Server Security Mastery: Cryptography Essentials delves into the critical role of cryptography in protecting servers from modern cyber threats. This comprehensive guide explores essential cryptographic concepts, practical implementation strategies, and advanced techniques to secure your systems. We’ll cover symmetric and asymmetric encryption, hashing algorithms, digital signatures, SSL/TLS, HTTPS implementation, key management, and much more. Understanding these fundamentals is crucial for building robust and resilient server infrastructure in today’s increasingly complex digital landscape.
From understanding the basics of encryption algorithms to mastering advanced techniques like perfect forward secrecy (PFS) and navigating the complexities of public key infrastructure (PKI), this guide provides a practical, step-by-step approach to securing your servers. We’ll examine real-world case studies, analyze successful security implementations, and explore emerging trends like post-quantum cryptography and the role of blockchain in enhancing server security.
By the end, you’ll possess the knowledge and skills to effectively implement and manage robust cryptographic security for your servers.
Introduction to Server Security
In today’s interconnected world, servers are the backbone of countless online services, from e-commerce platforms and social media networks to critical infrastructure systems. The security of these servers is paramount, as a breach can have devastating consequences, ranging from financial losses and reputational damage to the compromise of sensitive personal data and disruption of essential services. A robust server security strategy is no longer a luxury; it’s a necessity for any organization operating in the digital realm.Server security encompasses a wide range of practices and technologies designed to protect server systems from unauthorized access, use, disclosure, disruption, modification, or destruction.
The increasing sophistication of cyberattacks necessitates a proactive and multi-layered approach, leveraging both technical and procedural safeguards. Cryptography, a cornerstone of modern security, plays a pivotal role in achieving this goal.
Server Security Threats
Servers face a constant barrage of threats from various sources. These threats can be broadly categorized into several key areas: malware, hacking attempts, and denial-of-service (DoS) attacks. Malware, encompassing viruses, worms, Trojans, and ransomware, can compromise server systems, steal data, disrupt operations, or even render them unusable. Hacking attempts, ranging from sophisticated targeted attacks to brute-force intrusions, aim to gain unauthorized access to server resources, often exploiting vulnerabilities in software or misconfigurations.
Denial-of-service attacks, often launched using botnets, flood servers with traffic, rendering them inaccessible to legitimate users. The consequences of a successful attack can be severe, leading to data breaches, financial losses, legal liabilities, and reputational damage. Understanding these threats is the first step towards mitigating their impact.
The Role of Cryptography in Server Security
Cryptography, the practice and study of techniques for secure communication in the presence of adversarial behavior, is fundamental to securing servers. It provides the essential tools to protect data confidentiality, integrity, and authenticity. Cryptography employs various techniques to achieve these goals, including encryption (transforming data into an unreadable format), digital signatures (verifying the authenticity and integrity of data), and hashing (creating a unique digital fingerprint of data).
These cryptographic methods are implemented at various layers of the server infrastructure, protecting data both in transit (e.g., using HTTPS for secure web communication) and at rest (e.g., encrypting data stored on hard drives). Strong cryptographic algorithms, coupled with secure key management practices, are essential components of a robust server security strategy. For example, the use of TLS/SSL certificates ensures secure communication between web servers and clients, preventing eavesdropping and data tampering.
Similarly, database encryption protects sensitive data stored in databases from unauthorized access, even if the database server itself is compromised. The effective implementation of cryptography is critical in mitigating the risks associated with malware, hacking, and DoS attacks.
Essential Cryptographic Concepts
Cryptography is the bedrock of modern server security, providing the mechanisms to protect data confidentiality, integrity, and authenticity. Understanding fundamental cryptographic concepts is crucial for any server administrator aiming for robust security. This section will delve into the core principles of symmetric and asymmetric encryption, hashing algorithms, and digital signatures.
