Server Protection: Cryptography Beyond Basics delves into the critical need for robust server security in today’s ever-evolving threat landscape. Basic encryption is no longer sufficient; sophisticated attacks demand advanced techniques. This exploration will cover advanced encryption algorithms, secure communication protocols, data loss prevention strategies, and intrusion detection and prevention systems, providing a comprehensive guide to securing your servers against modern threats.
We’ll examine the practical implementation of these strategies, offering actionable steps and best practices for a more secure server environment.
From understanding the limitations of traditional encryption methods to mastering advanced techniques like PKI and HSMs, this guide provides a practical roadmap for building a resilient and secure server infrastructure. We’ll compare and contrast various approaches, highlighting their strengths and weaknesses, and providing clear, actionable advice for implementation and ongoing maintenance. The goal is to empower you with the knowledge to effectively protect your valuable data and systems.
Introduction to Server Protection
Basic encryption, while a crucial first step, offers insufficient protection against the sophisticated threats targeting modern servers. The reliance on solely encrypting data at rest or in transit overlooks the multifaceted nature of server vulnerabilities and the increasingly complex attack vectors employed by malicious actors. This section explores the limitations of basic encryption and examines the evolving threat landscape that necessitates a more comprehensive approach to server security.The limitations of basic encryption methods stem from their narrow focus.
They primarily address the confidentiality of data, ensuring only authorized parties can access it. However, modern attacks often target other aspects of server security, such as integrity, availability, and authentication. Basic encryption does little to mitigate attacks that exploit vulnerabilities in the server’s operating system, applications, or network configuration, even if the data itself is encrypted. Furthermore, the widespread adoption of basic encryption techniques has made them a predictable target, leading to the development of sophisticated countermeasures by attackers.
Evolving Threat Landscape and its Impact on Server Security Needs
The threat landscape is constantly evolving, driven by advancements in technology and the increasing sophistication of cybercriminals. The rise of advanced persistent threats (APTs), ransomware attacks, and supply chain compromises highlights the need for a multi-layered security approach that goes beyond basic encryption. APTs, for example, can remain undetected within a system for extended periods, subtly exfiltrating data even if encryption is in place.
Ransomware attacks, meanwhile, focus on disrupting services and demanding payment, often targeting vulnerabilities unrelated to encryption. Supply chain compromises exploit weaknesses in third-party software or services, potentially bypassing server-level encryption entirely. The sheer volume and complexity of these threats necessitate a move beyond simple encryption strategies.
Examples of Sophisticated Attacks Bypassing Basic Encryption
Several sophisticated attacks effectively bypass basic encryption. Consider a scenario where an attacker gains unauthorized access to a server’s administrative credentials through phishing or social engineering. Even if data is encrypted, the attacker can then decrypt it using those credentials or simply modify server configurations to disable encryption entirely. Another example is a side-channel attack, where an attacker exploits subtle variations in system performance or power consumption to extract information, even from encrypted data.
This technique bypasses the encryption algorithm itself, focusing on indirect methods of data extraction. Furthermore, attacks targeting vulnerabilities in the server’s underlying operating system or applications can lead to data breaches, regardless of whether encryption is implemented. These vulnerabilities, often exploited through zero-day exploits, can provide an attacker with complete access to the system, rendering encryption largely irrelevant.
A final example is a compromised trusted platform module (TPM), which can be exploited to circumvent the security measures that rely on hardware-based encryption.
Advanced Encryption Techniques
Server protection necessitates robust encryption strategies beyond the basics. This section delves into advanced encryption techniques, comparing symmetric and asymmetric approaches, exploring Public Key Infrastructure (PKI) implementation, and examining the crucial role of digital signatures. Finally, a hypothetical server security architecture incorporating these advanced methods will be presented.
