Server Security 101: Cryptography Fundamentals delves into the crucial role cryptography plays in protecting your server infrastructure. In today’s interconnected world, where cyber threats are constantly evolving, understanding the fundamentals of cryptography is paramount for maintaining robust server security. This guide will explore various cryptographic techniques, from symmetric and asymmetric encryption to hashing algorithms and digital certificates, equipping you with the knowledge to safeguard your valuable data and systems.
We’ll examine the strengths and weaknesses of different encryption algorithms, explore the practical applications of public key infrastructure (PKI), and discuss the importance of secure key management. Furthermore, we’ll delve into the workings of SSL/TLS and SSH, vital protocols for securing internet communication and remote server access. By understanding these core concepts, you can significantly improve your server’s resilience against a wide range of attacks.
Introduction to Server Security
In today’s interconnected world, servers are the backbone of countless online services, from e-commerce platforms and social media networks to critical infrastructure and government systems. The security of these servers is paramount, as a breach can lead to significant financial losses, reputational damage, and even legal repercussions. Understanding the threats and implementing robust security measures is therefore not just a best practice, but a necessity for any organization operating online.Server security encompasses the protection of server hardware, software, and data from unauthorized access, use, disclosure, disruption, modification, or destruction.
A compromised server can expose sensitive customer data, intellectual property, and internal business operations, resulting in severe consequences. The increasing sophistication of cyberattacks necessitates a proactive and multi-layered approach to server security, with cryptography playing a crucial role.
Server Security Threats
Servers face a wide array of threats, constantly evolving in their methods and sophistication. These threats can be broadly categorized into several types, each demanding specific security countermeasures.
- Malware Infections: Viruses, worms, Trojans, and ransomware can compromise server systems, leading to data theft, system disruption, and data encryption for ransom. For example, the NotPetya ransomware attack in 2017 crippled numerous organizations worldwide, causing billions of dollars in damages.
- Denial-of-Service (DoS) Attacks: These attacks flood servers with traffic, making them unavailable to legitimate users. Distributed Denial-of-Service (DDoS) attacks, orchestrated from multiple sources, are particularly difficult to mitigate and can cause significant downtime.
- Unauthorized Access: Hackers can exploit vulnerabilities in server software or operating systems to gain unauthorized access, potentially stealing data or installing malware. Weak passwords, outdated software, and misconfigured security settings are common entry points.
- Data Breaches: The theft of sensitive data, such as customer information, financial records, or intellectual property, can have devastating consequences for organizations, leading to legal liabilities and reputational damage. The Equifax data breach in 2017, exposing the personal information of millions of individuals, serves as a stark reminder of the potential impact.
- Insider Threats: Malicious or negligent employees can pose a significant threat to server security. This can involve intentional data theft, accidental data leaks, or the introduction of malware.
Cryptography’s Role in Server Security
Cryptography is the cornerstone of modern server security, providing the tools and techniques to protect data confidentiality, integrity, and authenticity. It employs mathematical algorithms to transform data into an unreadable format (encryption), ensuring that only authorized parties can access it. Cryptography plays a vital role in several key aspects of server security:
- Data Encryption: Protecting data at rest (stored on the server) and in transit (being transmitted to and from the server) using encryption algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman). This prevents unauthorized access even if the server is compromised.
- Secure Communication: Establishing secure connections between servers and clients using protocols like TLS/SSL (Transport Layer Security/Secure Sockets Layer), which use cryptography to encrypt communication and verify the identity of parties involved. This is crucial for protecting sensitive data exchanged during online transactions.
- Authentication and Authorization: Verifying the identity of users and devices accessing the server using techniques like digital signatures and public key infrastructure (PKI). This ensures that only authorized individuals can access server resources.
- Data Integrity: Using cryptographic hash functions to verify the integrity of data, ensuring that it hasn’t been tampered with during transmission or storage. This helps detect any unauthorized modifications.
