Cryptography for Server Admins: An In-Depth Look delves into the crucial role cryptography plays in securing modern server infrastructure. This comprehensive guide explores essential concepts, from symmetric and asymmetric encryption to hashing algorithms and digital certificates, equipping server administrators with the knowledge to effectively protect sensitive data and systems. We’ll examine practical applications, best practices, and troubleshooting techniques, empowering you to build robust and secure server environments.
This exploration covers a wide range of topics, including the strengths and weaknesses of various encryption algorithms, the importance of key management, and the practical implementation of secure communication protocols like SSH. We’ll also address advanced techniques and common troubleshooting scenarios, providing a holistic understanding of cryptography’s vital role in server administration.
Introduction to Cryptography for Server Administration: Cryptography For Server Admins: An In-Depth Look
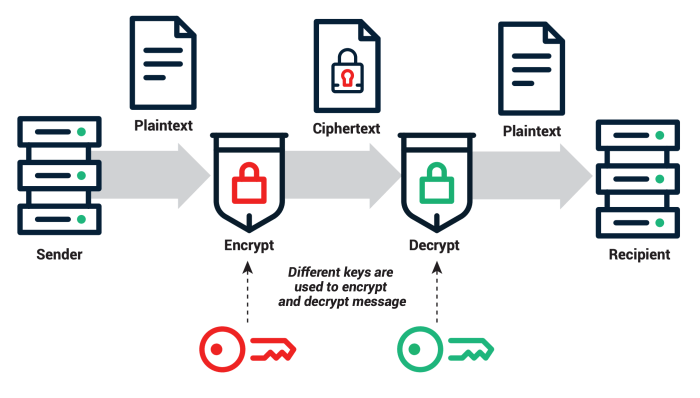
Cryptography is the cornerstone of secure server administration, providing the essential tools to protect sensitive data and maintain the integrity of server infrastructure. Understanding fundamental cryptographic concepts is paramount for any server administrator aiming to build and maintain robust security. This section will explore these concepts and their practical applications in securing servers.Cryptography, at its core, involves transforming readable data (plaintext) into an unreadable format (ciphertext) using encryption algorithms.
This ciphertext can only be deciphered with the correct decryption key. This process ensures confidentiality, preventing unauthorized access to sensitive information. Beyond confidentiality, cryptography also offers mechanisms for data integrity verification (ensuring data hasn’t been tampered with) and authentication (verifying the identity of users or systems). These aspects are crucial for maintaining a secure and reliable server environment.
Importance of Cryptography in Securing Server Infrastructure
Cryptography plays a multifaceted role in securing server infrastructure, protecting against a wide range of threats. Strong encryption protects data at rest (stored on hard drives) and in transit (while being transmitted over a network). Digital signatures ensure the authenticity and integrity of software updates and configurations, preventing malicious code injection. Secure authentication protocols, such as TLS/SSL, protect communication between servers and clients, preventing eavesdropping and man-in-the-middle attacks.
Without robust cryptographic measures, servers are vulnerable to data breaches, unauthorized access, and system compromise, leading to significant financial and reputational damage. For example, a server storing customer credit card information without proper encryption could face severe penalties under regulations like PCI DSS.
Common Cryptographic Threats Faced by Server Administrators
Server administrators face numerous cryptographic threats, many stemming from vulnerabilities in cryptographic implementations or insecure configurations.
- Weak or outdated encryption algorithms: Using outdated algorithms like DES or weak key lengths for AES leaves systems vulnerable to brute-force attacks. For example, a server using 56-bit DES encryption could be easily compromised with modern computing power.
- Improper key management: Poor key management practices, including weak key generation, inadequate storage, and insufficient key rotation, significantly weaken security. Compromised keys can render even the strongest encryption useless. A breach resulting from insecure key storage could expose all encrypted data.
- Man-in-the-middle (MITM) attacks: These attacks involve an attacker intercepting communication between a server and a client, potentially modifying or stealing data. If a server doesn’t use proper TLS/SSL certificates and verification, it becomes susceptible to MITM attacks.
- Cryptographic vulnerabilities in software: Exploitable flaws in cryptographic libraries or applications can allow attackers to bypass security measures. Regular software updates and security patching are crucial to mitigate these risks. The Heartbleed vulnerability, which affected OpenSSL, is a prime example of how a single cryptographic flaw can have devastating consequences.