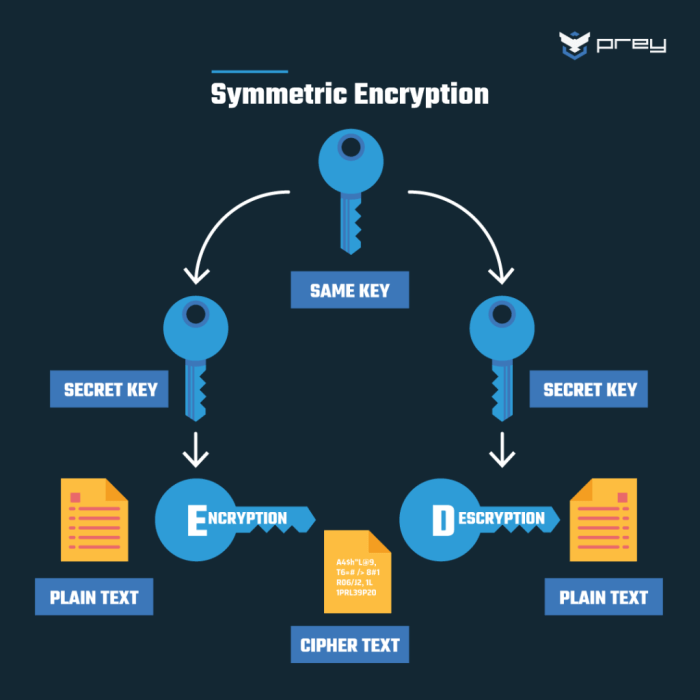
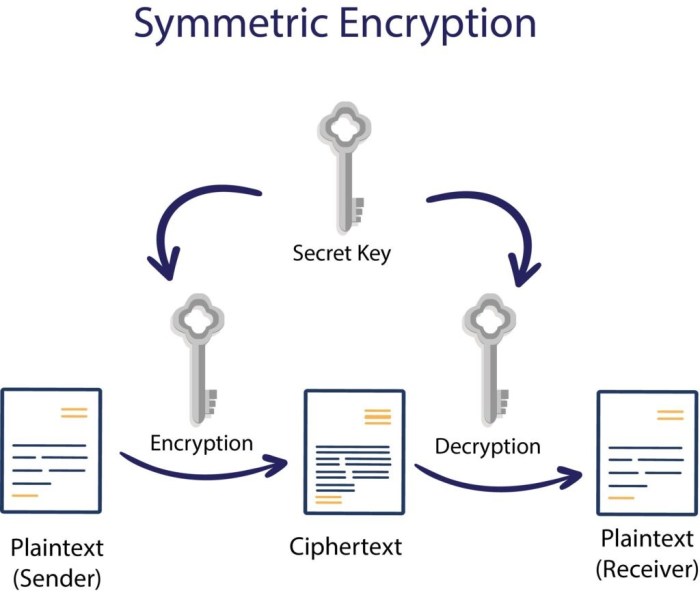
Symmetric vs. Asymmetric Encryption
Symmetric encryption uses a single, secret key for both encryption and decryption. This offers speed and efficiency, making it suitable for encrypting large datasets. However, secure key exchange presents a significant challenge. Asymmetric encryption, conversely, employs a pair of keys: a public key for encryption and a private key for decryption. This eliminates the need for secure key exchange, as the public key can be widely distributed.
However, asymmetric encryption is computationally more intensive than symmetric encryption, making it less suitable for encrypting large amounts of data. In practice, a hybrid approach is often employed, using asymmetric encryption for key exchange and symmetric encryption for data encryption. For instance, TLS/SSL uses RSA (asymmetric) for the initial handshake and AES (symmetric) for the subsequent data transfer.
Public Key Infrastructure (PKI) for Server Authentication
Public Key Infrastructure (PKI) provides a framework for managing and distributing digital certificates. These certificates bind a public key to the identity of a server, enabling clients to verify the server’s authenticity. A Certificate Authority (CA) is a trusted third party that issues and manages digital certificates. The process involves the server generating a key pair, submitting a certificate signing request (CSR) to the CA, and receiving a digitally signed certificate.
Clients can then verify the certificate’s validity by checking its chain of trust back to the root CA. This process ensures that clients are communicating with the legitimate server and not an imposter. For example, websites using HTTPS rely on PKI to ensure secure connections. The browser verifies the website’s certificate, confirming its identity before establishing a secure connection.
Digital Signatures for Data Integrity and Authenticity
Digital signatures provide a mechanism to verify the integrity and authenticity of data. They are created using the sender’s private key and can be verified using the sender’s public key. The signature is cryptographically linked to the data, ensuring that any alteration to the data will invalidate the signature. This provides assurance that the data has not been tampered with and originates from the claimed sender.
