Encryption for Servers: What You Need to Know. In today’s interconnected world, securing sensitive data is paramount. Server encryption is no longer a luxury but a necessity, a crucial defense against increasingly sophisticated cyber threats. This guide delves into the essential aspects of server encryption, covering various methods, implementation strategies, and best practices to safeguard your valuable information.
We’ll explore different encryption algorithms, their strengths and weaknesses, and how to choose the right method for your specific server environment. From setting up encryption on Linux and Windows servers to managing encryption keys and mitigating vulnerabilities, we’ll equip you with the knowledge to build a robust and secure server infrastructure. We will also examine the impact of encryption on server performance and cost, providing strategies for optimization and balancing security with efficiency.
Introduction to Server Encryption
Server encryption is the process of transforming data into an unreadable format, known as ciphertext, to protect sensitive information stored on servers from unauthorized access. This is crucial in today’s digital landscape where data breaches are increasingly common and the consequences can be devastating for businesses and individuals alike. Implementing robust server encryption is a fundamental security practice that significantly reduces the risk of data exposure and maintains compliance with various data protection regulations.The importance of server encryption cannot be overstated.
A successful data breach can lead to significant financial losses, reputational damage, legal repercussions, and loss of customer trust. Protecting sensitive data such as customer information, financial records, intellectual property, and confidential business communications is paramount, and server encryption is a primary defense mechanism. Without it, sensitive data stored on servers becomes vulnerable to various threats, including hackers, malware, and insider attacks.
Types of Server Encryption
Server encryption employs various methods to protect data at rest and in transit. These methods differ in their implementation and level of security. Understanding these differences is critical for selecting the appropriate encryption strategy for a specific environment.
- Disk Encryption: This technique encrypts the entire hard drive or storage device where the server’s data resides. Examples include BitLocker (Windows) and FileVault (macOS). This protects data even if the physical server is stolen or compromised.
- Database Encryption: This focuses on securing data within databases by encrypting sensitive fields or the entire database itself. This method often involves integrating encryption directly into the database management system (DBMS).
- File-Level Encryption: This involves encrypting individual files or folders on the server. This provides granular control over data protection, allowing for selective encryption of sensitive files while leaving less critical data unencrypted.
- Transport Layer Security (TLS)/Secure Sockets Layer (SSL): These protocols encrypt data during transmission between the server and clients. This protects data from interception during communication, commonly used for securing websites (HTTPS).
Examples of Data Breaches Due to Inadequate Server Encryption
Several high-profile data breaches highlight the critical need for robust server encryption. The lack of proper encryption has been a contributing factor in many instances, resulting in the exposure of millions of sensitive records.The Target data breach in 2013, for example, resulted from attackers gaining access to the retailer’s network through a third-party vendor with weak security practices. The compromised credentials allowed the attackers to access Target’s payment processing system, resulting in the theft of millions of credit card numbers.
Inadequate server encryption played a significant role in the severity of this breach. Similarly, the Equifax breach in 2017 exposed the personal information of nearly 150 million people due to vulnerabilities in the company’s systems and a failure to patch a known Apache Struts vulnerability. This illustrates the risk of unpatched systems and lack of comprehensive encryption.
These examples underscore the importance of a proactive and multi-layered approach to server security, with robust encryption forming a cornerstone of that approach.
Types of Encryption Methods
Server security relies heavily on robust encryption methods to protect sensitive data. Choosing the right encryption algorithm depends on factors like the sensitivity of the data, performance requirements, and the specific application. Broadly, encryption methods fall into two categories: symmetric and asymmetric. Understanding the strengths and weaknesses of each is crucial for effective server security.
