The Cryptographic Shield: Safeguarding Server Data is paramount in today’s digital landscape. Server breaches cost businesses millions, leading to data loss, reputational damage, and legal repercussions. This comprehensive guide explores the multifaceted world of server security, delving into encryption techniques, hashing algorithms, access control mechanisms, and robust key management practices. We’ll navigate the complexities of securing your valuable data, examining real-world scenarios and offering practical solutions to fortify your digital defenses.
From understanding the vulnerabilities that cryptographic shielding protects against to implementing multi-factor authentication and regular security audits, we’ll equip you with the knowledge to build a robust and resilient security posture. This isn’t just about technology; it’s about building a comprehensive strategy that addresses both technical and human factors, ensuring your server data remains confidential, integral, and available.
Introduction to Cryptographic Shielding for Server Data
Server data security is paramount in today’s interconnected world. The potential consequences of a data breach – financial losses, reputational damage, legal repercussions, and loss of customer trust – are severe and far-reaching. Protecting sensitive information stored on servers is therefore not just a best practice, but a critical necessity for any organization, regardless of size or industry.
Robust cryptographic techniques are essential components of a comprehensive security strategy.Cryptographic shielding safeguards server data against a wide range of threats. These include unauthorized access, data breaches resulting from malicious attacks (such as malware infections or SQL injection), insider threats, and data loss due to hardware failure or theft. Effective cryptographic methods mitigate these risks by ensuring confidentiality, integrity, and authenticity of the data.
Overview of Cryptographic Methods for Server Data Protection
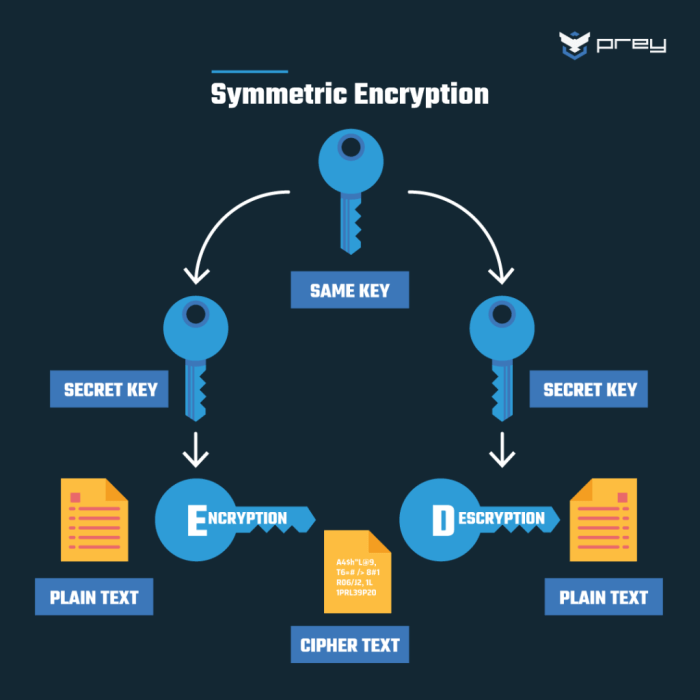
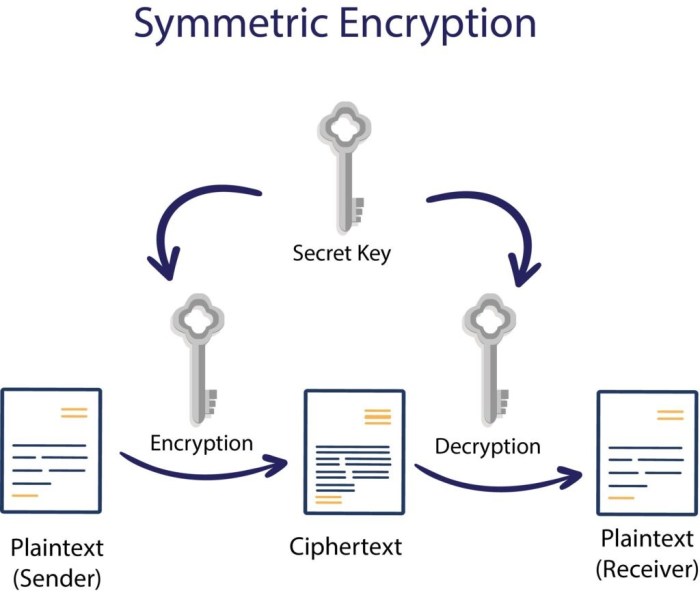
Several cryptographic methods are employed to protect server data. These methods are often used in combination to create a layered security approach. The choice of method depends on the sensitivity of the data, the specific security requirements, and performance considerations. Common techniques include:Symmetric-key cryptography utilizes a single secret key for both encryption and decryption. Algorithms like AES (Advanced Encryption Standard) are widely used for their speed and strong security.
