Secure Your Server with Cryptographic Excellence: In today’s interconnected world, server security is paramount. Cyber threats are constantly evolving, demanding robust defenses. Cryptography, the art of secure communication, plays a crucial role in protecting your valuable data and maintaining the integrity of your systems. This guide explores essential cryptographic techniques and best practices to fortify your server against a wide range of attacks, from simple breaches to sophisticated intrusions.
We’ll delve into encryption, authentication, access control, and vulnerability mitigation, equipping you with the knowledge to build a truly secure server environment.
We’ll cover implementing SSL/TLS certificates, encrypting data at rest, choosing strong encryption keys, and configuring secure SSH access. We’ll also examine various authentication methods, including multi-factor authentication (MFA), and discuss robust access control mechanisms like role-based access control (RBAC). Furthermore, we’ll explore strategies for protecting against common vulnerabilities like SQL injection and cross-site scripting (XSS), and the importance of regular security audits and penetration testing.
Finally, we’ll detail how to establish a secure network configuration, implement data backup and disaster recovery plans, and effectively monitor and manage server logs.
Introduction to Server Security and Cryptography
In today’s interconnected world, servers form the backbone of countless online services, storing and processing vast amounts of sensitive data. The security of these servers is paramount, as a breach can lead to significant financial losses, reputational damage, and legal repercussions. Robust server security is no longer a luxury; it’s a critical necessity for businesses and individuals alike.
This section explores the fundamental role of cryptography in achieving this essential security.Cryptography, the practice and study of techniques for secure communication in the presence of adversarial behavior, is the cornerstone of modern server security. It provides the tools and methods to protect data confidentiality, integrity, and authenticity, ensuring that only authorized users can access and manipulate sensitive information.
Without robust cryptographic implementations, servers are vulnerable to a wide array of attacks, ranging from data theft and manipulation to denial-of-service disruptions.
A Brief History of Cryptographic Techniques in Server Security
Early cryptographic techniques, such as the Caesar cipher (a simple substitution cipher), were relatively easy to break. However, the development of more sophisticated methods, like the Data Encryption Standard (DES) in the 1970s and the Advanced Encryption Standard (AES) in the 2000s, marked significant advancements in securing digital communication. The rise of public-key cryptography, pioneered by Whitfield Diffie and Martin Hellman, revolutionized the field, enabling secure key exchange and digital signatures.
The evolution of cryptographic techniques continues to this day, driven by the constant arms race between cryptographers and attackers. Modern server security relies heavily on a combination of these advanced techniques, constantly adapting to new threats and vulnerabilities.
Comparison of Cryptographic Algorithms
The selection of appropriate cryptographic algorithms is crucial for effective server security. The choice often depends on the specific security requirements and performance constraints of the application. Symmetric and asymmetric algorithms represent two fundamental approaches.
| Algorithm Type | Key Management | Speed | Use Cases |
|---|---|---|---|
| Symmetric | Single, secret key shared between sender and receiver | Fast | Data encryption at rest and in transit (e.g., AES, DES) |
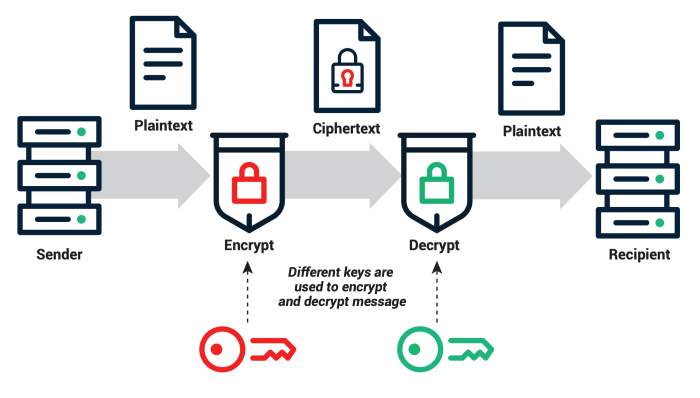
| Asymmetric | Two keys: a public key for encryption and a private key for decryption | Slow | Key exchange, digital signatures, authentication (e.g., RSA, ECC) |
Implementing Encryption Techniques
Robust encryption is paramount for securing your server and protecting sensitive data. This section details the implementation of various encryption techniques, focusing on practical steps and best practices to ensure a secure server environment. We will cover SSL/TLS certificate implementation for secure communication, data-at-rest encryption using disk encryption, strong key management, and secure SSH configuration.
