The Cryptographic Shield for Your Server: In today’s digital landscape, where cyber threats loom large, securing your server is paramount. A robust cryptographic shield isn’t just a security measure; it’s the bedrock of your server’s integrity, safeguarding sensitive data and ensuring uninterrupted operations. This comprehensive guide delves into the crucial components, implementation strategies, and future trends of building an impenetrable cryptographic defense for your server.
We’ll explore essential cryptographic elements like encryption algorithms, hashing functions, and digital signatures, examining their strengths and weaknesses in protecting your server from data breaches, unauthorized access, and other malicious activities. We’ll also cover practical implementation steps, best practices for maintenance, and advanced techniques like VPNs and intrusion detection systems to bolster your server’s security posture.
Introduction: The Cryptographic Shield For Your Server
A cryptographic shield, in the context of server security, is a comprehensive system of cryptographic techniques and protocols designed to protect server data and operations from unauthorized access, modification, or disclosure. It acts as a multi-layered defense mechanism, employing various encryption methods, authentication protocols, and access control measures to ensure data confidentiality, integrity, and availability.A robust cryptographic shield is paramount for maintaining the security and reliability of server infrastructure.
In today’s interconnected world, servers are vulnerable to a wide range of cyber threats, and the consequences of a successful attack—data breaches, financial losses, reputational damage, and legal liabilities—can be devastating. A well-implemented cryptographic shield significantly reduces the risk of these outcomes by providing a strong defense against malicious actors.
Threats Mitigated by a Cryptographic Shield
A cryptographic shield effectively mitigates a broad spectrum of threats targeting server security. These include data breaches, where sensitive information is stolen or leaked; unauthorized access, granting malicious users control over server resources and data; denial-of-service (DoS) attacks, which disrupt server availability; man-in-the-middle (MitM) attacks, where communication between the server and clients is intercepted and manipulated; and malware infections, where malicious software compromises server functionality and security.
Securing your server demands a robust cryptographic shield, protecting sensitive data from unauthorized access. For a deep dive into the various methods and best practices, check out this comprehensive guide: Server Encryption: The Ultimate Guide. Implementing strong encryption is paramount for maintaining the integrity and confidentiality of your server’s cryptographic shield, ensuring data remains safe and secure.
For example, the use of Transport Layer Security (TLS) encryption protects against MitM attacks by encrypting communication between a web server and client browsers. Similarly, strong password policies and multi-factor authentication (MFA) significantly reduce the risk of unauthorized access. Regular security audits and penetration testing further strengthen the overall security posture.
Core Components of a Cryptographic Shield
A robust cryptographic shield for your server relies on a layered approach, combining several essential components to ensure data confidentiality, integrity, and authenticity. These components work in concert to protect sensitive information from unauthorized access and manipulation. Understanding their individual roles and interactions is crucial for building a truly secure system.
Essential Cryptographic Primitives
The foundation of any cryptographic shield rests upon several core cryptographic primitives. These include encryption algorithms, hashing functions, and digital signatures, each playing a unique but interconnected role in securing data. Encryption algorithms ensure confidentiality by transforming readable data (plaintext) into an unreadable format (ciphertext). Hashing functions provide data integrity by generating a unique fingerprint of the data, allowing detection of any unauthorized modifications.
Digital signatures, based on asymmetric cryptography, guarantee the authenticity and integrity of data by verifying the sender’s identity and ensuring data hasn’t been tampered with.
Key Management in Cryptographic Systems
Effective key management is paramount to the security of the entire cryptographic system. Compromised keys render even the strongest algorithms vulnerable. A comprehensive key management strategy should include secure key generation, storage, distribution, rotation, and revocation protocols. Robust key management practices typically involve using Hardware Security Modules (HSMs) for secure key storage and management, employing strong key generation algorithms, and implementing regular key rotation schedules to mitigate the risk of long-term key compromise.
Furthermore, access control mechanisms must be strictly enforced to limit the number of individuals with access to cryptographic keys.