This method is efficient for encrypting large volumes of data but requires secure key management to prevent unauthorized access. An example would be encrypting database backups using a strong AES key stored securely.Asymmetric-key cryptography, also known as public-key cryptography, employs a pair of keys: a public key for encryption and a private key for decryption. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are prominent examples.
This method is crucial for secure communication and digital signatures, ensuring data integrity and authenticity. For instance, SSL/TLS certificates use asymmetric cryptography to secure web traffic.Hashing algorithms create one-way functions, transforming data into a fixed-size string (hash). SHA-256 and SHA-3 are examples of widely used hashing algorithms. These are essential for data integrity verification, ensuring that data hasn’t been tampered with.
This is often used to check the integrity of downloaded software or to verify the authenticity of files.Digital signatures combine hashing and asymmetric cryptography to provide authentication and non-repudiation. A digital signature ensures that a message originates from a specific sender and hasn’t been altered. This is critical for ensuring the authenticity of software updates or legally binding documents.
Blockchain technology relies heavily on digital signatures for its security.
Data Encryption at Rest and in Transit, The Cryptographic Shield: Safeguarding Server Data
Data encryption is crucial both while data is stored (at rest) and while it’s being transmitted (in transit). Encryption at rest protects data from unauthorized access even if the server is compromised. Full disk encryption (FDE) is a common method to encrypt entire hard drives. Encryption in transit protects data as it moves across a network, typically using protocols like TLS/SSL for secure communication.
For example, HTTPS encrypts communication between a web browser and a web server.
Encryption at rest and in transit are two fundamental aspects of a robust data security strategy. They form a layered defense, protecting data even in the event of a server compromise or network attack.
Encryption Techniques for Server Data Protection
Protecting server data requires robust encryption techniques. The choice of encryption method depends on various factors, including the sensitivity of the data, performance requirements, and the level of security needed. This section will explore different encryption techniques and their applications in securing server data.
Symmetric and Asymmetric Encryption Algorithms
Symmetric encryption uses the same secret key for both encryption and decryption. This method is generally faster than asymmetric encryption, making it suitable for encrypting large volumes of data. However, secure key exchange presents a significant challenge. Asymmetric encryption, on the other hand, employs a pair of keys: a public key for encryption and a private key for decryption.
This eliminates the need for secure key exchange as the public key can be widely distributed. While offering strong security, asymmetric encryption is computationally more intensive and slower than symmetric encryption. Therefore, a hybrid approach, combining both symmetric and asymmetric encryption, is often used for optimal performance and security. Symmetric encryption handles the bulk data encryption, while asymmetric encryption secures the exchange of the symmetric key.
Public-Key Infrastructure (PKI) in Securing Server Data
Public Key Infrastructure (PKI) provides a framework for managing digital certificates and public keys. It’s crucial for securing server data by enabling secure communication and authentication. PKI uses digital certificates to bind public keys to entities (like servers or individuals), ensuring authenticity and integrity. When a server needs to communicate securely, it presents its digital certificate, which contains its public key and is signed by a trusted Certificate Authority (CA).
The recipient verifies the certificate’s authenticity with the CA, ensuring they are communicating with the legitimate server. This process underpins secure protocols like HTTPS, which uses PKI to encrypt communication between web browsers and servers. PKI also plays a vital role in securing other server-side operations, such as secure file transfer and email communication.