Digital signatures are widely used in various applications, including software distribution, secure email, and code signing. For instance, a software download might include a digital signature to verify its authenticity and integrity, preventing malicious code from being distributed as legitimate software.
Hypothetical Server Security Architecture
A secure server architecture could utilize a combination of advanced encryption techniques. The server could employ TLS/SSL for secure communication with clients, using RSA for the initial handshake and AES for data encryption. Server-side data could be encrypted at rest using AES-256 with strong key management practices. Digital signatures could be used to authenticate server-side software updates and verify the integrity of configuration files.
A robust PKI implementation, including a well-defined certificate lifecycle management process, would be crucial for managing digital certificates and ensuring trust. Regular security audits and penetration testing would be essential to identify and address vulnerabilities. This layered approach combines several security mechanisms to create a comprehensive and robust server protection strategy. Regular key rotation and proactive monitoring would further enhance security.
Secure Communication Protocols: Server Protection: Cryptography Beyond Basics
Secure communication protocols are fundamental to server protection, ensuring data integrity and confidentiality during transmission. These protocols employ various cryptographic techniques to establish secure channels between servers and clients, preventing eavesdropping and data manipulation. Understanding their functionalities and security features is crucial for implementing robust server security measures.
Several protocols are commonly used to secure server communication, each offering a unique set of strengths and weaknesses. The choice of protocol often depends on the specific application and security requirements.
TLS/SSL
TLS (Transport Layer Security) and its predecessor, SSL (Secure Sockets Layer), are widely used protocols for securing network connections, primarily for web traffic (HTTPS). TLS/SSL establishes an encrypted connection between a client (like a web browser) and a server, protecting data exchanged during the session. Key security features include encryption using symmetric and asymmetric cryptography, message authentication codes (MACs) for data integrity verification, and certificate-based authentication to verify the server’s identity.
This prevents man-in-the-middle attacks and ensures data confidentiality. TLS 1.3 is the current version, offering improved performance and security compared to older versions.
SSH
SSH (Secure Shell) is a cryptographic network protocol for secure remote login and other secure network services over an unsecured network. It provides strong authentication and encrypted communication, protecting sensitive information such as passwords and commands. Key security features include public-key cryptography for authentication, symmetric encryption for data confidentiality, and integrity checks to prevent data tampering. SSH is commonly used for managing servers remotely and transferring files securely.
Comparison of Secure Communication Protocols
| Protocol | Primary Use Case | Strengths | Weaknesses |
|---|---|---|---|
| TLS/SSL | Web traffic (HTTPS), other application-layer protocols | Widely supported, robust encryption, certificate-based authentication, data integrity checks | Complexity, potential vulnerabilities in older versions (e.g., TLS 1.0, 1.1), susceptible to certain attacks if not properly configured |
| SSH | Remote login, secure file transfer, secure remote command execution | Strong authentication, robust encryption, excellent for command-line interactions, widely supported | Can be complex to configure, potential vulnerabilities if not updated regularly, less widely used for application-layer protocols compared to TLS/SSL |
Data Loss Prevention (DLP) Strategies
Data Loss Prevention (DLP) is critical for maintaining the confidentiality, integrity, and availability of server data. Effective DLP strategies encompass a multi-layered approach, combining technical safeguards with robust operational procedures. This section details key DLP strategies focusing on data encryption, both at rest and in transit, and Artikels a practical implementation procedure.Data encryption, a cornerstone of DLP, transforms readable data into an unreadable format, rendering it inaccessible to unauthorized individuals.
This protection is crucial both when data is stored (at rest) and while it’s being transmitted (in transit). Effective DLP necessitates a comprehensive strategy encompassing both aspects.
Data Encryption at Rest
Data encryption at rest protects data stored on server hard drives, SSDs, and other storage media. This involves encrypting data before it is written to storage and decrypting it only when accessed by authorized users. Strong encryption algorithms, such as AES-256, are essential for robust protection. Implementation typically involves configuring the operating system or storage system to encrypt data automatically.
Regular key management and rotation are vital to mitigate the risk of key compromise. Examples include using BitLocker for Windows servers or FileVault for macOS servers. These built-in tools provide strong encryption at rest.
