Server Security Redefined by Cryptography: In an era of escalating cyber threats, traditional server security measures are proving increasingly inadequate. This exploration delves into the transformative power of cryptography, examining how its advanced techniques are revolutionizing server protection and mitigating the vulnerabilities inherent in legacy systems. We’ll dissect various cryptographic algorithms, their applications in securing data at rest and in transit, and the challenges in implementing robust cryptographic solutions.
The journey will cover advanced concepts like homomorphic encryption and post-quantum cryptography, ultimately painting a picture of a future where server security is fundamentally redefined by cryptographic innovation.
From the infamous Yahoo! data breach to the ongoing evolution of ransomware attacks, the history of server security is punctuated by high-profile incidents highlighting the limitations of traditional approaches. Firewalls and intrusion detection systems, while crucial, are often reactive rather than proactive. Cryptography, however, offers a more proactive and robust defense, actively protecting data at every stage of its lifecycle.
This article will explore the fundamental principles of cryptography and its practical applications in securing various server components, from databases to network connections, offering a comprehensive overview of this essential technology.
Introduction
The digital landscape has witnessed a dramatic escalation in server security threats, evolving from relatively simple intrusions to sophisticated, multi-vector attacks. Early server security relied heavily on perimeter defenses like firewalls and basic access controls, a paradigm insufficient for today’s interconnected world. This shift necessitates a fundamental re-evaluation of our approach, moving towards a more robust, cryptographically-driven security model.Traditional server security methods primarily focused on access control lists (ACLs), intrusion detection systems (IDS), and antivirus software.
Server security is fundamentally redefined by cryptography, moving beyond traditional methods. For a deeper dive into the practical applications and strategic implementations, explore the essential strategies outlined in The Cryptographic Edge: Server Security Strategies. Understanding these strategies is crucial for bolstering server defenses and mitigating modern threats, ultimately transforming how we approach server security.
While these tools provided a baseline level of protection, they proved increasingly inadequate against the ingenuity and persistence of modern cybercriminals. The reliance on signature-based detection, for example, left systems vulnerable to zero-day exploits and polymorphic malware. Furthermore, the increasing complexity of server infrastructures, with the rise of cloud computing and microservices, added layers of difficulty to managing and securing these systems effectively.
High-Profile Server Breaches and Their Impact
Several high-profile server breaches vividly illustrate the consequences of inadequate security. The 2017 Equifax breach, resulting from an unpatched Apache Struts vulnerability, exposed the personal data of nearly 150 million individuals, leading to significant financial losses and reputational damage. Similarly, the Yahoo! data breaches, spanning multiple years, compromised billions of user accounts, highlighting the long-term vulnerabilities inherent in legacy systems.
These incidents underscore the catastrophic financial, legal, and reputational repercussions that organizations face when their server security fails. The cost of these breaches extends far beyond immediate financial losses, encompassing legal fees, regulatory penalties, and the long-term erosion of customer trust.
Limitations of Legacy Approaches
Legacy server security approaches, while offering some protection, suffer from inherent limitations. The reliance on perimeter security, for instance, becomes less effective in the face of sophisticated insider threats or advanced persistent threats (APTs) that bypass external defenses. Traditional methods also struggle to keep pace with the rapid evolution of attack vectors, often lagging behind in addressing newly discovered vulnerabilities.
Moreover, the complexity of managing numerous security tools and configurations across large server infrastructures can lead to human error and misconfigurations, creating further vulnerabilities. The lack of end-to-end encryption and robust authentication mechanisms further compounds these issues, leaving sensitive data exposed to potential breaches.
Cryptography’s Role in Modern Server Security
Cryptography forms the bedrock of modern server security, providing the essential tools to protect data confidentiality, integrity, and authenticity. Without robust cryptographic techniques, servers would be vulnerable to a wide range of attacks, from data breaches and unauthorized access to man-in-the-middle attacks and denial-of-service disruptions. This section delves into the fundamental principles and applications of cryptography in securing server infrastructure.
Fundamental Principles of Cryptography in Server Security
The core principles underpinning cryptography’s role in server security are confidentiality, integrity, and authentication. Confidentiality ensures that only authorized parties can access sensitive data. Integrity guarantees that data remains unaltered during transmission and storage. Authentication verifies the identity of both the sender and the receiver, preventing impersonation and ensuring the legitimacy of communication. These principles are achieved through the use of various cryptographic algorithms and protocols.
