Cryptographic Keys: Unlocking Server Security – this exploration delves into the critical role of cryptographic keys in safeguarding server infrastructure. We’ll examine various key types, from symmetric to asymmetric, and their practical applications in securing data both at rest and in transit. Understanding key generation, management, and exchange is paramount; we’ll cover best practices, including secure key rotation and the utilization of hardware security modules (HSMs).
Further, we’ll navigate the complexities of Public Key Infrastructure (PKI) and its impact on server authentication, exploring potential vulnerabilities and mitigation strategies. Finally, we’ll address the emerging threat of quantum computing and the future of cryptography.
This journey will illuminate how these seemingly abstract concepts translate into tangible security measures for your servers, enabling you to build robust and resilient systems capable of withstanding modern cyber threats. We’ll compare encryption algorithms, discuss key exchange protocols, and analyze the potential impact of quantum computing on current security practices, equipping you with the knowledge to make informed decisions about securing your valuable data.
Introduction to Cryptographic Keys in Server Security
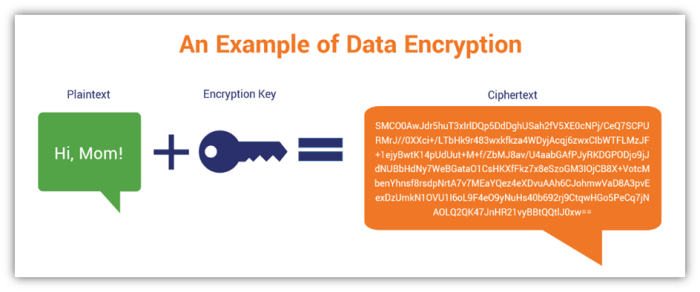
Cryptographic keys are fundamental to securing server infrastructure. They act as the gatekeepers of data, controlling access and ensuring confidentiality, integrity, and authenticity. Without robust key management, even the most sophisticated security measures are vulnerable. Understanding the different types of keys and their applications is crucial for building a secure server environment.Cryptographic keys are used in various algorithms to encrypt and decrypt data, protecting it from unauthorized access.
The strength of the encryption directly depends on the key’s length and the algorithm’s robustness. Improper key management practices, such as weak key generation or insecure storage, significantly weaken the overall security posture.
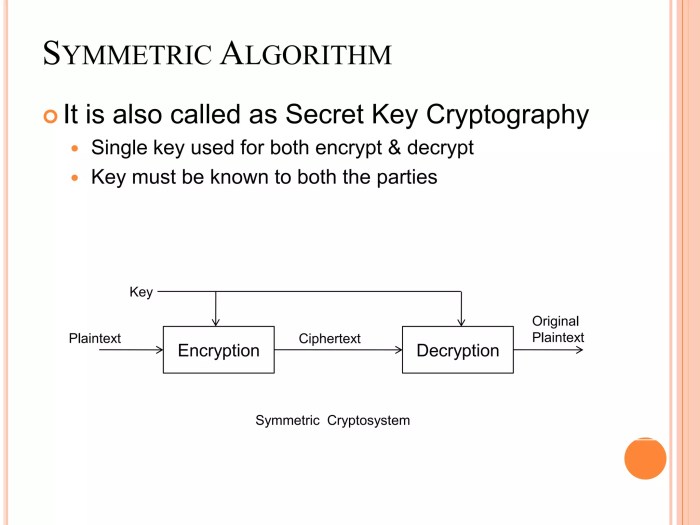
Symmetric Keys
Symmetric key cryptography uses a single secret key for both encryption and decryption. This means the same key is used to scramble the data and unscramble it later. The primary advantage of symmetric encryption is its speed and efficiency. It’s significantly faster than asymmetric encryption, making it suitable for encrypting large volumes of data. Examples of symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard), commonly used to protect data at rest on servers.
For instance, AES-256 is widely employed to encrypt databases and files stored on server hard drives. However, the secure distribution and management of the single key present a significant challenge.
