Server Security Trends: Cryptography Leads the Way. The digital landscape is a battlefield, a constant clash between innovation and malicious intent. As servers become the lifeblood of modern businesses and infrastructure, securing them is no longer a luxury—it’s a necessity. This exploration delves into the evolving strategies for safeguarding server environments, highlighting the pivotal role of cryptography in this ongoing arms race.
We’ll examine the latest advancements, from post-quantum cryptography to zero-trust architectures, and uncover the key practices that organizations must adopt to stay ahead of emerging threats.
From traditional encryption methods to the cutting-edge advancements in post-quantum cryptography, we’ll dissect the techniques used to protect sensitive data. We’ll also cover crucial aspects of server hardening, data loss prevention (DLP), and the implementation of robust security information and event management (SIEM) systems. Understanding these strategies is paramount for building a resilient and secure server infrastructure capable of withstanding the ever-evolving cyber threats of today and tomorrow.
Introduction to Server Security Trends
The current landscape of server security is characterized by a constantly evolving threat environment. Cybercriminals are employing increasingly sophisticated techniques, targeting vulnerabilities in both hardware and software to gain unauthorized access to sensitive data and systems. This includes everything from distributed denial-of-service (DDoS) attacks that overwhelm servers, rendering them inaccessible, to highly targeted exploits leveraging zero-day vulnerabilities before patches are even available.
The rise of ransomware attacks, which encrypt data and demand payment for its release, further complicates the situation, causing significant financial and reputational damage to organizations.The interconnected nature of today’s world underscores the critical importance of robust server security measures. Businesses rely heavily on servers to store and process crucial data, manage operations, and interact with customers. A successful cyberattack can lead to data breaches, service disruptions, financial losses, legal liabilities, and damage to brand reputation.
The impact extends beyond individual organizations; widespread server vulnerabilities can trigger cascading failures across interconnected systems, affecting entire industries or even critical infrastructure. Therefore, investing in and maintaining strong server security is no longer a luxury but a necessity for survival and success in the digital age.
Evolution of Server Security Technologies
Server security technologies have undergone a significant evolution, driven by the escalating sophistication of cyber threats. Early approaches primarily focused on perimeter security, using firewalls and intrusion detection systems to prevent unauthorized access. However, the shift towards cloud computing and the increasing reliance on interconnected systems necessitate a more comprehensive and layered approach. Modern server security incorporates a variety of technologies, including advanced firewalls, intrusion prevention systems, data loss prevention (DLP) tools, vulnerability scanners, security information and event management (SIEM) systems, and endpoint detection and response (EDR) solutions.
The integration of these technologies enables proactive threat detection, real-time response capabilities, and improved incident management. Furthermore, the increasing adoption of automation and artificial intelligence (AI) in security solutions allows for more efficient threat analysis and response, helping organizations stay ahead of emerging threats. The move towards zero trust architecture, which assumes no implicit trust, further enhances security by verifying every access request regardless of its origin.
Cryptography’s Role in Server Security
Cryptography is the cornerstone of modern server security, providing the essential tools to protect data confidentiality, integrity, and authenticity. Without robust cryptographic techniques, sensitive information stored on and transmitted to and from servers would be vulnerable to interception, alteration, and unauthorized access. This section details the key cryptographic methods used to safeguard server environments.
Encryption Techniques for Server Data Protection
Encryption is the process of transforming readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic key. Only those possessing the correct key can decrypt the ciphertext back into plaintext. This protects data at rest (stored on servers) and in transit (moving between servers or clients). Several encryption techniques are employed, categorized broadly as symmetric and asymmetric.