- Brute-force attacks: These attacks involve trying various combinations of passwords or keys until the correct one is found. Weak passwords and insufficient complexity requirements make systems susceptible to brute-force attacks. A server with a simple password policy could be easily compromised.
Symmetric-key Cryptography
Symmetric-key cryptography employs a single, secret key for both encryption and decryption. This contrasts with asymmetric cryptography, which uses separate keys. Its simplicity and speed make it ideal for securing large amounts of data, but secure key distribution remains a crucial challenge.Symmetric-key algorithms are categorized by their block size (the amount of data encrypted at once) and key size (the length of the secret key).
A larger key size generally implies greater security, but also impacts performance. The choice of algorithm and key size depends on the sensitivity of the data and the available computational resources.
Symmetric-key Algorithm Comparison: AES, DES, 3DES
AES (Advanced Encryption Standard), DES (Data Encryption Standard), and 3DES (Triple DES) represent different generations of symmetric-key algorithms. AES, the current standard, offers significantly improved security and performance compared to its predecessors. DES, while historically significant, is now considered insecure due to its relatively short key size. 3DES, a more robust version of DES, attempts to mitigate DES’s vulnerabilities but is less efficient than AES.AES boasts a variable block size (typically 128 bits) and key sizes of 128, 192, or 256 bits.
Its strength lies in its sophisticated mathematical structure, making it highly resistant to brute-force and cryptanalytic attacks. DES, with its 64-bit block size and 56-bit key, is vulnerable to modern attacks due to its smaller key size. 3DES applies the DES algorithm three times, effectively increasing the key size and security, but it is significantly slower than AES.
Performance Characteristics of Symmetric-key Encryption Methods
The performance of symmetric-key encryption methods is primarily influenced by the algorithm’s complexity and the key size. AES, despite its strong security, generally offers excellent performance, especially with hardware acceleration. 3DES, due to its triple application of the DES algorithm, exhibits significantly slower performance. DES, while faster than 3DES, is computationally inexpensive because of its outdated design but is considered insecure for modern applications.
Factors such as hardware capabilities, implementation details, and data volume also influence overall performance. Modern CPUs often include dedicated instructions for accelerating AES encryption and decryption, further enhancing its practical performance.
Securing Sensitive Data on a Server using Symmetric-key Encryption: A Scenario
Consider a server hosting sensitive customer financial data. A symmetric-key algorithm, such as AES-256 (AES with a 256-bit key), can be used to encrypt the data at rest. The server generates a unique AES-256 key, which is then securely stored (e.g., using a hardware security module – HSM). All data written to the server is encrypted using this key before storage.
When data is requested, the server decrypts it using the same key. This ensures that even if an attacker gains unauthorized access to the server’s storage, the data remains confidential. Regular key rotation and secure key management practices are crucial for maintaining the security of this system. Failure to securely manage the encryption key renders this approach useless.
Symmetric-key Algorithm Speed and Key Size Comparison
| Algorithm | Key Size (bits) | Typical Speed (Approximate) | Security Level |
|---|---|---|---|
| DES | 56 | Fast | Weak – Insecure for modern applications |
| 3DES | 168 (effective) | Moderate | Moderate – Considerably slower than AES |
| AES-128 | 128 | Fast | Strong |
| AES-256 | 256 | Fast (slightly slower than AES-128) | Very Strong |
Asymmetric-key Cryptography
Asymmetric-key cryptography, also known as public-key cryptography, represents a fundamental shift from the limitations of symmetric-key systems. Unlike symmetric encryption, which relies on a single secret key shared between parties, asymmetric cryptography employs a pair of keys: a public key and a private key. This key pair is mathematically linked, allowing for secure communication and authentication in a much broader context.
The public key can be widely distributed, while the private key remains strictly confidential, forming the bedrock of secure online interactions.Asymmetric encryption utilizes complex mathematical functions to ensure that data encrypted with the public key can only be decrypted with the corresponding private key, and vice-versa. This characteristic allows for secure key exchange and digital signatures, functionalities impossible with symmetric encryption alone.
This section will delve into the core principles of two prominent asymmetric encryption algorithms: RSA and ECC, and illustrate their practical applications in server security.