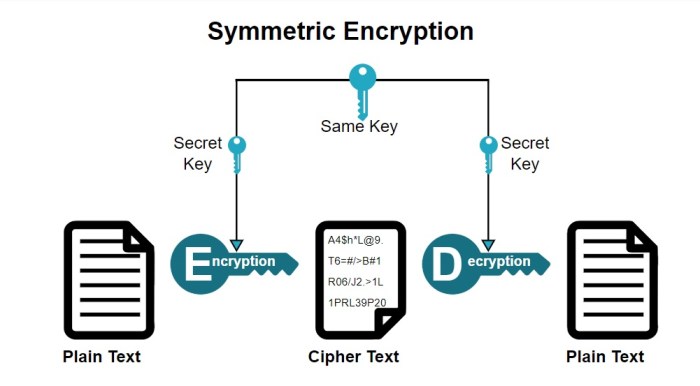
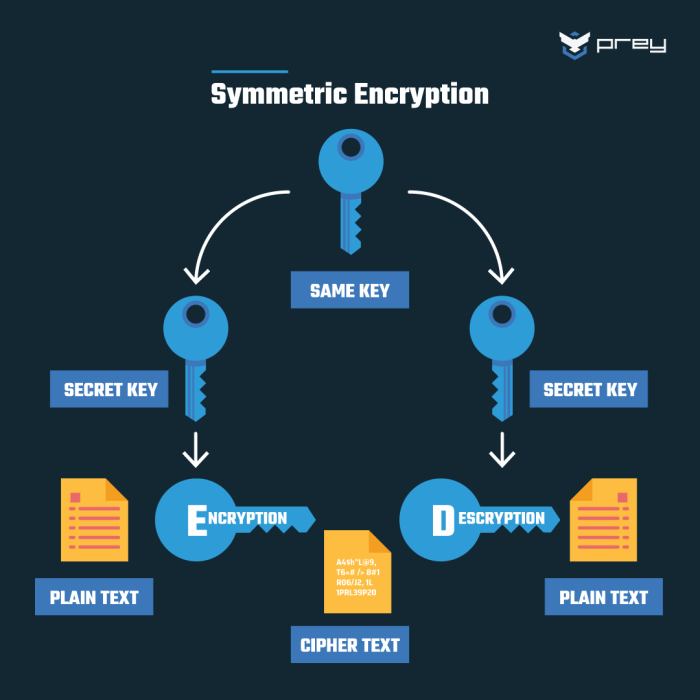
Symmetric encryption uses the same secret key to encrypt and decrypt data. This makes it faster than asymmetric encryption but requires a secure method for key exchange. Asymmetric encryption, on the other hand, uses a pair of keys: a public key for encryption and a private key for decryption. This eliminates the need for secure key exchange but is computationally more expensive.
Symmetric Encryption: AES
AES (Advanced Encryption Standard) is a widely used symmetric block cipher known for its speed and strong security. It encrypts data in blocks of 128 bits, using keys of 128, 192, or 256 bits. The longer the key, the higher the security level, but also the slightly slower the encryption/decryption process. AES is highly suitable for encrypting large volumes of data, such as databases or files stored on servers.
Its widespread adoption and rigorous testing make it a reliable choice for many server applications. However, the need for secure key distribution remains a critical consideration.
Asymmetric Encryption: RSA and ECC
RSA (Rivest–Shamir–Adleman) and ECC (Elliptic Curve Cryptography) are prominent asymmetric encryption algorithms. RSA relies on the mathematical difficulty of factoring large numbers. It’s commonly used for digital signatures and key exchange, often in conjunction with symmetric encryption for bulk data encryption. The key size in RSA significantly impacts security and performance; larger keys offer better security but are slower.ECC, on the other hand, relies on the algebraic structure of elliptic curves.
It offers comparable security to RSA with much smaller key sizes, leading to faster encryption and decryption. This makes ECC particularly attractive for resource-constrained environments or applications requiring high performance. However, ECC’s widespread adoption is relatively newer compared to RSA, meaning that its long-term security might still be under more scrutiny.