SSL/TLS Certificate Implementation for Secure Communication
SSL/TLS certificates are fundamental for securing communication between a client and a server. They establish an encrypted connection, preventing eavesdropping and data tampering. The process involves obtaining a certificate from a trusted Certificate Authority (CA), configuring your web server (e.g., Apache, Nginx) to use the certificate, and ensuring proper chain of trust is established. A correctly configured SSL/TLS connection encrypts all data transmitted between the client and server, protecting sensitive information like passwords, credit card details, and personal data.
Misconfiguration can lead to vulnerabilities, exposing your server and users to attacks. Regular renewal of certificates is crucial to maintain security and avoid certificate expiry-related disruptions.
Data-at-Rest Encryption Using Disk Encryption, Secure Your Server with Cryptographic Excellence
Disk encryption safeguards data stored on the server’s hard drives even if the physical hardware is compromised. This is achieved by encrypting the entire hard drive or specific partitions using encryption software like LUKS (Linux Unified Key Setup) or BitLocker (Windows). The encryption process involves generating an encryption key, which is used to encrypt all data written to the disk.
Only with the correct key can the data be decrypted and accessed. Disk encryption adds an extra layer of security, protecting data from unauthorized access in case of theft or loss of the server hardware. Implementing disk encryption requires careful consideration of key management practices, ensuring the key is securely stored and protected against unauthorized access.
Strong Encryption Key Selection and Lifecycle Management
Choosing strong encryption keys is crucial for effective data protection. Keys should be generated using cryptographically secure random number generators and should have sufficient length to resist brute-force attacks. For example, AES-256 uses a 256-bit key, offering a very high level of security. Key lifecycle management involves defining procedures for key generation, storage, rotation, and destruction. Keys should be regularly rotated to minimize the impact of potential compromises.
A robust key management system should be implemented, using secure storage mechanisms like hardware security modules (HSMs) for sensitive keys. This helps ensure the confidentiality and integrity of the encryption keys. Failing to manage keys properly can render even the strongest encryption useless.
Secure SSH Access Configuration
SSH (Secure Shell) is a protocol used for secure remote access to servers. Proper configuration of SSH is essential to prevent unauthorized access. This includes disabling password authentication, enabling key-based authentication using SSH keys, restricting SSH access to specific IP addresses or networks, and regularly updating the SSH server software. A well-configured SSH server significantly reduces the risk of brute-force attacks targeting the SSH login credentials.
For instance, configuring SSH to only accept connections from specific IP addresses limits the attack surface, preventing unauthorized access attempts from untrusted sources. Using strong SSH keys further enhances security, as they are far more difficult to crack than passwords. Regularly auditing SSH logs helps detect and respond to suspicious activity.
Authentication and Access Control
Securing a server involves not only protecting its data but also controlling who can access it. Authentication and access control mechanisms are crucial for preventing unauthorized access and maintaining data integrity. Robust implementation of these security measures is paramount to mitigating the risk of breaches and data compromise.
Authentication Methods
Authentication verifies the identity of a user or system attempting to access a server. Several methods exist, each with its strengths and weaknesses. Password-based authentication, while widely used, is vulnerable to brute-force attacks and phishing. Multi-factor authentication (MFA) significantly enhances security by requiring multiple forms of verification. Biometric authentication, using fingerprints or facial recognition, offers strong security but can be susceptible to spoofing.
Token-based authentication, using one-time passwords or hardware tokens, provides a strong layer of security. Public key infrastructure (PKI) utilizes digital certificates to authenticate users and systems, offering a high level of security but requiring complex infrastructure management.
Multi-Factor Authentication (MFA) Implementation
MFA strengthens authentication by requiring users to provide more than one form of verification. A common approach is combining something the user knows (password), something the user has (security token or authenticator app), and something the user is (biometric data). Implementation involves integrating an MFA provider into the server’s authentication system. This often entails configuring the authentication server to require a second factor after successful password authentication.
The MFA provider then verifies the second factor, allowing access only if both factors are validated. For example, after a successful password login, the user might receive a one-time code via SMS or authenticator app, which must be entered to gain access. Proper configuration and user education are vital for effective MFA deployment.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a robust access control mechanism that grants permissions based on a user’s role within the system. Instead of assigning permissions individually to each user, RBAC assigns permissions to roles, and users are then assigned to those roles. This simplifies permission management and reduces the risk of errors. For instance, an administrator role might have full access to the server, while a user role has only read-only access to specific directories.