Hypothetical Scenario: Encrypting Sensitive Server Files
Imagine a healthcare provider storing patient medical records on a server. These records are highly sensitive and require robust encryption. The provider implements a hybrid encryption scheme: Asymmetric encryption is used to secure the symmetric key, which then encrypts the patient data. The server’s private key decrypts the symmetric key, allowing access to the encrypted records.
This ensures only authorized personnel with access to the server’s private key can decrypt the patient data.
| Encryption Method | Key Length (bits) | Algorithm Type | Strengths and Weaknesses |
|---|---|---|---|
| AES (Advanced Encryption Standard) | 256 | Symmetric | Strengths: Fast, widely used, robust. Weaknesses: Requires secure key exchange. |
| RSA (Rivest-Shamir-Adleman) | 2048 | Asymmetric | Strengths: Secure key exchange, digital signatures. Weaknesses: Slower than symmetric algorithms, computationally intensive. |
| Hybrid (AES + RSA) | 256 (AES) + 2048 (RSA) | Hybrid | Strengths: Combines speed and security. Weaknesses: Requires careful key management for both algorithms. |
Data Integrity and Hashing Algorithms
Data integrity, the assurance that data has not been altered or corrupted, is paramount in server security. Hashing algorithms play a crucial role in verifying this integrity by generating a unique “fingerprint” for a given data set. This fingerprint, called a hash, can be compared against a previously stored hash to detect any modifications, however subtle. Even a single bit change will result in a completely different hash value, providing a robust mechanism for detecting data tampering.Hashing algorithms are one-way functions; meaning it’s computationally infeasible to reverse the process and obtain the original data from the hash.
The cryptographic shield protecting your server data relies heavily on robust encryption techniques. Understanding the nuances of this protection is crucial, and a deep dive into Server Encryption: The Ultimate Shield Against Hackers will illuminate how this works. Ultimately, effective server-side encryption is the cornerstone of a truly secure cryptographic shield, safeguarding your valuable information from unauthorized access.
This characteristic is essential for security, as it prevents malicious actors from reconstructing the original data from its hash. This makes them ideal for verifying data integrity without compromising the confidentiality of the data itself.
Common Hashing Algorithms and Their Applications
Several hashing algorithms are widely used in server security, each with its own strengths and weaknesses. SHA-256 (Secure Hash Algorithm 256-bit) and SHA-512 (Secure Hash Algorithm 512-bit) are part of the SHA-2 family, known for their robust security and are frequently used for verifying software integrity, securing digital signatures, and protecting data stored in databases. MD5 (Message Digest Algorithm 5), while historically popular, is now considered cryptographically broken and should be avoided due to its vulnerability to collision attacks.
This means that it’s possible to find two different inputs that produce the same hash value, compromising data integrity verification. Another example is RIPEMD-160, a widely used hashing algorithm designed to provide collision resistance, and is often employed in conjunction with other cryptographic techniques for enhanced security. The choice of algorithm depends on the specific security requirements and the level of risk tolerance.
For instance, SHA-256 or SHA-512 are generally preferred for high-security applications, while RIPEMD-160 might suffice for less critical scenarios.
Vulnerabilities of Weak Hashing Algorithms
The use of weak hashing algorithms presents significant security risks. Choosing an outdated or compromised algorithm can leave server data vulnerable to various attacks.
The following are potential vulnerabilities associated with weak hashing algorithms:
- Collision Attacks: A collision occurs when two different inputs produce the same hash value. This allows attackers to replace legitimate data with malicious data without detection, as the hash will remain unchanged. This is a major concern with algorithms like MD5, which has been shown to be susceptible to efficient collision attacks.
- Pre-image Attacks: This involves finding an input that produces a given hash value. While computationally infeasible for strong algorithms, weak algorithms can be vulnerable, potentially allowing attackers to reconstruct original data or forge digital signatures.
