted using strong encryption algorithms. Access to these files should be strictly controlled, and they should be stored securely, ideally outside the main application directory.
- Log Files: Log files can contain sensitive data. Encrypting log files at rest is advisable, especially if they contain personally identifiable information (PII). Regular log rotation and secure storage are also important considerations.
- Application Code: Protecting source code is crucial to prevent intellectual property theft and maintain the integrity of the application. Code signing and secure repositories can help.
Authentication and Authorization Mechanisms
Robust authentication and authorization are cornerstones of server security, preventing unauthorized access and protecting sensitive data. These mechanisms work in tandem: authentication verifies the identity of a user or system, while authorization determines what actions that verified entity is permitted to perform. A failure in either can compromise the entire server’s security posture.
Authentication Methods
Authentication confirms the identity of a user or system attempting to access a server. Several methods exist, each with varying levels of security and complexity. The choice depends on the sensitivity of the data and the risk tolerance of the organization.
- Passwords: Passwords, while a common method, are vulnerable to brute-force attacks and phishing. Strong password policies, including length requirements, complexity rules, and regular changes, are crucial to mitigate these risks. However, even with strong policies, passwords remain a relatively weak form of authentication on their own.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification. Common examples include combining a password with a one-time code from an authenticator app (like Google Authenticator or Authy) or a security token, or biometric authentication such as fingerprint or facial recognition. MFA significantly reduces the likelihood of unauthorized access, even if a password is compromised.
- Certificates: Digital certificates, issued by trusted Certificate Authorities (CAs), provide strong authentication by binding a public key to an identity. This is commonly used for secure communication (TLS/SSL) and for authenticating servers and clients within a network. The use of certificates relies on a robust Public Key Infrastructure (PKI) for trust and management.
Authorization Mechanisms and Access Control Lists (ACLs)
Authorization determines what resources a successfully authenticated user or system can access and what actions they are permitted to perform. Access Control Lists (ACLs) are a common method for implementing authorization. ACLs define permissions for specific users or groups on individual resources, such as files, directories, or database tables. A well-designed ACL ensures that only authorized entities can access and manipulate sensitive data.
For example, a database administrator might have full access to a database, while a regular user might only have read-only access to specific tables. Granular control through ACLs is crucial for maintaining data integrity and confidentiality.
System Architecture for Strong Authentication and Authorization
A robust system architecture integrates strong authentication and authorization mechanisms throughout the application and infrastructure. This typically involves:
- Centralized Authentication Service: A central authentication service, such as a Lightweight Directory Access Protocol (LDAP) server or an identity provider (IdP) like Okta or Azure Active Directory, manages user identities and credentials. This simplifies user management and ensures consistency across different systems.
- Role-Based Access Control (RBAC): RBAC assigns permissions based on roles, rather than individual users. This simplifies administration and allows for easy management of user permissions as roles change. For example, a “database administrator” role might be assigned full database access, while a “data analyst” role might have read-only access.
- Regular Security Audits and Monitoring: Regular audits and monitoring are essential to detect and respond to security breaches. This includes reviewing logs for suspicious activity, regularly updating ACLs, and conducting penetration testing to identify vulnerabilities.
Secure Coding Practices for Servers
Secure coding practices are paramount in server-side development, forming the first line of defense against a wide range of attacks. Neglecting these practices can expose sensitive data, compromise system integrity, and lead to significant financial and reputational damage. This section details common vulnerabilities and Artikels best practices for building robust and secure server applications.
Common Server-Side Vulnerabilities
Server-side code is susceptible to various vulnerabilities, many stemming from insecure programming practices. Understanding these weaknesses is crucial for effective mitigation. SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and insecure direct object references (IDOR) are among the most prevalent threats. These vulnerabilities often exploit weaknesses in input validation, output encoding, and session management.
Best Practices for Secure Code
Implementing secure coding practices requires a multi-faceted approach. This includes using a secure development lifecycle (SDLC) that incorporates security considerations at every stage, from design and development to testing and deployment. Employing a layered security model, incorporating both preventative and detective controls, significantly strengthens the overall security posture. Regular security audits and penetration testing are also essential to identify and address vulnerabilities before they can be exploited.