RBAC is implemented through access control lists (ACLs) or similar mechanisms that define the permissions associated with each role. Regular audits and reviews of assigned roles and permissions are crucial for maintaining security and preventing privilege escalation.
Securing User Accounts and Passwords
Strong password policies and practices are fundamental to securing user accounts. This includes enforcing minimum password length, complexity requirements (uppercase, lowercase, numbers, symbols), and regular password changes. Password managers can help users create and manage strong, unique passwords for various accounts. Implementing account lockout mechanisms after multiple failed login attempts thwarts brute-force attacks. Regularly auditing user accounts to identify and disable inactive or compromised accounts is crucial.
Furthermore, using strong encryption for stored passwords, such as bcrypt or Argon2, prevents unauthorized access even if the password database is compromised. Educating users about phishing and social engineering tactics is vital in preventing compromised credentials.
Protecting Against Common Vulnerabilities
Server security is a multifaceted challenge, and a robust strategy necessitates proactive measures to address common vulnerabilities. Neglecting these vulnerabilities can lead to data breaches, service disruptions, and significant financial losses. This section details common threats and effective mitigation strategies.
SQL Injection
SQL injection attacks exploit vulnerabilities in database interactions. Attackers inject malicious SQL code into input fields, potentially gaining unauthorized access to sensitive data or manipulating database operations. For example, an attacker might input '; DROP TABLE users; -- into a username field, causing the database to delete the entire user table. Effective mitigation involves parameterized queries or prepared statements, which separate data from SQL code, preventing malicious input from being interpreted as executable commands.
Input sanitization, rigorously validating and filtering user input to remove potentially harmful characters, is also crucial. Employing a web application firewall (WAF) adds an additional layer of protection by filtering malicious traffic before it reaches the server.
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) attacks involve injecting malicious scripts into websites viewed by other users. These scripts can steal user cookies, redirect users to phishing sites, or deface websites. Consider a scenario where a website doesn’t properly sanitize user-provided data displayed on a forum. An attacker could post a script that steals cookies from other users visiting the forum.
Mitigation strategies include robust input validation and output encoding. Input validation checks for potentially harmful characters or patterns in user input, while output encoding converts special characters into their HTML entities, preventing them from being executed as code. A content security policy (CSP) further enhances security by restricting the sources from which the browser can load resources, minimizing the impact of successful XSS attacks.
Server Software Patching and Updating
Regular patching and updating of server software are paramount. Outdated software often contains known vulnerabilities that attackers can exploit. The frequency of updates varies depending on the software and its criticality; however, a prompt response to security patches is essential. For instance, the timely application of a patch addressing a critical vulnerability in a web server can prevent a large-scale data breach.
Securing your server demands robust cryptographic practices. Understanding the latest advancements is crucial, and you can find insightful analysis in this excellent article on Server Security Trends: Cryptography Leads the Way , which highlights the importance of staying ahead of evolving threats. By implementing cutting-edge cryptographic techniques, you significantly enhance your server’s resilience against attacks.
Establishing a robust patch management system, including automated updates where possible, is crucial for maintaining a secure server environment. This system should include a thorough testing process in a staging environment before deploying updates to production servers.
Security Audits and Penetration Testing
Regular security audits and penetration testing provide proactive identification of vulnerabilities. Security audits involve systematic reviews of security policies, procedures, and configurations to identify weaknesses. Penetration testing simulates real-world attacks to identify exploitable vulnerabilities. For example, a penetration test might reveal a weakness in a firewall configuration that allows unauthorized access to the server. The results of both audits and penetration tests provide valuable insights for strengthening server security, allowing for the timely remediation of identified vulnerabilities.
These activities should be performed regularly, with the frequency dependent on the criticality of the system and the level of risk tolerance.
Secure Network Configuration
A robust server security strategy necessitates a meticulously designed network configuration that minimizes vulnerabilities and maximizes protection. This involves implementing firewalls, intrusion detection systems, network segmentation, VPNs, and carefully configured network access control lists (ACLs). These elements work synergistically to create a layered defense against unauthorized access and malicious attacks.
Firewall Implementation
Firewalls act as the first line of defense, filtering network traffic based on predefined rules. They examine incoming and outgoing packets, blocking those that don’t meet specified criteria. Effective firewall configuration involves defining rules based on source and destination IP addresses, ports, and protocols. For example, a rule might allow inbound SSH traffic on port 22 only from specific IP addresses, while blocking all other inbound connections on that port.
Multiple firewall layers, including both hardware and software firewalls, can be implemented for enhanced protection, providing a defense-in-depth strategy. Regular updates and maintenance are crucial to ensure the firewall remains effective against emerging threats.
