Cryptography: The Server’s Best Defense. In today’s interconnected world, server security is paramount. Cyber threats are constantly evolving, demanding robust protection. This comprehensive guide explores the critical role of cryptography in safeguarding your server infrastructure, from securing data at rest and in transit to implementing secure communication protocols and mitigating common cryptographic attacks. We’ll delve into symmetric and asymmetric encryption, key management, digital signatures, and the burgeoning field of hardware security modules (HSMs), providing practical strategies for bolstering your server’s defenses against increasingly sophisticated threats.
We’ll examine real-world examples of security breaches stemming from weak cryptographic practices, illustrating the dire consequences of neglecting robust security measures. Understanding the intricacies of cryptography is no longer optional; it’s a necessity for anyone responsible for maintaining a secure server environment. This guide aims to equip you with the knowledge and tools needed to effectively protect your valuable data and maintain the integrity of your systems.
Introduction to Server Security and Cryptography
In today’s interconnected world, servers are the backbone of countless online services, storing and processing vast amounts of sensitive data. Protecting this data from unauthorized access and manipulation is paramount, and cryptography plays a crucial role in achieving this. Without robust cryptographic techniques, servers are vulnerable to a wide range of attacks, potentially leading to significant financial losses, reputational damage, and legal repercussions.
This section will explore the fundamental importance of cryptography in securing server infrastructure and examine the various threats it mitigates.Cryptography provides the essential building blocks for secure server communication and data protection. It employs mathematical techniques to transform readable data (plaintext) into an unreadable format (ciphertext), ensuring confidentiality. Furthermore, it offers mechanisms for data integrity verification, ensuring data hasn’t been tampered with, and for authentication, verifying the identity of communicating parties.
These cryptographic primitives are essential for securing various aspects of server operations, from securing network traffic to protecting stored data.
Types of Threats Mitigated by Cryptography
Cryptography protects against a diverse range of threats targeting server infrastructure. These threats can be broadly categorized into confidentiality breaches, integrity violations, and authentication failures. Effective cryptographic solutions are designed to counter each of these threat vectors.
- Confidentiality breaches: These involve unauthorized access to sensitive data stored on or transmitted by the server. Cryptography, through techniques like encryption, prevents attackers from reading confidential information, even if they manage to intercept it.
- Integrity violations: These occur when data is altered without authorization. Cryptographic hash functions and digital signatures allow servers and clients to verify the integrity of data, ensuring it hasn’t been modified during transmission or storage.
- Authentication failures: These involve attackers impersonating legitimate users or services to gain unauthorized access. Cryptography, using techniques like digital certificates and public key infrastructure (PKI), enables secure authentication, verifying the identity of communicating parties.
Examples of Server Breaches Due to Weak Cryptography
Numerous high-profile server security breaches have been directly attributed to weak or improperly implemented cryptography. These incidents underscore the critical need for strong and up-to-date cryptographic practices.
- The Heartbleed bug (2014): This vulnerability in the OpenSSL cryptographic library allowed attackers to extract sensitive data, including private keys and user credentials, from affected servers. The bug stemmed from a flaw in the implementation of the TLS/SSL heartbeat extension, a feature designed to maintain network connections.
- The Equifax data breach (2017): This massive breach exposed the personal information of over 147 million people. The breach was partially attributed to the failure to patch a known vulnerability in the Apache Struts framework, which involved outdated and vulnerable cryptographic libraries.