RSA Cryptography
RSA, named after its inventors Rivest, Shamir, and Adleman, is one of the oldest and most widely used public-key cryptosystems. It relies on the mathematical difficulty of factoring large numbers, specifically the product of two large prime numbers. The public key consists of the modulus (the product of the two primes) and a public exponent, while the private key is derived from the prime factors and the public exponent.
Encryption involves raising the plaintext message to the power of the public exponent modulo the modulus. Decryption uses a related mathematical operation involving the private key to recover the original plaintext. The security of RSA hinges on the computational infeasibility of factoring extremely large numbers. A sufficiently large key size (e.g., 2048 bits or more) is crucial to withstand current and foreseeable computational power.
Elliptic Curve Cryptography (ECC)
Elliptic Curve Cryptography offers a compelling alternative to RSA, achieving comparable security levels with significantly smaller key sizes. ECC leverages the mathematical properties of elliptic curves over finite fields. The public and private keys are points on the elliptic curve, and the cryptographic operations involve point addition and scalar multiplication. The security of ECC relies on the difficulty of solving the elliptic curve discrete logarithm problem.
Because of its efficiency in terms of computational resources and key size, ECC is increasingly favored for applications where bandwidth or processing power is limited, such as mobile devices and embedded systems. It also finds widespread use in securing server communications.
Asymmetric Encryption in Server Authentication and Secure Communication
Asymmetric encryption plays a vital role in establishing secure connections and authenticating servers. One prominent example is the use of SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols, which are fundamental to secure web browsing and other internet communications. During the SSL/TLS handshake, the server presents its public key to the client. The client then uses this public key to encrypt a symmetric session key, which is then sent to the server.
Only the server, possessing the corresponding private key, can decrypt this session key. Subsequently, all further communication between the client and server is encrypted using this much faster symmetric key. This hybrid approach combines the security benefits of asymmetric encryption for key exchange with the efficiency of symmetric encryption for bulk data transfer. Another crucial application is in digital signatures, which are used to verify the authenticity and integrity of data transmitted from a server.
A server’s private key is used to create a digital signature, which can be verified by anyone using the server’s public key. This ensures that the data originates from the claimed server and hasn’t been tampered with during transmission.
Symmetric vs. Asymmetric Encryption: Key Differences
The core difference lies in the key management. Symmetric encryption uses a single secret key shared by all communicating parties, while asymmetric encryption employs a pair of keys – a public and a private key. Symmetric encryption is significantly faster than asymmetric encryption for encrypting large amounts of data, but key exchange poses a major challenge. Asymmetric encryption, while slower for bulk data, elegantly solves the key exchange problem and enables digital signatures.
The choice between symmetric and asymmetric encryption often involves a hybrid approach, leveraging the strengths of both methods. For instance, asymmetric encryption is used for secure key exchange, while symmetric encryption handles the actual data encryption and decryption.
Hashing Algorithms
Hashing algorithms are fundamental cryptographic tools used to ensure data integrity and enhance security, particularly in password management. They function by transforming input data of any size into a fixed-size string of characters, known as a hash. This process is designed to be one-way; it’s computationally infeasible to reverse the hash to obtain the original input. This one-way property is crucial for several security applications within server administration.Hashing algorithms like SHA-256 (Secure Hash Algorithm 256-bit) and MD5 (Message Digest Algorithm 5) are widely employed, though MD5 is now considered cryptographically broken due to vulnerabilities.
The strength of a hashing algorithm lies in its resistance to collisions and pre-image attacks.
SHA-256 and MD5 in Data Integrity and Password Security
SHA-256, a member of the SHA-2 family, is a widely accepted and robust hashing algorithm. Its 256-bit output significantly reduces the probability of collisions—where two different inputs produce the same hash. This characteristic is vital for verifying data integrity. For instance, a server can generate a SHA-256 hash of a file and store it alongside the file. Later, it can recalculate the hash and compare it to the stored value.
Any discrepancy indicates data corruption or tampering. In password security, SHA-256 (or other strong hashing algorithms like bcrypt or Argon2) hashes passwords before storing them. Even if a database is compromised, the attacker only obtains the hashes, not the plain-text passwords. Recovering the original password from a strong hash is computationally impractical. MD5, while historically popular, is now unsuitable for security-sensitive applications due to the discovery of efficient collision-finding techniques.