Intrusion Detection System (IDS) Deployment
While firewalls prevent unauthorized access, an intrusion detection system (IDS) actively monitors network traffic for malicious activity. An IDS analyzes network packets for patterns indicative of attacks, such as port scans, denial-of-service attempts, or malware infections. Upon detecting suspicious activity, the IDS generates alerts, allowing administrators to take appropriate action, such as blocking the offending IP address or investigating the incident.
IDS can be implemented as network-based systems, monitoring traffic at the network perimeter, or host-based systems, monitoring traffic on individual servers. A combination of both provides comprehensive protection. The effectiveness of an IDS depends heavily on its ability to accurately identify malicious activity and its integration with other security tools.
Network Segmentation Benefits
Network segmentation divides a network into smaller, isolated segments. This limits the impact of a security breach, preventing an attacker from gaining access to the entire network. For example, a server hosting sensitive customer data might be placed in a separate segment from a web server, limiting the potential damage if the web server is compromised. This approach reduces the attack surface and enhances overall network security.
The benefits include improved security posture, easier network management, and enhanced performance through reduced network congestion.
VPN Configuration for Secure Remote Access
Virtual Private Networks (VPNs) create secure, encrypted connections over public networks, enabling secure remote access to servers. VPNs encrypt all data transmitted between the remote client and the server, protecting it from eavesdropping and unauthorized access. VPN configuration involves setting up a VPN server on the network and configuring clients to connect to it. Strong encryption protocols, such as IPsec or OpenVPN, should be used to ensure data confidentiality and integrity.
Implementing multi-factor authentication (MFA) further enhances security, requiring users to provide multiple forms of authentication before granting access. Regular audits of VPN configurations are critical to identify and address potential weaknesses.
Network Access Control List (ACL) Configuration
Network Access Control Lists (ACLs) define rules that control access to network resources. They specify which users or devices are permitted to access specific network segments or services. ACLs can be implemented on routers, switches, and firewalls to restrict unauthorized access. For example, an ACL might allow only specific IP addresses to access a database server, preventing unauthorized access to sensitive data.
Effective ACL configuration requires a thorough understanding of network topology and security requirements. Regular reviews and updates are essential to ensure that ACLs remain effective in protecting network resources. Incorrectly configured ACLs can inadvertently block legitimate traffic, highlighting the need for careful planning and testing.
Data Backup and Disaster Recovery: Secure Your Server With Cryptographic Excellence

Data backup and disaster recovery are critical components of a robust server security strategy. A comprehensive plan ensures business continuity and minimizes data loss in the event of hardware failure, cyberattacks, or natural disasters. This section Artikels strategies for creating effective backups and implementing efficient recovery procedures.
Data Backup Strategy
A well-defined data backup strategy should address several key aspects. The frequency of backups depends on the rate of data change and the acceptable level of potential data loss. For critical systems, real-time or near real-time backups might be necessary, while less critical systems may only require daily or weekly backups. The storage location should be geographically separate from the primary server location to mitigate the risk of simultaneous data loss.
This could involve using a cloud-based storage solution, a secondary on-site server, or a remote data center. Furthermore, the backup strategy should include a clear process for verifying the integrity and recoverability of the backups. This might involve regular testing of the restoration process to ensure that data can be effectively retrieved. Multiple backup copies should be maintained, using different backup methods (e.g., full backups, incremental backups, differential backups) to provide redundancy and ensure data protection.
Disaster Recovery Techniques
Several disaster recovery techniques can be implemented to ensure business continuity in the event of a disaster. These techniques range from simple failover systems to complex, multi-site solutions. Failover systems automatically switch to a secondary server in the event of a primary server failure. This ensures minimal downtime and maintains service availability. More sophisticated solutions might involve a hot site, a fully equipped data center that can quickly take over operations in case of a disaster.
A warm site offers similar functionality but with slightly longer recovery times due to the need for some system configuration. Cold sites offer the lowest cost, but require the most time to restore operations. The choice of disaster recovery technique depends on factors such as the criticality of the server, budget, and recovery time objectives (RTOs) and recovery point objectives (RPOs).
For instance, a financial institution with strict regulatory requirements might opt for a hot site to minimize downtime, while a smaller business with less stringent requirements might choose a warm site or even a cold site.
Backup and Recovery Testing
Regular testing of backup and recovery procedures is crucial to ensure their effectiveness. This involves periodically restoring data from backups to verify their integrity and recoverability. Testing should simulate real-world scenarios, including hardware failures and data corruption. The frequency of testing depends on the criticality of the system and the complexity of the backup and recovery procedures.