Types of Cryptographic Algorithms Used in Server Protection
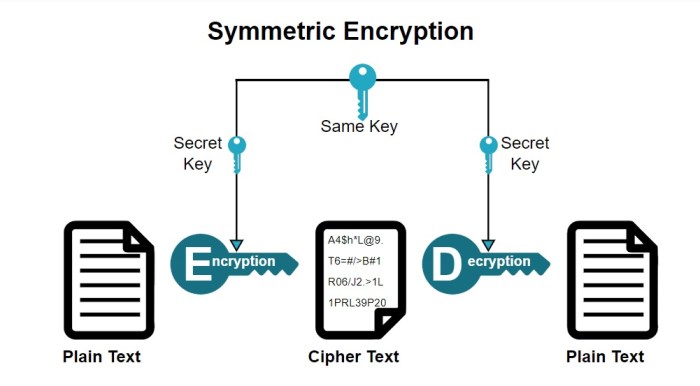
Several types of cryptographic algorithms are employed to secure servers. Symmetric-key cryptography uses the same secret key for both encryption and decryption. This approach is generally faster than asymmetric cryptography but requires a secure method for key exchange. Examples include AES (Advanced Encryption Standard) and DES (Data Encryption Standard), commonly used for encrypting data at rest and in transit.Asymmetric-key cryptography, also known as public-key cryptography, uses a pair of keys: a public key for encryption and a private key for decryption.
This eliminates the need for secure key exchange, as the public key can be widely distributed. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are prominent examples used for secure communication, digital signatures, and key exchange protocols like TLS/SSL.Hashing algorithms generate a fixed-size string (hash) from an input of any size. These are primarily used for data integrity verification.
If the input data changes even slightly, the resulting hash will be drastically different. SHA-256 and SHA-3 are widely used examples in server security for password storage and data integrity checks. It is crucial to note that hashing is a one-way function; it’s computationally infeasible to retrieve the original data from the hash.
Comparison of Cryptographic Techniques
The choice of cryptographic technique depends on the specific security requirements and constraints. Symmetric-key algorithms generally offer higher speed but require secure key management. Asymmetric-key algorithms provide better key management but are computationally more intensive. Hashing algorithms are excellent for integrity checks but do not provide confidentiality. A balanced approach often involves combining different techniques to leverage their respective strengths.
For instance, a secure server might use asymmetric cryptography for initial key exchange and then switch to faster symmetric cryptography for bulk data encryption.
Comparison of Encryption Algorithms
| Algorithm | Speed | Security Level | Key Size (bits) |
|---|---|---|---|
| AES-128 | Very Fast | High (currently considered secure) | 128 |
| AES-256 | Fast | Very High (currently considered secure) | 256 |
| RSA-2048 | Slow | High (currently considered secure, but key size is crucial) | 2048 |
| ECC-256 | Moderate | High (offers comparable security to RSA-2048 with smaller key size) | 256 |
Securing Specific Server Components with Cryptography
Cryptography is no longer a luxury but a fundamental necessity for modern server security. Its application extends beyond general security principles to encompass the specific protection of individual server components and the data they handle. Effective implementation requires a layered approach, combining various cryptographic techniques to safeguard data at rest, in transit, and during access.
Database Encryption: Securing Data at Rest
Protecting data stored on a server’s database is paramount. Database encryption employs cryptographic algorithms to transform sensitive data into an unreadable format, rendering it inaccessible to unauthorized individuals even if the database is compromised. Common techniques include transparent data encryption (TDE), which encrypts the entire database, and columnar encryption, which focuses on specific sensitive columns. The choice of encryption method depends on factors like performance overhead and the sensitivity of the data.
For example, a financial institution might employ TDE for its customer transaction database, while a less sensitive application might use columnar encryption to protect only specific fields like passwords. Strong key management is crucial; using hardware security modules (HSMs) for key storage provides an additional layer of security.
Securing Data in Transit: TLS/SSL and VPNs
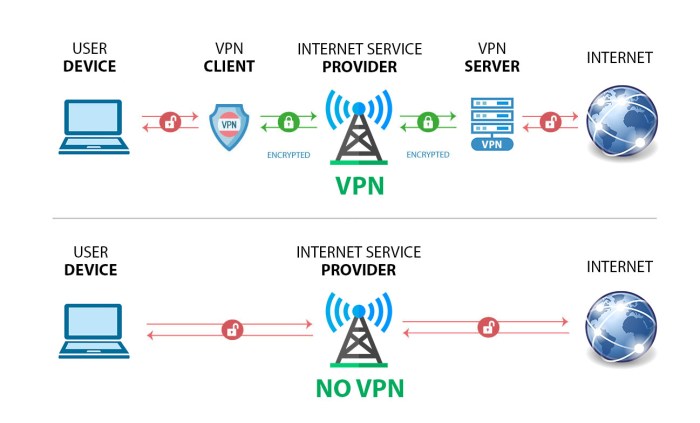
Data transmitted between the server and clients needs robust protection against eavesdropping and tampering. Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are widely used protocols that establish encrypted connections. TLS/SSL uses public key cryptography to encrypt communication, ensuring confidentiality and integrity. Virtual Private Networks (VPNs) extend this protection by creating an encrypted tunnel between the client and the server, often used to secure remote access to servers or to encrypt traffic traversing untrusted networks.