Symmetric vs. Asymmetric Encryption for Servers
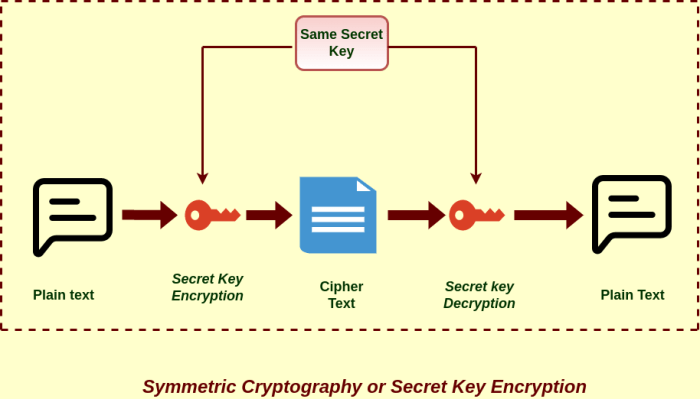
Server security relies heavily on encryption to protect sensitive data. Choosing the right encryption method—symmetric or asymmetric—is crucial for balancing security needs with performance considerations. This section compares and contrasts these two fundamental approaches, highlighting their strengths and weaknesses within the server environment.Symmetric and asymmetric encryption differ fundamentally in how they manage encryption keys. Symmetric encryption uses a single secret key to encrypt and decrypt data, while asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption.
This key management difference leads to significant variations in their applicability and security profiles on servers.
Symmetric Encryption in Server Environments
Symmetric encryption algorithms, such as AES (Advanced Encryption Standard) and DES (Data Encryption Standard), are known for their speed and efficiency. They are well-suited for encrypting large amounts of data quickly, a crucial factor for servers handling substantial data traffic. However, the secure distribution and management of the single secret key present a significant challenge. Compromise of this key compromises the entire encrypted data set.
Therefore, symmetric encryption is often used to protect data at rest or in transit after the key has been securely established using asymmetric methods. Examples of server-side applications employing symmetric encryption include database encryption, file system encryption, and securing data in transit within a trusted network.
Asymmetric Encryption in Server Environments
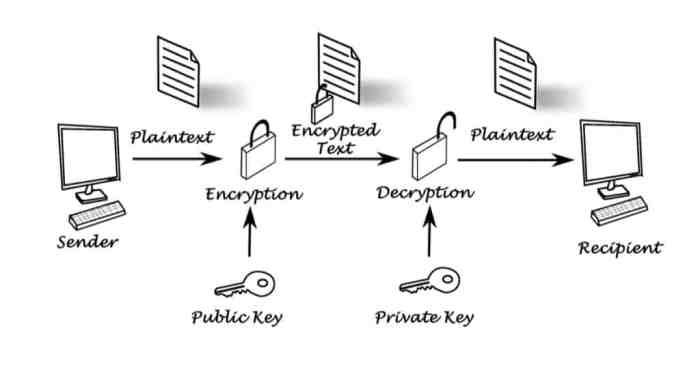
Asymmetric encryption, utilizing algorithms like RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography), offers a different approach to key management. The public key can be freely distributed, allowing anyone to encrypt data intended for the server. Only the server, possessing the corresponding private key, can decrypt it. This eliminates the need for secure key exchange for each communication, a significant advantage in less-secure network environments.
However, asymmetric encryption is computationally more intensive than symmetric encryption, making it less suitable for encrypting large volumes of data. On servers, asymmetric encryption is typically used for tasks like key exchange (e.g., establishing a shared secret key for symmetric encryption using Diffie-Hellman), digital signatures (verifying the authenticity and integrity of data), and secure authentication protocols (e.g., SSL/TLS).
Combined Use of Symmetric and Asymmetric Encryption, Cryptography: The Server’s Best Defense
A robust server security architecture often leverages both symmetric and asymmetric encryption in a complementary manner. A common scenario involves using asymmetric encryption to securely exchange a symmetric encryption key. This is the basis of many secure communication protocols. For instance, consider a web server using HTTPS. The initial handshake uses asymmetric encryption (RSA) to exchange a session key.
Once the session key is established securely, all subsequent communication between the client and server uses fast and efficient symmetric encryption (AES) to encrypt and decrypt the data. This hybrid approach combines the security benefits of asymmetric encryption for key exchange with the speed and efficiency of symmetric encryption for data transfer. The server uses its private key to decrypt the initial handshake, obtaining the symmetric key.
All subsequent data is encrypted and decrypted using this much faster symmetric key. This model ensures both security and performance.
