Cryptography: The Future of Server Security. This exploration delves into the critical role cryptography plays in safeguarding modern server infrastructure. From its historical roots to the cutting-edge advancements needed to counter the threats of quantum computing, we’ll examine the evolving landscape of server security. This journey will cover key concepts, practical applications, and emerging trends that promise to shape the future of data protection.
We’ll investigate post-quantum cryptography, advanced encryption techniques like homomorphic encryption, and the crucial aspects of secure key management. The discussion will also encompass the increasing role of hardware-based security, such as TPMs and HSMs, and the potential of blockchain technology to enhance server security and auditability. Finally, we’ll look ahead to anticipate how artificial intelligence and other emerging technologies will further influence cryptographic practices in the years to come.
Introduction to Cryptography in Server Security
Cryptography is the cornerstone of modern server security, providing the essential tools to protect sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction. It’s a multifaceted field employing mathematical techniques to ensure confidentiality, integrity, and authenticity of information exchanged and stored within a server environment. Without robust cryptographic methods, the entire digital infrastructure would be vulnerable to a myriad of cyber threats.Cryptography’s fundamental principles revolve around the use of algorithms and keys to transform readable data (plaintext) into an unreadable format (ciphertext) and back again.
This transformation, known as encryption and decryption, relies on the secrecy of the key. The strength of a cryptographic system depends heavily on the complexity of the algorithm and the length and randomness of the key. Other crucial principles include digital signatures for authentication and verification, and hashing algorithms for data integrity checks.
Historical Overview of Cryptographic Methods in Server Protection
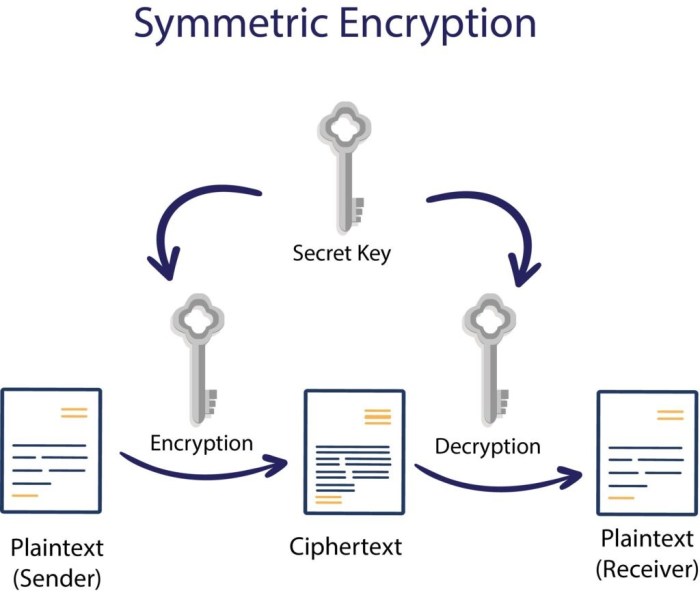
Early forms of cryptography, such as Caesar ciphers (simple substitution ciphers), were relatively simple and easily broken. The advent of the computer age ushered in significantly more complex methods. Symmetric-key cryptography, where the same key is used for encryption and decryption (like DES and 3DES), dominated for a period, but suffered from key distribution challenges. The development of public-key cryptography (asymmetric cryptography) revolutionized the field.
Algorithms like RSA, based on the difficulty of factoring large numbers, allowed for secure key exchange and digital signatures without the need to share secret keys directly. This breakthrough was crucial for the secure operation of the internet and its server infrastructure. The evolution continued with the introduction of elliptic curve cryptography (ECC), offering comparable security with smaller key sizes, making it highly efficient for resource-constrained environments.
Common Cryptographic Algorithms in Modern Server Infrastructure
Modern server infrastructure relies on a combination of symmetric and asymmetric cryptographic algorithms. Transport Layer Security (TLS), the protocol securing HTTPS connections, employs a handshake process involving both. Typically, an asymmetric algorithm like RSA or ECC is used to exchange a symmetric key, which is then used for faster encryption and decryption of the actual data during the session.
Examples of common symmetric algorithms used include AES (Advanced Encryption Standard) in various key lengths (128, 192, and 256 bits), offering robust protection against brute-force attacks. For digital signatures and authentication, RSA and ECC are widely prevalent. Hashing algorithms like SHA-256 and SHA-3 are essential for data integrity checks, ensuring that data hasn’t been tampered with during transmission or storage.
