Encryption for Servers: Comprehensive Guide – Encryption for Servers: A Comprehensive Guide delves into the crucial role of encryption in securing sensitive data. This guide explores various encryption methods, from symmetric to asymmetric algorithms, and provides a practical understanding of implementation across different server operating systems and layers. We’ll navigate the complexities of key management, SSL/TLS configurations, database encryption, and address common challenges, ultimately empowering you to build robust and secure server environments.
We’ll examine the strengths and weaknesses of common algorithms like AES, RSA, and ECC, offering a clear comparison of their security levels and performance impacts. This guide also covers best practices for key rotation, monitoring encryption effectiveness, and mitigating potential vulnerabilities. By the end, you’ll have a solid grasp of the principles and techniques needed to secure your server infrastructure effectively.
Introduction to Server Encryption
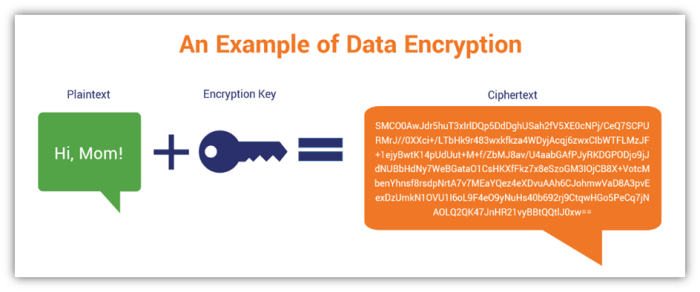
Server encryption is paramount for safeguarding sensitive data stored on and transmitted through servers. In today’s interconnected world, where cyber threats are ever-present, robust encryption is no longer a luxury but a necessity for maintaining data integrity, confidentiality, and compliance with regulations like GDPR and HIPAA. Without proper encryption, sensitive information—including customer data, financial records, and intellectual property—becomes vulnerable to theft, unauthorized access, and breaches, leading to significant financial losses, reputational damage, and legal repercussions.The core function of server encryption is to transform readable data (plaintext) into an unreadable format (ciphertext) using cryptographic algorithms.
This ensures that even if an attacker gains access to the server, the data remains protected and unintelligible without the appropriate decryption key. The choice of encryption method significantly impacts the security and performance of the server.
Types of Server Encryption
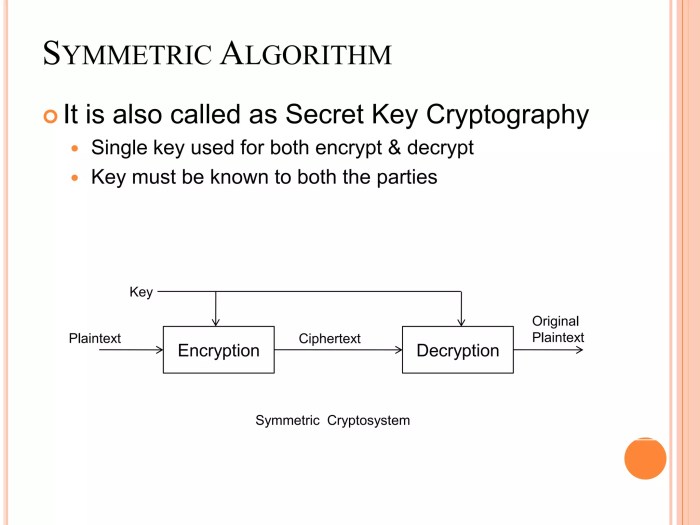
Server encryption primarily employs two types of cryptography: symmetric and asymmetric. Symmetric encryption uses the same secret key for both encryption and decryption. This method is generally faster and more efficient than asymmetric encryption, making it suitable for encrypting large volumes of data. However, secure key exchange presents a challenge. Asymmetric encryption, on the other hand, uses a pair of keys: a public key for encryption and a private key for decryption.
The public key can be widely distributed, while the private key must remain confidential. This eliminates the need for secure key exchange, making it ideal for secure communication and digital signatures. However, it’s computationally more intensive than symmetric encryption.