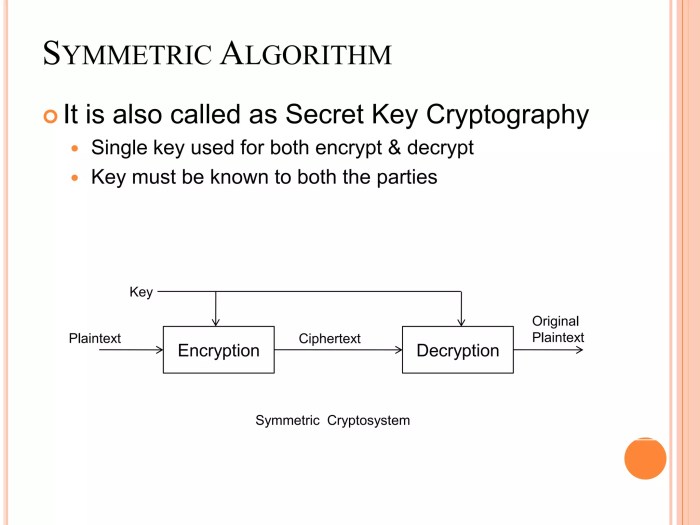
Symmetric and Asymmetric Encryption Algorithms
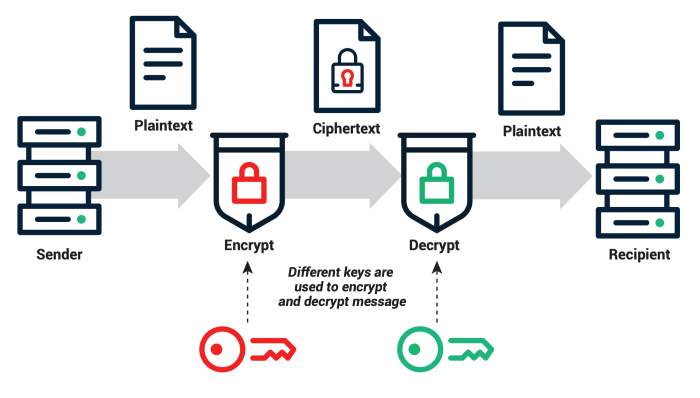
Symmetric encryption uses the same secret key for both encryption and decryption. This makes it fast and efficient but presents challenges in key distribution and management. Asymmetric encryption, conversely, employs separate keys – a public key for encryption and a private key for decryption. This solves the key distribution problem but is computationally more intensive.
| Algorithm | Type | Key Length (bits) | Strengths/Weaknesses |
|---|---|---|---|
| AES (Advanced Encryption Standard) | Symmetric | 128, 192, 256 | Strengths: Widely adopted, fast, robust. Weaknesses: Requires secure key exchange. |
| DES (Data Encryption Standard) | Symmetric | 56 | Strengths: Historically significant. Weaknesses: Considered insecure due to short key length; vulnerable to brute-force attacks. |
| RSA (Rivest-Shamir-Adleman) | Asymmetric | 1024, 2048, 4096 | Strengths: Widely used for digital signatures and key exchange. Weaknesses: Slower than symmetric algorithms; key management is crucial. |
| ECC (Elliptic Curve Cryptography) | Asymmetric | Variable | Strengths: Offers comparable security to RSA with shorter key lengths, making it more efficient. Weaknesses: Implementation complexity can introduce vulnerabilities. |
Hashing Algorithms, Server Security Mastery: Cryptography Essentials
Hashing algorithms transform data of any size into a fixed-size string of characters, called a hash or message digest. These are one-way functions; it’s computationally infeasible to reverse the process and obtain the original data from the hash. Hashing is vital for data integrity verification and password storage.Examples of widely used hashing algorithms include SHA-256 (Secure Hash Algorithm 256-bit), SHA-512, and MD5 (Message Digest Algorithm 5).
While MD5 is considered cryptographically broken and should not be used for security-sensitive applications, SHA-256 and SHA-512 are currently considered secure. SHA-512 offers a higher level of collision resistance than SHA-256 due to its larger output size. A collision occurs when two different inputs produce the same hash value.