These algorithms are integrated into various protocols and technologies, including secure email (S/MIME), digital certificates (X.509), and virtual private networks (VPNs). The choice of algorithm depends on factors such as security requirements, performance considerations, and the specific application.
Post-Quantum Cryptography and its Implications

The advent of quantum computing presents a significant threat to the security of current cryptographic systems. Quantum computers, leveraging principles of quantum mechanics, possess the potential to break widely used public-key algorithms like RSA and ECC, rendering much of our digital infrastructure vulnerable. This necessitates the development and implementation of post-quantum cryptography (PQC), which aims to create cryptographic systems resistant to attacks from both classical and quantum computers.
The transition to PQC is a crucial step in ensuring the long-term security of our digital world.Post-quantum cryptographic algorithms are designed to withstand attacks from both classical and quantum computers. They utilize mathematical problems believed to be intractable even for powerful quantum computers, offering a new layer of security for sensitive data and communications. These algorithms encompass a variety of approaches, each with its own strengths and weaknesses, impacting their suitability for different applications.
Threats Posed by Quantum Computing to Current Cryptographic Methods
Quantum computers exploit the principles of superposition and entanglement to perform computations in fundamentally different ways than classical computers. This allows them to efficiently solve certain mathematical problems that are computationally infeasible for classical computers, including those underpinning many widely used public-key cryptosystems. Specifically, Shor’s algorithm, a quantum algorithm, can efficiently factor large numbers and compute discrete logarithms, directly undermining the security of RSA and ECC, which rely on the difficulty of these problems for their security.
The potential for a large-scale quantum computer to break these algorithms poses a serious threat to the confidentiality, integrity, and authenticity of data protected by these systems. This threat extends to various sectors, including finance, healthcare, and national security, where sensitive information is often protected using these vulnerable algorithms. The potential impact underscores the urgent need for a transition to post-quantum cryptography.
Characteristics and Functionalities of Post-Quantum Cryptographic Algorithms
Post-quantum cryptographic algorithms leverage mathematical problems considered hard for both classical and quantum computers. These problems often involve lattice-based cryptography, code-based cryptography, multivariate cryptography, hash-based cryptography, and isogeny-based cryptography. Each approach offers different levels of security, performance characteristics, and key sizes. For instance, lattice-based cryptography relies on the difficulty of finding short vectors in high-dimensional lattices, while code-based cryptography leverages error-correcting codes and the difficulty of decoding random linear codes.
These algorithms share the common goal of providing security against quantum attacks while maintaining reasonable performance on classical hardware. The functionality remains similar to traditional public-key systems: key generation, encryption, decryption, digital signatures, and key exchange. However, the underlying mathematical principles and the resulting key sizes and computational overhead may differ significantly.
Comparison of Different Post-Quantum Cryptography Approaches
The following table compares different post-quantum cryptography approaches, highlighting their strengths, weaknesses, and typical use cases. The selection of an appropriate algorithm depends on the specific security requirements, performance constraints, and implementation considerations of the application.
| Algorithm | Strengths | Weaknesses | Use Cases |
|---|---|---|---|
| Lattice-based | Relatively fast, versatile, good performance | Larger key sizes compared to some other approaches | Encryption, digital signatures, key encapsulation |
| Code-based | Strong security based on well-studied mathematical problems | Relatively slow, larger key sizes | Digital signatures, particularly suitable for long-term security needs |
| Multivariate | Compact keys, fast signature verification | Relatively slow signature generation, potential vulnerability to certain attacks | Digital signatures in resource-constrained environments |
| Hash-based | Proven security, forward security | Limited number of signatures per key pair, large key sizes | Digital signatures where forward security is crucial |
| Isogeny-based | Relatively small key sizes, good performance | Relatively new, less widely studied | Key exchange, digital signatures |
Advanced Encryption Techniques for Server Data
Protecting sensitive data stored on servers requires robust encryption methods beyond traditional symmetric and asymmetric algorithms. Advanced techniques like homomorphic encryption offer the potential for secure data processing without decryption, addressing the limitations of conventional approaches in cloud computing and distributed environments. This section delves into the implementation and implications of homomorphic encryption and explores potential vulnerabilities in advanced encryption techniques generally.
