Server Security Revolutionized by Cryptography: The digital landscape has irrevocably changed. Once reliant on rudimentary firewalls and access controls, server security now hinges on the sophisticated power of cryptography. This evolution, from basic perimeter defenses to robust encryption and authentication protocols, has fundamentally reshaped how we protect sensitive data and critical infrastructure in the face of increasingly complex cyber threats.
This exploration delves into the history, present state, and future of cryptography’s pivotal role in safeguarding our digital world.
We’ll examine the various types of cryptography – symmetric, asymmetric, and hashing – and their applications in securing data both at rest and in transit. From SSL/TLS implementation to advanced techniques like homomorphic encryption and post-quantum cryptography, we’ll uncover the multifaceted ways cryptography strengthens server security. We’ll also address crucial elements like key management, certificate handling, and the challenges posed by emerging threats, providing a comprehensive overview of this critical field.
The Evolution of Server Security: Server Security Revolutionized By Cryptography
Server security has undergone a dramatic transformation, evolving from rudimentary measures to sophisticated cryptographic systems. Early server security primarily relied on physical security and basic access controls, leaving them vulnerable to a range of attacks. The widespread adoption of cryptography has fundamentally altered this landscape, providing robust defenses against increasingly sophisticated threats.The limitations of traditional security measures become apparent when considering the evolution of cyberattacks.
Firewalls, while effective at blocking known threats based on IP addresses and port numbers, are easily circumvented by sophisticated attackers who employ techniques like port scanning, denial-of-service attacks, and exploiting software vulnerabilities. Similarly, access controls, while essential for managing user permissions, are vulnerable to social engineering, phishing attacks, and password cracking. These traditional methods offer a perimeter defense, but lack the depth necessary to protect against modern, targeted attacks that exploit internal weaknesses.
Early Server Security and its Vulnerabilities
Before the widespread adoption of strong cryptography, server security relied heavily on physical security measures, such as locked server rooms and restricted access. Access controls were primarily based on simple usernames and passwords, often with weak password policies. This approach was highly vulnerable to various attacks, including unauthorized physical access, password guessing, and exploiting known software vulnerabilities. The lack of robust encryption meant that data transmitted to and from servers was easily intercepted and compromised.
For instance, early e-commerce websites often transmitted credit card information without encryption, making them prime targets for data breaches.
Advancements in Cryptography and their Impact on Server Security
The history of cryptography’s impact on server security can be broadly categorized into several key phases. Early symmetric encryption algorithms, like DES, offered a significant improvement over plaintext transmission, but were susceptible to brute-force attacks as computing power increased. The development of public-key cryptography in the 1970s, pioneered by Diffie-Hellman and RSA, revolutionized server security. Public-key cryptography allowed for secure key exchange and digital signatures, paving the way for secure communication protocols like SSL/TLS.
The advent of digital certificates further enhanced security by providing a mechanism for verifying the authenticity of servers and ensuring secure communication. The timeline below illustrates these key advancements:
| Year | Advancement | Impact on Server Security |
|---|---|---|
| 1976 | Diffie-Hellman key exchange | Enabled secure key exchange over insecure channels. |
| 1977 | RSA algorithm | Provided a robust method for encryption and digital signatures. |
| 1994 | SSL 1.0 | Introduced a framework for secure communication over the internet. |
| 1996 | SSL 3.0 | Improved security and addressed vulnerabilities in previous versions. |
| 1999 | TLS 1.0 | Successor to SSL, offering enhanced security features. |
| 2006 | TLS 1.1 and 1.2 | Further improvements in security and performance. |
| 2018 | TLS 1.3 | Significant enhancements in security, performance, and efficiency. |
The ongoing evolution of cryptographic techniques continues to improve server security. The emergence of post-quantum cryptography, designed to resist attacks from quantum computers, represents a crucial next step in ensuring long-term security.