Implementing Secure Communication Protocols: Cryptography: The Server’s Best Defense
Secure communication protocols are paramount for protecting server-client interactions. These protocols ensure data integrity, confidentiality, and authenticity, safeguarding sensitive information exchanged between the server and its users. The most prevalent and widely adopted protocol for achieving this level of security is Transport Layer Security (TLS), formerly known as Secure Sockets Layer (SSL).TLS/SSL encrypts the communication channel between a server and a client, preventing eavesdropping and data tampering.
It establishes a secure connection through a complex handshake process involving cryptographic algorithms and digital certificates, ensuring only authorized parties can access and exchange information. This protection is vital for applications handling sensitive data, such as online banking, e-commerce, and email.
The Role of TLS/SSL in Securing Server-Client Communication
TLS/SSL operates at the transport layer of the network stack, providing a secure tunnel over an underlying insecure network like the internet. This tunnel ensures that all data transmitted between the client and the server is encrypted, protecting it from unauthorized access. Beyond encryption, TLS/SSL also provides mechanisms for verifying the server’s identity using digital certificates, preventing man-in-the-middle attacks where an attacker intercepts communication.
The protocol’s use of various cryptographic algorithms allows for flexible and robust security, adaptable to different threat models and security requirements. Furthermore, TLS/SSL supports features like Perfect Forward Secrecy (PFS), enhancing long-term security by ensuring that the compromise of a server’s private key does not compromise past communications.
Establishing a Secure Connection Using TLS/SSL: A Step-by-Step Process
The establishment of a secure TLS/SSL connection follows a well-defined handshake process. This process involves several steps, beginning with the client initiating the connection and ending with the establishment of an encrypted communication channel. The handshake involves a negotiation of cryptographic parameters, authentication of the server, and the generation of a shared secret key used for symmetric encryption of the subsequent communication.
A simplified representation of this process would show a series of messages exchanged between the client and server, each message containing information relevant to the key exchange and authentication process. The process can be visualized as a series of steps:
1. Client Hello
The client initiates the connection by sending a “Client Hello” message, specifying supported TLS versions, cipher suites (encryption algorithms), and other parameters.
2. Server Hello
The server responds with a “Server Hello” message, selecting a cipher suite from the client’s list, and sending its digital certificate.
3. Certificate Verification
The client verifies the server’s certificate against a trusted Certificate Authority (CA). If the certificate is valid, the client proceeds; otherwise, the connection is aborted.
4. Key Exchange
The client and server exchange messages to establish a shared secret key using a key exchange algorithm (e.g., Diffie-Hellman).
5. Change Cipher Spec
Both client and server send a “Change Cipher Spec” message, indicating a switch to encrypted communication.
6. Finished
Both client and server send a “Finished” message, encrypted using the shared secret key, confirming the successful establishment of the secure connection. After this, all further communication is encrypted.
Configuring a Web Server with Strong TLS/SSL Encryption: A Step-by-Step Guide
Configuring a web server for strong TLS/SSL encryption involves several key steps. The specific steps may vary depending on the web server software used (e.g., Apache, Nginx), but the general principles remain the same. The primary objective is to ensure that the server is using a strong cipher suite, a valid and up-to-date certificate, and appropriate security headers.
1. Obtain a Certificate
Acquire a TLS/SSL certificate from a trusted Certificate Authority (CA). This certificate digitally binds the server’s identity to its public key. Let’s Encrypt is a popular and free option for obtaining certificates.
2. Install the Certificate
Install the certificate and its private key on the web server. The exact method varies based on the server software, typically involving placing the files in specific directories and configuring the server to use them.
3. Configure the Web Server
Configure the web server to use the certificate and enforce secure connections (HTTPS). This usually involves specifying the certificate and key files in the server’s configuration files.
4. Enable Strong Cipher Suites
Ensure the server is configured to use only strong and modern cipher suites, avoiding outdated and vulnerable algorithms. This can be done by specifying a list of preferred cipher suites in the server configuration.
5. Implement HTTP Strict Transport Security (HSTS)
HSTS forces all connections to the server to use HTTPS, preventing downgrade attacks. This involves adding an HSTS header to the server’s responses.