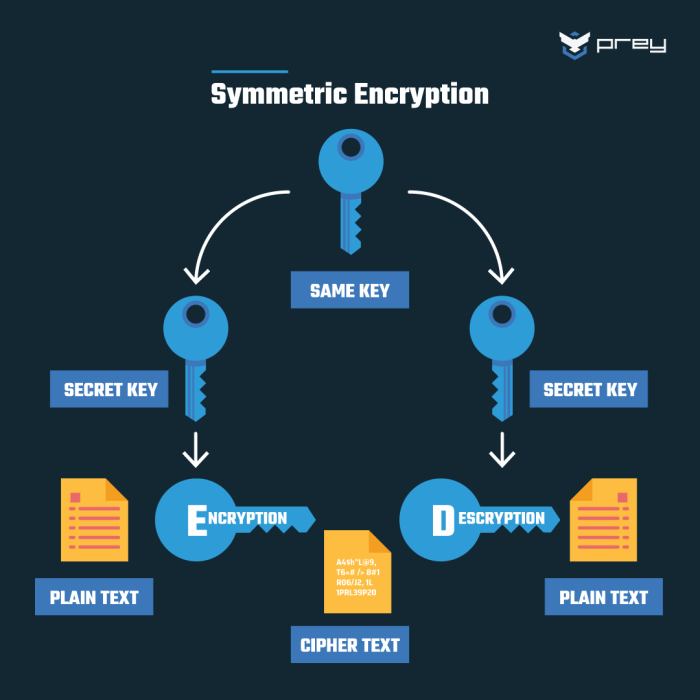
Symmetric-key Cryptography
Symmetric-key cryptography relies on a single, secret key to both encrypt and decrypt data. This shared secret must be securely distributed to all parties involved, making key management a crucial aspect of its implementation. The strength of symmetric encryption hinges on the algorithm’s complexity and the key’s length; longer keys generally offer greater security against brute-force attacks. Symmetric algorithms are generally faster and more efficient than asymmetric algorithms, making them suitable for encrypting large amounts of data.
Symmetric-key Algorithm Principles
Symmetric-key encryption involves transforming plaintext into ciphertext using a secret key. The same key, kept confidential, is then used to reverse the process, recovering the original plaintext. This process relies on a mathematical function, the encryption algorithm, that is computationally infeasible to reverse without possessing the correct key. The security of the system is directly dependent on the secrecy of this key and the robustness of the algorithm.
Compromising the key renders the entire encrypted data vulnerable.
Comparison of Symmetric-key Algorithms: AES, DES, 3DES, Server Security 101: Cryptography Fundamentals
Several symmetric-key algorithms exist, each with varying levels of security and performance characteristics. AES, DES, and 3DES are prominent examples. AES (Advanced Encryption Standard) is the current industry standard, offering superior security compared to its predecessors. DES (Data Encryption Standard) is an older algorithm considered insecure for modern applications due to its relatively short key length. 3DES (Triple DES) is a strengthened version of DES, applying the DES algorithm three times to enhance security, but it’s slower and less efficient than AES.
Strengths and Weaknesses of Symmetric-Key Algorithms
| Algorithm | Strengths | Weaknesses | Key Size (bits) |
|---|---|---|---|
| AES | High security, fast performance, widely adopted standard, flexible key sizes | Susceptible to side-channel attacks if not implemented carefully | 128, 192, 256 |
| DES | Simple to implement (historically) | Vulnerable to brute-force attacks due to its 56-bit key size, considered insecure for modern applications | 56 |
| 3DES | Improved security over DES, relatively simple to implement | Slower than AES, more complex than DES, potential vulnerabilities related to its underlying DES structure | 112 (effective) |
Asymmetric-key Cryptography
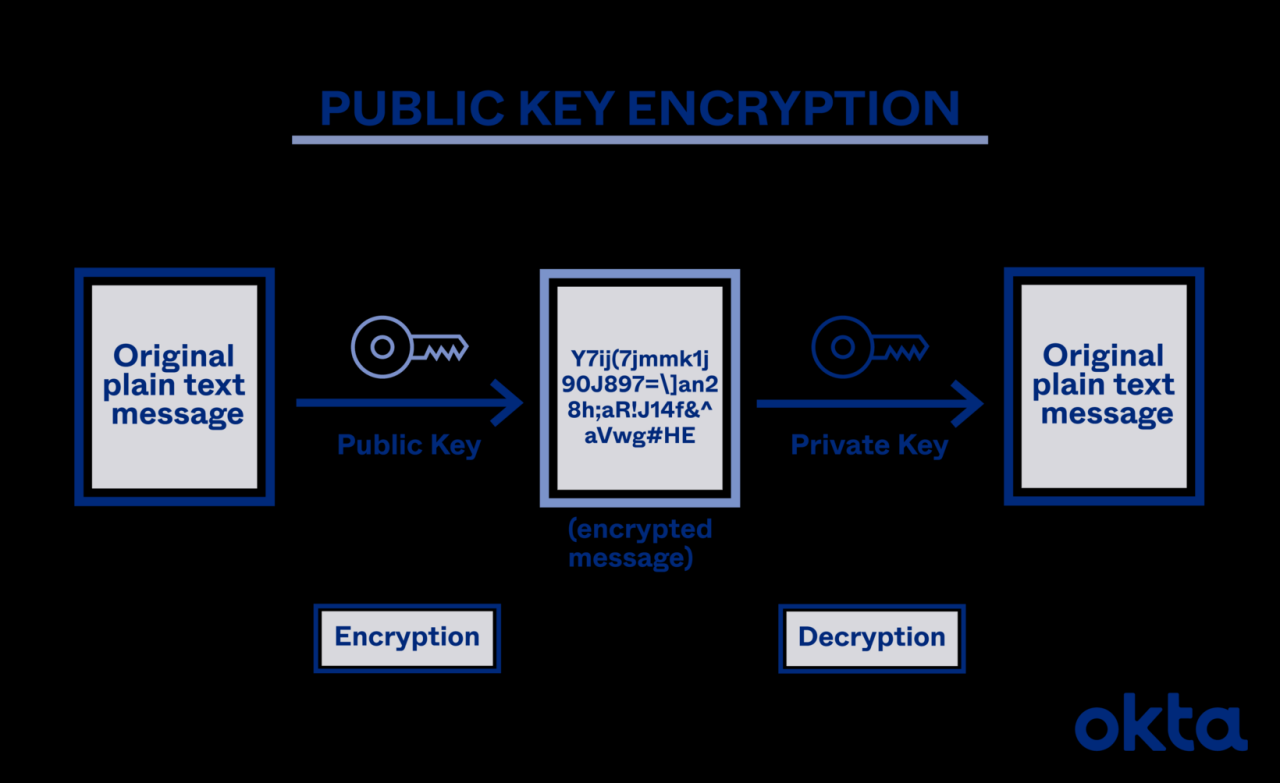
Asymmetric-key cryptography, also known as public-key cryptography, represents a fundamental shift from symmetric-key systems. Unlike symmetric encryption, which relies on a single secret key shared between parties, asymmetric cryptography employs a pair of keys: a public key and a private key. This key pair is mathematically linked, allowing for secure communication and digital signatures without the need to share a secret key directly.
This crucial difference enables secure communication over insecure channels, addressing a major limitation of symmetric systems.Asymmetric-key cryptography leverages the principle of one-way functions, mathematical operations that are easy to compute in one direction but computationally infeasible to reverse without possessing specific information (the private key). This one-way property forms the bedrock of its security.
Public and Private Keys