The Role of HTTPS and Digital Certificates
The widespread adoption of HTTPS, a protocol that utilizes TLS/SSL to encrypt communication between web browsers and servers, has significantly improved the security of online interactions. Digital certificates, issued by trusted certificate authorities, play a critical role in HTTPS by verifying the identity of websites and ensuring the integrity of the encryption process. This prevents man-in-the-middle attacks, where attackers intercept communication between the browser and server.
The padlock icon displayed in web browsers indicates a secure HTTPS connection, providing users with visual assurance of the security of the website.
Cryptography’s Core Role in Modern Server Security
Cryptography underpins the security of modern servers, providing the essential mechanisms to protect data confidentiality, integrity, and authenticity. Without robust cryptographic techniques, sensitive information exchanged between servers and clients would be vulnerable to interception, manipulation, and forgery, rendering online services insecure and unreliable. The evolution of cryptography has directly impacted the development of secure online infrastructure, from simple password protection to the complex systems safeguarding online banking and e-commerce.
Types of Cryptography Used for Server Security
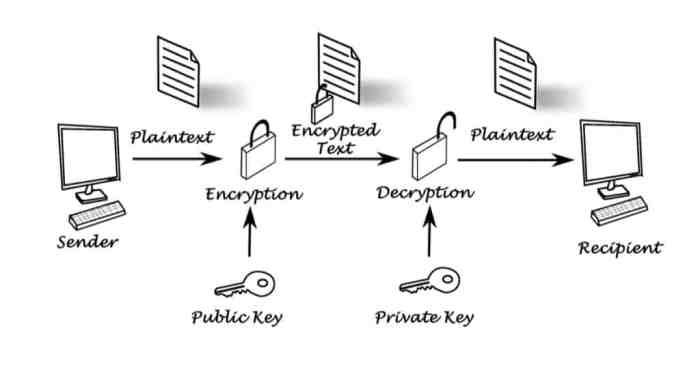
Server security relies on a combination of symmetric, asymmetric, and hashing algorithms to achieve a multi-layered defense against various threats. Symmetric cryptography uses the same key for both encryption and decryption, offering high speed but posing challenges in key distribution. Asymmetric cryptography, conversely, utilizes separate keys for encryption and decryption (public and private keys), addressing the key distribution problem but sacrificing some speed.
Hashing algorithms, on the other hand, generate a fixed-size output (hash) from any input, primarily used for data integrity verification and password storage. The effective implementation of these techniques is crucial for comprehensive server security.
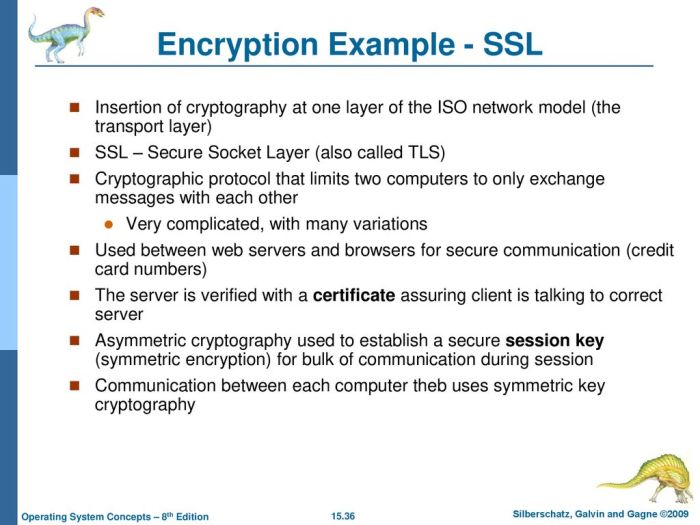
SSL/TLS and Web Server Security
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a widely implemented cryptographic protocol that secures communication between web servers and clients. It leverages asymmetric cryptography for initial key exchange and symmetric cryptography for the bulk encryption of data during the session. The process involves a handshake where the server presents its certificate, containing its public key, to the client.