Common Encryption Algorithms
Several encryption algorithms are commonly used for server security. These algorithms are constantly being evaluated and updated to withstand evolving attack techniques. Symmetric algorithms like AES (Advanced Encryption Standard) are widely used for their speed and robustness. AES is available in various key sizes (128, 192, and 256 bits), with longer key sizes offering greater security. Another example is 3DES (Triple DES), an older but still used algorithm, offering a balance between security and compatibility.
For asymmetric encryption, RSA (Rivest-Shamir-Adleman) is a prevalent algorithm used for key exchange and digital signatures. Elliptic Curve Cryptography (ECC) is a newer algorithm that offers comparable security to RSA but with smaller key sizes, leading to improved performance and efficiency. The selection of an appropriate algorithm depends on factors like security requirements, performance needs, and compatibility with existing infrastructure.
Choosing a strong and well-vetted algorithm is crucial for maintaining a high level of security.
Choosing the Right Encryption Method: Encryption For Servers: Comprehensive Guide
Selecting the appropriate encryption method for your server is crucial for maintaining data confidentiality and integrity. The choice depends on a complex interplay of factors, including the sensitivity of the data, performance requirements, and the overall security architecture. A poorly chosen encryption method can leave your server vulnerable to attacks, while an overly secure method might significantly impact performance.
This section will analyze several common encryption algorithms and the considerations involved in making an informed decision.
Symmetric and asymmetric encryption algorithms offer distinct advantages and disadvantages. Symmetric algorithms, like AES, use the same key for encryption and decryption, offering faster speeds. Asymmetric algorithms, such as RSA and ECC, utilize separate keys for encryption and decryption, providing better key management but slower performance. The choice between them often depends on the specific application and security needs.
Comparison of Encryption Algorithms
Several factors influence the selection of an encryption algorithm for server security. Key considerations include the algorithm’s strength against known attacks, its computational performance, and the complexity of key management. Three prominent algorithms – AES, RSA, and ECC – will be compared below.
| Algorithm | Security Level | Performance | Key Management |
|---|---|---|---|
| AES-256 | Very High (considered secure for most applications, with 256-bit key size providing substantial resistance to brute-force attacks) | High (relatively fast encryption and decryption speeds) | Moderate (requires secure key exchange and storage) |
| RSA-2048 | High (2048-bit key size offers good security against current factoring algorithms, though quantum computing poses a future threat) | Low (significantly slower than AES, especially for large datasets) | Complex (requires careful handling of public and private keys, often involving certificate authorities) |
| ECC (secp256r1) | High (provides comparable security to RSA-2048 with significantly shorter key lengths, making it more efficient) | Medium (faster than RSA-2048 but generally slower than AES) | Moderate (key management is less complex than RSA but still requires secure storage and handling) |
Factors Influencing Encryption Method Selection
Choosing the optimal encryption method requires a careful assessment of various factors. These factors often involve trade-offs between security and performance. For instance, while AES-256 provides exceptional security, its performance might be a concern when encrypting massive datasets in real-time. Conversely, RSA-2048, while secure, is significantly slower. This section details these crucial factors.
Performance: The speed of encryption and decryption is critical, especially for applications requiring real-time processing. AES generally outperforms RSA and ECC in terms of speed. The performance impact should be carefully evaluated, especially for applications with high throughput requirements like database encryption or network traffic encryption.
Security Level: The chosen algorithm’s resistance to attacks is paramount. AES-256, with its large key size, offers excellent security against brute-force and known cryptanalytic attacks. RSA and ECC offer strong security, but their security is tied to the key size and the underlying mathematical problems’ difficulty. The security level must be commensurate with the sensitivity of the data being protected.
Key Management: Secure key management is crucial for any encryption system. AES requires secure key exchange and storage, which is relatively simpler compared to RSA, which necessitates managing public and private keys. ECC presents a moderate level of key management complexity, generally simpler than RSA but more complex than AES.
Implementing Server-Side Encryption
Implementing server-side encryption involves securing data at rest and in transit on your servers. This crucial security measure protects sensitive information from unauthorized access, even if the server itself is compromised. The process varies depending on the operating system and the specific encryption tools used, but generally involves configuring the encryption method, managing encryption keys, and implementing key rotation strategies.
