Cryptography: The Future of Server Security. This isn’t just about keeping data safe; it’s about securing the very foundation of our digital world. As cyber threats evolve with breathtaking speed, so too must our defenses. This exploration delves into the cutting-edge cryptographic techniques shaping the future of server protection, from post-quantum cryptography and blockchain integration to homomorphic encryption and the transformative potential of zero-knowledge proofs.
We’ll examine how these innovations are strengthening server security, mitigating emerging threats, and paving the way for a more secure digital landscape.
The journey ahead will cover the fundamental principles of cryptography, comparing symmetric and asymmetric encryption methods, and then delve into the implications of quantum computing and the urgent need for post-quantum cryptography. We’ll explore the role of blockchain in enhancing data integrity, the possibilities of homomorphic encryption for secure cloud computing, and the use of zero-knowledge proofs for secure authentication.
Finally, we’ll investigate the crucial role of hardware-based security and discuss the ethical considerations surrounding these powerful technologies.
Introduction to Cryptography in Server Security
Cryptography is the cornerstone of modern server security, providing the essential mechanisms to protect data confidentiality, integrity, and authenticity. Without robust cryptographic techniques, sensitive information stored on and transmitted through servers would be vulnerable to eavesdropping, tampering, and forgery, rendering online services unreliable and insecure. This section explores the fundamental principles of cryptography, its historical evolution, and a comparison of key encryption methods used in securing servers.
At its core, cryptography involves transforming readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic algorithm and a key. The process of transforming plaintext into ciphertext is called encryption, while the reverse process, transforming ciphertext back into plaintext, is called decryption. The security of the system relies heavily on the secrecy and strength of the key, the complexity of the algorithm, and the proper implementation of cryptographic protocols.
Evolution of Cryptographic Techniques in Server Protection
Early cryptographic techniques, such as the Caesar cipher (a simple substitution cipher), were easily broken. However, the development of more sophisticated techniques, including symmetric and asymmetric encryption, significantly improved server security. The advent of digital signatures and hash functions further enhanced the ability to verify data integrity and authenticity. The transition from simpler, easily-breakable algorithms to complex, computationally intensive algorithms like AES and RSA reflects this evolution.
Cryptography: The Future of Server Security hinges on proactive measures against evolving threats. Understanding how to effectively mitigate vulnerabilities is crucial, and a deep dive into Cryptographic Solutions for Server Vulnerabilities offers valuable insights. This knowledge empowers developers to build robust, secure server infrastructures, ultimately shaping the future of online safety.
The increasing processing power of computers has driven the need for ever more robust cryptographic methods, and this ongoing arms race between attackers and defenders continues to shape the field. Modern server security relies on a layered approach, combining multiple cryptographic techniques to achieve a high level of protection.
Symmetric and Asymmetric Encryption Methods in Server Contexts
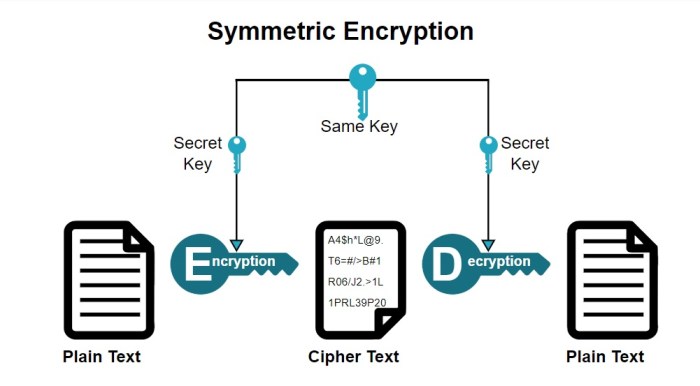
Symmetric encryption uses the same key for both encryption and decryption. This method is generally faster than asymmetric encryption, making it suitable for encrypting large amounts of data. Examples of widely used symmetric algorithms include Advanced Encryption Standard (AES) and Triple DES (3DES). However, the secure exchange of the secret key poses a significant challenge. The key must be transmitted securely to all parties involved, often through a separate, secure channel.
Compromise of this key compromises the entire system.