Cryptographic keys are fundamental to securing servers, acting as the gatekeepers of sensitive data. Understanding how these keys function is crucial, especially when addressing vulnerabilities. For a deeper dive into mitigating these weaknesses, explore comprehensive strategies in our guide on Cryptographic Solutions for Server Vulnerabilities. Proper key management, including generation, storage, and rotation, remains paramount for robust server security.
Asymmetric Keys
Asymmetric key cryptography, also known as public-key cryptography, uses a pair of keys: a public key and a private key. The public key can be freely distributed, while the private key must be kept secret. Data encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. This solves the key distribution problem inherent in symmetric encryption.
Asymmetric encryption is slower than symmetric encryption but is crucial for tasks such as secure communication (TLS/SSL) and digital signatures. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are examples of asymmetric algorithms used to secure server communications. For example, HTTPS uses asymmetric encryption to establish a secure connection between a web browser and a web server, exchanging a symmetric key for subsequent communication.
Key Usage in Data Encryption
Data encryption, whether at rest or in transit, relies heavily on cryptographic keys. Data at rest refers to data stored on a server’s hard drive or other storage media. Data in transit refers to data being transmitted across a network. For data at rest, symmetric encryption is often preferred due to its speed. The data is encrypted using a symmetric key, and the key itself might be further encrypted using asymmetric encryption and stored securely.
For data in transit, asymmetric encryption is used to establish a secure connection and then a symmetric key is exchanged for encrypting the actual data. This hybrid approach leverages the strengths of both symmetric and asymmetric encryption. For instance, a file server might use AES-256 to encrypt files at rest, while the communication between the server and clients utilizes TLS/SSL, which involves asymmetric key exchange followed by symmetric encryption of the data being transferred.
Key Generation and Management Best Practices
Robust cryptographic key generation and management are paramount for maintaining the security of server infrastructure. Weak keys or compromised key management practices can severely undermine even the strongest encryption algorithms, leaving systems vulnerable to attack. This section details best practices for generating, storing, and rotating cryptographic keys to minimize these risks.
Secure Key Generation Methods
Secure key generation relies heavily on the quality of randomness used. Cryptographically secure pseudo-random number generators (CSPRNGs) are essential, as they produce sequences of numbers that are statistically indistinguishable from true randomness. These generators should be seeded with sufficient entropy, drawn from sources like hardware random number generators (HRNGs), system noise, and user interaction. Insufficient entropy leads to predictable keys, rendering them easily crackable.
Operating systems typically provide CSPRNGs; however, it’s crucial to verify their proper configuration and usage to ensure adequate entropy is incorporated. For high-security applications, dedicated hardware security modules (HSMs) are often preferred as they offer tamper-resistant environments for key generation and storage.
Key Storage Strategies
Storing cryptographic keys securely is as crucial as generating them properly. Compromised key storage can lead to immediate and catastrophic security breaches. Hardware Security Modules (HSMs) offer a robust solution, providing a physically secure and tamper-resistant environment for key generation, storage, and management. HSMs are specialized hardware devices that protect cryptographic keys from unauthorized access, even if the surrounding system is compromised.
For less sensitive keys, secure key management systems (KMS) offer a software-based alternative, often incorporating encryption and access control mechanisms to protect keys. These systems manage key lifecycles, access permissions, and auditing, but their security depends heavily on the underlying infrastructure’s security. The choice between HSMs and KMS depends on the sensitivity of the data being protected and the overall security posture of the organization.
Secure Key Rotation Policy
A well-defined key rotation policy is crucial for mitigating risks associated with compromised keys. Regular key rotation involves periodically generating new keys and replacing old ones. The frequency of rotation depends on the sensitivity of the data and the potential impact of a compromise. For highly sensitive data, frequent rotation, such as monthly or even weekly, may be necessary.