Its use should be avoided in modern server environments.
Collision Resistance in Hashing Algorithms
Collision resistance is a critical property of a secure hashing algorithm. It means that it is computationally infeasible to find two different inputs that produce the same hash value. A collision occurs when two distinct inputs generate identical hash outputs. If a hashing algorithm lacks sufficient collision resistance, an attacker could potentially create a malicious file with the same hash as a legitimate file, thus bypassing integrity checks.
The discovery of collision attacks against MD5 highlights the importance of using cryptographically secure hashing algorithms like SHA-256, which have a significantly higher resistance to collisions. The strength of collision resistance is directly related to the length of the hash output and the underlying mathematical design of the algorithm.
Verifying Data Integrity Using Hashing in a Server Environment
Hashing plays a vital role in ensuring data integrity within server environments. Consider a scenario where a large software update is downloaded to a server. The server administrator can generate a SHA-256 hash of the downloaded file and compare it to a previously published hash provided by the software vendor. This comparison verifies that the downloaded file is authentic and hasn’t been tampered with during transmission.
This technique is commonly used for software distribution, secure file transfers, and database backups. Discrepancies between the calculated and published hashes indicate potential issues, prompting investigation and preventing the deployment of corrupted data. This process adds a crucial layer of security, ensuring the reliability and trustworthiness of data within the server environment.
Digital Certificates and Public Key Infrastructure (PKI)
Digital certificates and Public Key Infrastructure (PKI) are crucial for establishing trust and securing communication in online environments, particularly for servers. They provide a mechanism to verify the identity of servers and other entities involved in a communication, ensuring that data exchanged is not intercepted or tampered with. This section will detail the components of a digital certificate, explain the workings of PKI, and illustrate its use in SSL/TLS handshakes.Digital certificates are essentially electronic documents that bind a public key to an identity.
This binding is verified by a trusted third party, a Certificate Authority (CA). The certificate contains information that allows a recipient to verify the authenticity and integrity of the public key. PKI provides the framework for issuing, managing, and revoking these certificates, creating a chain of trust that extends from the root CA down to individual certificates.
Digital Certificate Components and Purpose
A digital certificate contains several key components that work together to ensure its validity and secure communication. These components include:
- Subject: The entity (e.g., a server, individual, or organization) to which the certificate is issued. This includes details such as the common name (often the domain name for servers), organization name, and location.
- Issuer: The Certificate Authority (CA) that issued the certificate. This allows verification of the certificate’s authenticity by checking the CA’s digital signature.
- Public Key: The recipient’s public key, which can be used to encrypt data or verify digital signatures.
- Serial Number: A unique identifier for the certificate, used for tracking and management purposes within the PKI system.
- Validity Period: The date and time range during which the certificate is valid. After this period, the certificate is considered expired and should not be trusted.
- Digital Signature: The CA’s digital signature, verifying the certificate’s authenticity and integrity. This signature is created using the CA’s private key and can be verified using the CA’s public key.
- Extensions: Additional information that might be included, such as the intended use of the certificate (e.g., server authentication, email encryption), or Subject Alternative Names (SANs) to cover multiple domain names or IP addresses.
The purpose of a digital certificate is to provide assurance that the public key associated with the certificate truly belongs to the claimed entity. This is crucial for securing communication because it prevents man-in-the-middle attacks where an attacker impersonates a legitimate server.
PKI Operation and Trust Establishment
PKI establishes trust through a hierarchical structure of Certificate Authorities (CAs). Root CAs are at the top of the hierarchy, and their public keys are pre-installed in operating systems and browsers. These root CAs issue certificates to intermediate CAs, which in turn issue certificates to end entities (e.g., servers). This chain of trust allows verification of any certificate by tracing it back to a trusted root CA.
If a certificate’s digital signature can be successfully verified using the corresponding CA’s public key, then the certificate’s authenticity and the associated public key are considered valid. This process ensures that only authorized entities can use specific public keys.
Digital Certificates in SSL/TLS Handshakes
SSL/TLS handshakes utilize digital certificates to establish a secure connection between a client (e.g., a web browser) and a server. The process generally involves these steps:
- Client initiates connection: The client initiates a connection to the server, requesting a secure connection.