6. Regularly Update Certificates
Certificates have expiration dates; ensure to renew them before they expire to avoid service interruptions.
Data Encryption at Rest and in Transit
Protecting server data is paramount for maintaining confidentiality, integrity, and availability. This involves employing robust encryption techniques both when data is stored (at rest) and when it’s being transmitted (in transit). Failure to adequately secure data in both states leaves it vulnerable to various threats, including unauthorized access, data breaches, and manipulation.Data encryption at rest and in transit are distinct but equally crucial aspects of a comprehensive server security strategy.
Effective implementation requires understanding the different encryption methods available and selecting the most appropriate ones based on factors like sensitivity of the data, performance requirements, and budget constraints.
Data Encryption at Rest
Encrypting data at rest involves securing data stored on server hard drives, databases, and other storage media. This prevents unauthorized access even if the server is compromised. Best practices include using strong encryption algorithms, regularly updating encryption keys, and implementing access control measures to limit who can decrypt the data. Full-disk encryption (FDE) is a common approach, encrypting the entire storage device.
File-level encryption provides granular control, allowing selective encryption of specific files or folders. Database encryption encrypts the data within the database itself, often at the column or table level. Choosing the right method depends on the specific needs and security posture of the organization.
Data Encryption in Transit
Data encryption in transit protects data while it’s being transmitted over a network, such as between a server and a client. This is crucial to prevent eavesdropping and man-in-the-middle attacks. Secure communication protocols like TLS/SSL (Transport Layer Security/Secure Sockets Layer) are widely used for encrypting data in transit. VPNs (Virtual Private Networks) create secure tunnels for data transmission, providing additional security.
HTTPS, a secure version of HTTP, uses TLS/SSL to encrypt communication between web browsers and web servers. The selection of the encryption method often depends on the application and the level of security required.
Comparison of Encryption Algorithms
The choice of encryption algorithm significantly impacts the security and performance of your server. Several factors must be considered, including key size, speed, and security level. The following table compares some common algorithms:
| Algorithm | Key Size (bits) | Speed | Security Level |
|---|---|---|---|
| AES (Advanced Encryption Standard) | 128, 192, 256 | Fast | High |
| RSA (Rivest-Shamir-Adleman) | 1024, 2048, 4096 | Slow | High (for sufficiently large key sizes) |
| ChaCha20 | 256 | Fast | High |
| ECC (Elliptic Curve Cryptography) | 256, 384, 521 | Relatively Fast | High (achieves comparable security with smaller key sizes than RSA) |
Key Management and Security
Secure key management is paramount for the effectiveness of any cryptographic system protecting a server. Compromised keys render even the strongest encryption algorithms vulnerable, leading to data breaches and system compromises. This section details crucial aspects of key generation, storage, and exchange protocols, emphasizing secure practices for server environments.Secure key generation involves creating cryptographic keys that are statistically unpredictable and resistant to various attacks.
Weak keys, easily guessed or derived, are a major security risk. Strong key generation relies on cryptographically secure pseudo-random number generators (CSPRNGs) to produce keys with sufficient entropy. The length of the key is also crucial; longer keys offer greater resistance to brute-force attacks. The specific algorithm used for key generation must be robust and well-vetted, ideally adhering to widely accepted standards and regularly updated to address emerging vulnerabilities.
The process should also include methods for verifying the integrity of the generated keys, ensuring they haven’t been tampered with.
Secure Key Generation and Storage
Secure key generation begins with the selection of a robust CSPRNG. This algorithm should be resistant to prediction and manipulation, producing keys that are statistically random and unpredictable. Factors such as the seed value used to initialize the CSPRNG, and the algorithm’s internal state, significantly impact the quality of the generated keys. For instance, a weak seed or a vulnerable CSPRNG algorithm could lead to predictable or easily guessable keys.
Key length is equally critical. Longer keys offer exponentially greater resistance to brute-force attacks, where an attacker tries all possible key combinations. For example, a 128-bit key offers significantly more security than a 64-bit key. The generation process itself should be tamper-proof, with mechanisms to detect any attempts to manipulate the key generation process. This might involve using hardware security modules (HSMs) or other trusted execution environments.Secure key storage is equally important.