Comparison of Encryption Algorithms
Various encryption algorithms offer different levels of security and performance. The choice of algorithm depends on the specific security requirements and computational resources available. Symmetric encryption algorithms, like AES, are generally faster but require secure key exchange, while asymmetric algorithms, like RSA, offer better key management but are computationally more expensive.
| Algorithm | Key Size (bits) | Speed | Security Level |
|---|---|---|---|
| AES (Advanced Encryption Standard) | 128, 192, 256 | High | High |
| RSA (Rivest-Shamir-Adleman) | 1024, 2048, 4096 | Low | High (depending on key size) |
| ChaCha20 | 256 | High | High |
| ECC (Elliptic Curve Cryptography) | 256, 384, 521 | Medium | High (smaller key size for comparable security to RSA) |
Implementing the Cryptographic Shield
Implementing a robust cryptographic shield for your server requires a methodical approach, encompassing careful planning, precise execution, and ongoing maintenance. This process involves selecting appropriate cryptographic algorithms, configuring them securely, and integrating them seamlessly into your server’s infrastructure. Failure to address any of these stages can compromise the overall security of your system.
A successful implementation hinges on understanding the specific security needs of your server and selecting the right tools to meet those needs. This includes considering factors like the sensitivity of the data being protected, the potential threats, and the resources available for managing the cryptographic infrastructure. A well-defined plan, developed before implementation begins, is crucial for a successful outcome.
Step-by-Step Implementation Procedure
Implementing a cryptographic shield involves a series of sequential steps. These steps, when followed diligently, ensure a comprehensive and secure cryptographic implementation. Skipping or rushing any step significantly increases the risk of vulnerabilities.
- Needs Assessment and Algorithm Selection: Begin by thoroughly assessing your server’s security requirements. Identify the types of data needing protection (e.g., user credentials, sensitive files, database contents). Based on this assessment, choose appropriate cryptographic algorithms (e.g., AES-256 for encryption, RSA for key exchange) that offer sufficient strength and performance for your workload. Consider industry best practices and recommendations when making these choices.
- Key Management and Generation: Secure key generation and management are paramount. Utilize strong random number generators (RNGs) to create keys. Implement a robust key management system, possibly leveraging hardware security modules (HSMs) for enhanced security. This system should incorporate key rotation schedules and secure storage mechanisms to mitigate risks associated with key compromise.
- Integration with Server Infrastructure: Integrate the chosen cryptographic algorithms into your server’s applications and operating system. This might involve using libraries, APIs, or specialized tools. Ensure seamless integration to avoid disrupting existing workflows while maximizing security. Thorough testing is crucial at this stage.
- Configuration and Testing: Carefully configure all cryptographic components. This includes setting appropriate parameters for algorithms, verifying key lengths, and defining access control policies. Rigorous testing is essential to identify and address any vulnerabilities or misconfigurations before deployment to a production environment. Penetration testing can be invaluable here.
- Monitoring and Maintenance: Continuous monitoring of the cryptographic infrastructure is critical. Regularly check for updates to cryptographic libraries and algorithms, and promptly apply security patches. Implement logging and auditing mechanisms to track access and usage of cryptographic keys and components. Regular key rotation should also be part of the maintenance plan.
Best Practices for Secure Cryptographic Infrastructure
Maintaining a secure cryptographic infrastructure requires adhering to established best practices. These practices minimize vulnerabilities and ensure the long-term effectiveness of the security measures.
The following best practices are essential for robust security:
- Use strong, well-vetted algorithms: Avoid outdated or weak algorithms. Regularly review and update to the latest standards and recommendations.
- Implement proper key management: This includes secure generation, storage, rotation, and destruction of cryptographic keys. Consider using HSMs for enhanced key protection.
- Regularly update software and libraries: Keep all software components, including operating systems, applications, and cryptographic libraries, updated with the latest security patches.
- Employ strong access control: Restrict access to cryptographic keys and configuration files to authorized personnel only.
- Conduct regular security audits: Periodic audits help identify vulnerabilities and ensure compliance with security standards.
Challenges and Potential Pitfalls, The Cryptographic Shield for Your Server
Implementing and managing cryptographic solutions presents several challenges. Understanding these challenges is crucial for effective mitigation strategies.
Key challenges include:
- Complexity: Cryptography can be complex, requiring specialized knowledge and expertise to implement and manage effectively. Incorrect implementation can lead to significant security weaknesses.