The public key, as its name suggests, can be freely distributed. Anyone can use the public key to encrypt a message intended for the holder of the corresponding private key. Only the holder of the private key, however, possesses the means to decrypt the message. Conversely, the private key can be used to create a digital signature, which can be verified using the corresponding public key.
This separation of keys provides a robust mechanism for authentication and confidentiality. The security of asymmetric cryptography rests on the computational difficulty of deriving the private key from the public key.
Understanding server security, starting with cryptography fundamentals, is crucial for protecting sensitive data. Efficiently managing this security, however, requires streamlined processes; consider optimizing your marketing efforts with strategies like those outlined in this excellent guide on 7 Cara Ampuh Marketing Automation: ROI Naik 300% to free up resources for robust security implementations. Ultimately, strong server security protects your business, and efficient processes enable you to dedicate more resources to those security measures.
RSA and ECC in Server Security
RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are two prominent asymmetric encryption algorithms widely used in server security. RSA, one of the oldest and most established algorithms, relies on the mathematical difficulty of factoring large numbers. Its strength is directly related to the size of the keys used; larger keys offer greater security but at the cost of increased computational overhead.
RSA is commonly used for securing HTTPS connections, digital signatures, and key exchange protocols.ECC, a more recent algorithm, offers comparable security to RSA with significantly smaller key sizes. This efficiency advantage makes ECC particularly attractive for resource-constrained devices and applications where bandwidth is a concern. ECC is increasingly favored in server security for its performance benefits and is used in various protocols and applications, including TLS (Transport Layer Security) and digital signature schemes.
The choice between RSA and ECC often depends on the specific security requirements and performance constraints of the application.
Digital Signatures for Authentication
Digital signatures provide a mechanism to verify the authenticity and integrity of digital data. In a typical scenario, a server needs to authenticate itself to a client. The server generates a digital signature using its private key on a message (e.g., a timestamp and other relevant data). The client then uses the server’s publicly available certificate (containing the public key) to verify the signature.
If the verification process succeeds, the client can be confident that the message originated from the legitimate server and hasn’t been tampered with.For example, consider a secure web server. The server possesses a private key and its corresponding public key is embedded within a digital certificate. When a client connects, the server presents this certificate. The client then verifies the certificate’s signature using a trusted root certificate authority, ensuring the server’s identity.
The server subsequently signs messages using its private key, allowing the client to verify the authenticity and integrity of communications. Failure to verify the signature would indicate a potential security breach or a man-in-the-middle attack.