Keys should be stored in a manner that protects them from unauthorized access, modification, or deletion. Common methods include storing keys in hardware security modules (HSMs), which provide tamper-resistant environments for key storage and management. Software-based key management systems can also be used, but they require robust security measures, such as encryption at rest and access control lists, to prevent unauthorized access.
Regular key rotation, replacing keys at predefined intervals, helps mitigate the risk of long-term key compromise. This limits the damage caused if a key is compromised, as the attacker only has access to a limited timeframe of data.
Key Management Systems
Several key management systems exist, each with its own advantages and disadvantages. Hardware Security Modules (HSMs) offer the highest level of security, providing tamper-resistant hardware for key generation, storage, and usage. However, they can be expensive and require specialized expertise to manage. Software-based key management systems are more cost-effective but require robust security measures to protect against software vulnerabilities and attacks.
Cloud-based key management systems offer scalability and accessibility but introduce dependencies on third-party providers and raise concerns about data sovereignty and security. The choice of a key management system depends on the specific security requirements, budget constraints, and technical expertise available.
Secure Key Exchange Protocol: Diffie-Hellman
The Diffie-Hellman key exchange is a widely used protocol for establishing a shared secret key over an insecure channel. It allows two parties to agree on a secret key without ever explicitly transmitting the key itself. This protocol relies on the computational difficulty of the discrete logarithm problem. The process involves two parties, Alice and Bob, agreeing on a public prime number (p) and a generator (g).
Each party then generates a private key (a for Alice, b for Bob) and calculates a public key (A = g a mod p for Alice, B = g b mod p for Bob). They exchange their public keys. Alice calculates the shared secret as S = B a mod p, and Bob calculates the shared secret as S = A b mod p.
Both calculations result in the same shared secret, which they can then use as a key for symmetric encryption. This protocol ensures that the shared secret is never transmitted directly, mitigating the risk of interception. However, it is crucial to use strong parameters (large prime numbers) and to protect against man-in-the-middle attacks, often by employing digital signatures or other authentication mechanisms.
Digital Signatures and Authentication
Digital signatures provide a crucial layer of security for server-side applications, ensuring both the authenticity and integrity of data exchanged. Unlike simple passwords, they leverage cryptographic techniques to verify the sender’s identity and guarantee that the message hasn’t been tampered with during transmission. This is paramount for maintaining trust and preventing unauthorized access or data manipulation.Digital signatures rely on asymmetric cryptography, employing a pair of keys: a private key (kept secret by the signer) and a public key (freely distributed).
The private key is used to create the signature, while the public key verifies it. This ensures that only the legitimate owner of the private key could have created the signature. The process involves hashing the data to create a digital fingerprint, then encrypting this hash with the private key. The recipient then uses the sender’s public key to decrypt the hash and compare it to a newly computed hash of the received data.
A match confirms both authenticity (the data originated from the claimed sender) and integrity (the data hasn’t been altered).
Digital Signature Implementation for Servers
Implementing digital signatures involves several steps. First, a trusted certificate authority (CA) issues a digital certificate containing the server’s public key and other identifying information. This certificate acts as a trusted vouch for the server’s identity. Next, the server uses its private key to generate a digital signature for any data it sends. This signature is then appended to the data.
The client receiving the data uses the server’s public key (obtained from the certificate) to verify the signature. If the verification process is successful, the client can be confident that the data originated from the server and hasn’t been modified in transit. Popular libraries and frameworks offer functionalities for streamlined implementation, reducing the need for complex low-level coding.
Robust cryptography is paramount for securing servers against increasingly sophisticated attacks. Understanding its current applications is crucial, but to truly future-proof your systems, consider the advancements discussed in this insightful article on Cryptography: The Future of Server Security. By staying ahead of the curve, you can ensure your server’s defenses remain impenetrable against tomorrow’s threats. Investing in strong cryptography today is an investment in tomorrow’s server security.
For instance, OpenSSL provides comprehensive tools for generating keys, creating and verifying signatures, and managing certificates.