Symmetric and Asymmetric Encryption Algorithms
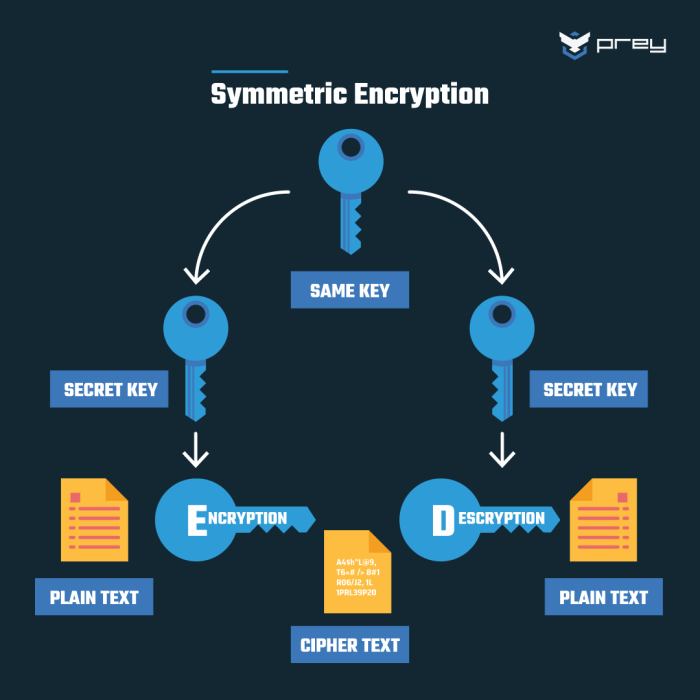
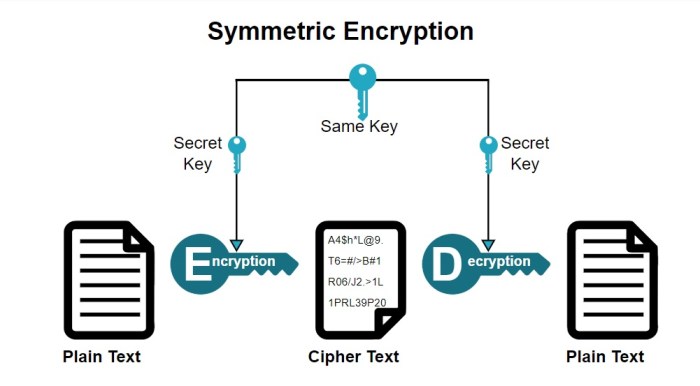
Symmetric encryption uses the same key for both encryption and decryption. This is generally faster than asymmetric encryption but requires secure key exchange. Examples include Advanced Encryption Standard (AES), a widely adopted standard known for its robustness, and Triple DES (3DES), an older but still relevant algorithm offering a balance of security and compatibility. AES operates with key sizes of 128, 192, or 256 bits, with longer key lengths offering greater security.
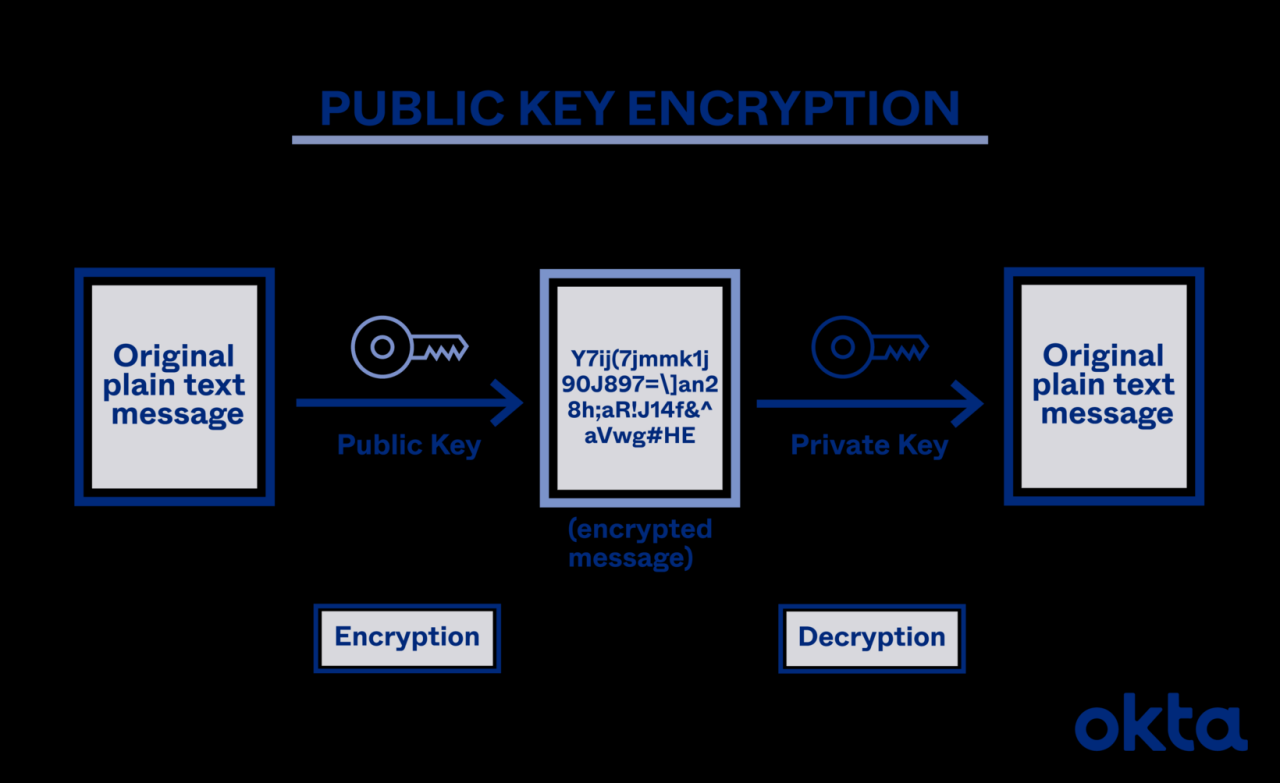
3DES uses three iterations of DES to enhance its security.Asymmetric encryption, also known as public-key cryptography, uses a pair of keys: a public key for encryption and a private key for decryption. The public key can be widely distributed, while the private key must be kept secret. This eliminates the need for secure key exchange inherent in symmetric encryption.
Examples include RSA, a widely used algorithm based on the mathematical difficulty of factoring large numbers, and Elliptic Curve Cryptography (ECC), which offers comparable security with smaller key sizes, making it efficient for resource-constrained environments. RSA keys are typically much larger than ECC keys for the same level of security.
Public Key Infrastructure (PKI) for Secure Server Communications
Public Key Infrastructure (PKI) is a system for creating, managing, distributing, using, storing, and revoking digital certificates and managing public-key cryptography. It provides a framework for verifying the authenticity and integrity of digital identities and ensuring secure communication. PKI is crucial for securing server communications, especially in HTTPS (using SSL/TLS certificates) and other secure protocols.
| PKI Component | Description | Example | Importance |