- Server sends certificate: The server responds by sending its digital certificate to the client.
- Client verifies certificate: The client verifies the server’s certificate by checking its digital signature using the CA’s public key. This verifies the server’s identity and the authenticity of its public key. The client also checks the certificate’s validity period and other relevant parameters.
- Key exchange: Once the certificate is verified, the client and server engage in a key exchange to establish a shared secret key for symmetric encryption. This key is used to encrypt all subsequent communication between the client and server.
- Secure communication: All further communication is encrypted using the shared secret key, ensuring confidentiality and integrity.
For example, when you visit a website using HTTPS, your browser performs an SSL/TLS handshake. The server presents its certificate, and your browser verifies it against its list of trusted root CAs. If the verification is successful, a secure connection is established, and your data is protected during transmission. Failure to verify the certificate will usually result in a warning or error message from your browser, indicating a potential security risk.
Secure Shell (SSH) and Secure Communication Protocols
Secure Shell (SSH) is a cornerstone of secure remote access, providing a crucial layer of protection for server administrators managing systems remotely. Its cryptographic foundation ensures confidentiality, integrity, and authentication, protecting sensitive data and preventing unauthorized access. This section delves into the cryptographic mechanisms within SSH and compares it to other secure remote access protocols, highlighting the critical role of strong SSH key management.SSH utilizes a combination of cryptographic techniques to establish and maintain a secure connection.
The process begins with key exchange, where the client and server negotiate a shared secret key. This key is then used to encrypt all subsequent communication. The most common key exchange algorithm used in SSH is Diffie-Hellman, which allows for secure key establishment over an insecure network. Following key exchange, symmetric encryption algorithms, such as AES (Advanced Encryption Standard), are employed to encrypt and decrypt the data exchanged between the client and server.
Furthermore, SSH incorporates message authentication codes (MACs), like HMAC (Hash-based Message Authentication Code), to ensure data integrity and prevent tampering. The authentication process itself can utilize password authentication, but the more secure method is public-key authentication, where the client authenticates itself to the server using a private key, corresponding to a public key stored on the server.
SSH Cryptographic Mechanisms
SSH leverages a multi-layered approach to security. The initial connection involves a handshake where the client and server negotiate the encryption algorithms and key exchange methods to be used. This negotiation is crucial for ensuring interoperability and adaptability to different security needs. Once a shared secret is established using a key exchange algorithm like Diffie-Hellman, symmetric encryption is used for all subsequent communication, significantly increasing speed compared to using asymmetric encryption for the entire session.
The chosen symmetric cipher, such as AES-256, encrypts the data, protecting its confidentiality. HMAC, using a strong hash function like SHA-256, adds a message authentication code to each packet, ensuring data integrity and preventing unauthorized modifications. Public-key cryptography, utilizing algorithms like RSA or ECDSA (Elliptic Curve Digital Signature Algorithm), is used for authentication, verifying the identity of the client to the server.
The client’s private key, kept secret, is used to generate a signature, which the server verifies using the client’s public key.
Comparison with Other Secure Remote Access Protocols
While SSH is the dominant protocol for secure remote access, other protocols exist, each with its strengths and weaknesses. For instance, Telnet, an older protocol, offers no encryption, making it highly vulnerable. Secure Telnet (STelnet) offers encryption but is less widely adopted than SSH. Other protocols, such as RDP (Remote Desktop Protocol) for Windows systems, provide secure remote access but often rely on proprietary mechanisms.
Compared to these, SSH stands out due to its open-source nature, widespread support across various operating systems, and robust cryptographic foundation. Its flexible architecture allows for the selection of strong encryption algorithms, making it adaptable to evolving security threats. The use of public-key authentication offers a more secure alternative to password-based authentication, mitigating the risks associated with password cracking.
SSH Key Management Best Practices
Strong SSH key management is paramount to the security of any system accessible via SSH. This includes generating strong keys with sufficient key length, storing private keys securely (ideally using a hardware security module or a secure key management system), regularly rotating keys, and implementing appropriate access controls. Using password-based authentication should be avoided whenever possible, in favor of public-key authentication, which offers a more robust and secure method.