Homomorphic Encryption Implementation for Secure Data Processing
Homomorphic encryption allows computations to be performed on encrypted data without requiring decryption. This is achieved through mathematical operations that maintain the encrypted data’s integrity and confidentiality while enabling specific computations on the ciphertext. The result of the computation, when decrypted, is equivalent to the result that would have been obtained by performing the computation on the plaintext data.
Fully homomorphic encryption (FHE) supports arbitrary computations, while partially homomorphic encryption (PHE) only allows specific operations, such as addition or multiplication. Implementing homomorphic encryption involves selecting an appropriate scheme (e.g., Brakerski-Gentry-Vaikuntanathan (BGV), Brakerski-Fan-Vercauteren (BFV), CKKS) based on the computational requirements and the type of operations needed. The chosen scheme dictates the key generation, encryption, homomorphic operations, and decryption processes.
Efficient implementation requires careful consideration of computational overhead, as homomorphic operations are generally more resource-intensive than conventional encryption methods.
Hypothetical System Using Fully Homomorphic Encryption for Cloud-Based Data Analysis
Imagine a healthcare provider utilizing a cloud-based system for analyzing patient data. Sensitive medical records (e.g., genomic data, diagnostic images) are encrypted using FHE before being uploaded to the cloud. Researchers can then perform complex statistical analyses on the encrypted data without ever accessing the plaintext. For example, they might calculate correlations between genetic markers and disease prevalence.
The cloud server performs the computations on the encrypted data, and the results are returned as encrypted values. Only authorized personnel with the decryption key can access the decrypted results of the analysis, ensuring patient data privacy throughout the entire process. This system demonstrates how FHE can facilitate collaborative data analysis while maintaining stringent data confidentiality in a cloud environment, a scenario applicable to many sectors needing privacy-preserving computations.
The system’s architecture would involve secure key management, robust access control mechanisms, and potentially multi-party computation protocols to further enhance security.
Potential Vulnerabilities in Implementing Advanced Encryption Techniques
Despite their advantages, advanced encryption techniques like homomorphic encryption are not without vulnerabilities. Improper key management remains a significant risk, as compromised keys can expose the underlying data. Side-channel attacks, which exploit information leaked during computation (e.g., timing, power consumption), can potentially reveal sensitive data even with strong encryption. The computational overhead associated with homomorphic encryption can be substantial, making it unsuitable for certain applications with stringent performance requirements.
Furthermore, the complexity of these schemes introduces the possibility of implementation errors, leading to vulnerabilities that could be exploited by attackers. Finally, the relatively nascent nature of FHE means that ongoing research is crucial to identify and address new vulnerabilities as they emerge. Robust security audits and rigorous testing are vital to mitigate these risks.
Secure Key Management and Distribution
Robust key management is paramount for the security of any server environment. Compromised keys render even the strongest cryptographic algorithms vulnerable. This section details secure key generation, storage, and distribution methods, focusing on challenges within distributed systems and outlining a secure key exchange protocol implementation.Secure key management encompasses the entire lifecycle of cryptographic keys, from their creation and storage to their use and eventual destruction.
Failure at any stage can compromise the security of the system. This includes protecting keys from unauthorized access, ensuring their integrity, and managing their revocation when necessary. The complexity increases significantly in distributed systems, where keys need to be shared securely across multiple nodes.
Secure Key Generation and Storage
Secure key generation relies on cryptographically secure random number generators (CSPRNGs). These generators produce unpredictable, statistically random sequences of bits, essential for creating keys that are resistant to attacks. The generated keys should be of appropriate length based on the security requirements and the algorithm used. For example, AES-256 requires a 256-bit key. Storage should leverage hardware security modules (HSMs) or other physically protected and tamper-resistant devices.
These offer a significant advantage over software-based solutions because they isolate keys from the main system, protecting them from malware and unauthorized access. Regular key rotation, replacing keys with new ones at predetermined intervals, further enhances security by limiting the impact of any potential compromise. Keys should also be encrypted using a key encryption key (KEK) before storage, adding an extra layer of protection.