Hashing Algorithms
Hashing algorithms are crucial for server security, providing a one-way function to transform data of any size into a fixed-size string of characters, known as a hash. This process is irreversible, meaning you cannot reconstruct the original data from the hash. This characteristic makes hashing invaluable for ensuring data integrity and securing passwords.Hashing algorithms are designed to be deterministic; the same input will always produce the same output.
However, even a tiny change in the input data will result in a significantly different hash, making them sensitive to alterations. This property is exploited to detect data tampering and verify data authenticity.
MD5, SHA-1, and SHA-256 Characteristics
The security and efficiency of hashing algorithms vary. MD5 (Message Digest Algorithm 5), SHA-1 (Secure Hash Algorithm 1), and SHA-256 (Secure Hash Algorithm 256-bit) are three widely used, yet distinct, algorithms. Understanding their differences is critical for choosing the right algorithm for a specific security need.
| Algorithm | Hash Size (bits) | Collision Resistance | Current Status |
|---|---|---|---|
| MD5 | 128 | Weak; collisions easily found | Deprecated; should not be used for security-sensitive applications |
| SHA-1 | 160 | Weak; practical collision attacks exist | Deprecated; should not be used for security-sensitive applications |
| SHA-256 | 256 | Strong; no known practical collision attacks | Recommended for most security applications |
MD5, despite its historical significance, is now considered cryptographically broken due to the discovery of practical collision attacks. This means that it’s possible to find two different inputs that produce the same MD5 hash, compromising its integrity. SHA-1, while stronger than MD5, also suffers from vulnerabilities and is considered deprecated. SHA-256, part of the SHA-2 family, offers significantly stronger collision resistance and is currently the recommended choice for most security applications.
Password Storage Using Hashing
Storing passwords directly in a database is extremely risky. Hashing provides a secure alternative. When a user registers, their password is hashed using a strong algorithm like SHA-256 (or bcrypt, scrypt, Argon2 which are key derivation functions designed specifically for password hashing). This hash is then stored in the database instead of the plain text password. When the user logs in, their entered password is hashed using the same algorithm, and the resulting hash is compared to the stored hash.
A match confirms the correct password without ever revealing the actual password in plain text. Adding a “salt” – a random string unique to each password – further enhances security, making it significantly harder for attackers to crack passwords even if they obtain the database. For example, a password “password123” salted with “uniqueSaltString” would produce a different hash than the same password salted with a different string.
Data Integrity Checks Using Hashing
Hashing is essential for verifying data integrity. A hash is generated for a file or data set before it’s transmitted or stored. Upon receiving or retrieving the data, the hash is recalculated. If the two hashes match, it confirms that the data hasn’t been tampered with during transmission or storage. This is widely used in software distribution (verifying that downloaded software hasn’t been modified), blockchain technology (ensuring the immutability of transactions), and many other applications where data integrity is paramount.
For instance, a software installer might include a SHA-256 hash of its files. Users can then independently calculate the hash of the downloaded files and compare it to the provided hash to verify the authenticity and integrity of the installation package.
Digital Certificates and Public Key Infrastructure (PKI)
Digital certificates are the cornerstone of secure server communication, providing a mechanism to verify the authenticity and integrity of websites and other online services. They act as digital IDs, binding a public key to an organization or individual, enabling secure communication and transactions over the internet. This section will explore the role of digital certificates and the Public Key Infrastructure (PKI) system that supports them.Digital certificates leverage asymmetric cryptography, employing a pair of mathematically linked keys: a public key and a private key.
The public key is freely distributed, while the private key remains strictly confidential. Digital certificates confirm the ownership of a public key, ensuring that communication with the intended party is genuine and not an imposter. This trust is crucial for secure interactions, from encrypted email to secure web browsing (HTTPS).
Digital Certificate Components
A digital certificate contains several key pieces of information that validate its authenticity and purpose. These components are crucial for verifying the identity of the certificate holder and ensuring the integrity of the certificate itself.
- Subject: This identifies the entity (individual, organization, or server) to whom the certificate is issued. This includes details such as the organization’s name, common name (e.g., www.example.com), and potentially other identifying information like location.
- Issuer: This indicates the Certificate Authority (CA) that issued the certificate. CAs are trusted third-party organizations responsible for verifying the identity of the certificate subject and guaranteeing the authenticity of the certificate.
- Public Key: The certificate contains the subject’s public key, which can be used to encrypt messages or verify digital signatures.
- Serial Number: A unique identifier assigned to the certificate by the issuing CA.
- Validity Period: The time frame during which the certificate is valid. After this period expires, the certificate is no longer trusted.
- Digital Signature: The CA’s digital signature ensures the certificate’s integrity. This signature, created using the CA’s private key, confirms that the certificate hasn’t been tampered with.