Data Encryption in Transit
Data encryption in transit protects data while it’s being transmitted over a network. This is crucial for preventing eavesdropping and data breaches during data transfer between servers, clients, and other systems. Secure protocols like HTTPS, SSH, and SFTP encrypt data using strong encryption algorithms, ensuring confidentiality and integrity during transmission. Implementing TLS/SSL certificates for web servers and using SSH for remote server access are essential practices.
Regular updates and patching of server software are critical to maintain the security of these protocols and to protect against known vulnerabilities.
Implementing Robust DLP Measures: A Step-by-Step Procedure
Implementing robust DLP measures requires a structured approach. The following steps Artikel a practical procedure:
- Conduct a Data Risk Assessment: Identify sensitive data stored on the server and assess the potential risks associated with its loss or unauthorized access.
- Define Data Classification Policies: Categorize data based on sensitivity levels (e.g., confidential, internal, public) to guide DLP implementation.
- Implement Data Encryption: Encrypt data at rest and in transit using strong encryption algorithms and secure protocols as described above.
- Establish Access Control Measures: Implement role-based access control (RBAC) to restrict access to sensitive data based on user roles and responsibilities.
- Implement Data Loss Prevention Tools: Consider deploying DLP software to monitor and prevent data exfiltration attempts.
- Regularly Monitor and Audit: Monitor system logs and audit access to sensitive data to detect and respond to security incidents promptly.
- Employee Training and Awareness: Educate employees about data security best practices and the importance of DLP.
Data Backup and Recovery Best Practices
Regular data backups are crucial for business continuity and disaster recovery. A robust backup and recovery strategy is an essential component of a comprehensive DLP strategy. Best practices include:
- Implement a 3-2-1 backup strategy: Maintain three copies of data, on two different media types, with one copy stored offsite.
- Regularly test backups: Periodically restore data from backups to ensure their integrity and recoverability.
- Use immutable backups: Employ backup solutions that prevent backups from being altered or deleted, enhancing data protection against ransomware attacks.
- Establish a clear recovery plan: Define procedures for data recovery in case of a disaster or security incident.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) are crucial components of a robust server security strategy. They act as the first line of defense against malicious activities targeting servers, providing real-time monitoring and automated responses to threats. Understanding their functionality and effective configuration is vital for maintaining server integrity and data security.IDPS encompasses two distinct but related technologies: Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS).
While both monitor network traffic and server activity for suspicious patterns, their responses differ significantly. IDS primarily focuses on identifying and reporting malicious activity, while IPS actively prevents or mitigates these threats in real-time.
Intrusion Detection System (IDS) Functionality
An IDS passively monitors network traffic and server logs for suspicious patterns indicative of intrusion attempts. This monitoring involves analyzing various data points, including network packets, system calls, and user activities. Upon detecting anomalies or known attack signatures, the IDS generates alerts, notifying administrators of potential threats. These alerts typically contain details about the detected event, its severity, and the affected system.
Effective IDS deployment relies on accurate signature databases and robust anomaly detection algorithms. False positives, while a concern, can be minimized through fine-tuning and careful configuration. For example, an IDS might detect a large number of failed login attempts from a single IP address, a strong indicator of a brute-force attack.
Intrusion Prevention System (IPS) Functionality
Unlike an IDS, an IPS actively intervenes to prevent or mitigate detected threats. Upon identifying a malicious activity, an IPS can take various actions, including blocking malicious traffic, resetting connections, and modifying firewall rules. This proactive approach significantly reduces the impact of successful attacks. For instance, an IPS could block an incoming connection attempting to exploit a known vulnerability before it can compromise the server.
The ability to actively prevent attacks makes IPS a more powerful security tool compared to IDS, although it also carries a higher risk of disrupting legitimate traffic if not properly configured.
IDPS Configuration and Deployment Best Practices
Effective IDPS deployment requires careful planning and configuration. This involves selecting the appropriate IDPS solution based on the specific needs and resources of the organization. Key considerations include the type of IDPS (network-based, host-based, or cloud-based), the scalability of the solution, and its integration with existing security infrastructure. Furthermore, accurate signature updates are crucial for maintaining the effectiveness of the IDPS against emerging threats.