Digital Signatures
Digital signatures provide authentication and data integrity verification. They use asymmetric cryptography to ensure that a message originates from a specific sender and hasn’t been tampered with. The sender uses their private key to create a digital signature of the message. The recipient then uses the sender’s public key to verify the signature. If the verification is successful, it confirms the message’s authenticity and integrity.For example, imagine Alice wants to send a secure message to Bob.
Alice uses her private key to create a digital signature for the message. She then sends both the message and the digital signature to Bob. Bob uses Alice’s public key to verify the signature. If the verification is successful, Bob can be confident that the message originated from Alice and hasn’t been altered during transmission. A mismatch indicates either tampering or that the message isn’t from Alice.
Implementing Cryptography for Server Security
Implementing cryptography is crucial for securing servers and protecting sensitive data. This section details the practical application of cryptographic principles, focusing on secure communication protocols and key management best practices. Effective implementation requires careful consideration of both the technical aspects and the organizational policies surrounding key handling.
Secure Communication Protocol Design using SSL/TLS
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a widely used protocol for establishing secure communication channels over a network. The handshake process, a crucial component of SSL/TLS, involves a series of messages exchanged between the client and the server to authenticate each other and establish a shared secret key. This key is then used to encrypt and decrypt subsequent communication.
The handshake process generally follows these steps:
- Client Hello: The client initiates the connection by sending a “Client Hello” message, specifying the supported SSL/TLS versions, cipher suites (encryption algorithms), and other parameters.
- Server Hello: The server responds with a “Server Hello” message, selecting a cipher suite from the client’s list and sending its certificate.
- Certificate Verification: The client verifies the server’s certificate using a trusted Certificate Authority (CA). This ensures the server’s identity.
- Key Exchange: The client and server exchange messages to establish a shared secret key. Different key exchange algorithms (like Diffie-Hellman or RSA) can be used. This process is crucial for secure communication.
- Change Cipher Spec: Both client and server signal a change to encrypted communication using the newly established secret key.
- Finished: Both client and server send “Finished” messages, encrypted using the shared secret key, to confirm the successful establishment of the secure connection.
HTTPS Implementation on Web Servers
HTTPS (HTTP Secure) secures web communication by using SSL/TLS over HTTP. Implementing HTTPS involves obtaining an SSL/TLS certificate from a trusted CA and configuring the web server to use it. A step-by-step guide is as follows:
- Obtain an SSL/TLS Certificate: Purchase a certificate from a reputable Certificate Authority (CA) like Let’s Encrypt (free option) or a commercial provider. This certificate binds a public key to your server’s domain name.
- Install the Certificate: Install the certificate and its private key on your web server. The specific steps vary depending on the web server software (Apache, Nginx, etc.).
- Configure the Web Server: Configure your web server to use the SSL/TLS certificate. This usually involves specifying the certificate and key files in the server’s configuration file.
- Test the Configuration: Test the HTTPS configuration using tools like Qualys SSL Labs Server Test to ensure proper implementation and identify potential vulnerabilities.
- Monitor and Update: Regularly monitor the certificate’s validity and renew it before it expires to maintain continuous secure communication.
Key Management and Secure Storage of Cryptographic Keys
Secure key management is paramount for maintaining the confidentiality and integrity of your server’s security. Compromised keys render your cryptographic protections useless. Best practices include:
- Key Generation: Use strong, randomly generated keys of appropriate length for the chosen algorithm. Avoid using weak or predictable keys.
- Key Storage: Store keys securely using hardware security modules (HSMs) or other secure storage solutions that offer protection against unauthorized access. Never store keys directly in plain text files.
- Key Rotation: Regularly rotate keys to minimize the impact of potential compromises. Establish a key rotation schedule and adhere to it diligently.