Public Key Infrastructure (PKI) Components
A PKI system is a complex infrastructure responsible for managing the lifecycle of digital certificates. Its various components work together to ensure the trustworthiness and security of digital certificates. A robust PKI system is essential for establishing and maintaining trust in online communications.
- Certificate Authorities (CAs): These are trusted third-party organizations responsible for issuing and managing digital certificates. They verify the identity of certificate applicants and issue certificates containing their public keys.
- Registration Authorities (RAs): RAs act as intermediaries between CAs and certificate applicants. They often handle the verification process, collecting necessary information from applicants before submitting it to the CA for certificate issuance.
- Certificate Revocation Lists (CRLs): CRLs are publicly accessible lists containing the serial numbers of revoked certificates. These certificates may be revoked due to compromise, expiration, or other reasons. Checking the CRL before trusting a certificate is a crucial security measure.
- Online Certificate Status Protocol (OCSP): OCSP is an alternative to CRLs that provides real-time certificate status checks. Instead of searching a potentially large CRL, an OCSP request is sent to an OCSP responder to determine the current status of a certificate.
- Repository: A secure location where certificates are stored and managed. This may be a central database or a distributed system, depending on the scale and complexity of the PKI system.
Obtaining and Using a Digital Certificate
The process of obtaining and using a digital certificate involves several steps, from the initial application to its eventual use in securing server communications. Each step is crucial for maintaining the security and trust associated with the certificate.
- Certificate Signing Request (CSR) Generation: The first step is generating a CSR. This involves creating a private key and a corresponding public key, and then creating a request containing the public key and relevant information about the certificate applicant.
- Certificate Authority Verification: The CSR is submitted to a CA or RA for verification. This process involves verifying the identity of the applicant and ensuring that they have the authority to request a certificate for the specified domain or entity.
- Certificate Issuance: Once the verification is complete, the CA issues a digital certificate containing the applicant’s public key and other relevant information. The certificate is digitally signed by the CA, ensuring its authenticity.
- Certificate Installation: The issued certificate is then installed on the server. This involves configuring the server to use the certificate for secure communication, typically by installing it in the server’s web server software (e.g., Apache or Nginx).
- Certificate Usage: Once installed, the server uses the certificate to establish secure connections with clients. When a client connects to the server, the server presents its certificate, allowing the client to verify the server’s identity and establish a secure encrypted connection.
Secure Socket Layer (SSL) / Transport Layer Security (TLS)
SSL/TLS are cryptographic protocols designed to provide secure communication over a computer network. They are essential for protecting sensitive data transmitted over the internet, ensuring confidentiality, integrity, and authenticity. This is achieved through the establishment of an encrypted connection between a client (like a web browser) and a server (like a web server). Without SSL/TLS, data transmitted between these two points would be vulnerable to interception and modification.SSL/TLS operates by creating a secure channel between the client and the server using a combination of symmetric and asymmetric cryptography, digital certificates, and hashing algorithms, all of which were discussed in previous sections.
This secure channel ensures that only the intended recipient can access the transmitted data, maintaining its confidentiality and preventing unauthorized access. Furthermore, it verifies the authenticity of the server, preventing man-in-the-middle attacks where a malicious actor intercepts the connection and impersonates the server.
The SSL/TLS Handshake Process
The SSL/TLS handshake is a critical process that establishes the secure connection between the client and the server. It involves a series of messages exchanged between the two parties to negotiate the security parameters and establish a shared secret key for symmetric encryption. The handshake process ensures that both parties agree on the encryption algorithms and cryptographic keys to be used for the session.
A failure at any stage of the handshake will prevent a secure connection from being established. This process is complex but crucial for the security of the communication.
Step-by-Step Explanation of Secure Communication using SSL/TLS
The establishment of a secure connection using SSL/TLS involves several key steps:
1. Client Hello
The client initiates the connection by sending a “Client Hello” message to the server. This message includes a list of supported cipher suites (combinations of encryption algorithms and hashing algorithms), the client’s random number, and other relevant information.
2. Server Hello
The server responds with a “Server Hello” message, selecting a cipher suite from the client’s list and sending its own random number. This message also includes the server’s certificate, which contains the server’s public key and other identifying information.
3. Certificate Verification
The client verifies the server’s certificate using the trusted Certificate Authority (CA) certificates stored in its trust store. This step ensures that the server is who it claims to be. If the certificate is invalid or untrusted, the client will terminate the connection.
4. Key Exchange
The client and server use the agreed-upon cipher suite and their respective random numbers to generate a shared secret key. This key is used for symmetric encryption of the subsequent communication. Different key exchange algorithms (like Diffie-Hellman) are used for this process, providing varying levels of security.
5. Change Cipher Spec
Both the client and the server send a “Change Cipher Spec” message to indicate that they will now begin using the newly generated shared secret key for symmetric encryption.