Understanding server encryption is crucial for robust security. This “Encryption for Servers: Comprehensive Guide” delves into advanced techniques, but if you’re just starting out, check out this excellent primer: Secure Your Server: Cryptography for Beginners. Once you grasp the fundamentals, you’ll be better equipped to navigate the complexities of securing your server infrastructure with advanced encryption methods.
This section details the steps for implementing server-side encryption on Linux and Windows servers, including examples of command-line tools and best practices for key management.
Server-Side Encryption on Linux
Implementing server-side encryption on Linux systems often leverages tools like dm-crypt for full-disk encryption or tools like OpenSSL for file and directory encryption. Full-disk encryption protects all data on the hard drive, while file/directory encryption provides granular control over which data is encrypted. For example, dm-crypt, integrated with LVM (Logical Volume Manager), provides a robust solution for encrypting entire partitions or logical volumes.
The process typically involves creating an encrypted volume, configuring the system to use it at boot, and managing the encryption key. Using LUKS (Linux Unified Key Setup) enhances key management features, allowing for multiple keys and key rotation.
Server-Side Encryption on Windows
Windows Server offers BitLocker Drive Encryption for full-disk encryption and Encrypting File System (EFS) for file and folder encryption. BitLocker, integrated into the operating system, encrypts entire drives, providing strong protection against unauthorized access. EFS, on the other hand, allows for selective encryption of individual files and folders. Both BitLocker and EFS utilize strong encryption algorithms and offer key management features.
For example, BitLocker allows for recovery keys to be stored in various locations, including Active Directory or on a USB drive. Administrators can manage encryption policies through Group Policy, enforcing encryption standards across the organization.
Command-Line Tools and Scripts for Encryption Management
Various command-line tools simplify encryption setup and management. On Linux, `cryptsetup` is commonly used with dm-crypt and LUKS. It provides commands for creating, opening, and managing encrypted volumes. For example, the command `cryptsetup luksFormat /dev/sda1` formats the partition `/dev/sda1` using LUKS encryption. On Windows, `manage-bde` is a command-line tool used to manage BitLocker encryption.
For example, `manage-bde -on c:` enables BitLocker encryption on the C: drive. Custom scripts can automate these processes, ensuring consistent encryption across multiple servers. These scripts can integrate with configuration management tools like Ansible or Puppet for easier deployment and management.
Securing Encryption Keys and Managing Key Rotation
Secure key management is paramount for server-side encryption. Encryption keys should be stored securely, ideally using hardware security modules (HSMs) or other robust key management systems. Regular key rotation is crucial for mitigating the risk of compromise. Implementing a key rotation schedule, such as rotating keys every 90 days, minimizes the potential impact of a key breach.
For example, with LUKS, multiple keys can be added to an encrypted volume, allowing for phased key rotation. Similarly, BitLocker allows for key recovery options and integration with Active Directory for centralized key management. Proper key management practices are essential for maintaining the integrity and confidentiality of encrypted data.
Encryption at Different Layers
Implementing encryption across multiple layers of a server system provides a layered security approach, significantly enhancing data protection. This strategy mitigates the risk of a single point of failure compromising the entire system. By encrypting data at different stages of its lifecycle, organizations can achieve a more robust and resilient security posture. This section explores encryption at the application, database, and network layers, comparing their advantages and disadvantages.
Different layers offer varying levels of protection and granular control. Choosing the right approach depends on the sensitivity of the data, the specific security requirements, and the overall system architecture. A comprehensive strategy typically involves a combination of these layers to create a multi-layered defense.
Application Layer Encryption
Application layer encryption involves encrypting data within the application itself before it’s stored in the database or transmitted over the network. This method offers strong protection as the data remains encrypted throughout its processing within the application. It’s particularly beneficial for sensitive data that needs to be protected even from privileged users within the system.
Advantages include strong data protection even from internal threats and the ability to implement granular access controls within the application logic. However, disadvantages include increased application complexity, potential performance overhead, and the need for robust key management within the application itself. If the application itself is compromised, the encryption may be bypassed.