For instance, a company might use a VPN to allow employees to securely access internal servers from their home computers, preventing unauthorized access and data interception. The selection between TLS/SSL and VPNs often depends on the specific security requirements and network architecture.
Digital Signatures: Authentication and Integrity
Digital signatures provide a mechanism to verify the authenticity and integrity of data. They leverage asymmetric cryptography, using a private key to create a signature and a corresponding public key to verify it. This ensures that the data originates from a trusted source and hasn’t been tampered with during transit or storage. Digital signatures are crucial for secure software updates, code signing, and verifying the integrity of sensitive documents stored on the server.
For example, a software vendor might use digital signatures to ensure that downloaded software hasn’t been modified by malicious actors. The verification process leverages cryptographic hash functions to ensure any change to the data will invalidate the signature.
Cryptography’s Enhancement of Access Control Mechanisms
Cryptography significantly enhances access control by providing strong authentication and authorization capabilities. Instead of relying solely on passwords, systems can use multi-factor authentication (MFA) that incorporates cryptographic tokens or biometric data. Access control lists (ACLs) can be encrypted and managed using cryptographic techniques to prevent unauthorized modification. Moreover, encryption can protect sensitive data even if an attacker gains unauthorized access, limiting the impact of a security breach.
For example, a server might implement role-based access control (RBAC) where users are granted access based on their roles, with cryptographic techniques ensuring that only authorized users can access specific data. This layered approach combines traditional access control methods with cryptographic enhancements to create a more robust security posture.
Advanced Cryptographic Techniques for Enhanced Server Security
Modern server security demands sophisticated cryptographic techniques to combat increasingly complex threats. Moving beyond basic encryption and digital signatures, advanced methods offer enhanced protection against both current and emerging attacks, including those that might exploit future quantum computing capabilities. This section explores several key advancements.
Homomorphic Encryption and its Application in Server Security
Homomorphic encryption allows computations to be performed on encrypted data without requiring decryption. This is crucial for server security as it enables processing of sensitive information while maintaining confidentiality. For instance, a cloud-based service could perform data analysis on encrypted medical records without ever accessing the plaintext data, preserving patient privacy. Different types of homomorphic encryption exist, including fully homomorphic encryption (FHE) which allows for arbitrary computations, and somewhat homomorphic encryption (SHE) which supports a limited set of operations.
The practical application of FHE is still limited by computational overhead, but SHE schemes are finding increasing use in privacy-preserving applications. Imagine a financial institution using SHE to calculate aggregate statistics from encrypted transaction data without compromising individual customer details. This functionality significantly strengthens data security in sensitive sectors.
Post-Quantum Cryptography and its Relevance to Future Server Protection
The advent of quantum computers poses a significant threat to current cryptographic algorithms, as they can potentially break widely used public-key systems like RSA and ECC. Post-quantum cryptography (PQC) addresses this by developing algorithms resistant to attacks from both classical and quantum computers. Several promising PQC candidates are currently under consideration by standardization bodies, including lattice-based cryptography, code-based cryptography, and multivariate cryptography.
These algorithms rely on mathematical problems believed to be hard even for quantum computers to solve. Implementing PQC in servers is crucial for long-term security, ensuring the confidentiality and integrity of data even in the face of future quantum computing advancements. For example, a government agency securing sensitive national security data would benefit greatly from migrating to PQC algorithms to ensure long-term protection against future quantum attacks.
Blockchain Technology’s Role in Enhancing Server Security, Server Security Redefined by Cryptography
Blockchain technology, with its inherent features of immutability and transparency, can significantly enhance server security. The decentralized and distributed nature of blockchain makes it highly resistant to single points of failure and malicious attacks. Blockchain can be used for secure logging, ensuring that server activity is accurately recorded and tamper-proof. Furthermore, it can be utilized for secure key management, distributing keys across multiple nodes and enhancing resilience against key compromise.