|---|---|---|---|
| Certificate Authority (CA) | Issues and manages digital certificates, vouching for the identity of entities. | Let’s Encrypt, DigiCert, GlobalSign | Provides trust and verification of digital identities. |
| Digital Certificate | Contains the public key of an entity, along with information verifying its identity, issued by a CA. | SSL/TLS certificate for a website | Provides authentication and encryption capabilities. |
| Registration Authority (RA) | Assists CAs by verifying the identities of applicants requesting certificates. | Internal department within an organization | Streamlines the certificate issuance process. |
| Certificate Revocation List (CRL) | A list of revoked certificates, indicating that they are no longer valid. | Published by CAs | Ensures that compromised certificates are not used. |
Hashing Algorithms for Data Integrity
Hashing algorithms generate a fixed-size string of characters (a hash) from an input data. Even a small change in the input data results in a significantly different hash. This is used to verify data integrity, ensuring that data has not been tampered with during storage or transmission. Examples include SHA-256 and SHA-3, which are widely used for their security and collision resistance.
Hashing is frequently used in conjunction with digital signatures to ensure both authenticity and integrity.
Digital Signatures for Authentication and Non-Repudiation
Digital signatures use cryptography to verify the authenticity and integrity of digital data. They provide a mechanism to ensure that a message or document originated from a specific sender and has not been altered. They are based on asymmetric cryptography, using the sender’s private key to create the signature and the sender’s public key to verify it. This prevents forgery and provides non-repudiation, meaning the sender cannot deny having signed the data.