Choosing the Right Encryption Method for Server Applications
The choice of encryption method depends heavily on the specific application. For instance, databases often benefit from the speed of AES for encrypting data at rest, while web servers might use RSA for secure communication via SSL/TLS handshakes. Email servers typically utilize a combination of both symmetric and asymmetric encryption, employing RSA for key exchange and AES for message body encryption.
| Algorithm | Key Size (bits) | Speed | Security Level |
|---|---|---|---|
| AES | 128, 192, 256 | Fast | High |
| RSA | 1024, 2048, 4096+ | Slow | High (depending on key size) |
| ECC | 256, 384, 521 | Faster than RSA | High (comparable to RSA with smaller key size) |
Implementing Encryption on Different Server Types
Implementing robust encryption across your server infrastructure is crucial for protecting sensitive data. The specific methods and steps involved vary depending on the operating system and the type of data being protected—data at rest (stored on the server’s hard drive) and data in transit (data moving between servers or clients). This section details the process for common server environments.
Linux Server Encryption
Securing a Linux server involves several layers of encryption. Disk encryption protects data at rest, while SSL/TLS certificates secure data in transit. For disk encryption, tools like LUKS (Linux Unified Key Setup) are commonly used. LUKS provides a standardized way to encrypt entire partitions or drives. The process typically involves creating an encrypted partition during installation or using a tool like `cryptsetup` to encrypt an existing partition.
After encryption, the system will require a password or key to unlock the encrypted partition at boot time. For data in transit, configuring a web server (like Apache or Nginx) to use HTTPS with a valid SSL/TLS certificate is essential. This involves obtaining a certificate from a Certificate Authority (CA), configuring the web server to use the certificate, and ensuring all communication is routed through HTTPS.
Additional security measures might include encrypting files individually using tools like GPG (GNU Privacy Guard) for sensitive data not managed by the web server.
Windows Server Encryption
Windows Server offers built-in encryption features through BitLocker Drive Encryption for protecting data at rest. BitLocker encrypts the entire system drive or specific data volumes, requiring a password or TPM (Trusted Platform Module) key for access. The encryption process can be initiated through the Windows Server management tools. For data in transit, the approach is similar to Linux: using HTTPS with a valid SSL/TLS certificate for web servers (IIS).
This involves obtaining a certificate, configuring IIS to use it, and enforcing HTTPS for all web traffic. Additional measures may involve encrypting specific files or folders using the Windows Encrypting File System (EFS). EFS provides file-level encryption, protecting data even if the hard drive is removed from the server.
Data Encryption at Rest and in Transit
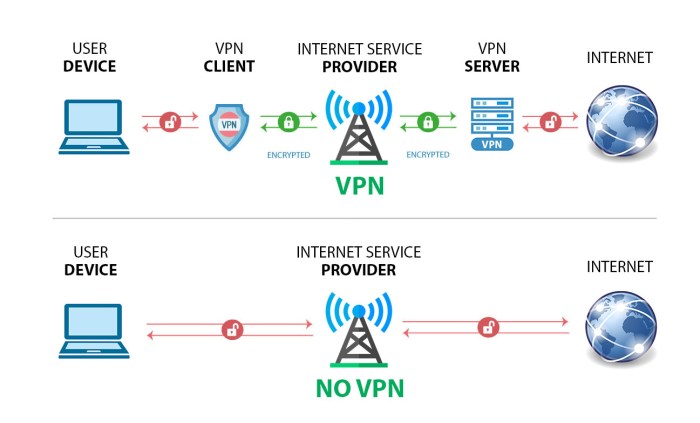
Encrypting data at rest and in transit are two distinct but equally important security measures. Data at rest, such as databases or configuration files, should be encrypted using tools like BitLocker (Windows), LUKS (Linux), or specialized database encryption features. This ensures that even if the server’s hard drive is compromised, the data remains unreadable. Data in transit, such as communication between a web browser and a web server, requires encryption protocols like TLS/SSL.
HTTPS, which uses TLS/SSL, is the standard for secure web communication. Using a trusted CA-signed certificate ensures that the server’s identity is verified, preventing man-in-the-middle attacks. Other protocols like SSH (Secure Shell) are used for secure remote access to servers. Database encryption can often be handled at the database level (e.g., using Transparent Data Encryption in SQL Server or similar features in other database systems).