Regular testing and fine-tuning are essential to minimize false positives and ensure that the system accurately identifies and responds to threats. Deployment should also consider the placement of sensors to maximize coverage and minimize blind spots within the network. Finally, a well-defined incident response plan is necessary to effectively handle alerts and mitigate the impact of detected intrusions.
Comparing IDS and IPS
The following table summarizes the key differences between IDS and IPS:
| Feature | IDS | IPS |
|---|---|---|
| Functionality | Detects and reports intrusions | Detects and prevents intrusions |
| Response | Generates alerts | Blocks traffic, resets connections, modifies firewall rules |
| Impact on network performance | Minimal | Potentially higher due to active intervention |
| Complexity | Generally less complex to configure | Generally more complex to configure |
Vulnerability Management and Patching
Proactive vulnerability management and timely patching are critical for maintaining the security of server environments. Neglecting these crucial aspects can expose servers to significant risks, leading to data breaches, system compromises, and substantial financial losses. A robust vulnerability management program involves identifying potential weaknesses, prioritizing their remediation, and implementing a rigorous patching schedule.Regular security patching and updates are essential to mitigate the impact of known vulnerabilities.
Exploitable flaws are constantly discovered in software and operating systems, and attackers actively seek to exploit these weaknesses. By promptly applying patches, organizations significantly reduce their attack surface and protect their servers from known threats. This process, however, must be carefully managed to avoid disrupting essential services.
Common Server Vulnerabilities and Their Impact
Common server vulnerabilities stem from various sources, including outdated software, misconfigurations, and insecure coding practices. For example, unpatched operating systems are susceptible to exploits that can grant attackers complete control over the server. Similarly, misconfigured databases can expose sensitive data to unauthorized access. The impact of these vulnerabilities can range from minor disruptions to catastrophic data breaches and significant financial losses, including regulatory fines and reputational damage.
A vulnerability in a web server, for instance, could lead to unauthorized access to customer data, resulting in substantial legal and financial repercussions. A compromised email server could enable phishing campaigns or the dissemination of malware, affecting both the organization and its clients.
Creating a Security Patching Schedule, Server Protection: Cryptography Beyond Basics
A well-defined security patching schedule is vital for efficient and effective vulnerability management. This schedule should encompass all servers within the organization’s infrastructure, including operating systems, applications, and databases. Prioritization should be based on factors such as criticality, risk exposure, and potential impact. Critical systems should receive patches immediately upon release, while less critical systems can be updated on a more regular basis, perhaps monthly or quarterly.
A rigorous testing phase should precede deployment to avoid unintended consequences. For example, a financial institution might prioritize patching vulnerabilities in its transaction processing system above those in a less critical internal communications server. The schedule should also incorporate regular vulnerability scans to identify and address any newly discovered vulnerabilities not covered by existing patches. Regular backups are also crucial to ensure data recovery in case of unexpected issues during patching.
Vulnerability Scanning and Remediation Process
The vulnerability scanning and remediation process involves systematically identifying, assessing, and mitigating security weaknesses. This process typically begins with automated vulnerability scans using specialized tools that analyze server configurations and software for known vulnerabilities. These scans produce reports detailing identified vulnerabilities, their severity, and potential impact. Following the scan, a thorough risk assessment is performed to prioritize vulnerabilities based on their potential impact and likelihood of exploitation.
Prioritization guides the remediation process, focusing efforts on the most critical vulnerabilities first. Remediation involves applying patches, updating software, modifying configurations, or implementing other security controls. After remediation, a follow-up scan is conducted to verify the effectiveness of the applied fixes. The entire process should be documented, enabling tracking of vulnerabilities, remediation efforts, and the overall effectiveness of the vulnerability management program.
For example, a company might use Nessus or OpenVAS for vulnerability scanning, prioritizing vulnerabilities with a CVSS score above 7.0 for immediate remediation.
Access Control and Authentication
Securing a server necessitates a robust access control and authentication system. This system dictates who can access the server and what actions they are permitted to perform, forming a critical layer of defense against unauthorized access and data breaches. Effective implementation requires a thorough understanding of various authentication methods and the design of a granular permission structure.Authentication methods verify the identity of a user attempting to access the server.