Post-Quantum Cryptography and its Implications
The advent of quantum computing presents a significant threat to the security of current cryptographic systems. Quantum computers, leveraging the principles of quantum mechanics, possess the potential to break widely used public-key algorithms like RSA and ECC, which underpin much of our digital security infrastructure. This necessitates a proactive shift towards post-quantum cryptography (PQC), algorithms designed to withstand attacks from both classical and quantum computers.The ability of quantum computers to efficiently solve the mathematical problems that secure our current systems is a serious concern.
For example, Shor’s algorithm, a quantum algorithm, can factor large numbers exponentially faster than the best-known classical algorithms, rendering RSA encryption vulnerable. Similarly, other quantum algorithms threaten the security of elliptic curve cryptography (ECC), another cornerstone of modern security. The potential consequences of a successful quantum attack range from data breaches and financial fraud to the disruption of critical infrastructure.
Promising Post-Quantum Cryptographic Algorithms
Several promising post-quantum cryptographic algorithms are currently under consideration for standardization. These algorithms leverage various mathematical problems believed to be hard for both classical and quantum computers. The National Institute of Standards and Technology (NIST) has led a significant effort to evaluate and standardize these algorithms, culminating in the selection of several algorithms for different cryptographic tasks. These algorithms represent diverse approaches, including lattice-based cryptography, code-based cryptography, multivariate cryptography, and hash-based cryptography.
Each approach offers unique strengths and weaknesses, leading to a diverse set of standardized algorithms to ensure robust security against various quantum attacks.
Preparing for the Transition to Post-Quantum Cryptography
Organizations need to begin planning for the transition to post-quantum cryptography proactively. A phased approach is recommended, starting with risk assessment and inventory of cryptographic systems. This involves identifying which systems rely on vulnerable algorithms and prioritizing their migration to PQC-resistant alternatives. The selection of appropriate PQC algorithms will depend on the specific application and security requirements.
Consideration should also be given to interoperability and compatibility with existing systems. Furthermore, organizations should engage in thorough testing and validation of their PQC implementations to ensure their effectiveness and security. Pilot projects can help assess the impact of PQC on existing systems and processes before widespread deployment. For example, a financial institution might begin by implementing PQC for a specific application, such as secure communication between branches, before extending it to other critical systems.
The transition to post-quantum cryptography is a significant undertaking, requiring careful planning, coordination, and ongoing monitoring. Early adoption and planning will be crucial to mitigating the potential risks posed by quantum computing.
Secure Configuration and Hardening
Secure server configuration and hardening are critical for mitigating vulnerabilities and protecting sensitive data. A robust security posture relies on proactive measures to minimize attack surfaces and limit the impact of successful breaches. This involves a multi-layered approach encompassing operating system updates, firewall management, access control mechanisms, and regular security assessments.
Implementing a comprehensive security strategy requires careful attention to detail and a thorough understanding of potential threats. Neglecting these crucial aspects can leave servers vulnerable to exploitation, leading to data breaches, service disruptions, and significant financial losses.
Secure Server Configuration Checklist
A secure server configuration checklist should be a cornerstone of any organization’s security policy. This checklist should be regularly reviewed and updated to reflect evolving threat landscapes and best practices. The following points represent a comprehensive, though not exhaustive, list of critical considerations.
- Operating System Updates: Implement a robust patching strategy to address known vulnerabilities promptly. This includes installing all critical and security updates released by the operating system vendor. Automate the update process whenever possible to ensure timely patching.
- Firewall Rules: Configure firewalls to allow only necessary network traffic. Implement the principle of least privilege, blocking all inbound and outbound connections except those explicitly required for legitimate operations. Regularly review and update firewall rules to reflect changes in application requirements and security posture.
- Access Controls: Implement strong access control mechanisms, including user authentication, authorization, and account management. Employ the principle of least privilege, granting users only the necessary permissions to perform their tasks. Regularly review and revoke unnecessary access privileges.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and misconfigurations. These audits should encompass all aspects of the server’s security posture, including operating system settings, network configurations, and application security.
- Log Management: Implement robust log management practices to monitor server activity and detect suspicious behavior. Centralized log management systems facilitate efficient analysis and incident response.
- Data Encryption: Encrypt sensitive data both in transit and at rest using strong encryption algorithms. This protects data from unauthorized access even if the server is compromised.