Imagine a distributed server system using blockchain to track and verify software updates, ensuring that only authorized and validated updates are deployed, mitigating the risk of malware injection. This robust approach offers an alternative security paradigm for modern server infrastructure.
Best Practices for Key Management and Rotation
Effective key management is paramount to maintaining strong server security. Neglecting proper key management practices can render even the most sophisticated cryptographic techniques vulnerable.
- Regular Key Rotation: Keys should be rotated at defined intervals, minimizing the window of vulnerability if a key is compromised.
- Secure Key Storage: Keys should be stored securely, using hardware security modules (HSMs) or other robust methods to protect them from unauthorized access.
- Access Control: Access to keys should be strictly controlled, following the principle of least privilege.
- Key Versioning: Maintaining versions of keys allows for easy rollback in case of errors or compromises.
- Auditing: Regular audits should be conducted to ensure compliance with key management policies and procedures.
- Key Escrow: Consider implementing key escrow procedures to ensure that keys can be recovered in case of loss or compromise, while balancing this with the need to prevent unauthorized access.
Practical Implementation and Challenges
The successful implementation of cryptographic systems in server security requires careful planning, execution, and ongoing maintenance. While cryptography offers powerful tools to protect sensitive data and infrastructure, several practical challenges must be addressed to ensure effective and reliable security. This section explores real-world applications, common implementation hurdles, and crucial security practices.Cryptography has demonstrably redefined server security in numerous real-world scenarios.
For example, HTTPS, using TLS/SSL, is ubiquitous, encrypting communication between web browsers and servers, protecting user data during transmission. Similarly, database encryption, employing techniques like transparent data encryption (TDE), safeguards sensitive information stored in databases even if the database server is compromised. The widespread adoption of digital signatures in software distribution ensures authenticity and integrity, preventing malicious code injection.
These examples highlight the transformative impact of cryptography on securing various aspects of server infrastructure.
Real-World Applications of Cryptography in Server Security
The integration of cryptography has led to significant advancements in server security across diverse applications. The use of TLS/SSL certificates for secure web communication protects sensitive user data during online transactions and browsing. Public key infrastructure (PKI) enables secure authentication and authorization, verifying the identity of users and servers. Furthermore, database encryption protects sensitive data at rest, minimizing the risk of data breaches even if the database server is compromised.
Finally, code signing using digital signatures ensures the integrity and authenticity of software applications, preventing malicious code injection.
Challenges in Implementing and Managing Cryptographic Systems
Implementing and managing cryptographic systems present several challenges. Key management, including generation, storage, and rotation, is crucial but complex. The selection of appropriate cryptographic algorithms and parameters is critical, considering factors like performance, security strength, and compatibility. Furthermore, ensuring proper integration with existing systems and maintaining compatibility across different platforms can be demanding. Finally, ongoing monitoring and updates are essential to address vulnerabilities and adapt to evolving threats.
Importance of Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are vital for maintaining the effectiveness of cryptographic systems. These assessments identify weaknesses and vulnerabilities in the implementation and management of cryptographic systems. They ensure that cryptographic algorithms and protocols are up-to-date and aligned with best practices. Furthermore, audits help to detect misconfigurations, key compromises, and other security breaches. Proactive vulnerability assessments and regular audits are essential for preventing security incidents and maintaining a strong security posture.
Potential Cryptographic Implementation Vulnerabilities and Mitigation Strategies
Effective cryptographic implementation requires careful consideration of various potential vulnerabilities. The following list details some common vulnerabilities and their corresponding mitigation strategies:
- Weak or outdated cryptographic algorithms: Using outdated or insecure algorithms makes systems vulnerable to attacks. Mitigation: Employ strong, well-vetted algorithms like AES-256 and use up-to-date cryptographic libraries.
- Improper key management: Weak or compromised keys render encryption useless. Mitigation: Implement robust key management practices, including secure key generation, storage, rotation, and access control.
- Implementation flaws: Bugs in the code implementing cryptographic functions can create vulnerabilities. Mitigation: Use well-tested, peer-reviewed cryptographic libraries and conduct thorough code reviews and security audits.
- Side-channel attacks: Attacks that exploit information leaked during cryptographic operations. Mitigation: Use constant-time implementations to prevent timing attacks and employ techniques to mitigate power analysis attacks.
- Insufficient randomness: Using predictable random numbers weakens encryption. Mitigation: Utilize robust, cryptographically secure random number generators (CSPRNGs).