A key rotation policy should clearly define the key lifespan, the process for generating new keys, the secure destruction of old keys, and the procedures for transitioning to the new keys. A robust audit trail should track all key generation, usage, and rotation events. This policy should be regularly reviewed and updated to reflect changes in the threat landscape and security best practices.
Comparison of Key Management Solutions
| Solution Name | Features | Security Level | Cost |
|---|---|---|---|
| Hardware Security Module (HSM) | Tamper-resistant hardware, key generation, storage, and management, strong access control | Very High | High |
| Cloud Key Management Service (e.g., AWS KMS, Azure Key Vault, Google Cloud KMS) | Centralized key management, integration with cloud services, key rotation, auditing | High | Medium to High (depending on usage) |
| Open-Source Key Management System (e.g., HashiCorp Vault) | Flexible, customizable, supports various key types and backends | Medium to High (depending on implementation and infrastructure) | Low to Medium |
| Self-Managed Key Management System (custom solution) | Highly customized, tailored to specific needs | Variable (highly dependent on implementation) | Medium to High (requires significant expertise and infrastructure) |
Symmetric vs. Asymmetric Encryption in Server Security
Server security relies heavily on encryption to protect sensitive data. Choosing between symmetric and asymmetric encryption methods depends on the specific security needs and trade-offs between speed, security, and key management complexity. Understanding these differences is crucial for effective server security implementation.Symmetric and asymmetric encryption differ fundamentally in how they handle encryption and decryption keys. Symmetric encryption uses the same secret key for both processes, while asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption.
This key management difference leads to significant variations in their performance characteristics and security implications.
Comparison of Symmetric and Asymmetric Encryption Algorithms
Symmetric encryption algorithms are generally faster than asymmetric algorithms. This speed advantage stems from their simpler mathematical operations. However, secure key exchange presents a significant challenge with symmetric encryption, as the shared secret key must be transmitted securely. Asymmetric encryption, while slower, solves this problem by using a public key for encryption, which can be openly distributed.
The private key remains secret and is only used for decryption. Symmetric algorithms offer stronger encryption for the same key size compared to asymmetric algorithms, but the key exchange vulnerability offsets this advantage in many scenarios.
Examples of Symmetric and Asymmetric Encryption Algorithms
Several symmetric and asymmetric algorithms are commonly used in server security. Examples of symmetric algorithms include Advanced Encryption Standard (AES), which is widely considered the industry standard for its speed and robust security, and Triple DES (3DES), an older but still used algorithm. Examples of asymmetric algorithms include RSA, a widely used algorithm based on the difficulty of factoring large numbers, and Elliptic Curve Cryptography (ECC), which offers comparable security with smaller key sizes, leading to performance advantages.
Use Cases for Symmetric and Asymmetric Encryption in Server Security
The choice between symmetric and asymmetric encryption depends on the specific application. Symmetric encryption is ideal for encrypting large amounts of data, such as databases or file backups, where speed is critical. For example, AES is frequently used to encrypt data at rest within a database. Asymmetric encryption is better suited for tasks like secure key exchange, digital signatures, and encrypting small amounts of data, such as communication between servers or authentication credentials.
For instance, RSA is often used to encrypt communication channels using techniques like TLS/SSL. A common hybrid approach involves using asymmetric encryption to securely exchange a symmetric key, then using the faster symmetric encryption for the bulk data transfer. This combines the strengths of both methods.
Public Key Infrastructure (PKI) and Server Authentication
Public Key Infrastructure (PKI) is a crucial system for securing server communication and establishing trust in the digital world. It provides a framework for issuing and managing digital certificates, which act as verifiable digital identities for servers and other entities. By leveraging asymmetric cryptography, PKI ensures the confidentiality, integrity, and authenticity of online interactions. This section will detail the components of PKI and explain how it enables secure server authentication.
PKI Components and Their Roles
A functioning PKI system relies on several key components working together. These components ensure the secure generation, distribution, and validation of digital certificates. Understanding these components is crucial for implementing and managing a robust PKI system.