- Regular Backups: Regularly back up server data to a secure offsite location. This ensures business continuity in the event of a disaster or data loss.
The Importance of Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying and mitigating vulnerabilities before they can be exploited by malicious actors. Security audits provide a systematic evaluation of the server’s security posture, identifying weaknesses in configuration, access controls, and other security mechanisms. Penetration testing simulates real-world attacks to assess the effectiveness of security controls and identify potential vulnerabilities.
A combination of both is highly recommended. Security audits offer a broader, more comprehensive view of the security landscape, while penetration testing provides a more targeted approach, focusing on potential points of entry and exploitation. The frequency of these assessments should be determined based on the criticality of the server and the associated risk profile.
Multi-Factor Authentication (MFA) Implementation, Server Security Trends: Cryptography Leads the Way
Multi-factor authentication (MFA) significantly enhances server security by requiring users to provide multiple forms of authentication before gaining access. This adds a layer of protection beyond traditional password-based authentication, making it significantly more difficult for attackers to compromise accounts, even if they obtain passwords through phishing or other means. Common MFA methods include one-time passwords (OTPs) generated by authenticator apps, security keys, and biometric authentication.
Implementing MFA involves configuring the server’s authentication system to require multiple factors. This might involve integrating with a third-party MFA provider or using built-in MFA capabilities offered by the operating system or server software. Careful consideration should be given to the choice of MFA methods, balancing security with usability and user experience.
Server security trends clearly indicate cryptography’s rising importance, driving the need for robust encryption methods. To stay ahead, understanding and implementing advanced techniques is crucial; learn more by checking out this guide on Secure Your Server with Advanced Cryptographic Techniques for practical steps. Ultimately, prioritizing strong cryptography remains paramount in today’s evolving threat landscape.
Data Loss Prevention (DLP) Strategies
Data loss in server environments can lead to significant financial losses, reputational damage, and legal repercussions. Effective Data Loss Prevention (DLP) strategies are crucial for mitigating these risks. These strategies encompass a multi-layered approach, combining technical controls with robust policies and procedures.
Common Data Loss Scenarios in Server Environments
Data breaches resulting from malicious attacks, such as ransomware or SQL injection, represent a major threat. Accidental deletion or modification of data by authorized personnel is another common occurrence. System failures, including hardware malfunctions and software bugs, can also lead to irretrievable data loss. Finally, insider threats, where employees intentionally or unintentionally compromise data security, pose a significant risk.
These scenarios highlight the need for comprehensive DLP measures.
Best Practices for Implementing DLP Measures
Implementing effective DLP requires a layered approach combining several key strategies. Data encryption, both in transit and at rest, is paramount. Strong encryption algorithms, coupled with secure key management practices, render stolen data unusable. Robust access control mechanisms, such as role-based access control (RBAC), limit user access to only the data necessary for their roles, minimizing the potential impact of compromised credentials.
Regular data backups are essential for recovery in case of data loss events. These backups should be stored securely, ideally offsite, to protect against physical damage or theft. Continuous monitoring and logging of server activity provides crucial insights into potential threats and data breaches, allowing for prompt remediation. Regular security audits and vulnerability assessments identify and address weaknesses in the server infrastructure before they can be exploited.
DLP Techniques and Effectiveness
The effectiveness of different DLP techniques varies depending on the specific threat. The following table Artikels several common techniques and their effectiveness against various threats:
| DLP Technique | Effectiveness Against Malicious Attacks | Effectiveness Against Accidental Data Loss | Effectiveness Against Insider Threats |
|---|---|---|---|
| Data Encryption | High (renders stolen data unusable) | High (protects data even if lost or stolen) | High (prevents unauthorized access to encrypted data) |
| Access Control (RBAC) | Medium (limits access to sensitive data) | Low (does not prevent accidental deletion) | Medium (restricts access based on roles and responsibilities) |
| Data Loss Prevention Software | Medium (can detect and prevent data exfiltration) | Low (primarily focuses on preventing unauthorized access) | Medium (can monitor user activity and detect suspicious behavior) |
| Regular Backups | High (allows data recovery after a breach) | High (allows recovery from accidental deletion or corruption) | Medium (does not prevent data loss but enables recovery) |
Zero Trust Security Model for Servers
The Zero Trust security model represents a significant shift from traditional perimeter-based security. Instead of assuming that anything inside the network is trustworthy, Zero Trust operates on the principle of “never trust, always verify.” This approach is particularly crucial for server environments, where sensitive data resides and potential attack vectors are numerous. By implementing Zero Trust, organizations can significantly reduce their attack surface and improve their overall security posture.Zero Trust security principles are based on continuous verification of every access request, regardless of origin.