- Access Control: Implement strict access control measures to limit the number of individuals who have access to cryptographic keys. Use role-based access control (RBAC) where appropriate.
- Key Backup and Recovery: Maintain secure backups of keys, stored separately from the primary keys, to enable recovery in case of loss or damage. Implement robust key recovery procedures.
Advanced Cryptographic Techniques

This section delves into more complex cryptographic methods and considerations crucial for robust server security. We will explore different Public Key Infrastructure (PKI) models, the critical concept of Perfect Forward Secrecy (PFS), and analyze vulnerabilities within common cryptographic algorithms and their respective mitigation strategies. Understanding these advanced techniques is paramount for building a truly secure server environment.
Public Key Infrastructure (PKI) Models
Several PKI models exist, each with its own strengths and weaknesses regarding scalability, trust management, and certificate lifecycle management. The choice of model depends heavily on the specific security needs and infrastructure of the organization. Key differences lie in the hierarchical structure and the mechanisms for certificate issuance and revocation.
- Hierarchical PKI: This model uses a hierarchical trust structure, with a root Certificate Authority (CA) at the top, issuing certificates to intermediate CAs, which in turn issue certificates to end entities. This model is widely used due to its scalability and established trust mechanisms. However, it can be complex to manage and a compromise of a single CA can have significant consequences.
- Cross-Certification: In this model, different PKIs trust each other by exchanging certificates. This allows for interoperability between different organizations or systems, but requires careful management of trust relationships and poses increased risk if one PKI is compromised.
- Web of Trust: This decentralized model relies on individuals vouching for the authenticity of other individuals’ public keys. While offering greater decentralization and resilience to single points of failure, it requires significant manual effort for trust establishment and verification, making it less suitable for large-scale deployments.
Perfect Forward Secrecy (PFS)
Perfect Forward Secrecy (PFS) ensures that the compromise of a long-term private key does not compromise past session keys. This is achieved by using ephemeral keys for each session, meaning that even if an attacker obtains the long-term key later, they cannot decrypt past communications. PFS significantly enhances security, as a single point of compromise does not unravel the security of all past communications.
Protocols like Diffie-Hellman (DH) and Elliptic Curve Diffie-Hellman (ECDH) with ephemeral key exchange are commonly used to implement PFS. The benefit is clear: even if a server’s private key is compromised, previous communication sessions remain secure.
Vulnerabilities of Common Cryptographic Algorithms and Mitigation Strategies
Several cryptographic algorithms, while once considered secure, have been shown to be vulnerable to various attacks. Understanding these vulnerabilities and implementing appropriate mitigation strategies is essential.
- DES (Data Encryption Standard): DES is now considered insecure due to its relatively short key length (56 bits), making it susceptible to brute-force attacks. Mitigation: Do not use DES; migrate to stronger algorithms like AES.
- MD5 (Message Digest Algorithm 5): MD5 is a cryptographic hash function that has been shown to be vulnerable to collision attacks, where two different inputs produce the same hash value. Mitigation: Use stronger hash functions like SHA-256 or SHA-3.
- RSA (Rivest-Shamir-Adleman): RSA, while widely used, is susceptible to attacks if implemented incorrectly or if the key size is too small. Mitigation: Use sufficiently large key sizes (at least 2048 bits) and implement RSA correctly, adhering to best practices.
Case Studies and Real-World Examples: Server Security Mastery: Cryptography Essentials
This section delves into real-world scenarios illustrating both the devastating consequences of cryptographic weaknesses and the significant benefits of robust cryptographic implementations in securing server infrastructure. We will examine a notable security breach stemming from flawed cryptography, a successful deployment of strong cryptography in a major system, and a hypothetical scenario demonstrating how proactive cryptographic measures could prevent or mitigate a server security incident.