- Performance overhead: Cryptographic operations can consume significant computational resources, potentially impacting the performance of applications and servers. Careful algorithm selection and optimization are necessary to mitigate this.
- Key management difficulties: Securely managing cryptographic keys is challenging and requires robust procedures and systems. Key compromise can have catastrophic consequences.
- Integration complexities: Integrating cryptographic solutions into existing systems can be difficult and require significant development effort. Incompatibility issues can arise if not properly addressed.
- Cost: Implementing and maintaining a secure cryptographic infrastructure can be expensive, especially when utilizing HSMs or other advanced security technologies.
Advanced Techniques and Considerations
Implementing robust cryptographic shields is crucial for server security, but a layered approach incorporating additional security measures significantly enhances protection. This section explores advanced techniques and considerations beyond the core cryptographic components, focusing on supplementary defenses that bolster overall server resilience against threats.
VPNs and Firewalls as Supplementary Security Measures
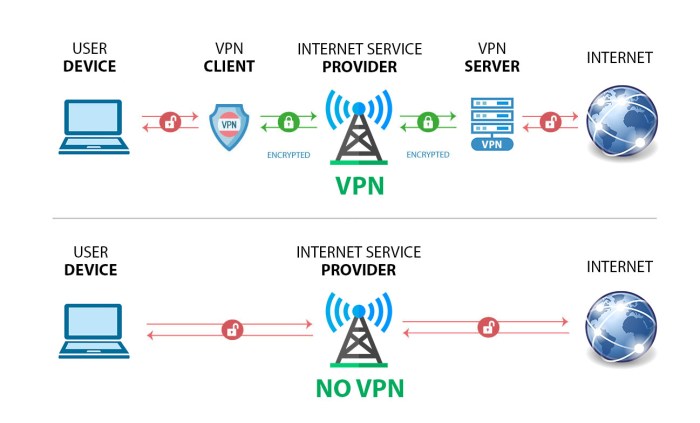
VPNs (Virtual Private Networks) and firewalls act as crucial supplementary layers of security when combined with a cryptographic shield. A VPN creates an encrypted tunnel between the server and clients, protecting data in transit from eavesdropping and manipulation. This is particularly important when sensitive data is transmitted over less secure networks. Firewalls, on the other hand, act as gatekeepers, filtering network traffic based on pre-defined rules.
They prevent unauthorized access attempts and block malicious traffic before it reaches the server, reducing the load on the cryptographic shield and preventing potential vulnerabilities from being exploited. The combination of a VPN and firewall creates a multi-layered defense, making it significantly harder for attackers to penetrate the server’s defenses. For example, a company using a VPN to encrypt all remote access to its servers and a firewall to block all inbound traffic except for specific ports used by legitimate applications greatly enhances security.
Intrusion Detection and Prevention Systems
Intrusion Detection and Prevention Systems (IDPS) provide real-time monitoring and protection against malicious activities. Intrusion Detection Systems (IDS) passively monitor network traffic and system logs for suspicious patterns, alerting administrators to potential threats. Intrusion Prevention Systems (IPS) actively block or mitigate detected threats. Integrating an IDPS with a cryptographic shield adds another layer of defense, enabling early detection and response to attacks that might bypass the cryptographic protections.
A well-configured IDPS can detect anomalies such as unauthorized access attempts, malware infections, and denial-of-service attacks, allowing for prompt intervention and minimizing the impact of a breach. For instance, an IDPS might detect a brute-force attack targeting a server’s SSH port, alerting administrators to the attack and potentially blocking the attacker’s IP address.
Secure Coding Practices
Secure coding practices are paramount in preventing vulnerabilities that could compromise the cryptographic shield. Weaknesses in application code can create entry points for attackers, even with strong cryptographic measures in place. Implementing secure coding practices involves following established guidelines and best practices to minimize vulnerabilities. This includes techniques like input validation to prevent injection attacks (SQL injection, cross-site scripting), proper error handling to avoid information leakage, and secure session management to prevent hijacking.