Secure Coding Techniques for Handling Sensitive Data
Protecting sensitive data necessitates robust encryption, both in transit and at rest. This involves using strong encryption algorithms like AES-256 and implementing secure key management practices. Data should be encrypted before being stored in databases or other persistent storage mechanisms. Furthermore, access control mechanisms should be implemented to restrict access to sensitive data based on the principle of least privilege.
Data minimization, limiting the collection and retention of sensitive data to only what is strictly necessary, is also a crucial security measure. Examples include encrypting payment information before storage and using strong password hashing algorithms to protect user credentials.
Input Validation and Output Encoding
Input validation is a critical step in preventing many common vulnerabilities. All user inputs should be rigorously validated to ensure they conform to expected formats and data types. This prevents malicious inputs from being injected into the application, such as SQL injection attacks. Output encoding ensures that data displayed to the user is properly sanitized to prevent cross-site scripting (XSS) attacks.
For example, HTML special characters should be escaped before being displayed on a web page. A robust input validation system would check for the correct data type, length, and format of input fields, rejecting any input that doesn’t conform to the predefined rules. Similarly, output encoding should consistently sanitize all user-provided data before displaying it, escaping special characters and preventing malicious code injection.
For example, a user’s name should be properly encoded before displaying it in an HTML context.
Regular Security Audits and Penetration Testing
Regular security assessments are crucial for maintaining the confidentiality, integrity, and availability of server data. Proactive identification and remediation of vulnerabilities significantly reduce the risk of data breaches, system compromises, and financial losses. A robust security posture relies on consistent monitoring and improvement, not just initial setup.
The Importance of Regular Security Assessments
Regular security assessments, encompassing vulnerability scans, penetration testing, and security audits, provide a comprehensive overview of a server’s security status. These assessments identify weaknesses in the system’s defenses, allowing for timely patching and mitigation of potential threats. The frequency of these assessments should be determined by factors such as the criticality of the server, the sensitivity of the data it handles, and the regulatory compliance requirements.
For example, a server hosting sensitive customer data might require monthly penetration testing, while a less critical server might only need quarterly assessments. The goal is to establish a continuous improvement cycle that proactively addresses emerging threats and vulnerabilities.
Penetration Testing Process for Servers
Penetration testing simulates real-world attacks to identify exploitable vulnerabilities in a server’s security infrastructure. The process typically involves several phases: planning, reconnaissance, vulnerability analysis, exploitation, reporting, and remediation. During the planning phase, the scope of the test is defined, including the target systems, the types of attacks to be simulated, and the acceptable level of risk. Reconnaissance involves gathering information about the target server, including its network configuration, operating system, and installed software.
Vulnerability analysis identifies potential weaknesses in the server’s security, while exploitation involves attempting to exploit those weaknesses to gain unauthorized access. Finally, a comprehensive report detailing the identified vulnerabilities and recommendations for remediation is provided. Post-remediation testing is then performed to validate the effectiveness of the implemented fixes.
Vulnerability Scanners and Security Analysis Tools
Various vulnerability scanners and security analysis tools are available to automate the detection of security weaknesses. These tools can scan servers for known vulnerabilities, misconfigurations, and outdated software. Examples include Nessus, OpenVAS, and QualysGuard. These tools often utilize databases of known vulnerabilities (like the Common Vulnerabilities and Exposures database, CVE) to compare against the server’s configuration and software versions.
Security Information and Event Management (SIEM) systems further enhance this process by collecting and analyzing security logs from various sources, providing real-time monitoring and threat detection capabilities. Automated tools significantly reduce the time and resources required for manual security assessments, allowing for more frequent and thorough analysis.
Comprehensive Server Security Audit Plan
A comprehensive server security audit should be a structured process with clearly defined timelines and deliverables.
| Phase | Activities | Timeline | Deliverables |
|---|---|---|---|
| Planning | Define scope, objectives, and methodology; identify stakeholders and resources. | 1 week | Audit plan document |
| Assessment | Conduct vulnerability scans, penetration testing, and review of security configurations and policies. | 2-4 weeks | Vulnerability report, penetration test report, security configuration review report |
| Reporting | Consolidate findings, prioritize vulnerabilities, and provide recommendations for remediation. | 1 week | Comprehensive security audit report |
| Remediation | Implement recommended security fixes and updates. | 2-4 weeks (variable) | Remediation plan, updated security configurations |
| Validation | Verify the effectiveness of remediation efforts through retesting and validation. | 1 week | Validation report |
This plan provides a framework; the specific timelines will vary depending on the complexity of the server infrastructure and the resources available. For example, a large enterprise environment might require a longer timeline compared to a small business. The deliverables ensure transparency and accountability throughout the audit process.