Different methods offer varying levels of security and convenience.
Comparison of Authentication Methods
Password-based authentication, while widely used, is susceptible to brute-force attacks and phishing scams. Multi-factor authentication (MFA), on the other hand, adds layers of verification, typically requiring something the user knows (password), something the user has (e.g., a security token or smartphone), and/or something the user is (biometric data like a fingerprint). MFA significantly enhances security by making it exponentially harder for attackers to gain unauthorized access even if they compromise a password.
Other methods include certificate-based authentication, using digital certificates to verify user identities, and token-based authentication, often employed in API interactions, where short-lived tokens grant temporary access. The choice of authentication method should depend on the sensitivity of the data and the level of security required.
Designing a Robust Access Control System
A well-designed access control system employs the principle of least privilege, granting users only the necessary permissions to perform their tasks. This minimizes the potential damage from compromised accounts. For example, a server administrator might require full access, while a database administrator would only need access to the database. A typical system would define roles (e.g., administrator, developer, user) and assign specific permissions to each role.
Permissions could include reading, writing, executing, and deleting files, accessing specific directories, or running particular commands. The system should also incorporate auditing capabilities to track user activity and detect suspicious behavior. Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) are common frameworks for implementing such systems. RBAC uses roles to assign permissions, while ABAC allows for more fine-grained control based on attributes of the user, resource, and environment.
Best Practices for Managing User Accounts and Passwords
Strong password policies are essential. These policies should mandate complex passwords, including a mix of uppercase and lowercase letters, numbers, and symbols, and enforce regular password changes. Password managers can assist users in creating and managing strong, unique passwords for various accounts. Regular account audits should be conducted to identify and disable inactive or compromised accounts. Implementing multi-factor authentication (MFA) for all user accounts is a critical best practice.
This significantly reduces the risk of unauthorized access even if passwords are compromised. Regular security awareness training for users helps educate them about phishing attacks and other social engineering techniques. The principle of least privilege should be consistently applied, ensuring that users only have the necessary permissions to perform their job functions. Regularly reviewing and updating access control policies and procedures ensures the system remains effective against evolving threats.
Security Auditing and Monitoring
Regular security audits and comprehensive server logging are paramount for maintaining robust server protection. These processes provide crucial insights into system activity, enabling proactive identification and mitigation of potential security threats before they escalate into significant breaches. Without consistent monitoring and auditing, vulnerabilities can remain undetected, leaving systems exposed to exploitation.Effective security auditing and monitoring involves a multi-faceted approach encompassing regular assessments, detailed log analysis, and well-defined incident response procedures.
This proactive strategy allows organizations to identify weaknesses, address vulnerabilities, and react swiftly to security incidents, minimizing potential damage and downtime.
Server Log Analysis Techniques
Analyzing server logs is critical for identifying security incidents. Logs contain a wealth of information regarding user activity, system processes, and security events. Effective analysis requires understanding the different log types (e.g., system logs, application logs, security logs) and using appropriate tools to search, filter, and correlate log entries. Looking for unusual patterns, such as repeated failed login attempts from unusual IP addresses or large-scale file transfers outside of normal business hours, are key indicators of potential compromise.
The use of Security Information and Event Management (SIEM) systems can significantly enhance the efficiency of this process by automating log collection, analysis, and correlation. For example, a SIEM system might alert administrators to a sudden surge in failed login attempts from a specific geographic location, indicating a potential brute-force attack.
Planning for Regular Security Audits
A well-defined plan for regular security audits is essential. This plan should detail the scope of each audit, the frequency of audits, the methodologies to be employed, and the individuals responsible for conducting and reviewing the audits. The plan should also specify how audit findings will be documented, prioritized, and remediated. A sample audit plan might involve quarterly vulnerability scans, annual penetration testing, and regular reviews of access control policies.
Prioritization of findings should consider factors like the severity of the vulnerability, the likelihood of exploitation, and the potential impact on the organization. For example, a critical vulnerability affecting a core system should be addressed immediately, while a low-severity vulnerability in a non-critical system might be scheduled for remediation in a future update.