The client verifies the certificate’s authenticity and then uses the public key to encrypt a symmetric session key, which is then sent to the server. Both client and server subsequently use this shared symmetric key for faster, efficient encryption and decryption of the transmitted data. This ensures confidentiality and integrity of the communication, preventing eavesdropping and data tampering.
Comparison of Encryption Algorithms
Various encryption algorithms offer different levels of security and performance. The choice of algorithm depends on the specific security requirements and computational resources available. For example, AES (Advanced Encryption Standard) is a widely used symmetric algorithm known for its strength and efficiency, while RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are prominent asymmetric algorithms. RSA, while robust, can be computationally intensive for very large key sizes.
ECC, on the other hand, offers comparable security with smaller key sizes, leading to improved performance.
Comparison of RSA, ECC, and AES Encryption
| Algorithm | Strength | Efficiency | Key Management |
|---|---|---|---|
| RSA | High, but computationally intensive for large key sizes | Relatively low, especially with large key sizes | Complex, requires careful management of private keys |
| ECC | High, comparable to RSA with smaller key sizes | High, due to smaller key sizes | Similar to RSA, but key sizes are smaller |
| AES | High, considered secure for appropriately sized keys | Very high, especially in hardware implementations | Requires secure key exchange mechanisms (e.g., using SSL/TLS) |
Securing Data at Rest and in Transit
Protecting data, whether stored or in motion, is paramount in modern server security. Cryptography plays a vital role in ensuring confidentiality, integrity, and availability of sensitive information. This section details the methods employed to secure data at rest and in transit, along with best practices for key and certificate management.
Data Encryption at Rest
Data encryption at rest safeguards information stored on servers and other storage media. This involves encrypting data before it’s written to disk or a database, ensuring that even if the storage medium is compromised, the data remains inaccessible without the decryption key. Common methods include full disk encryption (FDE), where the entire disk is encrypted, and database encryption, which focuses on securing specific database tables or columns.
FDE solutions like BitLocker (Windows) and FileVault (macOS) are widely used, leveraging techniques like AES-256 for robust encryption. Database encryption often integrates directly into the database management system (DBMS), offering granular control over which data is encrypted. For example, database systems like Oracle and PostgreSQL provide built-in encryption capabilities.
Secure Data Transmission Protocol
A secure data transmission protocol leverages cryptography to protect data during transit between systems. A robust protocol typically involves the following steps:
- Establishment of a Secure Channel: The communication begins with a secure channel establishment, often using Transport Layer Security (TLS) or its predecessor, Secure Sockets Layer (SSL). This involves a handshake process where the server and client authenticate each other and agree on a shared encryption key.
- Data Encryption: Once the secure channel is established, all data transmitted is encrypted using a symmetric encryption algorithm, such as AES, ensuring confidentiality. The chosen key is derived from the key exchange process during the TLS/SSL handshake.
- Data Integrity Verification: A message authentication code (MAC) or a digital signature is used to ensure data integrity, preventing unauthorized modifications during transit. This verification process is integrated into the protocol.
- Data Transmission: The encrypted and authenticated data is then transmitted over the network.
- Data Decryption: Upon receiving the data, the recipient uses the shared key to decrypt the data, verifying the MAC or digital signature to confirm its integrity.
Key Management and Certificate Handling
Effective key management and certificate handling are crucial for maintaining the security of encrypted data. Secure key storage, regular key rotation, and access control mechanisms are essential. This often involves dedicated hardware security modules (HSMs) for storing sensitive cryptographic keys. Certificate management involves issuing, renewing, and revoking digital certificates used for authentication and encryption. A Public Key Infrastructure (PKI) is typically used to manage certificates, ensuring trust and authenticity.
Regular audits and monitoring of key usage and certificate lifecycles are vital to mitigate risks.
Vulnerabilities and Cryptographic Mitigation
Several vulnerabilities can compromise data storage and transmission. Cryptography plays a key role in mitigating these risks:
- Data breaches: Encryption at rest and in transit protects data from unauthorized access even if a breach occurs. Strong encryption algorithms and secure key management significantly reduce the impact of data breaches.