Responding to Security Incidents
Effective incident response is crucial for minimizing the damage caused by a security breach and maintaining the integrity of server systems. A well-defined plan, coupled with regular training and drills, is essential for a swift and efficient response. This section details the steps involved in responding to security incidents, encompassing containment, eradication, recovery, and post-incident analysis.
Incident Response Plan Stages
A robust incident response plan typically follows a structured methodology. This involves clearly defined stages, each with specific tasks and responsibilities. A common framework involves Preparation, Identification, Containment, Eradication, Recovery, and Post-Incident Activity. Each stage is crucial for minimizing damage and ensuring a smooth return to normal operations. Failure to properly execute any stage can significantly prolong the recovery process and increase the potential for long-term damage.
Containment Procedures
Containing a security breach involves isolating the affected systems to prevent further compromise. This might involve disconnecting affected servers from the network, disabling affected accounts, or implementing firewall rules to restrict access. The goal is to limit the attacker’s ability to move laterally within the network and access sensitive data. For example, if a malware infection is suspected, disconnecting the infected machine from the network is the immediate priority.
This prevents the malware from spreading to other systems and potentially encrypting more data.
Eradication Techniques
Once the affected systems are contained, the next step is to eradicate the threat. This might involve removing malware, patching vulnerabilities, resetting compromised accounts, or reinstalling operating systems. The specific techniques used will depend on the nature of the security breach. For instance, if a server is compromised by a rootkit, a complete system reinstallation might be necessary to ensure complete eradication.
Thorough logging and monitoring are crucial during this phase to ensure that the threat is fully removed and not lurking in a hidden location.
Recovery Procedures
Recovery involves restoring systems and data to a functional state. This might involve restoring data from backups, reinstalling software, and reconfiguring network settings. A well-defined backup and recovery strategy is essential for a successful recovery. For example, a company that uses regular, incremental backups can restore its systems and data much faster than a company that only performs infrequent full backups.
The recovery process should be meticulously documented to aid future incident response efforts.
Post-Incident Activity
After the incident is resolved, a post-incident activity review is critical. This involves analyzing the incident to identify root causes, vulnerabilities, and weaknesses in the security posture. This analysis informs improvements to security controls, policies, and procedures to prevent similar incidents in the future. For instance, if the breach was caused by a known vulnerability, the organization should implement a patch management system to ensure that systems are updated promptly.
This analysis also serves to improve the incident response plan itself, making it more efficient and effective for future events.
Example Incident Response Plan: Ransomware Attack
- Preparation: Regular backups, security awareness training, incident response team established.
- Identification: Detection of unusual system behavior, ransomware notification.
- Containment: Immediate network segmentation, isolation of affected systems.
- Eradication: Malware removal, system restore from backups.
- Recovery: Data restoration, system reconfiguration, application reinstatement.
- Post-Incident Activity: Vulnerability assessment, security policy review, employee training.
Example Incident Response Plan: Data Breach
- Preparation: Data loss prevention (DLP) tools, regular security audits, incident response plan.
- Identification: Detection of unauthorized access attempts, suspicious network activity.
- Containment: Blocking malicious IP addresses, disabling compromised accounts.
- Eradication: Removal of malware, patching vulnerabilities.
- Recovery: Data recovery, system reconfiguration, notification of affected parties.
- Post-Incident Activity: Forensic investigation, legal counsel, security policy review.
Incident Response Process Flowchart
[Imagine a flowchart here. The flowchart would visually represent the stages described above: Preparation -> Identification -> Containment -> Eradication -> Recovery -> Post-Incident Activity. Each stage would be a box, with arrows connecting them to show the sequential nature of the process. Decision points, such as whether containment is successful, could be represented with diamonds. The flowchart would provide a clear, visual representation of the incident response process.]
Future Trends in Server Cryptography
The landscape of server-side security is constantly evolving, driven by advancements in computing power, the increasing sophistication of cyber threats, and the emergence of new technologies. Understanding these trends and adapting security practices accordingly is crucial for maintaining the integrity and confidentiality of sensitive data. This section explores some key future trends in server cryptography, focusing on emerging technologies and their potential impact.