Database Layer Encryption
Database layer encryption focuses on protecting data at rest within the database. This is achieved through database-specific features or through the use of specialized encryption tools. This method protects data from unauthorized access to the database server itself, whether through physical access, malicious software, or network breaches.
Advantages include centralized encryption management, protection of data even if the application is compromised, and relatively straightforward integration with existing database systems. Disadvantages include potential performance impacts on database operations, the risk of encryption keys being compromised if the database server is compromised, and potential limitations on data search and retrieval capabilities if encryption is not handled carefully.
Network Layer Encryption
Network layer encryption, commonly implemented using VPNs or TLS/SSL, secures data in transit between the server and clients. This approach protects data from eavesdropping and tampering during transmission across networks. It’s crucial for protecting sensitive data exchanged over public or untrusted networks.
Advantages include broad protection for all data transmitted over the network, relatively simple implementation using standard protocols, and readily available tools and technologies. Disadvantages include reliance on the security of the encryption protocols used, the potential for performance overhead, and the fact that data is still vulnerable once it reaches the server or client.
Hypothetical System Architecture with Multi-Layered Encryption
A robust system architecture should employ encryption at multiple layers for comprehensive protection. Consider this example:
The following points detail a hypothetical system architecture incorporating encryption at multiple layers, illustrating how a multi-layered approach provides robust data security.
- Network Layer: All communication between clients and servers is secured using TLS/SSL, encrypting data in transit. This protects against eavesdropping and tampering during transmission.
- Database Layer: The database utilizes Transparent Data Encryption (TDE) to encrypt data at rest. This protects against unauthorized access to the database server.
- Application Layer: The application itself encrypts sensitive data, such as personally identifiable information (PII), before it’s stored in the database. This ensures that even if the database is compromised, the PII remains protected. The application also employs strong access controls, limiting access to sensitive data based on user roles and permissions.
Key Management Best Practices
Robust key management is the cornerstone of effective server encryption. Without secure key handling, even the strongest encryption algorithms are vulnerable. Compromised keys render your encrypted data readily accessible to attackers, negating the entire purpose of encryption. This section Artikels best practices for managing encryption keys throughout their lifecycle, minimizing risks and maximizing data protection.Key management encompasses the entire lifecycle of a cryptographic key, from its generation and storage to its use and eventual destruction.
Secure key management practices are essential for maintaining the confidentiality, integrity, and availability of sensitive data stored on servers. Failure to implement these practices can lead to significant security breaches and financial losses.
Key Generation
Secure key generation involves employing cryptographically secure pseudorandom number generators (CSPRNGs) to create keys that are statistically unpredictable. These generators should be properly seeded and regularly tested for randomness. The length of the key should be appropriate for the chosen encryption algorithm and the sensitivity of the data being protected. For example, AES-256 requires a 256-bit key, providing a significantly higher level of security than AES-128 with its 128-bit key.
Using weak or predictable keys is a major vulnerability that can be easily exploited.
Key Storage, Encryption for Servers: Comprehensive Guide
Storing encryption keys securely is paramount. Keys should never be stored in plain text or easily accessible locations. Hardware security modules (HSMs) offer a robust solution, providing tamper-resistant hardware for key generation, storage, and management. Cloud-based key management services, like those offered by major cloud providers, can also be a viable option, provided they are properly configured and audited.
Software-based solutions should only be considered if they implement strong encryption and access controls, and are regularly updated and patched. Consider the sensitivity of your data when selecting your storage method.
Key Rotation
Regular key rotation is a critical security practice. By periodically replacing encryption keys with new ones, the impact of a potential key compromise is limited. The frequency of key rotation depends on the sensitivity of the data and the potential risks. A common approach is to rotate keys every 90 days or even more frequently, based on risk assessments and regulatory requirements.
A well-defined key rotation policy should specify the process, timing, and responsibilities involved. The old keys should be securely destroyed after rotation to prevent their reuse.