- Man-in-the-middle attacks: TLS/SSL encrypts communication, preventing eavesdropping and data manipulation by malicious actors.
- Data leakage: Proper access controls and encryption limit the exposure of sensitive information. Data loss prevention (DLP) tools can further enhance security.
- Insider threats: Strong authentication, authorization, and monitoring help detect and prevent malicious actions by insiders.
Authentication and Authorization Mechanisms
Robust authentication and authorization are cornerstones of modern server security, ensuring only legitimate users and processes can access sensitive resources. These mechanisms, heavily reliant on cryptography, prevent unauthorized access and maintain data integrity. This section details the crucial role of PKI, MFA, and digital signatures, alongside common attack vectors targeting these systems.
Public Key Infrastructure (PKI) and Secure Authentication
Public Key Infrastructure (PKI) provides a framework for secure authentication by leveraging asymmetric cryptography. Each entity (server, user, application) possesses a unique pair of cryptographic keys: a public key, freely distributed, and a private key, kept secret. Authentication occurs when a server verifies a client’s identity using their public key to decrypt a message encrypted with the client’s private key.
This process confirms the message originated from the claimed entity and ensures its integrity. PKI also relies on Certificate Authorities (CAs) to issue digital certificates, binding public keys to identities, thus providing trust and verification. For instance, a web server presenting a certificate signed by a trusted CA assures the client that the server’s identity is legitimate.
The trust chain, from the client’s trusted root CA down to the server’s certificate, guarantees secure communication.
Multi-Factor Authentication (MFA) Implementation in Server Security
Multi-factor authentication (MFA) enhances server security by requiring multiple forms of authentication before granting access. This layered approach significantly reduces the risk of unauthorized access, even if one authentication factor is compromised. Typical implementations combine something the user knows (password), something the user has (security token or smartphone), and something the user is (biometrics). For server access, MFA might involve requiring a password and a one-time code generated by an authenticator app on a mobile device.
This approach adds an extra layer of security, making brute-force attacks and credential theft considerably more challenging. For example, a server administrator might need to use their password and a hardware security key to access the server’s management console.
Digital Signatures and Verification of Server Communications Integrity
Digital signatures employ cryptography to verify the authenticity and integrity of server communications. A digital signature, created using the sender’s private key, is appended to a message. The recipient uses the sender’s public key to verify the signature, confirming the message’s origin and ensuring it hasn’t been tampered with during transit. This process guarantees that the data received is exactly what was sent, preventing unauthorized modifications or data injection attacks.
For example, secure software updates often use digital signatures to ensure the downloaded package is authentic and hasn’t been maliciously altered. Any alteration to the software package would invalidate the digital signature, alerting the recipient to potential tampering.
Attacks Exploiting Authentication and Authorization Weaknesses
Weaknesses in authentication and authorization systems can be exploited by various attacks. Brute-force attacks attempt to guess passwords or security tokens through repeated attempts. Man-in-the-middle (MITM) attacks intercept communication between the client and server, potentially capturing credentials or manipulating messages. Session hijacking involves stealing an active user session to gain unauthorized access. Credential stuffing uses previously compromised credentials to attempt logins on different systems.
Phishing attacks trick users into revealing their credentials. Denial-of-service (DoS) attacks can overwhelm authentication systems, preventing legitimate users from accessing resources. Effective security strategies must account for and mitigate these potential vulnerabilities through strong password policies, robust MFA implementation, regular security audits, and the use of up-to-date security protocols.
Advanced Cryptographic Techniques for Enhanced Security

The evolution of server security necessitates the adoption of advanced cryptographic techniques to counter increasingly sophisticated threats. These methods go beyond traditional encryption and authentication, offering more robust protection against both current and emerging attacks, including those posed by quantum computing. This section will explore several key advancements in cryptography that are revolutionizing server security.