Challenges of Key Distribution and Management in Distributed Systems
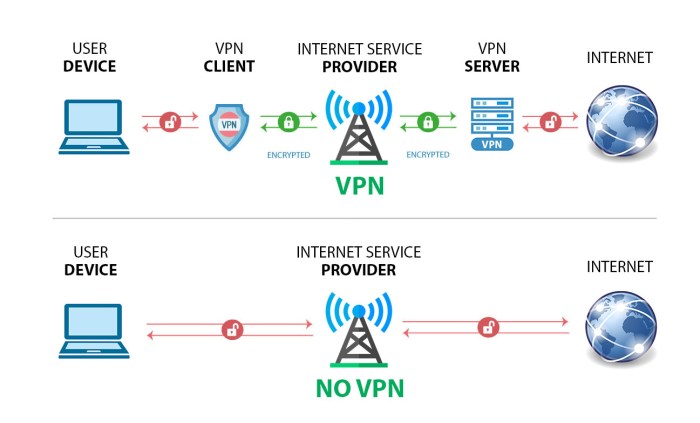
In distributed systems, securely distributing and managing keys presents significant challenges. The inherent complexity of managing keys across multiple interconnected nodes increases the risk of exposure. Maintaining key consistency across all nodes is crucial, requiring robust synchronization mechanisms. Network vulnerabilities can be exploited to intercept keys during transmission, requiring secure communication channels such as VPNs or TLS.
Additionally, managing revocation and updates of keys across a distributed network requires careful coordination to prevent inconsistencies and disruptions. The sheer number of keys involved can become unwieldy, demanding efficient management tools and strategies. For example, a large-scale cloud infrastructure with numerous servers and applications will require a sophisticated key management system to handle the volume and complexity of keys involved.
Implementing a Secure Key Exchange Protocol using Diffie-Hellman
The Diffie-Hellman key exchange (DHKE) is a widely used algorithm for establishing a shared secret key between two parties over an insecure channel. This shared secret can then be used for encrypting subsequent communications. The following steps Artikel the implementation of a secure key exchange using DHKE:
- Agreement on Public Parameters: Both parties, Alice and Bob, agree on a large prime number (p) and a generator (g) modulo p. These values are publicly known and do not need to be kept secret.
- Private Key Generation: Alice generates a secret random integer (a) as her private key. Bob similarly generates a secret random integer (b) as his private key.
- Public Key Calculation: Alice calculates her public key (A) as A = g a mod p. Bob calculates his public key (B) as B = g b mod p.
- Public Key Exchange: Alice and Bob exchange their public keys (A and B) over the insecure channel. This exchange is public and does not compromise security.
- Shared Secret Calculation: Alice calculates the shared secret (S) as S = B a mod p. Bob calculates the shared secret (S) as S = A b mod p. Mathematically, both calculations result in the same value: S = g ab mod p.
- Symmetric Encryption: Alice and Bob now use the shared secret (S) as the key for a symmetric encryption algorithm, such as AES, to encrypt their subsequent communications.
The security of DHKE relies on the computational difficulty of the discrete logarithm problem. This problem involves finding the private key (a or b) given the public key (A or B), the prime number (p), and the generator (g). With sufficiently large prime numbers, this problem becomes computationally infeasible for current computing power.
Hardware-Based Security Enhancements
Hardware-based security significantly strengthens server cryptography by offloading computationally intensive cryptographic operations and protecting sensitive cryptographic keys from software-based attacks. This approach provides a crucial layer of defense against sophisticated threats, enhancing overall server security posture. Integrating dedicated hardware components improves the speed and security of cryptographic processes, ultimately reducing vulnerabilities.
Trusted Platform Modules (TPMs) and Server Security
Trusted Platform Modules (TPMs) are specialized microcontrollers integrated into the motherboard of many modern servers. They provide a secure hardware root of trust for measuring the system’s boot process and storing cryptographic keys. This ensures that only authorized software and configurations can access sensitive data. TPMs utilize a variety of cryptographic algorithms and secure storage mechanisms to achieve this, including secure key generation, storage, and attestation.
For example, a TPM can be used to verify the integrity of the operating system before allowing the server to boot, preventing malicious bootloaders from compromising the system. Additionally, TPMs are often employed in secure boot processes, ensuring that only trusted components are loaded during startup. The secure storage of cryptographic keys within the TPM protects them from theft or compromise even if the server’s operating system is compromised.
Hardware-Based Security Features Enhancing Cryptographic Operations
Several hardware-based security features directly enhance the performance and security of cryptographic operations. These include dedicated cryptographic coprocessors that accelerate encryption and decryption processes, reducing the computational load on the main CPU and potentially improving performance. Furthermore, hardware-based random number generators (RNGs) provide high-quality randomness essential for secure key generation, eliminating the vulnerabilities associated with software-based RNGs. Another significant improvement comes from hardware-accelerated digital signature verification, which speeds up authentication processes and reduces the computational overhead of verifying digital signatures.