Key Access Control
Restricting access to encryption keys is essential. The principle of least privilege should be applied, granting only authorized personnel access to keys based on their job responsibilities. Multi-factor authentication (MFA) should be mandatory for accessing key management systems. Regular audits and monitoring of key access logs are crucial to detect and prevent unauthorized access attempts. Implement strong access controls and regularly review user permissions to ensure they remain appropriate.
Vulnerabilities Associated with Poor Key Management
Poor key management practices can lead to several serious vulnerabilities, including data breaches, unauthorized access, and regulatory non-compliance. Examples include: storing keys in easily accessible locations; using weak or predictable keys; failing to rotate keys regularly; granting excessive access privileges; and lacking proper audit trails. These vulnerabilities can result in significant financial losses, reputational damage, and legal repercussions.
A comprehensive key management strategy is therefore crucial for mitigating these risks.
SSL/TLS and HTTPS Encryption
SSL/TLS (Secure Sockets Layer/Transport Layer Security) and HTTPS (Hypertext Transfer Protocol Secure) are fundamental to securing web server communications. They establish an encrypted link between a web server and a client (typically a web browser), protecting sensitive data transmitted during browsing and online transactions. Understanding how SSL/TLS certificates function and implementing HTTPS is crucial for any website prioritizing security.SSL/TLS certificates are digital certificates that verify the identity of a website and enable encrypted communication.
They work by using public key cryptography, where a website possesses a private key and a corresponding public key is made available to clients. This allows for secure communication without needing to share the private key, ensuring data confidentiality and integrity. The certificate, issued by a trusted Certificate Authority (CA), contains the website’s public key, its domain name, and other relevant information.
Browsers verify the certificate’s authenticity against the CA’s root certificate, ensuring the connection is legitimate and secure.
SSL/TLS Certificate Acquisition and Installation
Obtaining an SSL/TLS certificate involves several steps. First, a Certificate Signing Request (CSR) is generated, containing the website’s public key and other identifying information. This CSR is then submitted to a CA, which verifies the website’s ownership and legitimacy. Upon successful verification, the CA issues the SSL/TLS certificate. The certificate is then installed on the web server, making it ready to use HTTPS.
Different CAs offer varying levels of validation and certificate types (e.g., Domain Validated, Organization Validated, Extended Validation). The choice depends on the website’s specific needs and security requirements. After installation, the web server is configured to use the certificate for secure communication.
HTTPS Configuration on Apache and Nginx Web Servers
Configuring a web server to use HTTPS involves several steps, primarily focusing on setting up the server to listen on port 443 (the standard port for HTTPS) and associating the SSL/TLS certificate with the server. For Apache, this typically involves modifying the Apache configuration file (e.g., `httpd.conf` or a virtual host configuration file) to include directives such as `Listen 443`, `SSLEngine on`, `SSLCertificateFile`, and `SSLCertificateKeyFile`, specifying the paths to the certificate and private key files.
Nginx requires similar configuration adjustments, using directives such as `listen 443 ssl;`, `ssl_certificate`, and `ssl_certificate_key` within the server block. Proper configuration ensures that all incoming traffic on port 443 is handled securely using the SSL/TLS certificate. Regular updates and monitoring of the server’s security configuration are essential to maintain a secure environment.
Database Encryption Techniques
Protecting sensitive data stored in databases is crucial for any organization. Database encryption provides a robust mechanism to safeguard this information, even in the event of a breach. Several techniques exist, each with its own strengths and weaknesses concerning performance and implementation complexity. Choosing the right approach depends on factors like the sensitivity of the data, the database system used, and the overall security architecture.Database encryption methods broadly fall into two categories: transparent encryption and application-level encryption.
Transparent encryption handles encryption and decryption automatically at the database level, requiring minimal changes to the application. Application-level encryption, conversely, involves encrypting data within the application before it reaches the database, necessitating modifications to the application code.
Transparent Database Encryption
Transparent encryption integrates seamlessly with the database management system (DBMS). The database itself manages the encryption and decryption processes, making it largely invisible to the application. This simplifies implementation as it doesn’t require extensive application code changes. However, it can introduce performance overhead depending on the encryption algorithm and the database system’s capabilities. Common examples include using built-in encryption features within DBMSs like Oracle’s Transparent Data Encryption (TDE) or SQL Server’s Always Encrypted.