At a minimum, testing should be conducted annually, but more frequent testing might be necessary for critical systems. Documentation of the testing process, including results and any identified issues, is essential for continuous improvement. This documentation should be easily accessible to all relevant personnel. Without regular testing, the effectiveness of the backup and recovery plan remains uncertain, potentially leading to significant data loss or extended downtime in a real disaster scenario.
Version Control for Secure Code Management
Version control systems (VCS), such as Git, provide a robust mechanism for managing and tracking changes to code. They offer a centralized repository for storing code, enabling collaboration among developers and facilitating the tracking of modifications. Using a VCS promotes secure code management by allowing for the easy rollback of changes in case of errors or security vulnerabilities.
Furthermore, VCS features like branching and merging allow for the development of new features or bug fixes in isolation, minimizing the risk of disrupting the main codebase. Regular commits and well-defined branching strategies ensure a clear history of code changes, aiding in identifying the source of errors and facilitating quick recovery from incidents. Moreover, the use of a VCS often integrates with security tools, allowing for automated code scanning and vulnerability detection.
The integration of security scanning tools into the VCS workflow ensures that security vulnerabilities are identified and addressed promptly.
Monitoring and Log Management
Proactive server monitoring and robust log management are critical components of a comprehensive server security strategy. They provide the visibility needed to detect, understand, and respond effectively to security threats before they can cause significant damage. Without these capabilities, even the most robust security measures can be rendered ineffective due to a lack of awareness of potential breaches or ongoing attacks.Effective log management provides a detailed audit trail of all server activities, allowing security professionals to reconstruct events, identify anomalies, and trace the origins of security incidents.
This capability is essential for compliance with various regulations and for building a strong security posture.
Server Monitoring for Threat Identification
Real-time server monitoring allows for the immediate detection of suspicious activity. This includes monitoring CPU usage, memory consumption, network traffic, and file system changes. Significant deviations from established baselines can indicate a potential attack or compromise. For example, a sudden spike in network traffic to an unusual destination could suggest a data exfiltration attempt. Similarly, unauthorized access attempts, detected through failed login attempts or unusual process executions, can be flagged immediately, allowing for swift intervention.
Automated alerts based on predefined thresholds can streamline the detection process, ensuring that security personnel are notified promptly of any potential issues.
Effective Log Management Implementation
Implementing effective log management requires a structured approach. This begins with the centralized collection of logs from all relevant server components, including operating systems, applications, and network devices. Logs should be standardized using a common format (like syslog) for easier analysis and correlation. Data retention policies must be defined to balance the need for historical analysis with storage limitations.
Consider factors like legal requirements and the potential for long-term investigations when determining retention periods. Encryption of logs in transit and at rest is crucial to protect sensitive information contained within them. Regular log rotation and archiving practices ensure that logs are managed efficiently and prevent storage overload.
Security Log Analysis Best Practices
Analyzing security logs effectively requires a combination of automated tools and human expertise. Automated tools can identify patterns and anomalies that might be missed by manual review. These tools can search for specific s, analyze event sequences, and generate alerts based on predefined rules. However, human analysts remain crucial for interpreting the context of these alerts and for identifying subtle indicators of compromise that automated tools might overlook.
Correlation of logs from multiple sources provides a more comprehensive view of security events, allowing analysts to piece together the sequence of events leading up to an incident. Regular review of security logs, even in the absence of alerts, can uncover hidden vulnerabilities or potential threats.
Security Information and Event Management (SIEM) Systems
SIEM systems provide a centralized platform for collecting, analyzing, and managing security logs from diverse sources. They offer advanced capabilities for log correlation, threat detection, and incident response. Examples of popular SIEM systems include Splunk, IBM QRadar, and Elastic Stack (formerly known as the ELK stack). These systems typically offer features such as real-time monitoring, automated alerts, customizable dashboards, and reporting capabilities.
They can integrate with other security tools, such as intrusion detection systems (IDS) and vulnerability scanners, to provide a holistic view of the security posture. The choice of SIEM system depends on factors such as the scale of the environment, budget, and specific security requirements.
Illustrative Example: Securing a Web Server
This section details a scenario involving a vulnerable web server and Artikels the steps to secure it using cryptographic techniques and best practices discussed previously. We will focus on a fictional e-commerce website to illustrate practical application of these security measures.Imagine an e-commerce website, “ShopSecure,” hosted on a web server with minimal security configurations. The server uses an outdated operating system, lacks robust firewall rules, and employs weak password policies.