- Rainbow Table Attacks: These attacks pre-compute a large table of hashes and their corresponding inputs, enabling attackers to quickly find the input for a given hash. Weak algorithms with smaller hash sizes are more susceptible to this type of attack.
- Length Extension Attacks: This vulnerability allows attackers to extend the length of a hashed message without knowing the original message, potentially modifying data without detection. This is particularly relevant when using algorithms like MD5 and SHA-1.
Access Control and Authentication Mechanisms
Robust access control and authentication are fundamental to safeguarding server data. These mechanisms determine who can access specific data and resources, preventing unauthorized access and maintaining data integrity. Implementing strong authentication and granular access control is crucial for mitigating the risks of data breaches and ensuring compliance with data protection regulations.
Access Control Models
Access control models define how subjects (users or processes) are granted access to objects (data or resources). Different models offer varying levels of granularity and complexity. The choice of model depends on the specific security requirements and the complexity of the system.
- Discretionary Access Control (DAC): In DAC, the owner of a resource determines who can access it. This is simple to implement but can lead to inconsistent security policies and vulnerabilities if owners make poor access decisions. For example, an employee might inadvertently grant excessive access to a sensitive file.
- Mandatory Access Control (MAC): MAC uses security labels to control access. These labels define the sensitivity level of both the subject and the object. Access is granted only if the subject’s security clearance is at least as high as the object’s security level. This model is often used in high-security environments, such as government systems, where strict access control is paramount. A typical example would be a system classifying documents as “Top Secret,” “Secret,” and “Confidential,” with users assigned corresponding clearance levels.
- Role-Based Access Control (RBAC): RBAC assigns permissions based on roles within an organization. Users are assigned to roles, and roles are assigned permissions. This simplifies access management and ensures consistency. For instance, a “Database Administrator” role might have permissions to create, modify, and delete database tables, while a “Data Analyst” role might only have read-only access.
- Attribute-Based Access Control (ABAC): ABAC is a more fine-grained approach that uses attributes of the subject, object, and environment to determine access. This allows for dynamic and context-aware access control. For example, access could be granted based on the user’s location, time of day, or the device being used.
Multi-Factor Authentication (MFA) Implementation
Multi-factor authentication significantly enhances security by requiring users to provide multiple forms of authentication. This makes it significantly harder for attackers to gain unauthorized access, even if they obtain one authentication factor.
- Choose Authentication Factors: Select at least two authentication factors. Common factors include something you know (password), something you have (security token or mobile device), and something you are (biometrics, such as fingerprint or facial recognition).
- Integrate MFA into Systems: Integrate the chosen MFA methods into all systems requiring access to sensitive server data. This may involve using existing MFA services or implementing custom solutions.
- Configure MFA Policies: Establish policies defining which users require MFA, which authentication factors are acceptable, and any other relevant parameters. This includes setting lockout thresholds after multiple failed attempts.
- User Training and Support: Provide comprehensive training to users on how to use MFA effectively. Offer adequate support to address any issues or concerns users may have.
- Regular Audits and Reviews: Regularly audit MFA logs to detect any suspicious activity. Review and update MFA policies and configurations as needed to adapt to evolving threats and best practices.
Role-Based Access Control (RBAC) Implementation
Implementing RBAC involves defining roles, assigning users to roles, and assigning permissions to roles. This structured approach streamlines access management and reduces the risk of security vulnerabilities.
- Define Roles: Identify the different roles within the organization that need access to server data. For each role, clearly define the responsibilities and required permissions.
- Create Roles in the System: Use the server’s access control mechanisms (e.g., Active Directory, LDAP) to create the defined roles. This involves assigning a unique name and defining the permissions for each role.
- Assign Users to Roles: Assign users to the appropriate roles based on their responsibilities. This can be done through a user interface or scripting tools.
- Assign Permissions to Roles: Grant specific permissions to each role, limiting access to only the necessary resources. This should follow the principle of least privilege, granting only the minimum necessary permissions.
- Regularly Review and Update: Regularly review and update roles and permissions to ensure they remain relevant and aligned with organizational needs. Remove or modify roles and permissions as necessary to address changes in responsibilities or security requirements.