Asymmetric encryption, also known as public-key cryptography, uses two separate keys: a public key for encryption and a private key for decryption. The public key can be widely distributed, while the private key must be kept secret. This eliminates the need for secure key exchange, as the sender uses the recipient’s public key to encrypt the message, and only the recipient with the corresponding private key can decrypt it.
RSA and Elliptic Curve Cryptography (ECC) are prominent examples of asymmetric algorithms frequently used for secure communication and digital signatures in server environments. While slower than symmetric encryption, asymmetric methods are crucial for key exchange and digital signatures, forming the foundation of many secure protocols like TLS/SSL.
In practice, many server-side security systems utilize a hybrid approach, combining the strengths of both symmetric and asymmetric encryption. For instance, TLS/SSL uses asymmetric encryption to establish a secure connection and exchange a symmetric key, which is then used for faster, symmetric encryption of the subsequent data exchange. This approach balances the speed of symmetric encryption with the secure key exchange capabilities of asymmetric encryption, resulting in a robust and efficient security system for servers.
Post-Quantum Cryptography and its Implications
The advent of quantum computing presents a significant threat to the security of current cryptographic systems. Quantum computers, leveraging the principles of quantum mechanics, possess the potential to break widely used public-key algorithms like RSA and ECC, rendering much of our current online security infrastructure vulnerable. This necessitates a proactive shift towards post-quantum cryptography (PQC), algorithms designed to resist attacks from both classical and quantum computers.
The transition to PQC is not merely a technological upgrade; it’s a crucial step in safeguarding sensitive data and maintaining the integrity of digital systems in the quantum era.Post-Quantum Cryptography Algorithm Transition StrategiesThe transition to post-quantum cryptography requires a carefully planned and phased approach. A rushed implementation could lead to unforeseen vulnerabilities and compatibility issues. A successful migration involves several key stages: assessment of existing cryptographic infrastructure, selection of appropriate post-quantum algorithms, implementation and testing of new algorithms, and finally, the phased deployment and retirement of legacy systems.
This process demands collaboration between researchers, developers, and policymakers to ensure a smooth and secure transition. For example, NIST’s standardization process for PQC algorithms provides a framework for evaluating and selecting suitable candidates, guiding organizations in their migration efforts. Furthermore, open-source libraries and tools are crucial for facilitating widespread adoption and reducing the barriers to entry for organizations of all sizes.
Post-Quantum Cryptographic Algorithm Comparison, Cryptography: The Future of Server Security
The following table compares some existing and post-quantum cryptographic algorithms, highlighting their strengths and weaknesses. Algorithm selection depends on specific security requirements, performance constraints, and implementation complexities.
| Algorithm | Type | Strengths | Weaknesses |
|---|---|---|---|
| RSA | Public-key | Widely deployed, well-understood | Vulnerable to Shor’s algorithm on quantum computers, computationally expensive for large key sizes |
| ECC (Elliptic Curve Cryptography) | Public-key | More efficient than RSA for comparable security levels | Vulnerable to Shor’s algorithm on quantum computers |
| CRYSTALS-Kyber | Public-key (lattice-based) | Fast, relatively small key sizes, considered secure against quantum attacks | Relatively new, ongoing research into potential vulnerabilities |
| CRYSTALS-Dilithium | Digital signature (lattice-based) | Fast, relatively small signature sizes, considered secure against quantum attacks | Relatively new, ongoing research into potential vulnerabilities |
| Falcon | Digital signature (lattice-based) | Compact signatures, good performance | Slightly slower than Dilithium |
| SPHINCS+ | Digital signature (hash-based) | Provable security, resistant to quantum attacks | Larger signature and key sizes compared to lattice-based schemes |
Hypothetical Post-Quantum Server Security Infrastructure
A hypothetical server security infrastructure incorporating post-quantum cryptographic methods might employ CRYSTALS-Kyber for key exchange (TLS 1.3 and beyond), CRYSTALS-Dilithium for digital signatures (code signing, authentication), and SPHINCS+ as a backup or for applications requiring extremely high security assurance. This layered approach would provide robust protection against both classical and quantum attacks. Data at rest could be protected using authenticated encryption with associated data (AEAD) schemes combined with post-quantum key management.