- Certificate Authority (CA): The CA is the trusted third party responsible for issuing and managing digital certificates. It verifies the identity of the certificate applicant and ensures the certificate’s validity. Think of a CA as a trusted notary public in the digital realm. Well-known CAs include DigiCert, Let’s Encrypt, and Sectigo. Their trustworthiness is established through rigorous audits and adherence to industry best practices.
- Registration Authority (RA): In larger PKI deployments, RAs act as intermediaries between the CA and certificate applicants. They handle the verification process, reducing the workload on the CA. Not all PKI systems utilize RAs; smaller systems often have the CA handle registration directly.
- Digital Certificates: These are electronic documents that contain the public key of a server (or other entity), along with information about the server’s identity, such as its domain name and the CA that issued the certificate. The certificate also includes a digital signature from the CA, which verifies its authenticity.
- Certificate Revocation List (CRL): This list contains the serial numbers of certificates that have been revoked by the CA. Revocation is necessary if a certificate is compromised or its validity needs to be terminated. Clients can check the CRL to ensure that a certificate is still valid.
- Online Certificate Status Protocol (OCSP): OCSP is a more efficient alternative to CRLs. Instead of downloading a potentially large CRL, clients query an OCSP responder to check the status of a specific certificate. This provides faster and more real-time validation.
Server Authentication Using Digital Certificates
Digital certificates are the cornerstone of server authentication within a PKI system. When a client connects to a server, the server presents its digital certificate to the client. The client then verifies the certificate’s authenticity by checking the CA’s digital signature and ensuring the certificate hasn’t been revoked. This process ensures that the client is communicating with the legitimate server and not an imposter.
Implementing Server Authentication with PKI: A Step-by-Step Process
Implementing server authentication using PKI involves several steps. Each step is crucial for establishing a secure and trusted connection.
- Generate a Certificate Signing Request (CSR): The server administrator generates a CSR, which includes the server’s public key and other identifying information.
- Obtain a Digital Certificate: The CSR is submitted to a CA (or RA). The CA verifies the server’s identity and, upon successful verification, issues a digital certificate.
- Install the Certificate: The issued digital certificate is installed on the server’s web server software (e.g., Apache, Nginx).
- Configure Server Software: The web server software is configured to present the digital certificate to clients during the SSL/TLS handshake.
- Client Verification: When a client connects to the server, the client’s browser (or other client software) verifies the server’s certificate, checking its validity and authenticity. If the verification is successful, a secure connection is established.
Securing Key Exchange and Distribution
Securely exchanging cryptographic keys between servers and clients is paramount for maintaining the confidentiality and integrity of data transmitted across a network. A compromised key exchange process can render even the strongest encryption algorithms ineffective, leaving sensitive information vulnerable to attack. This section explores various methods for secure key exchange, potential vulnerabilities, and best practices for mitigating risks.The process of key exchange necessitates robust mechanisms to prevent eavesdropping and manipulation.
Failure to adequately secure this process can lead to man-in-the-middle attacks, where an attacker intercepts and replaces legitimate keys, gaining unauthorized access to encrypted communications. Therefore, selecting appropriate key exchange protocols and implementing rigorous security measures is critical for maintaining a secure server environment.
Diffie-Hellman Key Exchange and its Variants
The Diffie-Hellman key exchange (DH) is a widely used method for establishing a shared secret key between two parties over an insecure channel. It relies on the mathematical properties of modular arithmetic to achieve this. Both parties agree on a public modulus (p) and a base (g), then each generates a private key (a and b respectively). They exchange public keys (g a mod p and g b mod p), and compute the shared secret key using their private key and the other party’s public key.
The resulting shared secret is identical for both parties, and is used for subsequent symmetric encryption. Variants like Elliptic Curve Diffie-Hellman (ECDH) offer improved efficiency and security for the same level of cryptographic strength. However, the security of DH relies on the computational difficulty of the discrete logarithm problem. Quantum computing advancements pose a long-term threat to the security of standard DH, making ECDH a more future-proof option.