Secure Key Management Practices
Secure key management is paramount to the effectiveness of any cryptographic system protecting server data. A compromised or poorly managed key renders even the strongest encryption algorithms vulnerable, negating all security measures implemented. This section details best practices for generating, storing, and rotating cryptographic keys to mitigate these risks.The core principles of secure key management revolve around minimizing the risk of unauthorized access and ensuring the integrity of the keys themselves.
Failure in any aspect – generation, storage, or rotation – can have severe consequences, potentially leading to data breaches, financial losses, and reputational damage. Therefore, a robust and well-defined key management strategy is essential for maintaining the confidentiality and integrity of server data.
Key Generation Best Practices
Secure key generation involves using cryptographically secure random number generators (CSPRNGs) to create keys that are statistically unpredictable. Weak or predictable keys are easily compromised through brute-force or other attacks. The length of the key is also crucial; longer keys offer significantly greater resistance to attacks. Industry standards and best practices should be followed diligently to ensure the generated keys meet the required security levels.
For example, using the operating system’s built-in CSPRNG, rather than a custom implementation, minimizes the risk of introducing vulnerabilities. Furthermore, regularly auditing the key generation process and its underlying components helps maintain the integrity of the system.
Key Storage and Protection
Storing cryptographic keys securely is equally critical. Keys should never be stored in plain text or easily accessible locations. Hardware security modules (HSMs) provide a highly secure environment for storing and managing cryptographic keys. HSMs are tamper-resistant devices that isolate keys from the main system, making them significantly harder to steal. Alternatively, if HSMs are not feasible, strong encryption techniques, such as AES-256 with a strong key, should be employed to protect keys stored on disk.
Access to these encrypted key stores should be strictly controlled and logged, with only authorized personnel having the necessary credentials. The implementation of robust access control mechanisms, including multi-factor authentication, is vital in preventing unauthorized access.
Key Rotation and Lifecycle Management
Regular key rotation is a crucial security practice. Keys should be rotated at predetermined intervals, based on risk assessment and regulatory compliance requirements. The frequency of rotation depends on the sensitivity of the data and the potential impact of a compromise. For highly sensitive data, more frequent rotation (e.g., monthly or even weekly) might be necessary. A well-defined key lifecycle management process should be implemented, including procedures for generating, storing, using, and ultimately destroying keys.
This process should be documented and regularly audited to ensure its effectiveness. During rotation, the old key should be securely destroyed to prevent its reuse or compromise. Proper key rotation minimizes the window of vulnerability, limiting the potential damage from a compromised key. Failing to rotate keys leaves the system vulnerable for extended periods, increasing the risk of a successful attack.
Risks Associated with Compromised or Weak Key Management
Compromised or weak key management practices can lead to severe consequences. A single compromised key can grant attackers complete access to sensitive server data, enabling data breaches, data manipulation, and denial-of-service attacks. This can result in significant financial losses, legal repercussions, and reputational damage for the organization. Furthermore, weak key generation practices can create keys that are easily guessed or cracked, rendering encryption ineffective.
The lack of proper key rotation extends the window of vulnerability, allowing attackers more time to exploit weaknesses. The consequences of inadequate key management can be catastrophic, highlighting the importance of implementing robust security measures throughout the entire key lifecycle.
Network Security and its Role in Data Protection
Network security plays a crucial role in safeguarding server data by establishing a robust perimeter defense and controlling access to sensitive information. A multi-layered approach, incorporating various security mechanisms, is essential to mitigate risks and prevent unauthorized access or data breaches. This section will explore key components of network security and their impact on server data protection.
Firewalls, Intrusion Detection Systems, and Intrusion Prevention Systems
Firewalls act as the first line of defense, filtering network traffic based on predefined rules. They examine incoming and outgoing packets, blocking malicious or unauthorized access attempts. Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity, generating alerts when potential threats are detected. Intrusion Prevention Systems (IPS), on the other hand, go a step further by actively blocking or mitigating identified threats in real-time.