This involves strong authentication, authorization, and continuous monitoring of all users and devices accessing server resources. The core tenet is to grant access only to the specific resources needed, for the shortest possible time, and with the least possible privileges. This granular approach minimizes the impact of a potential breach, as compromised credentials or systems will only grant access to a limited subset of resources.
Implementing Zero Trust in Server Environments
Implementing Zero Trust in a server environment involves a multi-faceted approach. Micro-segmentation plays a critical role in isolating different server workloads and applications. This technique divides the network into smaller, isolated segments, limiting the impact of a breach within a specific segment. For example, a database server could be isolated from a web server, preventing lateral movement by an attacker.
Combined with micro-segmentation, the principle of least privilege access ensures that users and applications only have the minimum necessary permissions to perform their tasks. This minimizes the damage caused by compromised accounts, as attackers would not have elevated privileges to access other critical systems or data. Strong authentication mechanisms, such as multi-factor authentication (MFA), are also essential, providing an additional layer of security against unauthorized access.
Regular security audits and vulnerability scanning are crucial to identify and address potential weaknesses in the server infrastructure.
Comparison of Zero Trust and Traditional Perimeter-Based Security
Traditional perimeter-based security models rely on a castle-and-moat approach, assuming that anything inside the network perimeter is trusted. This model focuses on securing the network boundary, such as firewalls and intrusion detection systems. However, this approach becomes increasingly ineffective in today’s distributed and cloud-based environments. Zero Trust, in contrast, operates on a “never trust, always verify” principle, regardless of location.
This makes it significantly more resilient to modern threats, such as insider threats and sophisticated attacks that bypass perimeter defenses. While traditional models rely on network segmentation at a broad level, Zero Trust utilizes micro-segmentation for much finer-grained control and isolation. In summary, Zero Trust provides a more robust and adaptable security posture compared to the traditional perimeter-based approach, particularly crucial in the dynamic landscape of modern server environments.
Emerging Trends in Server Security
The landscape of server security is constantly evolving, driven by advancements in technology and the ever-increasing sophistication of cyber threats. Several emerging trends are significantly impacting how organizations approach server protection, demanding a proactive and adaptive security posture. These trends, including AI-powered security, blockchain technology, and serverless computing security, offer both significant benefits and unique challenges.
AI-Powered Security
Artificial intelligence is rapidly transforming server security by automating threat detection, response, and prevention. AI algorithms can analyze vast amounts of data from various sources – network traffic, system logs, and security tools – to identify anomalies and potential threats that might escape traditional rule-based systems. This capability enables faster and more accurate detection of intrusions, malware, and other malicious activities.
For example, AI-powered intrusion detection systems can learn the normal behavior patterns of a server and flag deviations as potential threats, significantly reducing the time it takes to identify and respond to attacks. However, challenges remain, including the need for high-quality training data to ensure accurate model performance and the potential for adversarial attacks that could manipulate AI systems.
The reliance on AI also introduces concerns about explainability and bias, requiring careful consideration of ethical implications and ongoing model monitoring.
Blockchain Technology in Server Security
Blockchain’s decentralized and immutable nature offers intriguing possibilities for enhancing server security. Its cryptographic security and transparency can improve data integrity, access control, and auditability. For instance, blockchain can be used to create a secure and transparent log of all server access attempts, making it difficult to tamper with or falsify audit trails. This can significantly aid in forensic investigations and compliance efforts.