Homomorphic Encryption for Secure Data Processing
Homomorphic encryption allows computations to be performed on encrypted data without requiring decryption. This is crucial for cloud computing and data analysis where sensitive information needs to be processed by third-party services without compromising confidentiality. For example, a hospital could use homomorphic encryption to allow a research institution to analyze patient data for disease patterns without ever seeing the underlying patient information.
The research institution can perform calculations on the encrypted data, and the results, also encrypted, can then be decrypted by the hospital to reveal the relevant insights while maintaining patient privacy. Different types of homomorphic encryption exist, including partially homomorphic encryption (supporting only a limited set of operations) and fully homomorphic encryption (supporting all operations). The practical application of fully homomorphic encryption is still under development, but advancements are constantly being made.
Blockchain Technology for Enhanced Server Security and Data Integrity
Blockchain’s decentralized and immutable nature makes it a powerful tool for enhancing server security and data integrity. By recording server events and data changes on a distributed ledger, blockchain creates a transparent and tamper-evident audit trail. This is particularly useful for preventing unauthorized modifications and ensuring data authenticity. Imagine a system where every software update, configuration change, and access attempt to a server is recorded on a blockchain.
Any attempt to tamper with the server would be immediately detectable as the blockchain would show a discrepancy. Furthermore, the distributed nature of blockchain makes it highly resistant to single points of failure, increasing overall system resilience. Practical applications include securing software supply chains and managing digital identities.
Quantum-Resistant Cryptography in the Face of Emerging Quantum Computing Threats
The advent of quantum computing poses a significant threat to current cryptographic systems. Quantum computers have the potential to break widely used algorithms like RSA and ECC, compromising the security of sensitive data. Quantum-resistant cryptography (also known as post-quantum cryptography) is designed to withstand attacks from both classical and quantum computers. Several promising approaches are being explored, including lattice-based cryptography, code-based cryptography, and multivariate cryptography.
These algorithms rely on mathematical problems believed to be intractable even for quantum computers. The National Institute of Standards and Technology (NIST) is leading an effort to standardize quantum-resistant algorithms, ensuring a smooth transition to a post-quantum world. Adopting these algorithms proactively is crucial for protecting long-term data confidentiality.
Zero-Knowledge Proofs for Identity Verification Without Revealing Sensitive Information
Zero-knowledge proofs allow one party (the prover) to demonstrate the truth of a statement to another party (the verifier) without revealing any information beyond the truth of the statement itself. This is particularly valuable for identity verification. For example, a user could prove their identity to a website without revealing their password or other sensitive personal data. This is achieved through cryptographic protocols that allow the verifier to be convinced of the prover’s identity without gaining access to the underlying credentials.
Zero-knowledge proofs are finding increasing applications in secure authentication, digital identity management, and blockchain systems, offering a strong privacy-enhancing alternative to traditional authentication methods.
Addressing Emerging Threats and Future Trends
The landscape of server security is constantly evolving, with new threats emerging alongside innovative cryptographic solutions. Understanding these emerging threats and anticipating future trends is crucial for maintaining robust server security. This section explores the challenges posed by advanced persistent threats (APTs), analyzes real-world breaches highlighting cryptographic vulnerabilities, delves into post-quantum cryptography, and Artikels future trends in server security and the role of evolving cryptographic techniques.
Advanced Persistent Threats (APTs) and Cryptographic Mitigation, Server Security Revolutionized by Cryptography
Advanced Persistent Threats (APTs) are sophisticated, long-term attacks often carried out by state-sponsored actors or highly organized criminal groups. These attacks often involve multiple stages, including initial compromise, lateral movement within the network, data exfiltration, and persistent access. Cryptography plays a vital role in mitigating APTs by providing confidentiality, integrity, and authentication. Strong encryption at rest and in transit hinders data exfiltration, while robust authentication mechanisms prevent unauthorized access.
Regular security audits and penetration testing, coupled with the implementation of multi-factor authentication and intrusion detection systems, further strengthen the defenses against APTs. The use of advanced techniques like code signing and digital signatures also helps verify the authenticity of software and prevent the execution of malicious code.