The combined use of firewalls, IDS, and IPS provides a layered security approach, enhancing the overall protection of server data. A robust firewall configuration, coupled with a well-tuned IDS and IPS, can significantly reduce the risk of successful attacks. For example, a firewall might block unauthorized access attempts from specific IP addresses, while an IDS would alert administrators to unusual network activity, such as a denial-of-service attack, allowing an IPS to immediately block the malicious traffic.
Virtual Private Networks (VPNs) for Secure Remote Access
VPNs establish secure connections over public networks, creating an encrypted tunnel between the user’s device and the server. This ensures that data transmitted between the two points remains confidential and protected from eavesdropping. VPNs are essential for securing remote access to server data, particularly for employees working remotely or accessing sensitive information from outside the organization’s network. The implementation involves configuring a VPN server on the network and distributing VPN client software to authorized users.
Upon connection, the VPN client encrypts all data transmitted to and from the server, protecting it from unauthorized access. For instance, a company using a VPN allows its employees to securely access internal servers and data from their home computers, without exposing the information to potential threats on public Wi-Fi networks.
Comparison of Network Security Protocols
Various network security protocols are used to secure data transmission, each with its own strengths and weaknesses. Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are widely used protocols for securing web traffic, encrypting communication between web browsers and servers. Secure Shell (SSH) provides secure remote access to servers, allowing administrators to manage systems and transfer files securely.
Internet Protocol Security (IPsec) secures communication at the network layer, protecting entire network segments. The choice of protocol depends on the specific security requirements and the nature of the data being transmitted. For example, TLS/SSL is ideal for securing web applications, while SSH is suitable for remote server administration, and IPsec can be used to protect entire VPN tunnels.
Each protocol offers varying levels of encryption and authentication, impacting the overall security of the data. A well-informed decision on protocol selection is crucial for effective server data protection.
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are critical components of a robust server security strategy. They provide a proactive approach to identifying and mitigating potential threats before they can exploit weaknesses and compromise sensitive data. A comprehensive program involves a systematic process of evaluating security controls, identifying vulnerabilities, and implementing remediation strategies. This process is iterative and should be conducted regularly to account for evolving threats and system changes.Proactive identification of vulnerabilities is paramount in preventing data breaches.
Regular security audits involve a systematic examination of server configurations, software, and network infrastructure to identify weaknesses that could be exploited by malicious actors. This includes reviewing access controls, checking for outdated software, and assessing the effectiveness of security measures. Vulnerability assessments employ automated tools and manual techniques to scan for known vulnerabilities and misconfigurations.
Vulnerability Assessment Tools and Techniques
Vulnerability assessments utilize a combination of automated tools and manual penetration testing techniques. Automated tools, such as Nessus, OpenVAS, and QualysGuard, scan systems for known vulnerabilities based on extensive databases of security flaws. These tools can identify missing patches, weak passwords, and insecure configurations. Manual penetration testing involves security experts simulating real-world attacks to uncover vulnerabilities that automated tools might miss.
This approach often includes social engineering techniques to assess human vulnerabilities within the organization. For example, a penetration tester might attempt to trick an employee into revealing sensitive information or granting unauthorized access. The results from both automated and manual assessments are then analyzed to prioritize vulnerabilities based on their severity and potential impact.
Vulnerability Remediation and Ongoing Security
Once vulnerabilities are identified, a remediation plan must be developed and implemented. This plan Artikels the steps required to address each vulnerability, including patching software, updating configurations, and implementing stronger access controls. Prioritization is crucial; critical vulnerabilities that pose an immediate threat should be addressed first. A well-defined process ensures that vulnerabilities are remediated efficiently and effectively. This process should include detailed documentation of the remediation steps, testing to verify the effectiveness of the fixes, and regular monitoring to prevent the recurrence of vulnerabilities.
For instance, after patching a critical vulnerability in a web server, the team should verify the patch’s successful implementation and monitor the server for any signs of compromise. Regular updates to security software and operating systems are also vital to maintain a high level of security. Furthermore, employee training programs focusing on security awareness and best practices are essential to minimize human error, a common cause of security breaches.