Digital Signature Enhancements to Server Security
Digital signatures significantly enhance server security in several ways. Firstly, they authenticate the server’s identity, preventing impersonation attacks where malicious actors pretend to be the legitimate server. This is particularly important for secure communication protocols like HTTPS, where digital signatures ensure that the client is communicating with the intended server and not a man-in-the-middle attacker. Secondly, they guarantee data integrity.
Any alteration to the data after signing will invalidate the signature, alerting the recipient to potential tampering. This protects against malicious modifications to sensitive data like financial transactions or user credentials. Thirdly, digital signatures contribute to non-repudiation, meaning the sender cannot deny having sent the data. This is crucial for legally binding transactions and audit trails. For example, a digitally signed software update guarantees that the update comes from the legitimate software vendor and hasn’t been tampered with, preventing the installation of malicious code.
Similarly, digitally signed server logs provide an immutable record of server activity, invaluable for security audits and incident response.
Protecting Against Common Cryptographic Attacks
Server-side cryptography, while crucial for security, is vulnerable to various attacks if not implemented and managed correctly. Understanding these threats and employing robust mitigation strategies is paramount for maintaining data confidentiality, integrity, and availability. This section details common attacks and provides practical defense mechanisms.
Known-Plaintext Attacks
Known-plaintext attacks exploit the knowledge of both the plaintext (original message) and its corresponding ciphertext (encrypted message) to deduce the encryption key. This information allows attackers to decrypt other messages encrypted with the same key. For example, if an attacker obtains a password reset email (plaintext) and its encrypted version (ciphertext), they might be able to derive the encryption key used and decrypt other sensitive data.
Mitigation focuses on strong key generation and management practices, employing keys with sufficient length and randomness, and regularly rotating keys to limit the window of vulnerability. Furthermore, using robust encryption algorithms resistant to known-plaintext attacks is essential.
Ciphertext-Only Attacks
In ciphertext-only attacks, the attacker only has access to the encrypted data. The goal is to decipher the ciphertext without knowing the plaintext or the key. This type of attack relies on statistical analysis of the ciphertext to identify patterns and weaknesses in the encryption algorithm. For instance, an attacker might analyze the frequency of certain ciphertext characters to infer information about the underlying plaintext.
Strong encryption algorithms with large keyspaces and resistance to frequency analysis are crucial defenses. Implementing techniques like padding and using modes of operation that obscure statistical patterns within the ciphertext further enhances security.
Chosen-Plaintext Attacks
Chosen-plaintext attacks allow the attacker to choose specific plaintexts and obtain their corresponding ciphertexts. This information can then be used to deduce the encryption key or weaken the encryption algorithm. A real-world example could involve an attacker submitting various inputs to a web application and observing the encrypted responses. This type of attack is mitigated by restricting access to encryption functions, ensuring only authorized personnel can encrypt data, and implementing input validation to prevent malicious inputs.
Employing algorithms resistant to chosen-plaintext attacks is also essential.
Chosen-Ciphertext Attacks
Similar to chosen-plaintext attacks, chosen-ciphertext attacks allow the attacker to choose specific ciphertexts and obtain their corresponding plaintexts. This attack model is more powerful and allows attackers to potentially recover the encryption key. The attacker might exploit vulnerabilities in the decryption process to obtain information about the key. Mitigation strategies involve carefully designing decryption processes to prevent information leakage and using authenticated encryption schemes which combine encryption and authentication to ensure data integrity and prevent chosen-ciphertext attacks.
Side-Channel Attacks
Side-channel attacks exploit information leaked through physical channels during cryptographic operations. This can include timing information, power consumption, or electromagnetic emissions. For instance, an attacker might measure the time it takes for a server to decrypt a ciphertext and use these timing variations to deduce parts of the key. Mitigation requires careful hardware and software design to minimize information leakage.
Techniques such as constant-time algorithms, power analysis countermeasures, and shielding against electromagnetic emissions can significantly reduce the effectiveness of side-channel attacks.
