Cryptographic Keys: Your Server’s Defense Mechanism – this seemingly technical phrase underpins the entire security of your digital infrastructure. Understanding how cryptographic keys work, how they’re managed, and the potential consequences of compromise is crucial for anyone responsible for server security. This exploration delves into the different types of keys, secure key generation and management practices, and the critical role they play in protecting sensitive data from unauthorized access.
We’ll examine various encryption algorithms, key exchange protocols, and explore strategies for mitigating the impact of a compromised key, including the implications of emerging technologies like quantum computing.
We’ll cover everything from the fundamental principles of symmetric and asymmetric encryption to advanced key management systems and the latest advancements in post-quantum cryptography. This detailed guide provides a comprehensive overview, equipping you with the knowledge to effectively secure your server environment.
Introduction to Cryptographic Keys
Cryptographic keys are fundamental to securing server data and ensuring the confidentiality, integrity, and authenticity of information exchanged between systems. They act as the gatekeepers, controlling access to encrypted data and verifying the legitimacy of communications. Without robust key management, even the most sophisticated encryption algorithms are vulnerable. Understanding the different types of keys and their applications is crucial for effective server security.Cryptographic keys are essentially strings of random characters that are used in mathematical algorithms to encrypt and decrypt data.
These algorithms are designed to be computationally infeasible to break without possessing the correct key. The strength of the encryption directly relies on the key’s length, randomness, and the security of its management. Breaching this security, whether through theft or compromise, can lead to devastating consequences, including data breaches and system compromises.
Symmetric Keys
Symmetric key cryptography uses a single secret key for both encryption and decryption. This means the same key is used to scramble the data and unscramble it. The key must be securely shared between the sender and receiver. Examples of symmetric key algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES), though DES is now considered insecure due to its relatively short key length.
Symmetric encryption is generally faster than asymmetric encryption, making it suitable for encrypting large amounts of data, such as files or databases stored on a server. For instance, a server might use AES to encrypt user data at rest, ensuring that even if the server’s hard drive is stolen, the data remains inaccessible without the decryption key.
Asymmetric Keys
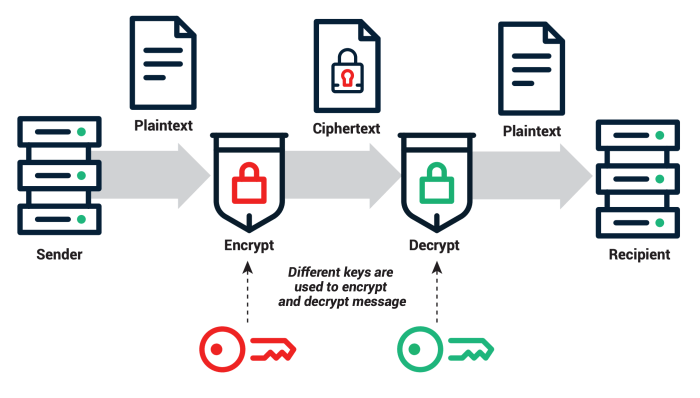
Asymmetric key cryptography, also known as public-key cryptography, uses a pair of keys: a public key and a private key. The public key can be freely distributed, while the private key must be kept secret. Data encrypted with the public key can only be decrypted with the corresponding private key, and vice-versa. This eliminates the need to share a secret key securely, a significant advantage over symmetric key cryptography.
RSA and ECC (Elliptic Curve Cryptography) are widely used asymmetric key algorithms. Asymmetric keys are commonly used for digital signatures, verifying the authenticity of data, and for secure key exchange in establishing secure communication channels like SSL/TLS connections. For example, a web server uses an asymmetric key pair for HTTPS. The server’s public key is embedded in the SSL certificate, allowing clients to securely connect and exchange symmetric keys for faster data encryption during the session.
Key Management
The secure generation, storage, and distribution of cryptographic keys are paramount to the effectiveness of any encryption system. Poor key management practices are a major source of security vulnerabilities. Key management involves several aspects: key generation using cryptographically secure random number generators, secure storage using hardware security modules (HSMs) or other secure methods, regular key rotation to limit the impact of a potential compromise, and secure key distribution using protocols like Diffie-Hellman.