Regular security audits and penetration testing are also essential to identify and address potential vulnerabilities in the codebase. For example, using parameterized queries instead of directly embedding user input in SQL queries prevents SQL injection attacks, a common vulnerability that can bypass cryptographic protections.
Case Studies
Real-world examples offer invaluable insights into the effectiveness and potential pitfalls of cryptographic shields. Examining both successful and unsuccessful implementations provides crucial lessons for securing server infrastructure. The following case studies illustrate the tangible benefits of robust cryptography and the severe consequences of neglecting security best practices.
Successful Implementation: Cloudflare’s Cryptographic Infrastructure
Cloudflare, a prominent content delivery network (CDN) and cybersecurity company, employs a multi-layered cryptographic approach to protect its vast network and user data. This includes using HTTPS for all communication, implementing robust certificate management practices, utilizing strong encryption algorithms like AES-256, and regularly updating cryptographic libraries. Their commitment to cryptographic security is evident in their consistent efforts to thwart DDoS attacks and protect user privacy.
The positive outcome is a highly secure and resilient platform that enjoys significant user trust and confidence. Their infrastructure has withstood numerous attacks, demonstrating the effectiveness of their comprehensive cryptographic strategy. The reduction in security breaches and the maintenance of user trust translate directly into increased revenue and a strengthened market position.
Unsuccessful Implementation: Heartbleed Vulnerability
The Heartbleed vulnerability, discovered in 2014, exposed the critical flaw in OpenSSL, a widely used cryptographic library. The vulnerability allowed attackers to extract sensitive data, including private keys, usernames, passwords, and other confidential information, from affected servers. This occurred because of a weakness in the OpenSSL’s implementation of the TLS/SSL heartbeat extension, which permitted unauthorized access to memory regions containing sensitive data.
The consequences were devastating, affecting numerous organizations and resulting in significant financial losses, reputational damage, and legal repercussions. Many companies suffered data breaches, leading to massive costs associated with remediation, notification of affected users, and legal settlements. The incident underscored the critical importance of rigorous code review, secure coding practices, and timely patching of vulnerabilities.
Key Lessons Learned
The following points highlight the crucial takeaways from these contrasting case studies:
The importance of these lessons cannot be overstated. A robust and well-maintained cryptographic shield is not merely a technical detail; it is a fundamental pillar of online security and business continuity.
- Comprehensive Approach: A successful cryptographic shield requires a multi-layered approach encompassing various security measures, including strong encryption algorithms, secure key management, and regular security audits.
- Regular Updates and Patching: Promptly addressing vulnerabilities and regularly updating cryptographic libraries are crucial to mitigating risks and preventing exploitation.
- Thorough Testing and Code Review: Rigorous testing and code review are essential to identify and rectify vulnerabilities before deployment.
- Security Awareness Training: Educating staff about security best practices and potential threats is critical in preventing human error, a common cause of security breaches.
- Financial and Reputational Costs: Neglecting cryptographic security can lead to significant financial losses, reputational damage, and legal liabilities.
Future Trends in Server-Side Cryptography

The landscape of server-side cryptography is constantly evolving, driven by the increasing sophistication of cyber threats and the emergence of new technological capabilities. Maintaining robust security requires a proactive approach, anticipating future challenges and adopting emerging cryptographic techniques. This section explores key trends shaping the future of server-side security and the challenges that lie ahead.The next generation of cryptographic shields will rely heavily on advancements in several key areas.
Post-quantum cryptography, for instance, is crucial in preparing for the advent of quantum computers, which pose a significant threat to currently used public-key cryptosystems. Similarly, homomorphic encryption offers the potential for secure computation on encrypted data, revolutionizing data privacy and security in various applications.
Post-Quantum Cryptography
Post-quantum cryptography (PQC) focuses on developing cryptographic algorithms that are resistant to attacks from both classical and quantum computers. Current widely-used algorithms like RSA and ECC are vulnerable to attacks from sufficiently powerful quantum computers. The National Institute of Standards and Technology (NIST) has been leading the effort to standardize PQC algorithms, with several candidates currently under consideration for standardization.