Security Checklist for Protecting Against Cryptographic Attacks
The following checklist summarizes key security measures to protect against common cryptographic attacks:
- Use strong, well-established encryption algorithms with sufficient key lengths.
- Implement robust key generation and management practices, including key rotation.
- Employ authenticated encryption schemes to ensure both confidentiality and integrity.
- Regularly update cryptographic libraries and software to patch known vulnerabilities.
- Restrict access to cryptographic keys and functions.
- Implement input validation to prevent malicious inputs from being used in cryptographic operations.
- Employ countermeasures against side-channel attacks, such as constant-time algorithms.
- Conduct regular security audits and penetration testing to identify and address vulnerabilities.
- Monitor system logs for suspicious activity related to cryptographic operations.
- Use hardware security modules (HSMs) for enhanced key protection.
Hardware Security Modules (HSMs)
Hardware Security Modules (HSMs) are dedicated cryptographic processing units designed to protect cryptographic keys and perform cryptographic operations in a secure environment. They offer a significantly higher level of security compared to software-based solutions, making them crucial for organizations handling sensitive data, particularly in server environments. Their secure architecture protects keys from unauthorized access, even if the server itself is compromised.HSMs provide several key benefits for server cryptography.
They offer tamper-resistance, meaning physical attempts to access the keys are detected and prevented. They also isolate cryptographic operations from the main server system, protecting against software vulnerabilities and malware. This isolation ensures that even if the operating system is compromised, the keys remain safe within the HSM’s secure environment. Furthermore, HSMs often include features such as key lifecycle management, allowing for automated key generation, rotation, and destruction, enhancing overall security posture.
Software-Based vs. Hardware-Based Cryptographic Solutions
Software-based cryptographic solutions, while often more cost-effective initially, are inherently vulnerable to attacks targeting the underlying operating system or application. Malware can easily steal keys stored in software, compromising the entire security system. Hardware-based solutions, such as HSMs, provide a significantly higher level of protection by isolating the cryptographic operations and keys within a physically secure device. This isolation makes it far more difficult for attackers to access keys, even with advanced techniques like privilege escalation or rootkit infections.
The choice between software and hardware-based cryptography depends on the sensitivity of the data being protected and the organization’s risk tolerance. For high-security applications, such as financial transactions or government data, HSMs are the preferred choice.
Cost and Complexity of HSM Implementation
Implementing HSMs involves a higher initial investment compared to software-based solutions. The cost includes the purchase of the HSM hardware itself, integration with existing server infrastructure, and potentially specialized training for administrators. Furthermore, HSMs often require more complex management procedures than software-based systems. However, the enhanced security provided by HSMs often outweighs the increased cost and complexity, particularly in environments where the cost of a data breach is significantly high.
For example, a financial institution processing millions of transactions daily would likely find the increased cost of HSMs justified by the protection against potentially devastating financial losses from a security breach. The long-term cost savings from avoided breaches and regulatory fines often outweigh the initial investment.
Future Trends in Server Cryptography
The landscape of server cryptography is in constant flux, driven by advancements in computing power, the emergence of new threats, and the ever-increasing demand for robust security. Understanding these evolving trends is crucial for maintaining the confidentiality, integrity, and availability of sensitive data stored and processed on servers. This section explores some key areas shaping the future of server-side cryptography.
Post-Quantum Cryptography
The advent of quantum computing poses a significant threat to currently used public-key cryptography algorithms like RSA and ECC. Quantum computers, with their ability to perform Shor’s algorithm, can potentially break these algorithms, rendering current encryption methods obsolete. Post-quantum cryptography (PQC) aims to develop cryptographic algorithms resistant to attacks from both classical and quantum computers. The National Institute of Standards and Technology (NIST) has been leading the effort to standardize PQC algorithms, selecting several candidates for various cryptographic tasks, including key establishment and digital signatures.
The transition to PQC will require a significant overhaul of existing cryptographic infrastructure, but the potential impact of quantum computers necessitates this proactive approach. For example, migrating to NIST-standardized PQC algorithms will involve updating server software, hardware, and communication protocols. This transition is expected to take several years, requiring careful planning and phased implementation to minimize disruption.