Furthermore, sensitive customer data, including credit card information, is transmitted without encryption. This creates numerous vulnerabilities, exposing the server and its data to various attacks.
Vulnerabilities of the Unsecured Web Server
The unsecured ShopSecure web server faces multiple threats. These include unauthorized access attempts via brute-force attacks targeting weak passwords, SQL injection vulnerabilities exploiting flaws in the database interaction, cross-site scripting (XSS) attacks manipulating website code to inject malicious scripts, and man-in-the-middle (MITM) attacks intercepting unencrypted data transmissions. Data breaches resulting from these vulnerabilities could lead to significant financial losses and reputational damage.
Securing the ShopSecure Web Server
Securing ShopSecure requires a multi-layered approach. The following steps detail the implementation of security measures using cryptographic techniques and best practices.
- Operating System Hardening: Upgrade to the latest stable version of the operating system and apply all security patches. This reduces the server’s vulnerability to known exploits. Regular updates are crucial for mitigating newly discovered vulnerabilities.
- Firewall Configuration: Implement a robust firewall to restrict inbound and outbound network traffic. Only essential ports (e.g., port 80 for HTTP, port 443 for HTTPS, port 22 for SSH) should be open. This prevents unauthorized access attempts from external sources.
- Strong Password Policies: Enforce strong password policies requiring a minimum length, complexity (uppercase, lowercase, numbers, symbols), and regular changes. Consider using a password manager to securely store and manage complex passwords.
- HTTPS Implementation: Obtain and install an SSL/TLS certificate to enable HTTPS. This encrypts all communication between the web server and clients, protecting sensitive data from eavesdropping and MITM attacks. Use a reputable Certificate Authority (CA).
- Input Validation and Sanitization: Implement robust input validation and sanitization to prevent SQL injection and XSS attacks. All user-supplied data should be thoroughly checked and escaped before being used in database queries or displayed on web pages.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify and address potential vulnerabilities before they can be exploited by attackers. This proactive approach helps maintain a high level of security.
- Database Security: Secure the database by implementing strong access control measures, limiting database user privileges, and regularly backing up the database. Use encryption for sensitive data stored within the database.
- Web Application Firewall (WAF): Deploy a WAF to filter malicious traffic and protect against common web application attacks such as SQL injection, XSS, and cross-site request forgery (CSRF).
- Intrusion Detection and Prevention System (IDS/IPS): Implement an IDS/IPS to monitor network traffic for malicious activity and automatically block or alert on suspicious events.
Secured Web Server Architecture
The secured ShopSecure web server architecture incorporates the following security measures:
- Secure Operating System: Up-to-date operating system with all security patches applied.
- Firewall: Restricting network access to essential ports only.
- HTTPS with Strong Encryption: All communication is encrypted using TLS 1.3 or higher with a certificate from a trusted CA.
- Input Validation and Sanitization: Protecting against SQL injection and XSS attacks.
- Strong Authentication: Using multi-factor authentication (MFA) wherever possible.
- Regular Security Audits: Proactive vulnerability identification and remediation.
- Database Encryption: Protecting sensitive data at rest.
- WAF and IDS/IPS: Providing an additional layer of protection against malicious traffic and attacks.
- Regular Backups: Ensuring data recovery in case of disaster.
Final Thoughts
Securing your server with cryptographic excellence isn’t a one-time task; it’s an ongoing process. By implementing the techniques and best practices Artikeld in this guide, you can significantly reduce your vulnerability to cyber threats. Remember, a layered security approach, combining strong cryptography with robust access control and vigilant monitoring, is crucial for maintaining a secure and reliable server environment.
Proactive security measures are far more effective and cost-efficient than reactive damage control. Stay informed about the latest threats and vulnerabilities, and regularly update your security protocols to stay ahead of the curve.
Frequently Asked Questions
What are the different types of encryption?
Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption.
How often should I update my server software?
Regularly, ideally as soon as security patches are released. This mitigates known vulnerabilities.
What is a SIEM system and why is it important?
A Security Information and Event Management (SIEM) system collects and analyzes security logs from various sources to detect and respond to security incidents.
How can I choose a strong password?
Use a passphrase – a long, complex sentence – rather than a simple word. Avoid using personal information.
What is the difference between a firewall and an intrusion detection system (IDS)?
A firewall controls network traffic, blocking unauthorized access. An IDS monitors network traffic for malicious activity and alerts administrators.