Regular security audits and updates would be essential to address emerging threats and vulnerabilities. The infrastructure would also need to be designed for efficient key rotation and management to mitigate the risks associated with key compromise. This proactive approach minimizes the potential impact of a successful quantum attack.
Blockchain Technology and Server Security: Cryptography: The Future Of Server Security
Blockchain technology, initially known for its role in cryptocurrencies, offers a compelling approach to enhancing server security and data integrity. Its decentralized and immutable nature provides several advantages over traditional centralized security models, creating a more resilient and trustworthy system for sensitive data. This section explores how blockchain can bolster server security, while also acknowledging its limitations and challenges.Blockchain enhances server security by providing a tamper-evident audit trail of all server activities.
Each transaction, including changes to server configurations, software updates, and access logs, is recorded as a block within the blockchain. This creates a verifiable and auditable history that makes it extremely difficult to alter or conceal malicious activities. For example, if a hacker attempts to modify server files, the change will be immediately apparent as a discrepancy in the blockchain record.
This increased transparency significantly reduces the risk of undetected intrusions and data breaches. Furthermore, the cryptographic hashing used in blockchain ensures data integrity. Any alteration to a block will result in a different hash value, instantly alerting administrators to a potential compromise.
Blockchain’s Enhanced Data Integrity and Immutability
The inherent immutability of blockchain is a key strength in securing server data. Once data is recorded on the blockchain, it cannot be easily altered or deleted, ensuring data integrity and authenticity. This characteristic is particularly valuable in situations requiring high levels of data security and compliance, such as in healthcare or financial institutions. For instance, medical records stored on a blockchain-based system would be protected against unauthorized modification or deletion, maintaining patient data accuracy and confidentiality.
Similarly, financial transactions recorded on a blockchain are inherently resistant to fraud and manipulation, bolstering the trust and reliability of the system.
Vulnerabilities in Blockchain-Based Server Security Implementations
While blockchain offers significant advantages, it is not without vulnerabilities. One major concern is the potential for 51% attacks, where a malicious actor gains control of more than half of the network’s computing power. This would allow them to manipulate the blockchain, potentially overriding security measures. Another vulnerability lies in the smart contracts that often govern blockchain interactions.
Flaws in the code of these contracts could be exploited by attackers to compromise the system. Furthermore, the security of the entire system relies on the security of the individual nodes within the network. A compromise of a single node could potentially lead to a breach of the entire system, especially if that node holds a significant amount of data.
Finally, the complexity of implementing and managing a blockchain-based security system can introduce new points of failure.
Scalability and Efficiency Challenges of Blockchain for Server Security
The scalability and efficiency of blockchain technology are significant challenges when considering its application to server security. Blockchain’s inherent design, requiring consensus mechanisms to validate transactions, can lead to slower processing speeds compared to traditional centralized systems. This can be a critical limitation in scenarios requiring real-time responses, such as intrusion detection and prevention. The storage requirements of blockchain can also be substantial, particularly for large-scale deployments.
Storing every transaction on multiple nodes across a network can become resource-intensive and costly, impacting the overall efficiency of the system. The energy consumption associated with maintaining a blockchain network is another major concern, especially for environmentally conscious organizations. For example, the high energy usage of proof-of-work consensus mechanisms has drawn criticism, prompting research into more energy-efficient alternatives like proof-of-stake.
Homomorphic Encryption for Secure Cloud Computing
Homomorphic encryption is a revolutionary cryptographic technique enabling computations to be performed on encrypted data without requiring decryption. This capability is particularly valuable in cloud computing, where sensitive data is often outsourced to third-party servers. By allowing computations on encrypted data, homomorphic encryption enhances data privacy and security while still allowing for useful processing.Homomorphic encryption allows computations to be performed directly on ciphertexts, producing an encrypted result that, when decrypted, matches the result of the same operation performed on the original plaintexts.
This eliminates the need to decrypt sensitive data before processing, thereby significantly improving security in cloud environments. The potential applications are vast, ranging from secure data analytics to private machine learning.