Failure to adequately manage keys can render the entire encryption system ineffective, potentially exposing sensitive server data to attackers. For example, if a server uses a weak random number generator for key generation, an attacker might be able to guess the keys and compromise the security of the server.
Key Generation and Management: Cryptographic Keys: Your Server’s Defense Mechanism

Robust cryptographic key generation and management are paramount for maintaining the security of any server. Compromised keys can lead to devastating data breaches and system failures. Therefore, employing secure practices throughout the key lifecycle – from generation to eventual decommissioning – is non-negotiable. This section details best practices for ensuring cryptographic keys remain confidential and trustworthy.
Secure Key Generation Methods
Generating cryptographically secure keys requires a process free from bias or predictability. Weakly generated keys are easily guessed or cracked, rendering encryption useless. Strong keys should be generated using cryptographically secure pseudo-random number generators (CSPRNGs). These algorithms leverage sources of entropy, such as hardware-based random number generators or operating system-level randomness sources, to produce unpredictable sequences of bits.
Avoid using simple algorithms or readily available pseudo-random number generators found in programming libraries, as these may not provide sufficient entropy and may be susceptible to attacks. The length of the key is also crucial; longer keys offer significantly greater resistance to brute-force attacks. The key length should align with the chosen cryptographic algorithm and the desired security level.
For example, AES-256 requires a 256-bit key, providing substantially stronger security than AES-128.
Key Storage and Protection
Once generated, keys must be stored securely to prevent unauthorized access. Storing keys directly on the server’s file system is highly discouraged due to vulnerabilities to malware and operating system compromises. A superior approach involves utilizing hardware security modules (HSMs). HSMs are dedicated cryptographic processing units that securely store and manage cryptographic keys. They offer tamper-resistant hardware and specialized security features, making them far more resilient to attacks than software-based solutions.
Even with HSMs, strong access control mechanisms, including role-based access control and multi-factor authentication, are essential to limit access to authorized personnel only. Regular security audits and vulnerability assessments should be conducted to identify and address any potential weaknesses in the key storage infrastructure.
Key Rotation Procedures, Cryptographic Keys: Your Server’s Defense Mechanism
Regular key rotation is a critical security practice that mitigates the risk of long-term key compromise. If a key is compromised, the damage is limited to the period it was in use. A well-defined key rotation schedule should be established and strictly adhered to. The frequency of rotation depends on the sensitivity of the data being protected and the risk tolerance of the organization.
Strong cryptographic keys are the bedrock of server security, protecting sensitive data from unauthorized access. Building a robust security posture requires understanding these fundamental elements, much like scaling a podcast requires a strategic approach; check out this guide on 5 Trik Rahasia Podcast Growth: 5000 Listener/Episode for insights into effective growth strategies. Ultimately, both server security and podcast success hinge on planning and execution of a solid strategy.
For highly sensitive data, more frequent rotation (e.g., monthly or even weekly) might be necessary. During rotation, the old key is securely decommissioned and replaced with a newly generated key. The process should be automated as much as possible to reduce the risk of human error. Detailed logging and auditing of all key rotation activities are essential for compliance and forensic analysis.
Comparison of Key Management Systems
The choice of key management system depends on the specific security requirements and resources of an organization. Below is a comparison of several common systems. Note that specific implementations and features can vary considerably between vendors and versions.
| System Name | Key Generation Method | Key Storage Method | Key Rotation Frequency |
|---|---|---|---|
| HSM (e.g., Thales, SafeNet) | CSPRNG within HSM | Dedicated hardware within HSM | Variable, often monthly or annually |
| Cloud KMS (e.g., AWS KMS, Azure Key Vault, Google Cloud KMS) | Cloud provider’s CSPRNG | Cloud provider’s secure storage | Configurable, often monthly or annually |
| Open-source Key Management System (e.g., HashiCorp Vault) | Configurable, often using CSPRNGs | Database or file system (with encryption) | Configurable, depends on implementation |
| Self-managed Key Management System | CSPRNG (requires careful selection and implementation) | Secure server (with strict access controls) | Configurable, requires careful planning |
Key Exchange and Distribution
Securely exchanging and distributing cryptographic keys is paramount to the integrity of any server environment. Failure in this process renders even the strongest encryption algorithms vulnerable. This section delves into the methods and challenges associated with this critical aspect of server security. We’ll explore established protocols and examine the complexities involved in distributing keys across multiple servers.The process of securely exchanging keys between two parties without a pre-shared secret is a fundamental challenge in cryptography.