Future Trends in Cryptographically Secure Servers

The landscape of server security is constantly evolving, driven by the emergence of new threats and advancements in cryptographic technologies. Understanding and adapting to these trends is crucial for maintaining robust and reliable server infrastructure. This section explores key future trends shaping cryptographically secure servers, focusing on emerging cryptographic approaches, the role of AI, and the increasing adoption of zero-trust security models.Emerging cryptographic technologies promise significant improvements in server security.
Post-quantum cryptography, designed to withstand attacks from quantum computers, is a prime example. Homomorphic encryption, allowing computations on encrypted data without decryption, offers enhanced privacy for sensitive information processed on servers. Lattice-based cryptography, known for its strong security properties and potential for efficient implementation, is also gaining traction. These advancements will redefine the capabilities and security levels achievable in server environments.
Post-Quantum Cryptography and its Impact
Post-quantum cryptography addresses the threat posed by quantum computers, which have the potential to break many currently used encryption algorithms. The transition to post-quantum cryptography requires careful planning and implementation, considering factors like algorithm selection, key management, and compatibility with existing systems. Standardization efforts are underway to ensure a smooth and secure transition. For example, the National Institute of Standards and Technology (NIST) has been actively involved in evaluating and selecting post-quantum cryptographic algorithms for widespread adoption.
This standardization is vital to prevent a widespread security vulnerability once quantum computers become powerful enough to break current encryption.
Artificial Intelligence in Enhancing Cryptographic Security
Artificial intelligence (AI) is increasingly being integrated into cryptographic security systems to enhance their effectiveness and adaptability. AI-powered systems can analyze vast amounts of data to identify anomalies and potential threats, improving threat detection and response. Furthermore, AI can assist in the development and implementation of more robust cryptographic algorithms by automating complex tasks and identifying vulnerabilities. For instance, AI can be used to analyze the effectiveness of different cryptographic keys and suggest stronger alternatives, making the entire system more resilient.
However, it is important to acknowledge the potential risks of using AI in cryptography, such as the possibility of adversarial attacks targeting AI-driven security systems.
Zero-Trust Security and its Integration with Cryptography
Zero-trust security is a model that assumes no implicit trust within or outside an organization’s network. Every access request, regardless of its origin, is verified before granting access. Cryptography plays a vital role in implementing zero-trust security by providing the necessary authentication, authorization, and data protection mechanisms. For example, strong authentication protocols like multi-factor authentication (MFA) combined with encryption and digital signatures ensure that only authorized users can access server resources.
Microsegmentation of networks and the use of granular access control policies, enforced through cryptographic techniques, further enhance security. A real-world example is the adoption of zero-trust principles by large organizations like Google and Microsoft, which leverage cryptography extensively in their internal and cloud infrastructure.
The Future of Server Security with Advanced Cryptography
The future of server security will be characterized by a layered, adaptive, and highly automated defense system leveraging advanced cryptographic techniques. AI-driven threat detection, coupled with post-quantum cryptography and robust zero-trust architectures, will create a significantly more secure environment. Continuous monitoring and automated responses to emerging threats will be crucial, alongside a focus on proactive security measures rather than solely reactive ones.
This will involve a shift towards more agile and adaptable security protocols that can respond to the ever-changing threat landscape, making server security more resilient and less prone to breaches.
Last Recap
The future of server security is inextricably linked to the continued advancement of cryptography. As cyber threats become more sophisticated, so too must our defenses. By embracing advanced techniques like homomorphic encryption, post-quantum cryptography, and integrating AI-driven security solutions, we can build a more resilient and secure digital infrastructure. While challenges remain in implementation and management, the transformative potential of cryptography is undeniable.
A future where servers are truly secure, not just defended, is within reach, powered by the ever-evolving landscape of cryptographic innovation. The journey towards this future demands continuous learning, adaptation, and a commitment to best practices in key management and security auditing.
Question Bank: Server Security Redefined By Cryptography
What are the key differences between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, offering faster speeds but requiring secure key exchange. Asymmetric encryption uses separate public and private keys, simplifying key exchange but being slower.
How does cryptography protect against insider threats?
While cryptography doesn’t directly prevent insider threats, strong access control mechanisms combined with auditing and logging features, all enhanced by cryptographic techniques, can significantly reduce the risk and impact of malicious insiders.
What is the role of digital certificates in server security?
Digital certificates, underpinned by public key infrastructure (PKI), verify the identity of servers, ensuring clients are connecting to the legitimate entity. This is crucial for secure communication protocols like TLS/SSL.