Heartbleed Vulnerability: A Case Study of Cryptographic Weakness
The Heartbleed vulnerability, discovered in 2014, exposed the critical weakness of improper implementation of the TLS/SSL protocol’s heartbeat extension. This flaw allowed attackers to extract up to 64KB of memory from affected servers, potentially revealing sensitive data like private keys, user credentials, and other confidential information. The vulnerability stemmed from a failure to properly validate the length of the data requested in the heartbeat extension.
Attackers could request a larger amount of data than the server expected, causing it to return a block of memory containing data beyond the intended scope. This exposed sensitive information stored in the server’s memory, including private keys used for encryption and authentication. The widespread impact of Heartbleed highlighted the severe consequences of even minor cryptographic implementation errors and underscored the importance of rigorous code review and security testing.
The vulnerability affected a vast number of servers worldwide, impacting various organizations and individuals. The remediation involved updating affected systems with patched versions of the OpenSSL library and reviewing all affected systems for potential data breaches.
Implementation of Strong Cryptography in the HTTPS Protocol
The HTTPS protocol, widely used to secure web communication, provides a prime example of a successful implementation of strong cryptography. Its effectiveness stems from a multi-layered approach combining various cryptographic techniques.
- Asymmetric Encryption for Key Exchange: HTTPS utilizes asymmetric cryptography (like RSA or ECC) for the initial key exchange, establishing a secure channel for subsequent communication. This ensures that the shared symmetric key remains confidential, even if intercepted during transmission.
- Symmetric Encryption for Data Transmission: Once a secure channel is established, symmetric encryption algorithms (like AES) are employed for encrypting the actual data exchanged between the client and the server. Symmetric encryption offers significantly faster performance compared to asymmetric encryption, making it suitable for large data transfers.
- Digital Certificates and Public Key Infrastructure (PKI): Digital certificates, issued by trusted Certificate Authorities (CAs), verify the identity of the server. This prevents man-in-the-middle attacks, where an attacker intercepts communication and impersonates the server. The PKI ensures that the client can trust the authenticity of the server’s public key.
- Hashing for Integrity Verification: Hashing algorithms (like SHA-256) are used to generate a unique fingerprint of the data. This fingerprint is transmitted along with the data, allowing the client to verify the data’s integrity and detect any tampering during transmission.
Hypothetical Scenario: Preventing a Data Breach with Strong Cryptography
Imagine a hypothetical e-commerce website storing customer credit card information in a database on its server. Without proper encryption, a successful data breach could expose all sensitive customer data, leading to significant financial losses and reputational damage. However, if the website had implemented robust encryption at rest and in transit, the impact of a breach would be significantly mitigated.
Encrypting the database at rest using AES-256 encryption would render the stolen data unusable without the decryption key. Furthermore, using HTTPS with strong TLS/SSL configuration would protect the transmission of customer data between the client and the server, preventing interception of credit card information during online transactions. Even if an attacker gained access to the server, the encrypted data would remain protected, minimizing the damage from the breach.
Regular security audits and penetration testing would further enhance the website’s security posture, identifying and addressing potential vulnerabilities before they could be exploited.
Future Trends in Server Security Cryptography
The landscape of server security is constantly evolving, driven by advancements in computing power and the emergence of new threats. Understanding and adapting to these changes is crucial for maintaining robust and secure server infrastructure. This section explores key future trends in server security cryptography, focusing on post-quantum cryptography and the role of blockchain technology.Post-quantum cryptography (PQC) is rapidly gaining importance as quantum computing technology matures.
The potential for quantum computers to break widely used public-key cryptography algorithms necessitates a proactive approach to securing server infrastructure against this emerging threat. The transition to PQC requires careful consideration of algorithm selection, implementation, and integration with existing systems.
Post-Quantum Cryptography and its Implications for Server Security
The development and standardization of post-quantum cryptographic algorithms are underway. Several promising candidates, including lattice-based, code-based, and multivariate cryptography, are being evaluated for their security and performance characteristics. The transition to PQC will involve significant changes in server infrastructure, requiring updates to software libraries, protocols, and hardware. For example, migrating to PQC algorithms might necessitate replacing existing TLS/SSL implementations with versions supporting post-quantum algorithms, a process requiring substantial testing and validation to ensure compatibility and performance.