These features typically encrypt data at rest, protecting it when the database is not actively being used.
Application-Level Encryption
In application-level encryption, the application encrypts data before sending it to the database and decrypts it after retrieval. This offers greater control over the encryption process, allowing for customized encryption algorithms and key management. However, it requires significant changes to the application code, increasing development time and complexity. This method also necessitates careful handling of keys within the application to avoid compromising security.
Application-level encryption can be advantageous when granular control over data encryption is needed, for instance, encrypting only specific columns or rows.
Performance Implications of Database Encryption Techniques
The performance impact of database encryption varies depending on several factors: the encryption algorithm used (AES-256 generally offers a good balance of security and performance), the hardware used (faster processors and dedicated encryption hardware can mitigate performance bottlenecks), and the volume of data being encrypted. Transparent encryption typically introduces less performance overhead compared to application-level encryption because it leverages the database’s optimized encryption routines.
However, application-level encryption can offer more flexibility to optimize encryption for specific use cases. For example, using a faster, but potentially less secure, algorithm for less sensitive data could improve performance while still maintaining a reasonable security posture. Thorough performance testing is essential before implementing any encryption method in a production environment.
Database Encryption Tools and Features
Choosing the right database encryption tool depends on the specific needs and capabilities of your organization. Several commercial and open-source tools are available. Below is a list illustrating some examples and their general features, keeping in mind that specific features can change with updates.
| Tool | Type | Features |
|---|---|---|
| Vormetric Data Security (now part of Micro Focus) | Commercial | Transparent encryption, key management, access control, data masking. Supports various database platforms. |
| Oracle Transparent Data Encryption (TDE) | Built-in (Oracle) | Encrypts data at rest, integrated with Oracle Database. Relatively easy to implement. |
| Microsoft SQL Server Always Encrypted | Built-in (SQL Server) | Client-side encryption, allows for encryption of sensitive columns without modifying applications significantly. |
| PGP | Open-source (with commercial options) | Widely used for encryption, but requires application-level integration for database encryption. |
Note: This table provides a general overview; consult the respective vendor documentation for the most up-to-date information on features and capabilities. The choice of tool should be based on a thorough assessment of your security requirements, performance needs, and budget.
Monitoring and Auditing Encryption
Effective monitoring and auditing are crucial for ensuring the ongoing integrity and security of server encryption. Regular checks are necessary to identify vulnerabilities, detect breaches, and maintain compliance with relevant regulations. A proactive approach to monitoring and auditing minimizes risk and facilitates a swift response to any security incidents.
Monitoring and auditing server encryption involves a multi-faceted approach encompassing technical checks, log analysis, and security information and event management (SIEM) integration. This process helps maintain the effectiveness of encryption mechanisms, verify the integrity of encryption keys, and provide evidence of compliance with security policies and industry best practices.
Key Metrics for Encryption Monitoring
Regularly monitoring key metrics provides insights into the health and effectiveness of your encryption infrastructure. These metrics can reveal potential issues before they escalate into significant security breaches. Key indicators include encryption key rotation frequency, the number of successful and failed encryption attempts, and the overall performance impact of encryption on server resources. Monitoring these metrics allows for proactive identification of potential weaknesses or anomalies.
Implementing Logging and Auditing for Encryption Events
Comprehensive logging and auditing are essential for tracking encryption-related activities. Detailed logs should record events such as key generation, key rotation, encryption and decryption operations, access attempts, and any errors encountered. These logs should be stored securely and protected from unauthorized access. Implementing robust logging practices provides a valuable audit trail for investigating security incidents and demonstrating compliance with regulatory requirements.
Consider using a centralized log management system to aggregate and analyze logs from multiple servers efficiently.
Detecting and Responding to Encryption Breaches or Vulnerabilities
Proactive vulnerability scanning and penetration testing are critical components of a robust security posture. Regularly scanning for known vulnerabilities in encryption software and protocols helps identify and address potential weaknesses before they can be exploited. Penetration testing simulates real-world attacks to identify vulnerabilities that automated scans might miss. In the event of a suspected breach, a well-defined incident response plan is essential for containing the damage, investigating the root cause, and restoring system security.