Types of Homomorphic Encryption Schemes
Several types of homomorphic encryption schemes exist, each with its strengths and weaknesses. The primary distinction lies in the types of operations they support. Fully homomorphic encryption (FHE) schemes support arbitrary computations, while partially homomorphic encryption (PHE) schemes support only specific operations.
- Partially Homomorphic Encryption (PHE): PHE schemes only support a limited set of operations. For example, some PHE schemes only allow for additions on encrypted data (additive homomorphic), while others only allow for multiplications (multiplicative homomorphic). RSA, used for public-key cryptography, exhibits a form of multiplicative homomorphism.
- Somewhat Homomorphic Encryption (SHE): SHE schemes can handle a limited number of additions and multiplications before the ciphertext becomes too noisy to decrypt reliably. This limitation necessitates careful design and optimization of the algorithms.
- Fully Homomorphic Encryption (FHE): FHE schemes represent the ideal scenario, supporting arbitrary computations on encrypted data without limitations. However, FHE schemes are significantly more complex and computationally expensive than PHE schemes.
Practical Limitations and Challenges of Homomorphic Encryption
Despite its potential, homomorphic encryption faces several practical limitations that hinder widespread adoption in server environments.
- High Computational Overhead: Homomorphic encryption operations are significantly slower than their non-encrypted counterparts. This performance penalty can be substantial, especially for complex computations, making it unsuitable for many real-time applications. For example, processing large datasets with FHE might take significantly longer than processing the same data in plaintext.
- Key Management Complexity: Securely managing encryption keys is crucial for the integrity of the system. The complexity of key generation, distribution, and revocation increases significantly with homomorphic encryption, requiring robust key management infrastructure.
- Ciphertext Size: The size of ciphertexts generated by homomorphic encryption can be considerably larger than the size of the corresponding plaintexts. This increased size can impact storage and bandwidth requirements, particularly when dealing with large datasets. For instance, storing encrypted data using FHE might require significantly more storage space compared to storing plaintext data.
- Error Accumulation: In some homomorphic encryption schemes, errors can accumulate during computations, potentially leading to incorrect results. Managing and mitigating these errors adds complexity to the implementation.
Examples of Homomorphic Encryption Applications in Secure Cloud Servers
While still nascent, homomorphic encryption is finding practical applications in specific areas. For example, secure genomic data analysis in the cloud allows researchers to analyze sensitive genetic information without compromising patient privacy. Similarly, financial institutions are exploring its use for secure financial computations, enabling collaborative analysis of sensitive financial data without revealing individual transactions. These examples demonstrate the potential of homomorphic encryption to transform data security in cloud computing, though the challenges related to computational overhead and ciphertext size remain significant hurdles to overcome.
Zero-Knowledge Proofs and Secure Authentication
Zero-knowledge proofs (ZKPs) represent a significant advancement in server security, enabling authentication and verification without compromising sensitive data. Unlike traditional authentication methods that require revealing credentials, ZKPs allow users to prove their identity or knowledge of a secret without disclosing the secret itself. This paradigm shift enhances security by minimizing the risk of credential theft and unauthorized access. The core principle lies in convincing a verifier of a statement’s truth without revealing any information beyond the statement’s validity.Zero-knowledge proofs are particularly valuable in enhancing server authentication protocols by providing a robust and secure method for verifying user identities.
This approach strengthens security against various attacks, including man-in-the-middle attacks and replay attacks, which are common vulnerabilities in traditional authentication systems. The inherent privacy protection offered by ZKPs also aligns with growing concerns about data privacy and compliance regulations.
Zero-Knowledge Proof Applications in Identity Verification
Several practical applications demonstrate the power of zero-knowledge proofs in verifying user identities without revealing sensitive information. For example, a user could prove ownership of a digital asset (like a cryptocurrency) without revealing the private key. Similarly, a user could authenticate to a server by proving knowledge of a password hash without disclosing the actual password. This prevents attackers from gaining access to the password even if they intercept the communication.
Another example is in access control systems, where users can prove they have the necessary authorization without revealing their credentials. This significantly reduces the attack surface and minimizes data breaches.