The Impact of Quantum Computing on Cryptography, The Art of Server Cryptography: Protecting Your Assets
Quantum computing poses a significant threat to currently used public-key cryptographic algorithms, such as RSA and ECC. Quantum computers, with their ability to perform computations exponentially faster than classical computers, could potentially break these algorithms, rendering them insecure and jeopardizing the confidentiality and integrity of data protected by them. This necessitates a transition to post-quantum cryptography (PQC), which involves developing cryptographic algorithms resistant to attacks from both classical and quantum computers.
The National Institute of Standards and Technology (NIST) is leading the effort to standardize PQC algorithms, with several candidates currently under consideration. The adoption of these algorithms will be a gradual process, requiring significant infrastructure changes and widespread industry collaboration. For example, the transition to PQC will involve updating software, hardware, and protocols across various systems, potentially impacting legacy systems and requiring considerable investment in new technologies and training.
A successful transition requires careful planning and phased implementation to minimize disruption and ensure a smooth migration to quantum-resistant cryptography.
Emerging Technologies in Server-Side Security
Several emerging technologies are poised to significantly impact server-side security. Homomorphic encryption, for instance, allows computations to be performed on encrypted data without decryption, providing a powerful tool for secure cloud computing and data analytics. This technique could revolutionize how sensitive data is processed and shared, enabling collaborative projects without compromising confidentiality. Furthermore, advancements in secure multi-party computation (MPC) enable multiple parties to jointly compute a function over their private inputs without revealing anything beyond the output.
This technology is particularly relevant in scenarios where data privacy is paramount, such as collaborative research or financial transactions. Blockchain technology, with its inherent security features, also holds potential for enhancing server security by providing tamper-proof audit trails and secure data storage. Its decentralized nature can enhance resilience against single points of failure and improve the overall security posture of server systems.
Predictions for Future Developments in Server Security Practices
Future server security practices will likely emphasize a more proactive and holistic approach, incorporating artificial intelligence (AI) and machine learning (ML) for threat detection and response. AI-powered systems can analyze vast amounts of data to identify anomalies and potential threats in real-time, enabling faster and more effective responses to security incidents. Moreover, the increasing adoption of zero-trust security models will shift the focus from perimeter security to verifying the identity and trustworthiness of every user and device accessing server resources, regardless of location.
This approach minimizes the impact of breaches by limiting access to sensitive data. We can anticipate a greater emphasis on automated security patching and configuration management to reduce human error and improve the overall security posture of server systems. Continuous monitoring and automated response mechanisms will become increasingly prevalent, minimizing the time it takes to identify and mitigate security threats.
Hypothetical Future Server Security System
A hypothetical future server security system might integrate several of these technologies. The system could utilize a quantum-resistant cryptographic algorithm for data encryption and authentication, coupled with homomorphic encryption for secure data processing. AI-powered threat detection and response systems would monitor the server environment in real-time, automatically identifying and mitigating potential threats. A zero-trust architecture would govern access control, requiring continuous authentication and authorization for all users and devices.
Blockchain technology could provide a tamper-proof audit trail of all security events, enhancing accountability and transparency. The system would also incorporate automated security patching and configuration management, minimizing human error and ensuring the server remains up-to-date with the latest security patches. This holistic and proactive approach would significantly enhance the security and resilience of server systems, protecting sensitive data from both current and future threats.
Conclusive Thoughts
Securing your server infrastructure is an ongoing process, not a one-time fix. Mastering the art of server cryptography requires vigilance, continuous learning, and adaptation to evolving threats. By implementing the strategies Artikeld in this guide – from robust encryption and key management to secure coding practices and proactive security audits – you can significantly reduce your vulnerability to cyberattacks and build a more secure and resilient digital environment.
The journey towards impenetrable server security is a continuous one, but with the right knowledge and dedication, it’s a journey worth undertaking.
FAQ Summary
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption.
How often should I rotate my cryptographic keys?
Key rotation frequency depends on the sensitivity of the data and the level of risk. Best practice recommends regular rotations, at least annually, or even more frequently for high-value assets.
What are some common server-side vulnerabilities?
Common vulnerabilities include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and insecure direct object references.
What is a Hardware Security Module (HSM)?
An HSM is a physical computing device that safeguards and manages cryptographic keys, offering a higher level of security than software-based key management.