Furthermore, blockchain can facilitate secure key management and identity verification, reducing the risk of unauthorized access. However, the scalability and performance of blockchain technology remain challenges, particularly when dealing with large volumes of server-related data. The energy consumption associated with some blockchain implementations also raises environmental concerns. Despite these challenges, blockchain’s potential to enhance server security is being actively explored, with promising applications emerging in areas such as secure software updates and tamper-proof configurations.
Serverless Computing Security
The rise of serverless computing presents both opportunities and challenges for security professionals. While serverless architectures abstract away much of the server management burden, they also introduce new attack vectors and complexities. Since developers don’t manage the underlying infrastructure, they rely heavily on the cloud provider’s security measures. This necessitates careful consideration of the security posture of the chosen cloud provider and a thorough understanding of the shared responsibility model.
Additionally, the ephemeral nature of serverless functions can make it challenging to monitor and log activities, potentially hindering threat detection and response. Securing serverless functions requires a shift in security practices, focusing on code-level security, identity and access management, and robust logging and monitoring. For example, implementing rigorous code review processes and using secure coding practices can mitigate vulnerabilities in serverless functions.
The use of fine-grained access control mechanisms can further restrict access to sensitive data and resources. Despite these challenges, serverless computing offers the potential for improved scalability, resilience, and cost-effectiveness, provided that security best practices are carefully implemented and monitored.
Vulnerability Management and Remediation: Server Security Trends: Cryptography Leads The Way
Proactive vulnerability management is crucial for maintaining server security. A robust process involves identifying potential weaknesses, assessing their risk, and implementing effective remediation strategies. This systematic approach minimizes the window of opportunity for attackers and reduces the likelihood of successful breaches.Vulnerability management encompasses a cyclical process of identifying, assessing, and remediating security flaws within server infrastructure. This involves leveraging automated tools and manual processes to pinpoint vulnerabilities, determine their severity, and implement corrective actions to mitigate identified risks.
Regular vulnerability scans, penetration testing, and security audits form the backbone of this ongoing effort, ensuring that servers remain resilient against emerging threats.
Vulnerability Identification and Assessment
Identifying vulnerabilities begins with utilizing automated vulnerability scanners. These tools analyze server configurations and software for known weaknesses, often referencing publicly available vulnerability databases like the National Vulnerability Database (NVD). Manual code reviews and security audits, performed by skilled security professionals, supplement automated scans to identify vulnerabilities not detectable by automated tools. Assessment involves prioritizing vulnerabilities based on their severity (critical, high, medium, low) and the likelihood of exploitation.
This prioritization guides the remediation process, ensuring that the most critical vulnerabilities are addressed first. Factors such as the vulnerability’s exploitability, the impact of a successful exploit, and the availability of a patch influence the severity rating. For example, a critical vulnerability might be a remotely exploitable flaw that allows for complete server compromise, while a low-severity vulnerability might be a minor configuration issue with limited impact.
The Role of Vulnerability Scanners and Penetration Testing Tools
Vulnerability scanners are automated tools that systematically probe servers for known weaknesses. They compare the server’s configuration and software versions against known vulnerabilities, providing a report detailing identified issues. Examples include Nessus, OpenVAS, and QualysGuard. Penetration testing, on the other hand, simulates real-world attacks to identify vulnerabilities that scanners might miss. Ethical hackers attempt to exploit weaknesses to determine the effectiveness of existing security controls and to uncover hidden vulnerabilities.
Penetration testing provides a more holistic view of server security posture than vulnerability scanning alone, revealing vulnerabilities that may not be publicly known or readily detectable through automated means. For instance, a penetration test might uncover a poorly configured firewall rule that allows unauthorized access, a vulnerability that a scanner might overlook.
Remediation Procedures
Handling a discovered security vulnerability follows a structured process. First, the vulnerability is verified to ensure it’s a genuine threat and not a false positive from the scanning tool. Next, the severity and potential impact are assessed to determine the urgency of remediation. This assessment considers factors like the vulnerability’s exploitability, the sensitivity of the data at risk, and the potential business impact of a successful exploit.
Once the severity is established, a remediation plan is developed and implemented. This plan may involve applying security patches, updating software, modifying server configurations, or implementing compensating controls. Following remediation, the vulnerability is retested to confirm that the issue has been successfully resolved. Finally, the entire process is documented, including the vulnerability details, the remediation steps taken, and the verification results.