Several protocols have been developed to address this, leveraging mathematical principles to achieve secure key establishment. The inherent difficulty lies in ensuring that only the intended recipients possess the exchanged key, preventing eavesdropping or manipulation by malicious actors.
Diffie-Hellman Key Exchange
The Diffie-Hellman key exchange is a widely used method for establishing a shared secret key over an insecure channel. It leverages the mathematical properties of modular arithmetic to achieve this. Both parties agree on a public prime number (p) and a generator (g). Each party then generates a private key (a and b respectively) and calculates a public key (A and B respectively) using the formula: A = g a mod p and B = g b mod p.
These public keys are exchanged. The shared secret key is then calculated independently by both parties using the formula: S = B a mod p = A b mod p. The security of this protocol relies on the computational difficulty of the discrete logarithm problem. A man-in-the-middle attack is a significant threat; therefore, authentication mechanisms are crucial to ensure the identity of communicating parties.
Challenges in Secure Key Distribution to Multiple Servers
Distributing keys securely to numerous servers introduces significant complexities. A central authority managing all keys becomes a single point of failure and a tempting target for attackers. Furthermore, the process of securely distributing and updating keys across a large network demands robust and scalable solutions. The risk of key compromise increases proportionally with the number of servers and the frequency of key updates.
Maintaining consistency and preventing unauthorized access across the entire network becomes a substantial operational challenge.
Comparison of Key Distribution Methods
Several methods exist for key distribution, each with its strengths and weaknesses. Symmetric key distribution, using a pre-shared secret key, is simple but requires a secure initial channel for key exchange. Asymmetric key distribution, using public-key cryptography, avoids the need for a secure initial channel but can be computationally more expensive. Key distribution centers offer centralized management but introduce a single point of failure.
Hierarchical key distribution structures offer a more robust and scalable approach, delegating key management responsibilities to reduce the risk associated with a central authority.
Secure Key Distribution Protocol for a Hypothetical Server Environment
Consider a hypothetical server environment comprising multiple web servers, database servers, and application servers. A hybrid approach combining hierarchical key distribution and public-key cryptography could provide a robust solution. A root key is stored securely, perhaps using a hardware security module (HSM). This root key is used to encrypt a set of intermediate keys, one for each server type (web servers, database servers, etc.).
Each server type’s intermediate key is then used to encrypt individual keys for each server within that type. Servers use their individual keys to encrypt communication with each other. Public key infrastructure (PKI) can be utilized for secure communication and authentication during the key distribution process. Regular key rotation and robust auditing mechanisms are essential components of this system.
This hierarchical structure limits the impact of a compromise, as the compromise of one server’s key does not necessarily compromise the entire system.
Key Usage and Encryption Algorithms
Cryptographic keys are the cornerstone of secure communication and data protection. Their effectiveness hinges entirely on the strength of the encryption algorithms that utilize them. Understanding these algorithms and their interplay with keys is crucial for implementing robust security measures. This section explores common encryption algorithms, their key usage, and the critical relationship between key length and overall security.Encryption algorithms employ cryptographic keys to transform plaintext (readable data) into ciphertext (unreadable data).
The process is reversible; the same algorithm, along with the correct key, decrypts the ciphertext back to plaintext. Different algorithms utilize keys in varying ways, impacting their speed, security, and suitability for different applications.
Common Encryption Algorithms and Key Usage
Symmetric encryption algorithms, like AES, use the same key for both encryption and decryption. For example, in AES-256, a 256-bit key is used to encrypt data. The same 256-bit key is then required to decrypt the resulting ciphertext. Asymmetric encryption algorithms, such as RSA, utilize a pair of keys: a public key for encryption and a private key for decryption.
A sender encrypts a message using the recipient’s public key, and only the recipient, possessing the corresponding private key, can decrypt it. This asymmetry is fundamental for secure key exchange and digital signatures. The RSA algorithm’s security relies on the computational difficulty of factoring large numbers.