Finally, hardware-based key management systems provide secure storage and management of cryptographic keys, mitigating the risk of key compromise. This allows for more efficient and secure key rotation and access control.
Comparison of Hardware Security Modules (HSMs)
Hardware Security Modules (HSMs) offer varying levels of security and capabilities, influencing their suitability for different applications. The choice of HSM depends heavily on the specific security requirements and the sensitivity of the data being protected.
- High-end HSMs: These typically offer the highest levels of security, including FIPS 140-2 Level 3 or higher certification, advanced key management features, and support for a wide range of cryptographic algorithms. They are often used in highly sensitive environments like financial institutions or government agencies. These HSMs may also offer features like tamper detection and self-destruct mechanisms to further enhance security.
- Mid-range HSMs: These provide a balance between security and cost. They typically offer FIPS 140-2 Level 2 certification and support a good range of cryptographic algorithms. They are suitable for applications with moderate security requirements.
- Low-end HSMs: These are often more affordable but may offer lower security levels, potentially only FIPS 140-2 Level 1 certification, and limited cryptographic algorithm support. They might be appropriate for applications with less stringent security needs.
The Role of Blockchain in Enhancing Server Security
Blockchain technology, known for its decentralized and immutable nature, offers a compelling approach to bolstering server security. Its inherent transparency and cryptographic security features can significantly improve data integrity, access control, and auditability, addressing vulnerabilities present in traditional server security models. By leveraging blockchain’s distributed ledger capabilities, organizations can create more robust and trustworthy server environments.Blockchain’s potential for securing server access and data integrity stems from its cryptographic hashing and chain-linking mechanisms.
Each transaction or change made to the server’s data is recorded as a block, cryptographically linked to the previous block, forming an immutable chain. This makes tampering with data extremely difficult and readily detectable. Furthermore, distributed consensus mechanisms, such as Proof-of-Work or Proof-of-Stake, ensure that no single entity can control or manipulate the blockchain, enhancing its resilience against attacks.
This distributed nature eliminates single points of failure, a common weakness in centralized server security systems.
Cryptography’s role in securing servers is paramount, shaping the future of data protection. Understanding the core principles is crucial, and a great starting point is our guide on Server Security 101: Cryptography Fundamentals , which covers essential algorithms and techniques. From there, you can explore more advanced cryptographic methods vital for robust server security in the years to come.
Blockchain’s Impact on Server Access Control, Cryptography: The Future of Server Security
Implementing blockchain for server access control involves creating a permissioned blockchain network where authorized users possess cryptographic keys granting them access. These keys are stored securely and verified through the blockchain, eliminating the need for centralized authentication systems vulnerable to breaches. Each access attempt is recorded on the blockchain, creating a permanent and auditable log of all activities.
This enhances accountability and reduces the risk of unauthorized access. For instance, a company could utilize a blockchain-based system to manage access to sensitive customer data, ensuring that only authorized personnel can access it, and all access attempts are transparently logged and verifiable.
Improving Server Operation Auditability with Blockchain
Blockchain’s immutability is particularly beneficial for auditing server operations. Every action performed on the server, from software updates to user logins, can be recorded as a transaction on the blockchain. This creates a comprehensive and tamper-proof audit trail, simplifying compliance efforts and facilitating investigations into security incidents. Traditional logging systems are susceptible to manipulation, but a blockchain-based audit trail provides a significantly higher level of assurance and trust.
Consider a financial institution utilizing a blockchain to track all server-side transactions. Any discrepancies or suspicious activity would be immediately apparent, significantly reducing the time and effort required for audits and fraud detection.
Challenges and Limitations of Blockchain in Server Security
Despite its potential, implementing blockchain for server security faces several challenges. Scalability remains a significant hurdle; processing large volumes of transactions on a blockchain can be slow and resource-intensive. The complexity of integrating blockchain technology into existing server infrastructure also poses a challenge, requiring significant technical expertise and investment. Furthermore, the energy consumption associated with some blockchain consensus mechanisms, particularly Proof-of-Work, raises environmental concerns.
Finally, the security of the blockchain itself depends on the security of the nodes participating in the network; a compromise of a significant number of nodes could jeopardize the integrity of the entire system. Careful consideration of these factors is crucial before deploying blockchain-based security solutions for servers.