Successful implementation will hinge on careful planning, resource allocation, and collaboration across the industry. The impact on performance needs careful evaluation as PQC algorithms often have higher computational overhead compared to their classical counterparts.
Blockchain Technology’s Role in Enhancing Server Security
Blockchain technology, known for its decentralized and tamper-proof nature, offers potential benefits for enhancing server security. Its inherent immutability can be leveraged to create secure audit trails, ensuring accountability and transparency in server operations. For instance, blockchain can record all access attempts, modifications, and configurations changes, creating an immutable record that is difficult to alter or falsify. Furthermore, decentralized identity management systems based on blockchain can improve authentication and authorization processes, reducing reliance on centralized authorities vulnerable to compromise.
While still relatively nascent, the application of blockchain in server security is a promising area of development, offering potential for increased trust and resilience. Real-world examples are emerging, with companies experimenting with blockchain for secure software updates and supply chain management, areas directly relevant to server security.
A Conceptual Framework for a Future-Proof Server Security System
A future-proof server security system should incorporate a multi-layered approach, integrating advanced cryptographic techniques with robust security practices. This framework would include:
1. Post-quantum cryptography
Implementing PQC algorithms for key exchange, digital signatures, and encryption to mitigate the threat of quantum computers.
2. Homomorphic encryption
Enabling computation on encrypted data without decryption, enhancing privacy and security in cloud-based server environments.
3. Secure multi-party computation (MPC)
Allowing multiple parties to jointly compute a function over their private inputs without revealing anything beyond the output.
4. Blockchain-based audit trails
Creating immutable records of server activities to enhance transparency and accountability.
5. AI-powered threat detection
Utilizing machine learning algorithms to identify and respond to evolving security threats in real-time.
6. Zero-trust security model
Server Security Mastery: Cryptography Essentials begins with understanding fundamental encryption algorithms. To truly master server security, however, you need a broader strategic perspective, which is why studying The Cryptographic Edge: Server Security Strategies is crucial. This deeper dive into comprehensive security practices complements the core cryptography knowledge, ensuring robust protection against modern threats. Ultimately, combining these approaches provides a truly robust security posture.
Assuming no implicit trust and verifying every access request, regardless of its origin.This integrated approach would provide a robust defense against a wide range of threats, both present and future, ensuring the long-term security and integrity of server infrastructure. The successful implementation of such a framework requires a collaborative effort between researchers, developers, and security professionals, along with continuous monitoring and adaptation to the ever-changing threat landscape.
Conclusive Thoughts
Mastering server security through cryptography is an ongoing process, requiring continuous learning and adaptation to emerging threats. This guide has provided a strong foundation in the essential concepts and practical techniques needed to build a secure server infrastructure. By implementing the strategies and best practices discussed, you can significantly reduce your vulnerability to attacks and protect your valuable data.
Remember to stay updated on the latest advancements in cryptography and security best practices to maintain a robust and resilient defense against evolving cyber threats. The future of server security relies on a proactive and informed approach to cryptography.
Detailed FAQs
What are the common types of server attacks that cryptography can mitigate?
Cryptography helps mitigate various attacks, including data breaches, man-in-the-middle attacks, denial-of-service attacks, and unauthorized access.
How often should cryptographic keys be rotated?
Key rotation frequency depends on the sensitivity of the data and the threat landscape. Best practices recommend regular rotation, often on a monthly or quarterly basis.
What is the difference between a digital signature and a digital certificate?
A digital signature verifies the authenticity and integrity of data, while a digital certificate verifies the identity of a website or server.
Are there any free tools available for implementing and managing cryptography?
Several open-source tools and libraries are available for implementing cryptographic functions, although careful selection and configuration are crucial.