Key Length and Security
The length of a cryptographic key directly impacts its security. Longer keys offer a significantly larger keyspace—the set of all possible keys. A larger keyspace makes brute-force attacks (trying every possible key) computationally infeasible. For example, a 128-bit AES key has a keyspace of 2 128 possible keys, while a 256-bit key has a keyspace of 2 256, which is exponentially larger and far more resistant to brute-force attacks.
Advances in computing power and the development of more sophisticated cryptanalysis techniques necessitate the use of longer keys to maintain a sufficient level of security over time. For instance, while AES-128 was once considered sufficient, AES-256 is now generally recommended for applications requiring long-term security.
Strengths and Weaknesses of Encryption Algorithms
Understanding the strengths and weaknesses of different encryption algorithms is vital for selecting the appropriate algorithm for a given application. The choice depends on factors like security requirements, performance needs, and the type of data being protected.
The following table summarizes some key characteristics:
| Algorithm | Type | Key Length (common) | Strengths | Weaknesses |
|---|---|---|---|---|
| AES | Symmetric | 128, 192, 256 bits | Fast, widely used, robust against known attacks | Vulnerable to side-channel attacks if not implemented carefully |
| RSA | Asymmetric | 1024, 2048, 4096 bits | Suitable for key exchange and digital signatures | Slower than symmetric algorithms, key length needs to be carefully chosen to resist factoring attacks |
| ECC (Elliptic Curve Cryptography) | Asymmetric | Variable, often smaller than RSA for comparable security | Provides comparable security to RSA with shorter key lengths, faster performance | Less widely deployed than RSA, susceptible to specific attacks if not implemented correctly |
Key Compromise and Mitigation
The compromise of a cryptographic key represents a significant security breach, potentially leading to data theft, system disruption, and reputational damage. The severity depends on the type of key compromised (symmetric, asymmetric, or hashing), its intended use, and the sensitivity of the data it protects. Understanding the implications of a compromise and implementing robust mitigation strategies are crucial for maintaining data integrity and system security.The implications of a compromised cryptographic key are far-reaching.
For example, a compromised symmetric key used for encrypting sensitive financial data could result in the theft of millions of dollars. Similarly, a compromised asymmetric private key used for digital signatures could lead to fraudulent transactions or the distribution of malicious software. The impact extends beyond immediate financial loss; rebuilding trust with customers and partners after a key compromise can be a lengthy and costly process.
Implications of Key Compromise
A compromised cryptographic key allows unauthorized access to encrypted data or the ability to forge digital signatures. This can lead to several serious consequences:
- Data breaches: Unauthorized access to sensitive information, including personal data, financial records, and intellectual property.
- Financial losses: Theft of funds, fraudulent transactions, and costs associated with remediation efforts.
- Reputational damage: Loss of customer trust and potential legal liabilities.
- System disruption: Compromised keys can render systems inoperable or vulnerable to further attacks.
- Regulatory penalties: Non-compliance with data protection regulations can result in significant fines.
Key Compromise Detection Methods
Detecting a key compromise can be challenging, requiring a multi-layered approach. Effective detection relies on proactive monitoring and analysis of system logs and security events.
- Log analysis: Regularly reviewing system logs for unusual activity, such as unauthorized access attempts or unexpected encryption/decryption operations, can provide early warnings of potential compromises.
- Intrusion detection systems (IDS): IDS can monitor network traffic for suspicious patterns and alert administrators to potential attacks targeting cryptographic keys.
- Security Information and Event Management (SIEM): SIEM systems correlate data from multiple sources to provide a comprehensive view of security events, facilitating the detection of key compromise attempts.
- Anomaly detection: Algorithms can identify unusual patterns in key usage or system behavior that might indicate a compromise. For example, a sudden spike in encryption/decryption operations could be a red flag.
- Regular security audits: Independent audits can help identify vulnerabilities and weaknesses in key management practices that could lead to compromises.
Key Compromise Mitigation Strategies
Responding effectively to a suspected key compromise requires a well-defined incident response plan. This plan should Artikel clear procedures for containing the breach, investigating its cause, and recovering from its impact.
- Immediate key revocation: Immediately revoke the compromised key to prevent further unauthorized access. This involves updating all systems and applications that use the key.