Regular audits of authorized keys should be performed to ensure that only authorized users have access to the server. In addition, implementing SSH key revocation mechanisms is crucial to quickly disable access for compromised keys. Failure to follow these best practices significantly increases the vulnerability of systems to unauthorized access and data breaches. For example, a weak or compromised SSH key can allow attackers complete control over a server, leading to data theft, system compromise, or even complete system failure.
Securing Databases with Cryptography
Database security is paramount in today’s digital landscape, where sensitive personal and business information is routinely stored and processed. Protecting this data from unauthorized access, both when it’s at rest (stored on disk) and in transit (moving across a network), requires robust cryptographic techniques. This section explores various methods for encrypting database data and analyzes the associated trade-offs.Database encryption methods aim to render data unintelligible to anyone without the correct decryption key.
This prevents unauthorized access even if the database server itself is compromised. The choice of encryption method depends heavily on factors such as performance requirements, the sensitivity of the data, and the specific database management system (DBMS) in use.
Data Encryption at Rest
Encrypting data at rest protects information stored on the database server’s hard drives or SSDs. This is crucial because even if the server is physically stolen or compromised, the data remains inaccessible without the decryption key. Common methods include full-disk encryption, table-level encryption, and column-level encryption. Full-disk encryption protects the entire database storage device, offering broad protection but potentially impacting performance.
Table-level encryption encrypts entire tables, offering a balance between security and performance, while column-level encryption encrypts only specific columns containing sensitive data, offering granular control and optimized performance for less sensitive data. The choice between these depends on the specific security and performance needs. For instance, a system storing highly sensitive financial data might benefit from column-level encryption for crucial fields like credit card numbers while employing table-level encryption for less sensitive information.
Data Encryption in Transit
Protecting data as it moves between the database server and client applications is equally important. Encryption in transit prevents eavesdropping and man-in-the-middle attacks. This typically involves using Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to encrypt the connection between the database client and server. This ensures that all communication, including queries and data transfers, is protected from interception.
The implementation of TLS typically involves configuring the database server to use a specific TLS/SSL certificate and enabling encryption on the connection string within the database client applications. For example, a web application connecting to a database backend should use HTTPS to secure the communication channel.
Trade-offs Between Database Encryption Techniques
Different database encryption techniques present different trade-offs between security, performance, and complexity. Full-disk encryption offers the strongest protection but can significantly impact performance due to the overhead of encrypting and decrypting the entire storage device. Table-level and column-level encryption provide more granular control, allowing for optimized performance by only encrypting sensitive data. However, they require more careful planning and implementation to ensure that the correct columns or tables are encrypted.
The choice of method requires a careful assessment of the specific security requirements and performance constraints of the system. For example, a high-transaction volume system might prioritize column-level encryption for critical data fields to minimize performance impact.
Designing an Encryption Strategy for a Relational Database
A comprehensive strategy for encrypting sensitive data in a relational database involves several steps. First, identify all sensitive data that requires protection. This might include personally identifiable information (PII), financial data, or other confidential information. Next, choose the appropriate encryption method based on the sensitivity of the data and the performance requirements. For instance, a system with high performance needs and less sensitive data might use table-level encryption, while a system with stringent security requirements and highly sensitive data might opt for column-level encryption.
Finally, implement the chosen encryption method using the capabilities provided by the database management system (DBMS) or through external encryption tools. Regular key management and rotation are essential to maintaining the security of the encrypted data. Failure to properly manage keys can negate the benefits of encryption. For example, a robust key management system with secure storage and regular key rotation should be implemented.
Implementing and Managing Cryptographic Keys
Effective cryptographic key management is paramount for maintaining the security of a server environment. Neglecting this crucial aspect can lead to severe vulnerabilities, exposing sensitive data and systems to compromise. This section details best practices for generating, storing, managing, and rotating cryptographic keys, emphasizing the importance of a robust key lifecycle management plan.
Secure key management encompasses a range of practices aimed at minimizing the risks associated with weak or compromised keys. These practices are crucial because cryptographic algorithms rely entirely on the secrecy and integrity of their keys. A compromised key renders the entire cryptographic system vulnerable, regardless of the algorithm’s strength. Therefore, a well-defined key management strategy is a non-negotiable element of robust server security.