This plan should Artikel procedures for isolating affected systems, analyzing logs, and notifying relevant stakeholders. Post-incident analysis is crucial for learning from past events and improving future security measures.
Addressing Common Encryption Challenges

Implementing and managing server encryption, while crucial for security, presents several hurdles. Understanding these challenges and employing effective mitigation strategies is vital for maintaining robust data protection. This section Artikels common difficulties encountered and provides practical solutions.
Many organizations face significant obstacles when attempting to implement comprehensive server encryption. These obstacles often stem from a combination of technical, logistical, and resource-related issues. Successfully navigating these challenges requires a proactive approach that prioritizes planning, thorough testing, and ongoing monitoring.
Key Management Complexity
Effective key management is paramount to successful encryption. Losing or compromising encryption keys renders the entire system vulnerable. The complexity of managing numerous keys across various servers and applications, ensuring their secure storage, rotation, and access control, is a significant challenge. Solutions include using dedicated Hardware Security Modules (HSMs) for key storage and management, implementing robust key rotation policies, and leveraging centralized key management systems.
These systems offer features such as access control lists, audit trails, and automated key lifecycle management, minimizing the risk of human error and unauthorized access.
Performance Overhead
Encryption and decryption processes consume computational resources. The impact on performance varies depending on the encryption algorithm, key size, and the hardware capabilities of the server. High-performance servers with dedicated cryptographic acceleration hardware can mitigate this impact. For instance, a server with a dedicated cryptographic coprocessor can handle encryption and decryption significantly faster than a server relying solely on its CPU.
Resource-constrained environments may require careful selection of encryption algorithms and key sizes to balance security with performance. Lightweight algorithms and optimized libraries can help minimize the performance overhead in such scenarios. For example, ChaCha20 is often preferred over AES in resource-constrained environments due to its faster performance and lower memory requirements.
Integration Challenges
Integrating encryption into existing systems can be complex, especially with legacy applications that weren’t designed with encryption in mind. Retrofitting encryption may require significant code changes and testing. Careful planning and phased implementation are crucial to minimize disruption. The use of APIs and standardized encryption libraries can simplify the integration process, ensuring compatibility and reducing development time.
Prioritizing applications handling sensitive data first during the implementation process allows for a more manageable approach and ensures the most critical assets are protected.
Cost Considerations
Implementing and maintaining robust server encryption involves costs associated with hardware, software, personnel, and training. The cost of implementing encryption can be significant, particularly for large organizations with many servers and applications. A cost-benefit analysis should be performed to justify the investment. Careful selection of encryption solutions and leveraging open-source tools can help minimize costs. Furthermore, prioritizing the encryption of the most sensitive data first can allow for a phased implementation that manages costs effectively while still providing significant security benefits.
Compliance Requirements
Meeting industry regulations and compliance standards, such as HIPAA, PCI DSS, and GDPR, often necessitates specific encryption practices. Understanding and adhering to these regulations is essential. Failing to comply can result in significant penalties. Regular audits and security assessments can help ensure ongoing compliance. Staying updated on evolving regulatory requirements is crucial to maintaining a secure and compliant environment.
Future Trends in Server Encryption
The landscape of server encryption is constantly evolving, driven by the increasing sophistication of cyber threats and the emergence of new cryptographic techniques. The next few years will witness significant advancements, impacting how we secure sensitive data at rest and in transit. This section explores key emerging technologies and their projected impact on server security.The demand for stronger, more efficient, and adaptable encryption methods is fueling innovation in the field.
This is particularly crucial given the looming threat of quantum computing, which has the potential to break many widely used encryption algorithms.
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on encrypted data without first decrypting it. This groundbreaking technology has the potential to revolutionize data privacy in cloud computing and other distributed environments. Imagine a scenario where sensitive medical data can be analyzed for research purposes without ever being decrypted, preserving patient confidentiality. While still in its early stages of development, homomorphic encryption is gradually becoming more practical and efficient, paving the way for its wider adoption in various sectors.