Continuous monitoring of system logs and security information and event management (SIEM) systems allows for the detection of suspicious activities and prompt response to potential threats.
Illustrative Example: Protecting a Database Server
This section details a practical example of implementing robust security measures for a hypothetical database server, focusing on encryption, access control, and other crucial safeguards. We’ll Artikel the steps involved and visualize the secured data flow, emphasizing the critical points of data encryption and user authentication. This example utilizes common industry best practices and readily available technologies.
Consider a company, “Acme Corp,” managing sensitive customer data in a MySQL database server. To protect this data, Acme Corp implements a multi-layered security approach.
Database Server Encryption
Implementing encryption at rest and in transit is paramount. This ensures that even if unauthorized access occurs, the data remains unreadable.
Acme Corp encrypts the database files using full-disk encryption (FDE) software like BitLocker (for Windows) or LUKS (for Linux). Additionally, all communication between the database server and client applications is secured using Transport Layer Security (TLS) with strong encryption ciphers. This protects data during transmission.
Access Control and Authentication
Robust access control mechanisms are vital to limit access to authorized personnel only.
- Role-Based Access Control (RBAC): Acme Corp implements RBAC, assigning users specific roles (e.g., administrator, data analyst, read-only user) with predefined permissions. This granular control ensures that only authorized individuals can access specific data subsets.
- Strong Passwords and Multi-Factor Authentication (MFA): All users are required to use strong, unique passwords and enable MFA, such as using a time-based one-time password (TOTP) application or a security key. This significantly reduces the risk of unauthorized logins.
- Regular Password Audits: Acme Corp conducts regular audits to enforce password complexity and expiry policies, prompting users to change passwords periodically.
Data Flow Visualization
Imagine a visual representation of the data flow within Acme Corp’s secured database server. Data requests from client applications (e.g., web applications, internal tools) first encounter the TLS encryption layer. The request is encrypted before reaching the server. The server then verifies the user’s credentials through the authentication process (e.g., username/password + MFA). Upon successful authentication, based on the user’s assigned RBAC role, access to specific database tables and data is granted.
The retrieved data is then encrypted before being transmitted back to the client application through the secure TLS channel. All data at rest on the server’s hard drive is protected by FDE.
This visual representation highlights the crucial security checkpoints at every stage of data interaction: encryption in transit (TLS), authentication, authorization (RBAC), and encryption at rest (FDE).
Regular Security Monitoring and Updates
Continuous monitoring and updates are essential for maintaining a secure database server.
Acme Corp implements intrusion detection systems (IDS) and security information and event management (SIEM) tools to monitor server activity and detect suspicious behavior. Regular security audits and vulnerability assessments are conducted to identify and address potential weaknesses. The database server software and operating system are kept up-to-date with the latest security patches.
End of Discussion

Securing server data is an ongoing process, not a one-time fix. By implementing a layered security approach that combines strong encryption, robust access controls, regular audits, and vigilant key management, organizations can significantly reduce their risk profile. This guide has provided a framework for understanding the critical components of a cryptographic shield, empowering you to safeguard your valuable server data and maintain a competitive edge in the ever-evolving threat landscape.
Remember, proactive security measures are the cornerstone of a resilient and successful digital future.
Clarifying Questions: The Cryptographic Shield: Safeguarding Server Data
What are the common types of server attacks that cryptographic shielding protects against?
Cryptographic shielding protects against various attacks, including data breaches, unauthorized access, man-in-the-middle attacks, and data manipulation. It helps ensure data confidentiality, integrity, and authenticity.
How often should cryptographic keys be rotated?
Key rotation frequency depends on the sensitivity of the data and the threat landscape. Best practices recommend rotating keys at least annually, or even more frequently for highly sensitive data.
What are the legal implications of failing to adequately protect server data?
Failure to adequately protect server data can result in significant legal penalties, including fines, lawsuits, and reputational damage, particularly under regulations like GDPR and CCPA.
Can encryption alone fully protect server data?
No. Encryption is a crucial component, but it must be combined with other security measures like access controls, regular audits, and strong key management for comprehensive protection.