Server security is undergoing a revolution thanks to advancements in cryptography, offering unprecedented protection against cyber threats. Understanding these complex systems requires a clear mind, something emphasized in the article, 7 Rahasia Sukses Mental Health Gen Z yang Wajib Diketahui! , which highlights the importance of mental well-being for optimal performance. Ultimately, robust server security, built on strong cryptographic foundations, is crucial in today’s digital landscape.
Real-World Server Security Breaches and Cryptographic Weaknesses
Several high-profile server security breaches have highlighted the critical role of cryptography and the devastating consequences of its weaknesses. For example, the Heartbleed bug (CVE-2014-0160), a vulnerability in OpenSSL, allowed attackers to steal sensitive data, including private keys, by exploiting a flaw in the heartbeat extension. This demonstrated the importance of rigorous code review and timely patching of cryptographic libraries.
Similarly, the Equifax breach in 2017, resulting from the exploitation of a known vulnerability in the Apache Struts framework, highlighted the need for proactive vulnerability management and strong encryption of sensitive data. The failure to implement and maintain robust encryption contributed significantly to the scale of the data breach.
Post-Quantum Cryptography and its Implications for Server Security
The development of quantum computers poses a significant threat to current cryptographic systems. Quantum computers have the potential to break widely used public-key algorithms like RSA and ECC, rendering current encryption methods vulnerable. Post-quantum cryptography (PQC) is a field of cryptography focused on developing algorithms that are resistant to attacks from both classical and quantum computers. Transitioning to PQC is a critical step in ensuring long-term server security.
This involves evaluating and implementing PQC algorithms like lattice-based cryptography, code-based cryptography, and multivariate cryptography, and integrating them into existing server infrastructure. The standardization process of PQC algorithms by NIST is a crucial step towards wider adoption and implementation.
Future Trends in Server Security and Evolving Cryptographic Techniques
The future of server security hinges on the continuous evolution of cryptographic techniques and their integration into a holistic security strategy.
- Homomorphic Encryption: Allows computations to be performed on encrypted data without decryption, enhancing data privacy in cloud computing and other distributed environments.
- Zero-Knowledge Proofs: Enables verification of information without revealing the information itself, improving authentication and authorization processes.
- Differential Privacy: Allows for data analysis while preserving individual privacy, becoming increasingly important with the growth of big data and AI.
- Blockchain Technology: Provides enhanced security and transparency for data integrity and provenance, particularly useful for securing supply chains and sensitive records.
- AI-driven Security: Utilizing machine learning to detect and respond to threats in real-time, enhancing the effectiveness of intrusion detection and prevention systems.
Outcome Summary
Cryptography isn’t merely a technological advancement; it’s the bedrock of modern server security. From its humble beginnings to its current sophisticated applications, cryptography has continually adapted to meet evolving threats. As we move forward, understanding and implementing robust cryptographic practices will remain paramount. The journey towards truly impenetrable server security is ongoing, but the advancements in cryptography offer a powerful arsenal in this crucial battle for digital safety.
Staying informed about emerging cryptographic techniques and their applications is essential for maintaining a secure online environment.
FAQ Summary
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses separate public and private keys. Symmetric is faster but requires secure key exchange; asymmetric is slower but offers better key management.
How often should SSL/TLS certificates be renewed?
SSL/TLS certificates typically have a lifespan of 1 to 2 years. Renewing them before expiration is crucial to maintain secure connections.
What are some common vulnerabilities in server security that cryptography addresses?
Common vulnerabilities include SQL injection, cross-site scripting (XSS), man-in-the-middle attacks, and data breaches. Cryptography mitigates these by encrypting data, verifying authenticity, and ensuring data integrity.
What is quantum-resistant cryptography?
Quantum-resistant cryptography refers to algorithms designed to withstand attacks from future quantum computers, which could break many currently used encryption methods.