Secure Web Server Configuration using HTTPS and SSL/TLS Certificates
A secure web server configuration requires obtaining and correctly implementing an SSL/TLS certificate. This involves obtaining a certificate from a reputable Certificate Authority (CA), such as Let’s Encrypt (a free and automated option), or a commercial CA. The certificate must then be installed on the web server (Apache, Nginx, IIS, etc.). The server’s configuration files need to be updated to use the certificate for HTTPS communication.
This usually involves specifying the certificate and key files in the server’s configuration. Furthermore, redirecting all HTTP traffic to HTTPS is crucial. This ensures that all communication is encrypted. Regular updates of the SSL/TLS certificate and the web server software are essential to maintain security. Using strong cipher suites and protocols during the configuration is also important to ensure the highest level of security.
A well-configured web server will only accept connections over HTTPS, actively rejecting any HTTP requests.
Key Management and Best Practices
Secure key management is paramount for the effectiveness of server encryption. Without robust key management practices, even the strongest encryption algorithms are vulnerable, rendering your server data susceptible to unauthorized access. This section details best practices for generating, storing, and rotating encryption keys, and explores the risks associated with weak or compromised keys.Effective key management hinges on several critical factors.
These include the secure generation of keys using cryptographically sound methods, the implementation of a secure storage mechanism that protects keys from unauthorized access or theft, and a regular key rotation schedule to mitigate the impact of potential compromises. Failure in any of these areas significantly weakens the overall security posture of your server infrastructure.
Key Generation Best Practices
Strong encryption keys must be generated using cryptographically secure random number generators (CSPRNGs). These generators produce unpredictable sequences of numbers, making it computationally infeasible to guess the key. Weak or predictable keys, generated using simple algorithms or insufficient entropy, are easily cracked, undermining the entire encryption process. Operating systems typically provide CSPRNGs; however, it’s crucial to ensure that these are properly configured and used.
For example, relying on the system’s default random number generator without additional strengthening mechanisms can leave your keys vulnerable. Furthermore, the length of the key is directly proportional to its strength; longer keys are exponentially more difficult to crack. The recommended key lengths vary depending on the algorithm used, but generally, longer keys offer superior protection.
Key Storage and Protection
Storing encryption keys securely is just as important as generating them securely. Keys should never be stored in plain text or easily accessible locations. Instead, they should be encrypted using a separate, strong key, often referred to as a “key encryption key” or “master key.” This master key itself should be protected with exceptional care, perhaps using hardware security modules (HSMs) or other secure enclaves.
Using a robust key management system (KMS) is highly recommended, as these systems provide a centralized and secure environment for managing the entire lifecycle of encryption keys.
Key Rotation and Lifecycle Management
Regular key rotation is a crucial aspect of secure key management. Rotating keys periodically minimizes the impact of a potential compromise. If a key is compromised, the damage is limited to the period since the last rotation. A well-defined key lifecycle, including generation, storage, use, and eventual retirement, should be established and strictly adhered to. The frequency of key rotation depends on the sensitivity of the data and the risk tolerance.
For highly sensitive data, more frequent rotation (e.g., monthly or even weekly) might be necessary. A formal process for key rotation, including documented procedures and audits, ensures consistency and reduces the risk of human error.
Key Management System Examples and Functionalities
Several key management systems are available, each offering a range of functionalities to assist in secure key management. Examples include HashiCorp Vault, AWS KMS, Azure Key Vault, and Google Cloud KMS. These systems typically provide features such as key generation, storage, rotation, access control, and auditing capabilities. They offer centralized management, allowing administrators to oversee and control all encryption keys within their infrastructure.
For example, AWS KMS allows for the creation of customer master keys (CMKs) which are encrypted and stored in a highly secure environment, with fine-grained access control policies to regulate who can access and use specific keys. This centralized approach reduces the risk of keys being scattered across different systems, making them easier to manage and more secure.