Incident Response Procedures
Establishing clear and comprehensive incident response procedures is vital for effective server protection. These procedures should Artikel the steps to be taken in the event of a security incident, including incident identification, containment, eradication, recovery, and post-incident activity. The procedures should also define roles and responsibilities, escalation paths, and communication protocols. For example, a procedure might involve immediately isolating an affected server, launching a forensic investigation to determine the cause and extent of the breach, restoring data from backups, and implementing preventative measures to avoid future incidents.
Regular testing and updates of these procedures are essential to ensure their effectiveness in real-world scenarios. Simulations and tabletop exercises can help organizations identify weaknesses in their incident response capabilities and refine their procedures accordingly.
Hardware Security Modules (HSMs)
Hardware Security Modules (HSMs) are physical computing devices designed to protect cryptographic keys and perform cryptographic operations securely. They offer a significantly higher level of security compared to software-based solutions by isolating sensitive cryptographic materials from the potentially vulnerable environment of a standard server. This isolation protects keys from theft, unauthorized access, and compromise, even if the server itself is compromised.HSMs provide several key benefits for enhanced server security.
Their dedicated hardware architecture, tamper-resistant design, and secure operating environments ensure that cryptographic operations are performed in a trusted and isolated execution space. This protects against various attacks, including malware, operating system vulnerabilities, and even physical attacks. The secure key management capabilities offered by HSMs are critical for protecting sensitive data and maintaining the confidentiality, integrity, and availability of server systems.
HSM Functionality and Benefits
HSMs offer a range of cryptographic functionalities, including key generation, storage, and management; digital signature creation and verification; encryption and decryption; and secure hashing. The benefits extend beyond simply storing keys; HSMs actively manage the entire key lifecycle, ensuring proper generation, rotation, and destruction of keys according to security best practices. This automated key management reduces the risk of human error and simplifies compliance with various regulatory standards.
Furthermore, the tamper-resistant nature of HSMs provides a high degree of assurance that cryptographic keys remain protected, even in the event of physical theft or unauthorized access. The physical security features, such as tamper-evident seals and intrusion detection systems, further enhance the protection of sensitive cryptographic assets.
Scenarios Benefiting from HSMs
HSMs are particularly beneficial in scenarios requiring high levels of security and compliance. For instance, in the financial services industry, HSMs are crucial for securing payment processing systems and protecting sensitive customer data. They are also essential for organizations handling sensitive personal information, such as healthcare providers and government agencies, where data breaches could have severe consequences. E-commerce platforms also rely heavily on HSMs to secure online transactions and protect customer payment information.
In these high-stakes environments, the enhanced security and tamper-resistance of HSMs are invaluable. Consider a scenario where a bank uses HSMs to protect its cryptographic keys used for online banking. Even if a sophisticated attacker compromises the bank’s servers, the keys stored within the HSM remain inaccessible, preventing unauthorized access to customer accounts and financial data.
Comparison of HSMs and Software-Based Key Management
Software-based key management solutions, while more cost-effective, lack the robust physical security and isolation provided by HSMs. Software-based solutions are susceptible to various attacks, including malware infections and operating system vulnerabilities, potentially compromising the security of stored cryptographic keys. HSMs, on the other hand, offer a significantly higher level of security by physically isolating the keys and cryptographic operations from the server’s environment.
While software-based solutions may suffice for less sensitive applications, HSMs are the preferred choice for critical applications requiring the highest level of security and regulatory compliance. The increased cost of HSMs is justified by the reduced risk of data breaches and the substantial financial and reputational consequences associated with such events. A comparison could be drawn between using a high-security safe for valuable jewelry (HSM) versus simply locking it in a drawer (software-based solution).
The safe offers far greater protection against theft and damage.
The Future of Server Protection Cryptography
The landscape of server security is constantly evolving, driven by the increasing sophistication of cyber threats and the rapid advancement of cryptographic techniques. The future of server protection hinges on the continued development and implementation of robust cryptographic methods, alongside proactive strategies to address emerging challenges. This section explores key trends, potential hurdles, and predictions shaping the future of server security cryptography.
Post-Quantum Cryptography
The advent of quantum computing poses a significant threat to current cryptographic systems. Quantum computers, with their immense processing power, have the potential to break widely used algorithms like RSA and ECC, rendering current encryption methods obsolete. Post-quantum cryptography (PQC) focuses on developing algorithms resistant to attacks from both classical and quantum computers. The National Institute of Standards and Technology (NIST) has been leading the effort to standardize PQC algorithms, with several candidates currently under consideration.