- Incident investigation: Conduct a thorough investigation to determine the extent of the compromise, identify the root cause, and assess the impact.
- Data recovery: Restore data from backups that are known to be uncompromised. This step is critical to minimizing data loss.
- System remediation: Patch vulnerabilities that allowed the compromise to occur and strengthen security controls to prevent future incidents.
- Notification and communication: Notify affected parties, such as customers and regulatory bodies, as appropriate, and communicate transparently about the incident.
Key Compromise Response Flowchart
The following flowchart illustrates the steps to take in response to a suspected key compromise:[Imagine a flowchart here. The flowchart would begin with a “Suspected Key Compromise” box, branching to “Confirm Compromise” (requiring log analysis, IDS alerts, etc.). A “Compromise Confirmed” branch would lead to “Revoke Key,” “Investigate Incident,” “Restore Data,” “Remediate Systems,” and “Notify Affected Parties,” all converging on a “Post-Incident Review” box.
A “Compromise Not Confirmed” branch would lead to a “Continue Monitoring” box.] The flowchart visually represents the sequential and iterative nature of the response process, highlighting the importance of swift action and thorough investigation. Each step requires careful planning and execution to minimize the impact of the compromise.
Future Trends in Cryptographic Keys
The landscape of cryptographic key management is constantly evolving, driven by advancements in computing power, the emergence of new threats, and the need for enhanced security in an increasingly interconnected world. Understanding these trends is crucial for organizations seeking to protect their sensitive data and maintain a strong security posture. The following sections explore key developments shaping the future of cryptographic key management.
Advancements in Key Management Technologies
Several key management technologies are undergoing significant improvements. Hardware Security Modules (HSMs) are becoming more sophisticated, offering enhanced tamper resistance and improved performance. Cloud-based key management services are gaining popularity, providing scalability and centralized control over keys across multiple systems. These services often incorporate advanced features like automated key rotation, access control, and auditing capabilities, simplifying key management for organizations of all sizes.
Furthermore, the development of more robust and efficient key generation algorithms, utilizing techniques like elliptic curve cryptography (ECC) and post-quantum cryptography, is further enhancing security and performance. For instance, the adoption of threshold cryptography, where a key is shared among multiple parties, mitigates the risk associated with a single point of failure.
Impact of Quantum Computing on Cryptographic Keys
The advent of powerful quantum computers poses a significant threat to current cryptographic systems. Quantum algorithms, such as Shor’s algorithm, can potentially break widely used public-key cryptosystems like RSA and ECC, rendering current key lengths insufficient. This necessitates a transition to post-quantum cryptography. The potential impact is substantial; organizations reliant on current encryption standards could face significant data breaches if quantum computers become powerful enough to break existing encryption.
This is particularly concerning for long-term data protection, where data may remain vulnerable for decades.
Post-Quantum Cryptography and its Implications for Server Security
Post-quantum cryptography (PQC) focuses on developing cryptographic algorithms that are resistant to attacks from both classical and quantum computers. Several promising PQC candidates are currently under evaluation by standardization bodies like NIST. The transition to PQC will require significant effort, including updating software, hardware, and protocols. Successful implementation will involve a phased approach, likely starting with the migration of critical systems and sensitive data.
For servers, this means updating cryptographic libraries and potentially upgrading hardware to support new algorithms. The cost and complexity of this transition are considerable, but the potential consequences of not adopting PQC are far greater. A real-world example is the ongoing NIST standardization process, which is aiming to provide organizations with a set of algorithms that are secure against both classical and quantum attacks.
Emerging Technologies Improving Key Security and Management
Several emerging technologies are enhancing key security and management. Blockchain technology offers potential for secure and transparent key management, providing an immutable record of key usage and access. Secure enclaves, hardware-isolated execution environments within processors, offer enhanced protection for cryptographic keys and operations. These enclaves provide a trusted execution environment, preventing unauthorized access even if the operating system or hypervisor is compromised.
Furthermore, advancements in homomorphic encryption allow computations to be performed on encrypted data without decryption, offering enhanced privacy and security in various applications, including cloud computing and data analytics. This is a particularly important area for securing sensitive data while enabling its use in collaborative environments.