Risks Associated with Weak or Compromised Keys
The consequences of weak or compromised encryption keys can be severe, potentially leading to data breaches, financial losses, reputational damage, and legal liabilities. Compromised keys allow unauthorized access to sensitive data, enabling attackers to steal confidential information, disrupt services, or even manipulate systems for malicious purposes. This can result in significant financial losses due to data recovery efforts, regulatory fines, and legal settlements.
The reputational damage caused by a data breach can be long-lasting, impacting customer trust and business relationships. Therefore, prioritizing robust key management practices is crucial to mitigate these significant risks.
Securing your server involves understanding various encryption methods and their implications. Building a strong online presence is equally crucial, and mastering personal branding strategies, like those outlined in this insightful article on 4 Rahasia Exclusive Personal Branding yang Viral 2025 , can significantly boost your reach. Ultimately, both robust server encryption and a powerful personal brand contribute to a secure and successful online identity.
Managing Encryption Costs and Performance: Encryption For Servers: What You Need To Know
Implementing server encryption offers crucial security benefits, but it’s essential to understand its impact on performance and overall costs. Balancing security needs with operational efficiency requires careful planning and optimization. Ignoring these factors can lead to significant performance bottlenecks and unexpected budget overruns.Encryption, by its nature, adds computational overhead. The process of encrypting and decrypting data consumes CPU cycles, memory, and I/O resources.
This overhead can be particularly noticeable on systems with limited resources or those handling high volumes of data. The type of encryption algorithm used, the key size, and the hardware capabilities all play a significant role in determining the performance impact. For example, AES-256 encryption, while highly secure, is more computationally intensive than AES-128.
Encryption’s Impact on Server Performance and Resource Consumption
The performance impact of encryption varies depending on several factors. The type of encryption algorithm (AES, RSA, etc.) significantly influences processing time. Stronger algorithms, offering higher security, generally require more computational power. Key size also plays a role; longer keys (e.g., 256-bit vs. 128-bit) increase processing time but enhance security.
The hardware used is another crucial factor; systems with dedicated cryptographic hardware (like cryptographic accelerators or specialized processors) can significantly improve encryption performance compared to software-only implementations. Finally, the volume of data being encrypted and decrypted directly impacts resource usage; high-throughput systems will experience a greater performance hit than low-throughput systems. For instance, a database server encrypting terabytes of data will experience a more noticeable performance slowdown than a web server encrypting smaller amounts of data.
Optimizing Encryption Performance
Several strategies can mitigate the performance impact of encryption without compromising security. One approach is to utilize hardware acceleration. Cryptographic accelerators or specialized processors are designed to handle encryption/decryption operations much faster than general-purpose CPUs. Another strategy involves optimizing the encryption process itself. This might involve using more efficient algorithms or employing techniques like parallel processing to distribute the workload across multiple cores.
Careful selection of the encryption algorithm and key size is also vital; choosing a balance between security and performance is crucial. For example, AES-128 might be sufficient for certain applications, while AES-256 is preferred for more sensitive data, accepting the associated performance trade-off. Finally, data compression before encryption can reduce the amount of data needing to be processed, improving overall performance.
Cost Implications of Server Encryption
Implementing and maintaining server encryption incurs various costs. These include the initial investment in hardware and software capable of handling encryption, the cost of licensing encryption software or hardware, and the ongoing expenses associated with key management and security audits. The cost of hardware acceleration, for example, can be substantial, especially for high-performance systems. Furthermore, the increased resource consumption from encryption can translate into higher energy costs and potentially necessitate upgrading server infrastructure to handle the additional load.
For instance, a company migrating to full disk encryption might need to invest in faster storage systems to maintain acceptable performance levels, representing a significant capital expenditure. Additionally, the need for specialized personnel to manage encryption keys and security protocols adds to the overall operational costs.