Vulnerabilities in Key Exchange and Mitigation Strategies
A significant vulnerability in key exchange lies in the possibility of man-in-the-middle (MITM) attacks. An attacker could intercept the public keys exchanged between two parties, replacing them with their own. This allows the attacker to decrypt and encrypt communications between the legitimate parties, remaining undetected. To mitigate this, digital signatures and certificates are essential. These ensure the authenticity of the exchanged keys, verifying that they originated from the expected parties.
Furthermore, perfect forward secrecy (PFS) is crucial. PFS ensures that even if a long-term private key is compromised, past communications remain secure because they were encrypted with ephemeral keys generated for each session. Using strong, well-vetted cryptographic libraries and keeping them updated is also essential in mitigating vulnerabilities.
Best Practices for Key Protection During Distribution and Transit
Protecting keys during distribution and transit is crucial. Keys should never be transmitted in plain text. Instead, they should be encrypted using a robust encryption algorithm with a strong key management system. Hardware security modules (HSMs) provide a highly secure environment for key generation, storage, and management. Keys should be regularly rotated to limit the impact of any potential compromise.
The use of secure channels, such as TLS/SSL, is vital when transferring keys over a network. Strict access control measures, including role-based access control (RBAC), should be implemented to limit who can access and manage cryptographic keys.
Common Key Exchange Protocols: Strengths and Weaknesses
Understanding the strengths and weaknesses of different key exchange protocols is vital for selecting the appropriate one for a given application. Here’s a comparison:
- Diffie-Hellman (DH): Widely used, relatively simple to implement. Vulnerable to MITM attacks without additional security measures. Susceptible to quantum computing attacks in the long term.
- Elliptic Curve Diffie-Hellman (ECDH): Offers improved efficiency and security compared to DH, using elliptic curve cryptography. More resistant to quantum computing attacks than standard DH, but still vulnerable to MITM attacks without additional measures.
- Transport Layer Security (TLS): A widely used protocol that incorporates key exchange mechanisms, such as ECDHE (Elliptic Curve Diffie-Hellman Ephemeral). Provides confidentiality, integrity, and authentication, mitigating many vulnerabilities associated with simpler key exchange methods. However, its complexity can make implementation and management challenging.
- Signal Protocol: Designed for end-to-end encryption in messaging applications. It uses a combination of techniques including double ratchet algorithms for forward secrecy and perfect forward secrecy. Highly secure but complex to implement. Requires careful consideration of session resumption and key rotation.
Impact of Quantum Computing on Cryptographic Keys: Cryptographic Keys: Unlocking Server Security
The advent of powerful quantum computers presents a significant threat to the security of current cryptographic systems. Algorithms that are computationally infeasible to break with classical computers could be rendered vulnerable by the unique capabilities of quantum algorithms, potentially jeopardizing sensitive data and infrastructure worldwide. This necessitates a proactive approach to developing and implementing post-quantum cryptography to safeguard against this emerging threat.The potential for quantum computers to break widely used encryption algorithms stems from Shor’s algorithm.
Unlike classical algorithms, Shor’s algorithm can efficiently factor large numbers and solve the discrete logarithm problem, both of which are fundamental to the security of many public-key cryptosystems such as RSA and ECC. This means that quantum computers could decrypt communications and access data protected by these algorithms with relative ease, undermining the confidentiality and integrity of digital information.
Threats Posed by Quantum Computing to Current Cryptographic Algorithms
Shor’s algorithm directly threatens the widely used RSA and ECC algorithms, which rely on the computational difficulty of factoring large numbers and solving the discrete logarithm problem, respectively. These algorithms underpin much of our current online security, from secure web browsing (HTTPS) to digital signatures and secure communication protocols. A sufficiently powerful quantum computer could break these algorithms, potentially leading to massive data breaches and the compromise of sensitive information.