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on encrypted data without decryption. This has significant implications for cloud computing and data privacy, allowing sensitive data to be processed remotely without compromising confidentiality. While still in its early stages of development, fully homomorphic encryption (FHE) schemes are becoming increasingly practical. Imagine a scenario where a financial institution outsources data analysis to a cloud provider.
With homomorphic encryption, the institution can encrypt its sensitive financial data before sending it to the cloud. The cloud provider can then perform the analysis on the encrypted data, returning the results in encrypted form. The institution can then decrypt the results, ensuring data privacy throughout the entire process. This technology is expected to grow in importance as reliance on cloud services increases.
Lattice-Based Cryptography
Lattice-based cryptography is a promising area of research, offering potential solutions for both post-quantum and homomorphic encryption. Lattice-based cryptosystems are based on the mathematical properties of lattices, which are complex mathematical structures. Their perceived security against both classical and quantum attacks makes them attractive candidates for future cryptographic systems. The difficulty of solving certain lattice problems is believed to be computationally hard even for quantum computers, thus offering a potential path toward quantum-resistant encryption.
Furthermore, some lattice-based schemes offer some degree of homomorphic properties, potentially bridging the gap between security and functionality. The ongoing research and development in this field suggest that lattice-based cryptography will play an increasingly significant role in server security.
Hardware-Based Security Enhancements
Hardware security modules (HSMs) are already playing a critical role in protecting cryptographic keys, but future developments will likely involve more sophisticated hardware solutions. These advancements may include specialized processors optimized for cryptographic operations, secure enclaves within CPUs, and even quantum-resistant hardware. For example, future HSMs might incorporate countermeasures against side-channel attacks, offering more robust protection against physical tampering.
This approach will significantly improve the security of cryptographic operations by making them harder to attack even with sophisticated physical access. The integration of quantum-resistant algorithms directly into hardware will also accelerate the transition to post-quantum cryptography.
Predictions for the Next 5-10 Years
Within the next five to ten years, we can expect a significant shift towards post-quantum cryptography, with widespread adoption of NIST-standardized algorithms. The use of homomorphic encryption will likely increase, especially in cloud computing environments, enabling secure data processing without compromising privacy. Lattice-based cryptography will likely become more prevalent, offering a strong foundation for both post-quantum and homomorphic encryption.
Hardware-based security will also continue to evolve, with more sophisticated HSMs and other hardware-based security mechanisms providing stronger protection against a wider range of attacks. The overall trend will be towards more integrated, robust, and adaptable cryptographic solutions designed to withstand the evolving threat landscape, including the potential threat of quantum computing.
Ultimate Conclusion
Securing your server infrastructure requires a multi-layered approach, and cryptography forms the bedrock of this defense. By implementing the strategies and best practices Artikeld in this guide—from choosing appropriate encryption algorithms and securely managing keys to leveraging HSMs and staying ahead of emerging threats—you can significantly reduce your vulnerability to cyberattacks. Remember, proactive security is far more cost-effective than reactive remediation.
Investing in robust cryptography is not just a security measure; it’s a strategic investment in the long-term health and stability of your server environment and the data it protects.
FAQ
What are the common types of cryptographic attacks targeting servers?
Common attacks include brute-force attacks, man-in-the-middle attacks, replay attacks, and injection attacks. Understanding these attack vectors is crucial for implementing effective mitigation strategies.
How often should server cryptographic keys be rotated?
Key rotation frequency depends on the sensitivity of the data and the specific security requirements. Best practices often recommend regular rotation, at least annually, or even more frequently for highly sensitive data.
What is the difference between encryption at rest and encryption in transit?
Encryption at rest protects data stored on a server’s hard drive or other storage media. Encryption in transit protects data as it travels between servers or clients, typically using protocols like TLS/SSL.
Are HSMs necessary for all server environments?
While HSMs offer superior security, they are not always necessary. The decision to implement HSMs depends on the sensitivity of the data being protected and the organization’s risk tolerance. For high-value assets, HSMs are highly recommended.