Balancing Security, Performance, and Cost-Effectiveness, Encryption for Servers: What You Need to Know
Balancing security, performance, and cost-effectiveness requires a holistic approach. A cost-benefit analysis should be conducted to evaluate the risks and rewards of different encryption strategies. This involves considering the potential financial impact of a data breach against the costs of implementing and maintaining encryption. Prioritizing the encryption of sensitive data first is often a sensible approach, focusing resources on the most critical assets.
Regular performance monitoring and optimization are crucial to identify and address any bottlenecks. Finally, choosing the right encryption algorithm, key size, and hardware based on specific needs and budget constraints is essential for achieving a balance between robust security and operational efficiency. A phased rollout of encryption, starting with less resource-intensive areas, can also help manage costs and minimize disruption.
Common Vulnerabilities and Mitigation Strategies
Server encryption, while crucial for data security, is not a foolproof solution. Implementing encryption incorrectly or failing to address potential vulnerabilities can leave your servers exposed to attacks. Understanding these weaknesses and implementing robust mitigation strategies is paramount to maintaining a secure server environment. This section details common vulnerabilities and provides practical steps for mitigating risks.
Weak Keys and Key Management Issues
Weak keys are a significant vulnerability. Keys that are too short, easily guessable, or generated using flawed algorithms are easily cracked, rendering encryption useless. Poor key management practices, such as inadequate key rotation, insecure storage, and lack of access control, exacerbate this risk. For example, using a key generated from a predictable sequence of numbers or a readily available password cracker’s wordlist is extremely dangerous.
Effective mitigation involves using strong, randomly generated keys of sufficient length (following NIST recommendations), employing robust key generation algorithms, and implementing a secure key management system with regular key rotation and strict access controls. Consider using hardware security modules (HSMs) for enhanced key protection.
Insecure Configurations and Misconfigurations
Incorrectly configured encryption protocols or algorithms can create significant vulnerabilities. This includes using outdated or insecure cipher suites, failing to properly configure authentication mechanisms, or misconfiguring access control lists (ACLs). For instance, relying on outdated TLS versions or failing to enforce strong encryption protocols like TLS 1.3 leaves your server open to attacks like downgrade attacks or man-in-the-middle attacks.
Mitigation requires careful configuration of encryption settings according to best practices and industry standards. Regularly auditing server configurations and employing automated security tools for vulnerability scanning can help detect and rectify misconfigurations.
Improper Implementation of Encryption Protocols
Incorrect implementation of encryption protocols, such as failing to properly authenticate clients before encrypting data or using flawed encryption libraries, can create vulnerabilities. For example, using a library with known vulnerabilities or failing to properly validate client certificates can expose your server to attacks. Careful selection and implementation of secure encryption libraries and protocols are essential. Thorough testing and code reviews are vital to ensure correct implementation and prevent vulnerabilities.
Encryption-Related Security Incidents: Detection and Response
Detecting encryption-related incidents requires proactive monitoring and logging. This includes monitoring for unusual encryption key usage patterns, failed authentication attempts, and any signs of unauthorized access or data breaches. Response plans should include incident response teams, well-defined procedures, and tools for isolating affected systems, containing the breach, and restoring data from backups. Regular security audits and penetration testing can help identify weaknesses before they can be exploited.
Security Best Practices to Prevent Vulnerabilities
Implementing a robust security posture requires a multi-layered approach. The following best practices are essential for preventing encryption-related vulnerabilities:
- Use strong, randomly generated keys of sufficient length, following NIST recommendations.
- Implement a secure key management system with regular key rotation and strict access controls.
- Utilize hardware security modules (HSMs) for enhanced key protection.
- Employ robust encryption algorithms and protocols, keeping them up-to-date and properly configured.
- Regularly audit server configurations and perform vulnerability scans.
- Implement robust authentication mechanisms to verify client identities.
- Conduct thorough testing and code reviews of encryption implementations.
- Establish comprehensive monitoring and logging to detect suspicious activity.
- Develop and regularly test incident response plans.
- Maintain regular backups of encrypted data.