The improvement in performance and reduction in computational overhead are key factors driving its progress. For example, advancements in Fully Homomorphic Encryption (FHE) schemes are leading to more efficient implementations, making them suitable for real-world applications.
Post-Quantum Cryptography
The advent of quantum computers poses a significant threat to current encryption standards. Post-quantum cryptography (PQC) aims to develop cryptographic algorithms that are resistant to attacks from both classical and quantum computers. The National Institute of Standards and Technology (NIST) is currently in the process of standardizing several PQC algorithms, which are expected to replace existing algorithms in the coming years.
The transition to PQC will be a gradual process, requiring careful planning and implementation to minimize disruption and ensure seamless security. Organizations should begin assessing their current cryptographic infrastructure and developing migration plans to incorporate PQC algorithms as they become standardized. For example, migrating to algorithms like CRYSTALS-Kyber for key establishment and CRYSTALS-Dilithium for digital signatures is a likely scenario in the near future.
Serverless Encryption
The rise of serverless computing architectures necessitates new approaches to encryption. Traditional server-side encryption methods may not be directly applicable in serverless environments due to their ephemeral nature and the distributed execution model. Therefore, new techniques and tools are being developed to ensure data security in serverless functions, focusing on integrating encryption directly into the function code or leveraging managed encryption services offered by cloud providers.
This includes leveraging functionalities built into serverless platforms for encryption at rest and in transit.
AI-Powered Encryption Management
Artificial intelligence (AI) and machine learning (ML) are being increasingly utilized to enhance encryption management. AI-powered systems can automate key management tasks, detect anomalies, and proactively address potential vulnerabilities. This automation can significantly improve efficiency and reduce the risk of human error, a common cause of security breaches. For instance, AI algorithms can analyze encryption logs to identify patterns indicating potential attacks or weaknesses in the encryption system, allowing for timely intervention.
Forecast for the Next 5 Years
Over the next five years, we can expect a significant shift towards post-quantum cryptography as NIST standards become widely adopted. Homomorphic encryption will likely see increased adoption in specific niche applications, particularly those involving sensitive data analysis in regulated industries. AI-powered encryption management will become more prevalent, automating key management and improving overall security posture. The serverless computing paradigm will drive innovation in encryption techniques tailored to its unique characteristics.
Furthermore, we will likely see a greater emphasis on integrated security solutions that combine encryption with other security mechanisms to provide comprehensive protection. The adoption of these advancements will depend on factors like technological maturity, regulatory frameworks, and market demand. For example, the healthcare sector, driven by stringent data privacy regulations, is likely to be an early adopter of homomorphic encryption.
Last Word
Securing your servers effectively requires a multifaceted approach to encryption, encompassing algorithm selection, key management, and implementation across multiple layers. This comprehensive guide has provided a detailed roadmap, covering everything from choosing the right encryption method and implementing it on various operating systems to monitoring for vulnerabilities and planning for future trends in server security. By understanding and implementing the best practices Artikeld here, you can significantly strengthen your server’s defenses and protect your valuable data from unauthorized access and breaches.
Q&A
What are the legal implications of not encrypting server data?
Failure to encrypt sensitive data can lead to significant legal repercussions, depending on the jurisdiction and the type of data involved. Non-compliance with data privacy regulations like GDPR or CCPA can result in hefty fines and legal action.
How often should encryption keys be rotated?
The frequency of key rotation depends on several factors, including the sensitivity of the data and the potential threat landscape. Best practices suggest regular rotation, at least annually, and more frequently if there’s a suspected compromise.
Can I encrypt only specific files or folders on my server?
Yes, you can selectively encrypt specific files or folders using tools that offer granular control over encryption. This approach allows for targeted protection of sensitive data while leaving less critical data unencrypted.
What is the impact of encryption on server performance?
Encryption does introduce some performance overhead, but the extent varies based on the algorithm, hardware, and implementation. Modern algorithms and optimized implementations minimize this impact, making encryption practical even for resource-constrained servers.