Key Generation Best Practices
Generating strong cryptographic keys involves employing robust random number generators (RNGs) and adhering to established key length recommendations. Weak or predictable keys are easily compromised, rendering encryption ineffective. The use of operating system-provided RNGs is generally recommended over custom implementations, as these are often rigorously tested and vetted for randomness. Key length should align with the algorithm used and the sensitivity of the data being protected; longer keys generally offer greater security.
Secure Key Storage
The secure storage of cryptographic keys is critical. Compromised storage mechanisms directly expose keys, defeating the purpose of encryption. Best practices involve utilizing hardware security modules (HSMs) whenever possible. HSMs provide a physically secure and tamper-resistant environment for key generation, storage, and management. If HSMs are unavailable, robust, encrypted file systems with strong access controls should be employed.
Keys should never be stored in plain text or easily accessible locations.
Key Management Risks
Weak key management practices expose organizations to a wide array of security risks. These risks include data breaches, unauthorized access to sensitive information, system compromise, and reputational damage. For instance, the use of weak or easily guessable passwords to protect keys can allow attackers to gain access to encrypted data. Similarly, storing keys in insecure locations or failing to rotate keys regularly can lead to prolonged vulnerability.
Key Rotation and Lifecycle Management
A well-defined key rotation and lifecycle management plan is essential for mitigating risks associated with long-term key use. Regular key rotation reduces the window of vulnerability in the event of a compromise. The frequency of key rotation depends on several factors, including the sensitivity of the data, the cryptographic algorithm used, and regulatory requirements. A comprehensive plan should detail procedures for generating, distributing, storing, using, and ultimately destroying keys at the end of their lifecycle.
This plan should also include procedures for handling key compromises.
Example Key Rotation Plan
A typical key rotation plan might involve rotating symmetric encryption keys every 90 days and asymmetric keys (like SSL/TLS certificates) annually, or according to the certificate’s validity period. Each rotation should involve generating a new key pair, securely distributing the new public key (if applicable), updating systems to use the new key, and securely destroying the old key pair.
Detailed logging and auditing of all key management activities are essential to ensure accountability and traceability.
Advanced Cryptographic Techniques for Server Security
Beyond the fundamental cryptographic principles, several advanced techniques significantly enhance server security. These methods offer stronger authentication, improved data integrity, and enhanced protection against sophisticated attacks, particularly relevant in today’s complex threat landscape. This section delves into three crucial advanced techniques: digital signatures, message authentication codes, and elliptic curve cryptography.
Digital Signatures for Authentication and Non-Repudiation
Digital signatures provide a mechanism to verify the authenticity and integrity of digital data. Unlike handwritten signatures, digital signatures leverage asymmetric cryptography to ensure non-repudiation—the inability of a signer to deny having signed a document. The process involves using a private key to create a signature for a message, which can then be verified by anyone using the corresponding public key.
This guarantees that the message originated from the claimed sender and hasn’t been tampered with. For example, a software update signed with the developer’s private key can be verified by users using the developer’s publicly available key, ensuring the update is legitimate and hasn’t been maliciously altered. The integrity is verified because any change to the message would invalidate the signature.
This is crucial for secure software distribution and preventing malicious code injection.
Message Authentication Codes (MACs) for Data Integrity
Message Authentication Codes (MACs) provide a method to ensure data integrity and authenticity. Unlike digital signatures, MACs utilize a shared secret key known only to the sender and receiver. A MAC is a cryptographic checksum generated using a secret key and the message itself. The receiver can then use the same secret key to calculate the MAC for the received message and compare it to the received MAC.
A match confirms both the integrity (the message hasn’t been altered) and authenticity (the message originated from the expected sender). MACs are commonly used in network protocols like IPsec to ensure the integrity of data packets during transmission. A mismatch indicates either tampering or an unauthorized sender. This is critical for securing sensitive data transmitted over potentially insecure networks.
Elliptic Curve Cryptography (ECC) in Securing Embedded Systems
Elliptic Curve Cryptography (ECC) offers a powerful alternative to traditional public-key cryptography, such as RSA. ECC achieves the same level of security with significantly shorter key lengths, making it particularly well-suited for resource-constrained environments like embedded systems. Embedded systems, found in many devices from smartcards to IoT sensors, often have limited processing power and memory. ECC’s smaller key sizes translate to faster encryption and decryption speeds and reduced storage requirements.