Illustrative Example: Protecting Database Access
Protecting sensitive data within a database server requires a robust security architecture, and cryptographic keys are central to this. This example details how various key types secure a hypothetical e-commerce database, safeguarding customer information and transaction details. We’ll examine the interplay between symmetric and asymmetric keys, focusing on encryption at rest and in transit, and user authentication.Database encryption at rest and in transit, user authentication, and secure key management are all crucial components of a secure database system.
A multi-layered approach using different key types is essential for robust protection against various threats.
Database Encryption
The database itself is encrypted using a strong symmetric encryption algorithm like AES-256. A unique, randomly generated AES-256 key, referred to as the Data Encryption Key (DEK), is used to encrypt all data within the database. This DEK is highly sensitive and needs to be protected meticulously. The DEK is never directly used to encrypt or decrypt data in a production environment; rather, it is protected and managed using a separate process.
Key Encryption Key (KEK) and Master Key
The DEK is further protected by a Key Encryption Key (KEK). The KEK is an asymmetric key; a longer-lived key only used for encrypting and decrypting other keys. The KEK is itself encrypted by a Master Key, which is stored securely, potentially in a hardware security module (HSM) or a highly secure key management system. This hierarchical key management approach ensures that even if the KEK is compromised, the DEK remains protected.
The Master Key represents the highest level of security; its compromise would be a critical security incident.
User Authentication
User authentication employs asymmetric cryptography using public-key infrastructure (PKI). Each user possesses a unique pair of keys: a private key (kept secret) and a public key (distributed). When a user attempts to access the database, their credentials are verified using their private key to sign a request. The database server uses the user’s corresponding public key to verify the signature, ensuring the request originates from the legitimate user.
This prevents unauthorized access even if someone gains knowledge of the database’s DEK.
Key Management Process
The key management process involves a series of steps:
- Key Generation: The Master Key is generated securely and stored in an HSM. The KEK is generated securely. The DEK is generated randomly for each database encryption operation.
- Key Encryption: The DEK is encrypted with the KEK. The KEK is encrypted with the Master Key.
- Key Storage: The encrypted KEK and the Master Key are stored securely in the HSM. The encrypted DEK is stored separately and securely.
- Key Retrieval: During database access, the Master Key is used to decrypt the KEK. The KEK is then used to decrypt the DEK. The DEK is then used to encrypt and decrypt the data in the database.
- Key Rotation: Regular key rotation of the DEK and KEK is crucial to mitigate the risk of compromise. This involves generating new keys and securely replacing the old ones.
Illustrative Diagram
Imagine a layered security pyramid. At the base is the database itself, containing encrypted customer data (encrypted with the DEK). The next layer is the DEK, encrypted with the KEK. Above that is the KEK, encrypted with the Master Key, which resides at the apex, securely stored within the HSM. User authentication happens parallel to this, with user private keys verifying requests against their corresponding public keys held by the database server.
This layered approach ensures that even if one layer is compromised, the others protect the sensitive data. Key rotation is depicted as a cyclical process, regularly replacing keys at each layer.
Closing Notes
Securing your server hinges on a robust understanding and implementation of cryptographic key management. From generating and storing keys securely to employing strong encryption algorithms and proactively mitigating potential compromises, the journey towards robust server security requires diligence and a proactive approach. By mastering the principles Artikeld here, you can significantly enhance your server’s defenses and protect your valuable data against ever-evolving threats.
The future of cryptography, particularly in the face of quantum computing, necessitates continuous learning and adaptation; staying informed is paramount to maintaining a secure digital environment.
FAQ Explained
What happens if my server’s private key is exposed?
Exposure of a private key renders the associated data vulnerable to decryption and unauthorized access. Immediate action is required, including key revocation, system patching, and a full security audit.
How often should I rotate my cryptographic keys?
Key rotation frequency depends on the sensitivity of the data and the risk assessment. Best practices suggest regular rotations, ranging from monthly to annually, with more frequent rotations for high-value assets.
What are some common key management system pitfalls to avoid?
Common pitfalls include inadequate key storage, insufficient key rotation, lack of access controls, and neglecting regular security audits. A well-defined key management policy is essential.
Can I use the same key for encryption and decryption?
This depends on the type of encryption. Symmetric encryption uses the same key for both, while asymmetric encryption uses separate public and private keys.