6. Finished
Both the client and the server send a “Finished” message, which is encrypted using the shared secret key. This message proves that both parties have successfully established the secure connection and confirms the integrity of the handshake process. The “Finished” message is essentially a hash of all the previous messages in the handshake, confirming that none have been tampered with.
7. Encrypted Communication
After the handshake is complete, all subsequent communication between the client and the server is encrypted using the shared secret key. This ensures that only the intended recipient can decipher the messages.
Secure Shell (SSH)
Secure Shell (SSH) is a cryptographic network protocol that provides a secure way to access and manage remote computers. It’s essential for server administration, allowing system administrators to execute commands, transfer files, and manage various aspects of a server securely over an untrusted network like the internet. Unlike less secure methods, SSH employs robust cryptographic techniques to protect against eavesdropping, tampering, and other attacks.SSH leverages cryptography for both authentication and encryption, ensuring only authorized users can access the server and that all communication remains confidential.
This is achieved through a combination of symmetric and asymmetric encryption algorithms, along with various authentication methods.
SSH Authentication Mechanisms
SSH offers several methods for verifying the identity of a user attempting to connect. These methods ensure that only legitimate users gain access to the server, preventing unauthorized access and potential security breaches. Common methods include password authentication, public key authentication, and certificate-based authentication. Each method offers varying levels of security, with public key authentication generally considered the most secure option.
SSH Encryption
SSH employs strong encryption to protect the confidentiality and integrity of data transmitted between the client and the server. This prevents eavesdropping and data manipulation during the session. The encryption process typically involves the exchange of cryptographic keys, ensuring secure communication throughout the connection. Different encryption algorithms, such as AES, are used depending on the SSH version and server configuration.
The choice of cipher suite influences the overall security of the SSH connection.
Securing SSH Configurations
Implementing robust security measures for SSH configurations is crucial to minimize vulnerabilities and protect against attacks. Several best practices should be followed to ensure optimal security.
SSH Port Change
Changing the default SSH port (port 22) is a fundamental step in enhancing security. Attackers frequently scan for this default port, so changing it makes it harder for automated attacks to find and compromise the server. This requires modifying the SSH configuration file (typically `sshd_config`) and restarting the SSH service. For example, changing the port to 2222 would require updating the `Port` directive in the configuration file.
Public Key Authentication
Public key authentication is significantly more secure than password authentication. It involves using a pair of cryptographic keys – a public key and a private key. The public key is placed on the server, while the private key is kept securely on the client machine. This method eliminates the risk of password guessing or brute-force attacks.
Disable Password Authentication
Once public key authentication is established, disabling password authentication entirely significantly strengthens security. This prevents attackers from attempting password-based attacks, even if they manage to gain access to the server through other means. This is accomplished by setting `PasswordAuthentication no` in the `sshd_config` file.
Regular Security Audits and Updates
Regular security audits are essential to identify and address any potential vulnerabilities. This includes checking for outdated SSH versions, weak cipher suites, and other misconfigurations. Keeping the SSH server software updated with the latest security patches is crucial to mitigate known vulnerabilities and protect against emerging threats. Regularly reviewing the server logs for suspicious activity is also a key aspect of security monitoring.
Restricting SSH Access
Limiting SSH access to only authorized users and IP addresses significantly reduces the attack surface. This can be achieved by configuring firewall rules to allow SSH connections only from specific IP addresses or networks. Additionally, using tools like `fail2ban` can help automatically block IP addresses that attempt multiple failed login attempts.
Regular Password Changes (if used)
If password authentication is used (although not recommended), enforcing strong passwords and implementing regular password change policies is crucial. Passwords should be complex and unique, combining uppercase and lowercase letters, numbers, and symbols. Regular password changes further mitigate the risk of compromised credentials.
Implementing Cryptography in Server Security
Implementing cryptographic solutions effectively is crucial for securing servers against various threats. This involves careful consideration of various factors, from algorithm selection to key management and performance optimization. Failure to properly implement cryptography can render even the most sophisticated security measures ineffective, leaving servers vulnerable to attacks.
Successful implementation hinges on a deep understanding of cryptographic principles and practical considerations. Choosing the right algorithms for specific needs, managing keys securely, and mitigating performance impacts are all critical aspects of a robust security posture. Ignoring these aspects can significantly compromise the overall security of the server infrastructure.
Key Management and Secure Storage
Secure key management is paramount to the success of any cryptographic system. Compromised keys render encryption useless, essentially granting attackers unrestricted access to sensitive data. Robust key management practices involve generating strong, unique keys, employing secure storage mechanisms (like hardware security modules or HSMs), and implementing strict access control policies. Regular key rotation is also essential to limit the impact of potential compromises.