The transition to PQC will require significant infrastructure changes, including updating software libraries, hardware, and protocols. The successful adoption of PQC will be vital in ensuring the long-term security of server-side systems. Examples of PQC algorithms include CRYSTALS-Kyber (for key encapsulation) and CRYSTALS-Dilithium (for digital signatures). These algorithms are designed to be resistant to known quantum algorithms, offering a path towards a more secure future.
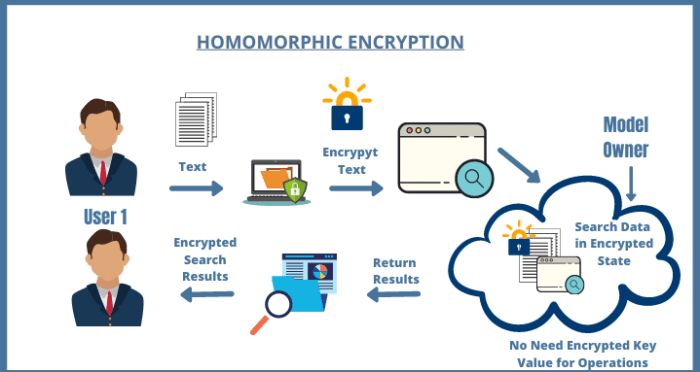
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on encrypted data without decryption. This groundbreaking technology enables secure cloud computing, data analysis, and collaborative work on sensitive information. While fully homomorphic encryption (FHE) remains computationally expensive, advancements in partially homomorphic encryption (PHE) schemes are making them increasingly practical for specific applications. For example, PHE could be used to perform aggregate statistics on encrypted data stored on a server without compromising individual data points.
The increasing practicality of homomorphic encryption presents significant opportunities for enhancing the security and privacy of server-side applications.
Challenges in Maintaining Effective Cryptographic Shields
Maintaining the effectiveness of cryptographic shields in the face of evolving threats presents ongoing challenges. The rapid pace of technological advancement requires continuous adaptation and the development of new cryptographic techniques. The complexity of implementing and managing cryptographic systems, particularly in large-scale deployments, can lead to vulnerabilities if not handled correctly. Furthermore, the increasing reliance on interconnected systems and the growth of the Internet of Things (IoT) introduce new attack vectors and increase the potential attack surface.
Addressing these challenges requires a multi-faceted approach that encompasses rigorous security audits, proactive threat modeling, and the adoption of robust security practices. One significant challenge is the potential for “crypto-agility,” the ability to easily switch cryptographic algorithms as needed to adapt to new threats or vulnerabilities.
Resources for Further Research
The following resources offer valuable insights into advanced cryptographic techniques and best practices:
- NIST Post-Quantum Cryptography Standardization Project: Provides information on the standardization process and the candidate algorithms.
- IACR (International Association for Cryptologic Research): A leading organization in the field of cryptography, offering publications and conferences.
- Cryptography Engineering Research Group (University of California, Berkeley): Conducts research on practical aspects of cryptography.
- Various academic journals and conferences dedicated to cryptography and security.
Last Word
Building a robust cryptographic shield for your server is an ongoing process, requiring vigilance and adaptation to evolving threats. By understanding the core components, implementing best practices, and staying informed about emerging technologies, you can significantly reduce your server’s vulnerability and protect your valuable data. Remember, a proactive and layered approach to server security, incorporating a strong cryptographic foundation, is the key to maintaining a secure and reliable online presence.
FAQ Overview
What are the common types of attacks a cryptographic shield protects against?
A cryptographic shield protects against various attacks, including data breaches, unauthorized access, man-in-the-middle attacks, and denial-of-service attacks. It also helps ensure data integrity and authenticity.
How often should I update my cryptographic keys?
The frequency of key updates depends on the sensitivity of your data and the risk level. Regular updates, following industry best practices, are crucial. Consider factors like key length, algorithm strength, and potential threats.
What happens if my cryptographic shield is compromised?
A compromised cryptographic shield can lead to severe consequences, including data breaches, financial losses, reputational damage, and legal repercussions. A comprehensive incident response plan is essential.
Can I implement a cryptographic shield myself, or do I need expert help?
The complexity of implementation depends on your technical expertise and the specific needs of your server. While some aspects can be handled independently, professional assistance is often recommended for optimal security and compliance.