Future Trends in Cryptographic Server Security
The landscape of server security is constantly evolving, driven by the relentless advancement of cryptographic techniques and the emergence of new threats. Predicting the future with certainty is impossible, but by analyzing current trends and technological breakthroughs, we can anticipate key developments that will shape server security over the next decade. These advancements will not only enhance existing security protocols but also introduce entirely new paradigms for protecting sensitive data.The next decade will witness a significant shift in how we approach server security, driven by the convergence of several powerful technological forces.
These forces will necessitate a re-evaluation of current cryptographic methods and a proactive approach to anticipating future vulnerabilities.
Emerging Trends in Cryptography
Several emerging cryptographic trends promise to significantly enhance server security. Post-quantum cryptography, already discussed, is a prime example, preparing us for a future where quantum computers pose a significant threat to current encryption standards. Beyond this, we’ll see the wider adoption of lattice-based cryptography, offering strong security even against quantum attacks, and advancements in homomorphic encryption, enabling computations on encrypted data without decryption, greatly enhancing privacy.
Furthermore, advancements in zero-knowledge proofs will allow for verification of data without revealing the data itself, improving authentication and authorization processes. The increasing integration of these advanced techniques will lead to a more robust and resilient server security ecosystem.
Impact of Artificial Intelligence on Cryptographic Methods
Artificial intelligence (AI) is poised to revolutionize both the offensive and defensive aspects of cryptography. On the offensive side, AI-powered attacks can potentially discover weaknesses in cryptographic algorithms more efficiently than traditional methods, necessitating the development of more resilient algorithms. Conversely, AI can be leveraged to enhance defensive capabilities. AI-driven systems can analyze vast amounts of data to detect anomalies and potential breaches, improving threat detection and response times.
For instance, AI can be trained to identify patterns indicative of malicious activity, such as unusual login attempts or data exfiltration attempts, allowing for proactive mitigation. The development of AI-resistant cryptographic techniques will be crucial to maintain a secure environment in the face of these advanced attacks. This involves creating algorithms that are less susceptible to AI-driven analysis and pattern recognition.
Visual Representation of the Evolution of Server Security
Imagine a timeline stretching from the early days of server security to the present and extending into the future. The early stages are represented by a relatively thin, vulnerable line symbolizing weak encryption standards and easily breached systems. As we move through the timeline, the line thickens, representing the introduction of stronger symmetric encryption algorithms like AES, the incorporation of public-key cryptography (RSA, ECC), and the rise of firewalls and intrusion detection systems.
The line further strengthens and diversifies, branching into different protective layers representing the implementation of VPNs, multi-factor authentication, and more sophisticated intrusion prevention systems. As we reach the present, the line becomes a complex, multi-layered network, showcasing the diverse and interconnected security measures employed. Extending into the future, the line continues to evolve, incorporating elements representing post-quantum cryptography, AI-driven threat detection, and the integration of blockchain technology.
The overall visual is one of increasing complexity and robustness, reflecting the constant evolution of server security in response to ever-evolving threats. The future of the line suggests a more proactive, intelligent, and adaptable security architecture.
Ending Remarks
Securing server infrastructure is paramount in today’s digital world, and cryptography stands as the cornerstone of this defense. As quantum computing and other advanced technologies emerge, the need for robust and adaptable cryptographic solutions becomes even more critical. By understanding the principles, techniques, and future trends discussed here, organizations can proactively protect their valuable data and systems, building a resilient security posture for the years ahead.
The journey towards a truly secure digital future necessitates a continuous evolution of cryptographic practices, a journey we’ve only just begun to explore.
Commonly Asked Questions: Cryptography: The Future Of Server Security
What are the biggest challenges in implementing post-quantum cryptography?
Major challenges include the computational overhead of many post-quantum algorithms, the need for standardized algorithms and protocols, and the potential for unforeseen vulnerabilities.
How does homomorphic encryption differ from traditional encryption methods?
Unlike traditional encryption, which requires decryption before processing, homomorphic encryption allows computations to be performed on encrypted data without revealing the underlying data.
What is the role of AI in future cryptographic advancements?
AI could both enhance and threaten cryptography. It can aid in cryptanalysis and the development of more robust algorithms, but it also presents new attack vectors.
How can organizations ensure they are prepared for the quantum computing threat?
Organizations should begin assessing their current cryptographic infrastructure, researching post-quantum algorithms, and developing migration plans to adopt quantum-resistant cryptography.