Understanding cryptography is crucial for server administrators, demanding a deep dive into its complexities. To truly master server security, however, you need to explore cutting-edge techniques, as detailed in this excellent resource: Unlock Server Security with Cutting-Edge Cryptography. This knowledge will significantly enhance your ability to implement robust security measures in “Cryptography for Server Admins: An In-Depth Look”.
This efficiency is crucial for securing these devices without compromising performance or security. For instance, ECC is widely used in securing communication between mobile devices and servers, minimizing the overhead on the mobile device’s battery life and processing capacity. The smaller key size also enhances the protection against side-channel attacks, which exploit information leaked during cryptographic operations.
Troubleshooting Cryptographic Issues on Servers
Implementing cryptography on servers is crucial for security, but misconfigurations or attacks can lead to vulnerabilities. This section details common problems, solutions, and attack response strategies. Effective troubleshooting requires a systematic approach, combining technical expertise with a strong understanding of cryptographic principles.
Common Cryptographic Configuration Errors
Incorrectly configured cryptographic systems are a frequent source of server vulnerabilities. These errors often stem from misunderstandings of key lengths, algorithm choices, or certificate management. For example, using outdated or weak encryption algorithms like DES or 3DES leaves systems susceptible to brute-force attacks. Similarly, improper certificate chain validation can lead to man-in-the-middle attacks. Failure to regularly rotate cryptographic keys weakens long-term security, as compromised keys can grant persistent access to attackers.
Finally, insufficient key management practices, including lack of proper storage and access controls, create significant risks.
Resolving Cryptographic Configuration Errors
Addressing configuration errors requires careful review of server logs and configurations. First, verify that all cryptographic algorithms and key lengths meet current security standards. NIST guidelines provide up-to-date recommendations. Next, meticulously check certificate chains for validity and proper trust relationships. Tools like OpenSSL can help validate certificates and identify potential issues.
Regular key rotation is essential; establish a schedule for key changes and automate the process where possible. Implement robust key management practices, including secure storage using hardware security modules (HSMs) and strict access control policies. Finally, thoroughly document all cryptographic configurations to aid in future troubleshooting and maintenance.
Detecting and Responding to Cryptographic Attacks, Cryptography for Server Admins: An In-Depth Look
Detecting cryptographic attacks often relies on monitoring system logs for suspicious activity. Unusual login attempts, unexpected certificate errors, or unusually high CPU usage related to cryptographic operations may indicate an attack. Intrusion detection systems (IDS) and security information and event management (SIEM) tools can help detect anomalous behavior. Regular security audits and penetration testing are vital for identifying vulnerabilities before attackers exploit them.
Responding to an attack involves immediate containment, damage assessment, and remediation. This may include disabling compromised services, revoking certificates, changing cryptographic keys, and patching vulnerabilities. Incident response plans should be developed and regularly tested to ensure effective and timely responses to security incidents. Post-incident analysis is crucial to understand the attack, improve security posture, and prevent future incidents.
End of Discussion
Securing server infrastructure requires a deep understanding of cryptographic principles and their practical applications. This in-depth look at cryptography for server administrators has highlighted the critical importance of robust encryption, secure key management, and the implementation of secure communication protocols. By mastering these concepts and best practices, you can significantly enhance the security posture of your server environments, protecting valuable data and mitigating potential threats.
The journey to a truly secure server infrastructure is ongoing, requiring constant vigilance and adaptation to evolving security landscapes.
Answers to Common Questions
What are the common types of cryptographic attacks server admins should be aware of?
Common attacks include brute-force attacks (against passwords or encryption keys), man-in-the-middle attacks (intercepting communication), and injection attacks (inserting malicious code). Understanding these threats is crucial for effective defense.
How often should cryptographic keys be rotated?
Key rotation frequency depends on the sensitivity of the data and the potential risk. Regular rotation, at least annually or even more frequently for high-risk scenarios, is a best practice to mitigate the impact of key compromise.
What are some open-source tools that can aid in cryptographic tasks?
OpenSSL is a widely used, powerful, and versatile command-line tool for various cryptographic operations. GnuPG provides encryption and digital signature capabilities. Many other tools exist, depending on specific needs.