This documentation aids in tracking remediation efforts and improves the overall security posture. For example, if a vulnerability in a web server is discovered, the remediation might involve updating the server’s software to the latest version, which includes a patch for the vulnerability. The server would then be retested to ensure the vulnerability is no longer present.
Security Information and Event Management (SIEM)
SIEM systems play a crucial role in modern server security by aggregating and analyzing security logs from various sources across an organization’s infrastructure. This centralized approach provides comprehensive visibility into security events, enabling proactive threat detection and rapid incident response. Effective SIEM implementation is vital for maintaining a strong security posture in today’s complex threat landscape.SIEM systems monitor and analyze server security logs from diverse sources, including operating systems, applications, databases, and network devices.
This consolidated view allows security analysts to identify patterns and anomalies indicative of malicious activity or security vulnerabilities. The analysis capabilities of SIEM extend beyond simple log aggregation, employing sophisticated algorithms to correlate events, detect threats, and generate alerts based on predefined rules and baselines. This real-time monitoring facilitates prompt identification and response to security incidents.
SIEM’s Role in Incident Detection and Response
SIEM’s core functionality revolves around detecting and responding to security incidents. By analyzing security logs, SIEM systems can identify suspicious activities such as unauthorized access attempts, data breaches, malware infections, and policy violations. Upon detecting a potential incident, the system generates alerts, notifying security personnel and providing contextual information to facilitate swift investigation and remediation. Automated responses, such as blocking malicious IP addresses or quarantining infected systems, can be configured to accelerate the incident response process and minimize potential damage.
The ability to replay events chronologically provides a detailed timeline of the incident, crucial for root cause analysis and preventing future occurrences. For example, a SIEM system might detect a large number of failed login attempts from a single IP address, triggering an alert and potentially initiating an automated block on that IP address. This rapid response can prevent a brute-force attack from succeeding.
SIEM Integration with Other Security Tools
The effectiveness of SIEM is significantly enhanced by its integration with other security tools. Seamless integration with tools like intrusion detection systems (IDS), vulnerability scanners, and endpoint detection and response (EDR) solutions creates a comprehensive security ecosystem. For instance, alerts generated by an IDS can be automatically ingested into the SIEM, enriching the context of security events and providing a more complete picture of the threat landscape.
Similarly, vulnerability scan results can be correlated with security events to prioritize remediation efforts and focus on the most critical vulnerabilities. Integration with EDR tools provides granular visibility into endpoint activity, enabling faster detection and response to endpoint-based threats. A well-integrated SIEM becomes the central hub for security information, facilitating more effective threat detection and incident response.
A hypothetical example: a vulnerability scanner identifies a critical vulnerability on a web server. The SIEM integrates this information, and if a subsequent exploit attempt is detected, the SIEM correlates the event with the known vulnerability, immediately alerting the security team and providing detailed context.
Closure
Securing server infrastructure in today’s complex digital world demands a multifaceted approach. While cryptography remains the cornerstone of server security, a holistic strategy incorporating robust configuration management, proactive vulnerability management, and the adoption of innovative security models like Zero Trust is crucial. By embracing emerging technologies like AI-powered security and staying informed about the latest threats, organizations can build a resilient defense against the ever-evolving landscape of cyberattacks.
The journey to optimal server security is continuous, demanding constant vigilance and adaptation to ensure the protection of valuable data and systems.
Expert Answers
What are some common server vulnerabilities?
Common vulnerabilities include outdated software, weak passwords, misconfigured firewalls, and unpatched operating systems. SQL injection and cross-site scripting (XSS) are also prevalent web application vulnerabilities that can compromise server security.
How often should server security audits be conducted?
The frequency of security audits depends on the criticality of the server and the industry regulations. However, at least annual audits are recommended, with more frequent checks for high-risk systems.
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption.
How can I implement multi-factor authentication (MFA) on my servers?
MFA can be implemented using various methods such as time-based one-time passwords (TOTP), hardware security keys, or biometric authentication. The specific implementation depends on the server operating system and available tools.