Furthermore, the impact extends beyond public-key cryptography; Grover’s algorithm, while less impactful than Shor’s, could also speed up brute-force attacks against symmetric-key algorithms, reducing their effective key lengths and weakening their security. This means that longer keys would be required to maintain a comparable level of security, potentially impacting performance and resource utilization.
Post-Quantum Cryptography Development and Implementation, Cryptographic Keys: Unlocking Server Security
Recognizing the potential threat, the global cryptographic community has been actively engaged in developing post-quantum cryptography (PQC). PQC encompasses cryptographic algorithms designed to be secure against both classical and quantum computers. Several promising candidates are currently under consideration by standardization bodies such as NIST (National Institute of Standards and Technology). The standardization process involves rigorous analysis and testing to ensure the selected algorithms are secure, efficient, and practical for widespread implementation.
This includes evaluating their performance characteristics across different platforms and considering their suitability for various applications. The transition to PQC will be a gradual process, requiring careful planning and coordination to minimize disruption and ensure a smooth migration path. Governments and organizations are investing heavily in research and development to accelerate the adoption of PQC.
Emerging Cryptographic Algorithms Resistant to Quantum Attacks
Several promising cryptographic algorithms are emerging as potential replacements for currently used algorithms vulnerable to quantum attacks. These algorithms fall into several categories, including lattice-based cryptography, code-based cryptography, multivariate cryptography, hash-based cryptography, and isogeny-based cryptography. Lattice-based cryptography, for example, relies on the computational hardness of problems related to lattices in high-dimensional spaces. Code-based cryptography utilizes error-correcting codes to create secure cryptosystems.
These algorithms offer varying levels of security and efficiency, and the optimal choice will depend on the specific application and security requirements. NIST’s ongoing standardization effort will help identify and recommend suitable algorithms for widespread adoption.
Illustrative Example of Quantum Computer Breaking Current Encryption
Imagine a scenario where a malicious actor gains access to a powerful quantum computer. This computer could be used to break the RSA encryption protecting a major bank’s online transaction system. By applying Shor’s algorithm, the quantum computer could efficiently factor the large numbers that constitute the bank’s RSA keys, thus decrypting the encrypted communications and gaining access to sensitive financial data such as account numbers, transaction details, and customer information.
This could result in significant financial losses for the bank, identity theft for customers, and a major erosion of public trust. The scale of such a breach could be far greater than any breach achieved using classical computing methods, highlighting the critical need for post-quantum cryptography.
Wrap-Up

Securing your server infrastructure hinges on a comprehensive understanding and implementation of cryptographic key management. From secure key generation and robust rotation policies to leveraging PKI for authentication and anticipating the challenges posed by quantum computing, a multi-faceted approach is essential. By mastering the principles discussed, you can significantly enhance your server’s security posture, protecting sensitive data and maintaining operational integrity in an increasingly complex threat landscape.
The journey into cryptographic keys might seem daunting, but the rewards – a secure and reliable server environment – are well worth the effort.
Question & Answer Hub
What is the difference between a symmetric and an asymmetric key?
Symmetric keys use the same key for encryption and decryption, offering speed but requiring secure key exchange. Asymmetric keys use a pair (public and private), enhancing security by only needing to share the public key, but at the cost of slower processing.
How often should I rotate my cryptographic keys?
Key rotation frequency depends on the sensitivity of the data and the risk tolerance. Regular, scheduled rotations, perhaps annually or even more frequently for high-value assets, are recommended to mitigate the impact of key compromise.
What are some common key exchange protocols?
Common protocols include Diffie-Hellman, RSA, and Elliptic Curve Diffie-Hellman (ECDH). Each has strengths and weaknesses regarding speed, security, and key size. The choice depends on specific security requirements.
What is post-quantum cryptography?
Post-quantum cryptography refers to cryptographic algorithms designed to be resistant to attacks from quantum computers. These are actively being developed to replace current algorithms vulnerable to quantum computing power.