Secure Server Access System using Zero-Knowledge Proofs
The following system architecture leverages zero-knowledge proofs for secure access to sensitive server resources:
- User Registration: Users register with the system, providing a unique identifier and generating a cryptographic key pair. The public key is stored on the server, while the private key remains solely with the user.
- Authentication Request: When a user attempts to access a resource, they initiate an authentication request to the server, including their unique identifier.
- Zero-Knowledge Proof Generation: The user generates a zero-knowledge proof demonstrating possession of the corresponding private key without revealing the key itself. This proof is digitally signed using the user’s private key to ensure authenticity.
- Proof Verification: The server verifies the received zero-knowledge proof using the user’s public key. The verification process confirms the user’s identity without exposing their private key.
- Resource Access: If the proof is valid, the server grants the user access to the requested resource. The entire process is encrypted, ensuring confidentiality.
This system ensures that only authorized users can access sensitive server resources, while simultaneously protecting the user’s private keys and other sensitive data from unauthorized access or disclosure. The use of digital signatures further enhances security by preventing unauthorized modification or replay attacks. The system’s strength relies on the cryptographic properties of the zero-knowledge proof protocol employed, ensuring a high level of security and privacy.
The system’s design minimizes the exposure of sensitive information, making it a highly secure authentication method.
Hardware-Based Security Enhancements

Hardware security modules (HSMs) represent a crucial advancement in bolstering server security by providing a physically secure environment for cryptographic operations. Their dedicated hardware and isolated architecture significantly reduce the attack surface compared to software-based implementations, safeguarding sensitive cryptographic keys and accelerating cryptographic processes. This enhanced security is particularly vital in environments handling sensitive data, such as financial transactions or healthcare records.The integration of HSMs offers several key advantages.
By offloading cryptographic tasks to specialized hardware, HSMs reduce the computational burden on the server’s main processor, improving overall system performance. Furthermore, the secure environment within the HSM protects cryptographic keys from unauthorized access, even if the server itself is compromised. This protection is crucial for maintaining data confidentiality and integrity.
Types of HSMs and Their Capabilities
HSMs are categorized based on their form factor, security features, and intended applications. Network HSMs, for instance, are accessed remotely via a network interface, allowing multiple servers to share a single HSM. This is cost-effective for organizations with numerous servers requiring cryptographic protection. Conversely, PCI HSMs are designed to meet the Payment Card Industry Data Security Standard (PCI DSS) requirements, ensuring compliance with strict regulations for handling payment card data.
Finally, cloud HSMs offer similar functionalities but are hosted within a cloud provider’s infrastructure, providing a managed solution for cloud-based applications. These variations reflect the diverse needs of different organizations and applications. The choice of HSM depends heavily on the specific security requirements and the overall infrastructure.
Illustrative Example: A Server with Hardware-Based Security Features
Imagine a high-security server designed for processing sensitive financial transactions. This server incorporates several hardware-based security features to enhance its resilience against attacks. At its core is a Network HSM, a tamper-resistant device physically secured within a restricted access area. This HSM houses the private keys required for encrypting and decrypting financial data. The server’s main processor interacts with the HSM via a secure communication channel, such as a dedicated network interface.
A Trusted Platform Module (TPM) is also integrated into the server’s motherboard. The TPM provides secure storage for boot-related keys and performs secure boot attestation, verifying the integrity of the operating system before it loads. Furthermore, the server is equipped with a secure element, a small chip dedicated to secure storage and processing of sensitive data. This secure element might handle authentication tokens or other sensitive information.
These components work in concert to ensure the confidentiality, integrity, and authenticity of data processed by the server. For example, the TPM verifies the integrity of the operating system, the HSM protects the cryptographic keys, and the secure element protects authentication tokens, creating a multi-layered security approach. This layered security approach makes it significantly more difficult for attackers to compromise the system and access sensitive data.
The Future Landscape of Server Security Cryptography
The field of server security cryptography is constantly evolving, driven by both the ingenuity of attackers and the relentless pursuit of more secure systems. Emerging trends and ethical considerations are inextricably linked, shaping a future where robust, adaptable cryptographic solutions are paramount. Understanding these trends and their implications is crucial for building secure and trustworthy digital infrastructures.The future of server security cryptography will be defined by a confluence of technological advancements and evolving threat landscapes.