The transition to PQC will require significant effort in updating infrastructure and software, ensuring compatibility and interoperability across systems. Successful implementation will rely on collaborative efforts between researchers, developers, and organizations to facilitate a smooth and secure migration.
Server protection relies heavily on robust cryptographic methods, going beyond simple encryption. To truly understand the evolving landscape of server security, it’s crucial to explore the advancements discussed in Cryptography: The Future of Server Security. This deeper understanding informs the development of more resilient and adaptable security protocols for your servers, ultimately strengthening your overall protection strategy.
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on encrypted data without decryption, preserving confidentiality while enabling data analysis and processing. This technology has immense potential in cloud computing, enabling secure data sharing and collaboration without compromising privacy. While still in its early stages of development, advancements in homomorphic encryption are paving the way for more secure and efficient data processing in various applications, including healthcare, finance, and government.
For example, medical researchers could analyze sensitive patient data without accessing the underlying information, accelerating research while maintaining patient privacy.
Advances in Lightweight Cryptography
The increasing prevalence of Internet of Things (IoT) devices and embedded systems necessitates lightweight cryptographic algorithms. These algorithms are designed to be efficient in terms of computational resources and energy consumption, making them suitable for resource-constrained devices. Advancements in lightweight cryptography are crucial for securing these devices, which are often vulnerable to attacks due to their limited processing capabilities and security features.
Examples include the development of optimized algorithms for resource-constrained environments, and the integration of hardware-based security solutions to enhance the security of these devices.
Challenges and Opportunities
The future of server protection cryptography faces several challenges, including the complexity of implementing new algorithms, the need for widespread adoption, and the potential for new vulnerabilities to emerge. However, there are also significant opportunities. The development of more efficient and robust cryptographic techniques can enhance the security of various applications, enabling secure data sharing and collaboration. Furthermore, advancements in cryptography can drive innovation in areas such as blockchain technology, secure multi-party computation, and privacy-preserving machine learning.
The successful navigation of these challenges and the realization of these opportunities will require continued research, development, and collaboration among researchers, industry professionals, and policymakers.
Predictions for the Future of Server Security
Within the next decade, we can anticipate widespread adoption of post-quantum cryptography, particularly in critical infrastructure and government systems. Homomorphic encryption will likely see increased adoption in specific niche applications, driven by the demand for secure data processing and analysis. Lightweight cryptography will become increasingly important as the number of IoT devices continues to grow. Furthermore, we can expect a greater emphasis on integrated security solutions, combining hardware and software approaches to enhance server protection.
The development of new cryptographic techniques and the evolution of existing ones will continue to shape the future of server security, ensuring the protection of sensitive data in an increasingly interconnected world. For instance, the increasing use of AI in cybersecurity will likely lead to the development of more sophisticated threat detection and response systems, leveraging advanced cryptographic techniques to protect against evolving cyber threats.
End of Discussion
Securing your servers requires a multifaceted approach extending beyond basic encryption. This exploration of Server Protection: Cryptography Beyond Basics has highlighted the critical need for advanced encryption techniques, secure communication protocols, robust data loss prevention strategies, and proactive intrusion detection and prevention systems. By implementing the strategies and best practices discussed, you can significantly enhance your server security posture, mitigating the risks associated with increasingly sophisticated cyber threats.
Regular security audits, vulnerability management, and a commitment to continuous improvement are essential for maintaining a secure and reliable server environment in the long term. The future of server security relies on adapting to evolving threats and embracing innovative cryptographic solutions.
Question & Answer Hub
What are some common server vulnerabilities that can be exploited?
Common vulnerabilities include outdated software, weak passwords, misconfigured firewalls, and insecure coding practices. These can lead to unauthorized access, data breaches, and system compromise.
How often should I update my server’s security patches?
Security patches should be applied as soon as they are released. Regular updates are crucial for mitigating known vulnerabilities.
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption.
How can I choose the right encryption algorithm for my server?
Algorithm selection depends on your specific security needs and the sensitivity of your data. Consult industry best practices and consider factors like performance and key length.