For instance, a company might implement a policy to rotate its encryption keys every 90 days, rendering any previously stolen keys useless after that period. Furthermore, strong key generation algorithms must be used, ensuring keys possess sufficient entropy to resist brute-force attacks. The storage environment must also be physically secure and resistant to tampering.
Balancing Security and Performance
Cryptography, while essential for security, can introduce performance overhead. Stronger encryption algorithms generally require more processing power, potentially impacting server response times and overall application performance. Finding the right balance between security and performance requires careful consideration of the specific application requirements and risk tolerance. For example, a high-security financial transaction system might prioritize strong encryption, even at the cost of some performance, while a low-security website might opt for a faster but less secure algorithm.
Techniques like hardware acceleration (using specialized cryptographic processors) can help mitigate performance impacts without compromising security. Careful selection of algorithms and optimization strategies, such as using efficient implementations and caching, are also critical for balancing security and performance effectively.
Practical Considerations for Implementing Cryptographic Solutions
Successful cryptographic implementation demands a holistic approach. This involves not only selecting appropriate algorithms and managing keys securely but also considering the entire security lifecycle. This includes regular security audits, vulnerability assessments, and penetration testing to identify and address potential weaknesses. Additionally, staying updated with the latest cryptographic best practices and industry standards is crucial to maintain a strong security posture.
Proper configuration of cryptographic libraries and frameworks is equally vital, as misconfigurations can negate the security benefits of even the strongest algorithms. Finally, thorough documentation of cryptographic processes and procedures is crucial for maintainability and troubleshooting. This documentation should detail key management practices, algorithm choices, and any specific security configurations implemented.
Common Cryptographic Vulnerabilities
Cryptography, while a powerful tool for securing server systems, is only as strong as its implementation. Improper use can introduce significant vulnerabilities, leaving systems exposed to various attacks. Understanding these common weaknesses is crucial for building robust and secure server infrastructure.Weaknesses in cryptographic algorithms and key management practices are the primary causes of many security breaches. These weaknesses can range from the selection of outdated or easily broken algorithms to insufficient key length, improper key generation, and inadequate key protection.
The consequences of these vulnerabilities can be severe, leading to data breaches, system compromise, and significant financial losses.
Weak Encryption Algorithms
The selection of an encryption algorithm is paramount. Using outdated or inherently weak algorithms significantly increases the risk of successful attacks. For instance, algorithms like DES (Data Encryption Standard) and 3DES (Triple DES) are considered outdated and vulnerable to brute-force attacks due to their relatively short key lengths. Modern standards, such as AES (Advanced Encryption Standard) with sufficiently long key lengths (e.g., 256-bit), are recommended to mitigate this risk.
The failure to update to stronger algorithms leaves systems vulnerable to decryption by attackers with sufficient computational resources.
Flawed Key Management Practices
Secure key management is as crucial as the choice of algorithm itself. Weak key generation methods, insufficient key lengths, and poor key storage practices all contribute to cryptographic vulnerabilities. For example, using predictable or easily guessable keys renders encryption useless. Similarly, storing keys insecurely, such as in plain text within a configuration file, makes them readily available to attackers who gain unauthorized access to the server.
Proper key management involves generating cryptographically secure random keys, using appropriate key lengths, implementing robust key storage mechanisms (e.g., hardware security modules), and establishing secure key rotation policies.
Side-Channel Attacks
Side-channel attacks exploit information leaked during cryptographic operations, such as timing variations, power consumption, or electromagnetic emissions. These attacks do not directly target the cryptographic algorithm itself but rather the physical implementation of the algorithm. For example, an attacker might measure the time it takes for a cryptographic operation to complete and use this information to deduce parts of the secret key.
Mitigating side-channel attacks requires careful hardware and software design, often involving techniques like constant-time algorithms and masking.
Cryptographic Misuse
Improper use of cryptographic techniques can also lead to vulnerabilities. This includes using cryptography for purposes it’s not designed for, such as using encryption to protect data integrity instead of a dedicated hashing algorithm. Another example is failing to verify the authenticity of a digital certificate before establishing a secure connection. This can lead to man-in-the-middle attacks, where an attacker intercepts communication and impersonates a legitimate server.
Real-World Examples
The Heartbleed bug (CVE-2014-0160), affecting OpenSSL, allowed attackers to extract sensitive data from servers due to a flaw in the heartbeat extension. This vulnerability exploited a buffer overflow condition, allowing attackers to read memory regions containing private keys and other sensitive information. The attack demonstrated the severe consequences of flaws in widely used cryptographic libraries. The infamous 2017 Equifax data breach was partly attributed to the failure to patch a known vulnerability in the Apache Struts framework.