Several key factors will shape this landscape, requiring proactive adaptation and innovative solutions.
Emerging Trends and Technologies
Several emerging technologies promise to significantly enhance server security cryptography. Post-quantum cryptography, already discussed, represents a critical step in preparing for the potential threat of quantum computing. Beyond this, advancements in lattice-based cryptography, multivariate cryptography, and code-based cryptography offer diverse and robust alternatives, enhancing the resilience of systems against various attack vectors. Furthermore, the integration of machine learning (ML) and artificial intelligence (AI) into cryptographic systems offers potential for automated threat detection and response, bolstering defenses against sophisticated attacks.
For example, ML algorithms can be used to analyze network traffic patterns and identify anomalies indicative of malicious activity, triggering automated responses to mitigate potential breaches. AI-driven systems can adapt and evolve their security protocols in response to emerging threats, creating a more dynamic and resilient security posture. This adaptive approach represents a significant shift from traditional, static security measures.
Ethical Considerations of Advanced Cryptographic Techniques
The deployment of advanced cryptographic techniques necessitates careful consideration of ethical implications. The increasing use of encryption, for instance, raises concerns about privacy and government surveillance. Balancing the need for strong security with the preservation of individual rights and freedoms requires a nuanced approach. The potential for misuse of cryptographic technologies, such as in the development of untraceable malware or the facilitation of illegal activities, must also be addressed.
Robust regulatory frameworks and ethical guidelines are essential to mitigate these risks and ensure responsible innovation in the field. For example, the debate surrounding backdoors in encryption systems highlights the tension between national security interests and the protection of individual privacy. Finding a balance between these competing concerns remains a significant challenge.
Emerging Threats Driving the Need for New Cryptographic Approaches
The constant evolution of cyber threats necessitates the development of new cryptographic approaches. The increasing sophistication of attacks, such as advanced persistent threats (APTs) and supply chain attacks, demands more robust and adaptable security measures. Quantum computing, as previously discussed, poses a significant threat to current cryptographic standards, necessitating a transition to post-quantum cryptography. Moreover, the growing prevalence of Internet of Things (IoT) devices, with their inherent security vulnerabilities, presents a significant challenge.
The sheer volume and diversity of IoT devices create a complex attack surface, requiring innovative cryptographic solutions to secure these interconnected systems. The rise of sophisticated AI-driven attacks, capable of autonomously exploiting vulnerabilities, further underscores the need for adaptive and intelligent security systems that can counter these threats effectively. For instance, the use of AI to create realistic phishing attacks or to automate the discovery and exploitation of zero-day vulnerabilities requires the development of equally sophisticated countermeasures.
Summary
The future of server security hinges on our ability to adapt and innovate in the face of ever-evolving threats. The cryptographic techniques discussed here – from post-quantum cryptography and blockchain integration to homomorphic encryption and zero-knowledge proofs – represent a critical arsenal in our ongoing battle for digital security. While challenges remain, the ongoing development and implementation of these advanced cryptographic methods offer a promising path toward a more secure and resilient digital future.
Continuous vigilance, adaptation, and a commitment to innovation are paramount to safeguarding our digital infrastructure and the sensitive data it protects.
FAQ Explained
What are the biggest risks to server security in the coming years?
The rise of quantum computing poses a significant threat, as it could break many currently used encryption algorithms. Advanced persistent threats (APTs) and sophisticated malware also represent major risks.
How can organizations effectively implement post-quantum cryptography?
A phased approach is recommended, starting with risk assessments and identifying critical systems. Then, select appropriate post-quantum algorithms, test thoroughly, and gradually integrate them into existing infrastructure.
What are the limitations of blockchain technology in server security?
Scalability and transaction speed can be limitations, especially for high-volume applications. Smart contract vulnerabilities and the potential for 51% attacks also pose risks.
Is homomorphic encryption a practical solution for all server security needs?
No, it’s computationally expensive and currently not suitable for all applications. Its use cases are more specialized, focusing on specific scenarios where computation on encrypted data is required.