Future Trends in Server Encryption
Server encryption is constantly evolving to meet the growing challenges of data breaches and cyberattacks. The future of server security hinges on the adoption of advanced encryption techniques that offer enhanced protection against increasingly sophisticated threats, including those posed by quantum computing. This section explores some of the key emerging trends shaping the landscape of server encryption.The development of new encryption technologies is driven by the need for stronger security and improved functionality.
Specifically, the rise of quantum computing necessitates the development of post-quantum cryptography, while the need for processing encrypted data without decryption drives research into homomorphic encryption. These advancements promise to significantly enhance data protection and privacy in the coming years.
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on encrypted data without requiring decryption. This groundbreaking technology has the potential to revolutionize data privacy in various sectors, from cloud computing to healthcare. Imagine a scenario where a hospital can allow researchers to analyze patient data without ever exposing the sensitive information itself. Homomorphic encryption makes this possible by enabling computations on the encrypted data, producing an encrypted result that can then be decrypted by the authorized party.
This approach dramatically reduces the risk of data breaches and ensures compliance with privacy regulations like HIPAA. Current limitations include performance overhead; however, ongoing research is focused on improving efficiency and making homomorphic encryption more practical for widespread adoption. For example, fully homomorphic encryption (FHE) schemes are actively being developed and improved, aiming to reduce computational complexity and enable more complex operations on encrypted data.
Post-Quantum Cryptography
The advent of quantum computers poses a significant threat to current encryption standards, as these powerful machines can potentially break widely used algorithms like RSA and ECC. Post-quantum cryptography (PQC) aims to develop cryptographic algorithms that are resistant to attacks from both classical and quantum computers. The National Institute of Standards and Technology (NIST) is leading a standardization effort to select and validate PQC algorithms.
The selection of standardized algorithms is expected to accelerate the transition to post-quantum cryptography, ensuring that critical infrastructure and sensitive data remain protected in the quantum era. Implementing PQC will involve replacing existing cryptographic systems with quantum-resistant alternatives, a process that will require careful planning and significant investment. For example, migrating legacy systems to support PQC algorithms will require substantial software and hardware updates.
Evolution of Server Encryption Technologies
A visual representation of the evolution of server encryption technologies could be depicted as a timeline. Starting with symmetric key algorithms like DES and 3DES in the early days, the timeline would progress to the widespread adoption of asymmetric key algorithms like RSA and ECC. The timeline would then show the emergence of more sophisticated techniques like elliptic curve cryptography (ECC) offering improved security with shorter key lengths.
Finally, the timeline would culminate in the present day with the development and standardization of post-quantum cryptography algorithms and the exploration of advanced techniques like homomorphic encryption. This visual would clearly illustrate the continuous improvement in security and the adaptation to evolving technological threats.
Closing Summary

Securing your servers through effective encryption is a multifaceted process requiring careful planning and ongoing vigilance. By understanding the various encryption methods, implementing robust key management practices, and staying informed about emerging threats and technologies, you can significantly reduce your risk of data breaches and maintain the integrity of your valuable information. This guide provides a foundational understanding; continuous learning and adaptation to the ever-evolving threat landscape are crucial for maintaining optimal server security.
FAQ
What is the difference between encryption at rest and in transit?
Encryption at rest protects data stored on a server’s hard drive or other storage media. Encryption in transit protects data while it’s being transmitted over a network.
How often should I rotate my encryption keys?
Key rotation frequency depends on the sensitivity of the data and the risk level. A good starting point is to rotate keys at least annually, but more frequent rotation (e.g., every six months or even quarterly) might be necessary for highly sensitive data.
What are some signs of a compromised encryption key?
Unusual server performance, unauthorized access attempts, and unexplained data modifications could indicate a compromised key. Regular security audits and monitoring are crucial for early detection.
Can encryption slow down my server performance?
Yes, encryption can impact performance, but the effect varies depending on the algorithm, key size, and hardware. Choosing efficient algorithms and optimizing server configurations can mitigate performance overhead.