This vulnerability allowed attackers to remotely execute code on the server, leading to the compromise of sensitive customer data. Both examples highlight the importance of regular security updates and proper cryptographic implementation.
Future Trends in Server Security Cryptography
The landscape of server security is constantly evolving, driven by advancements in computing power and the emergence of new threats. Cryptography, the foundation of secure communication and data protection, is adapting to meet these challenges. This section explores emerging cryptographic techniques and their potential impact on securing servers in the future. We will examine the critical role of post-quantum cryptography and discuss ongoing challenges and future research directions in this dynamic field.The increasing sophistication of cyberattacks necessitates a continuous evolution of cryptographic methods.
Traditional algorithms, while effective in many current applications, face potential vulnerabilities as computing power increases and new attack vectors are discovered. Therefore, proactive research and development in cryptography are crucial for maintaining a strong security posture for servers.
Post-Quantum Cryptography
Post-quantum cryptography (PQC) focuses on developing cryptographic algorithms that are resistant to attacks from both classical computers and quantum computers. Quantum computers, with their potential to solve certain computational problems exponentially faster than classical computers, pose a significant threat to widely used public-key cryptosystems like RSA and ECC. The transition to PQC is a critical step in ensuring long-term server security.
Several promising PQC algorithms, such as lattice-based cryptography, code-based cryptography, and multivariate cryptography, are currently under evaluation and standardization by NIST (National Institute of Standards and Technology). The adoption of these algorithms will require significant changes in infrastructure and protocols, but it’s a necessary investment to protect against future quantum attacks. For instance, the migration to PQC could involve replacing existing SSL/TLS certificates with certificates based on PQC algorithms, requiring careful planning and phased implementation.
This transition presents a complex challenge, but the potential risk of a widespread breach due to quantum computing necessitates proactive measures.
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on encrypted data without first decrypting it. This technology holds significant promise for enhancing privacy in cloud computing and other distributed systems. Imagine a scenario where sensitive medical data is stored on a cloud server; homomorphic encryption could allow authorized parties to perform analysis on this data without ever accessing the decrypted information, thus ensuring patient privacy.
While still in its early stages of development, the successful implementation of fully homomorphic encryption could revolutionize data security and privacy, particularly in the context of server-based applications handling sensitive information. Challenges remain in terms of efficiency and practicality, but ongoing research is paving the way for more efficient and widely applicable homomorphic encryption schemes.
Lightweight Cryptography
The proliferation of IoT devices and resource-constrained environments necessitates the development of lightweight cryptography. These algorithms are designed to be efficient in terms of computational resources, memory, and power consumption, making them suitable for deployment on devices with limited capabilities. Lightweight cryptography is essential for securing communication and data integrity in resource-constrained environments like IoT devices, which are often targets for cyberattacks due to their limited security capabilities.
The development of efficient and secure lightweight cryptographic primitives is crucial for securing the growing number of connected devices and the data they generate and process. Examples include adapting existing algorithms for low-resource environments or developing entirely new, optimized algorithms.
Secure Multi-party Computation (MPC)
Secure multi-party computation (MPC) allows multiple parties to jointly compute a function over their private inputs without revealing anything beyond the output. This technique is particularly relevant for scenarios requiring collaborative computation without compromising individual data privacy. Imagine financial institutions needing to jointly compute a risk assessment without revealing their individual customer data; MPC could enable this secure collaboration.
While computationally intensive, advances in MPC techniques are making it increasingly practical for server-based applications. The growing adoption of MPC highlights its potential in various sectors, including finance, healthcare, and government, where secure collaborative computations are crucial.
Final Thoughts: Server Security 101: Cryptography Fundamentals
Mastering the fundamentals of cryptography is no longer optional; it’s a necessity for anyone responsible for server security. This guide has provided a foundational understanding of key cryptographic concepts and their practical applications in securing your server environment. From understanding the intricacies of encryption algorithms to implementing secure key management practices, you’re now better equipped to navigate the complexities of server security and protect your valuable data from malicious actors.
Remember, staying informed about emerging threats and evolving cryptographic techniques is crucial for maintaining a robust and secure server infrastructure in the long term.
Commonly Asked Questions
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption.
How often should I update my server’s SSL/TLS certificates?
SSL/TLS certificates should be renewed before their expiration date to avoid service interruptions. The exact renewal frequency depends on the certificate type but is typically between 1 and 2 years.
What are some common signs of a compromised server?
Unusual network activity, unauthorized access attempts, slow performance, and unexpected changes to files or system configurations are all potential indicators of a compromised server.
What is post-quantum cryptography?
Post-quantum cryptography refers to cryptographic algorithms that are designed to be secure even against attacks from quantum computers.