Cryptography’s Role in Server Security is paramount in today’s digital landscape. From safeguarding sensitive data at rest to securing communications in transit, robust cryptographic techniques are the bedrock of a secure server infrastructure. Understanding the intricacies of symmetric and asymmetric encryption, hashing algorithms, and digital signatures is crucial for mitigating the ever-evolving threats to online systems. This exploration delves into the practical applications of cryptography, examining real-world examples of both successful implementations and devastating breaches caused by weak cryptographic practices.
We’ll dissect various encryption methods, comparing their strengths and weaknesses in terms of speed, security, and key management. The importance of secure key generation, storage, and rotation will be emphasized, along with the role of authentication and authorization mechanisms like digital signatures and access control lists. We will also examine secure communication protocols such as TLS/SSL, SSH, and HTTPS, analyzing their security features and vulnerabilities.
Finally, we’ll look towards the future of cryptography and its adaptation to emerging threats like quantum computing.
Introduction to Cryptography in Server Security
Cryptography is the cornerstone of modern server security, providing the essential mechanisms to protect sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction. Without robust cryptographic techniques, servers would be incredibly vulnerable to a wide range of attacks, rendering online services insecure and unreliable. Its role encompasses securing data at rest (stored on the server), in transit (being transmitted to and from the server), and in use (being processed by the server).Cryptography employs various algorithms to achieve these security goals.
Understanding these algorithms and their applications is crucial for implementing effective server security.
Symmetric-key Cryptography
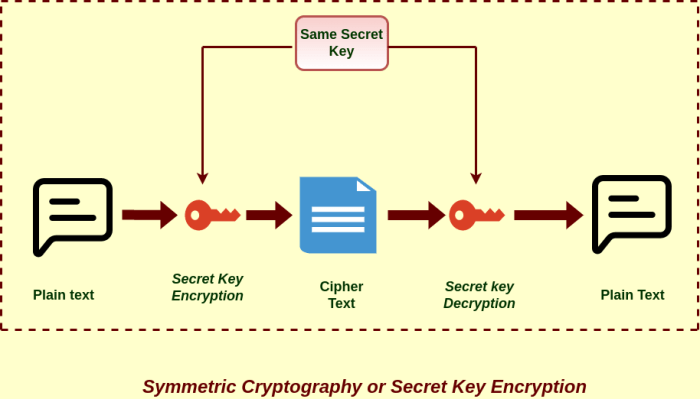
Symmetric-key cryptography uses a single secret key to both encrypt and decrypt data. This approach is generally faster than asymmetric cryptography, making it suitable for encrypting large volumes of data. The security of symmetric-key cryptography hinges entirely on the secrecy of the key; if an attacker obtains the key, they can decrypt the data. Popular symmetric-key algorithms include Advanced Encryption Standard (AES), which is widely used for securing data at rest and in transit, and Triple DES (3DES), an older algorithm still used in some legacy systems.
The strength of a symmetric cipher depends on the key size and the algorithm’s design. A longer key length generally provides stronger security. For example, AES-256, which uses a 256-bit key, is considered highly secure.
Cryptography plays a vital role in securing servers, protecting sensitive data from unauthorized access and manipulation. Understanding its various applications is crucial, and for a deep dive into the subject, check out The Cryptographic Shield: Safeguarding Your Server for practical strategies. Ultimately, effective server security hinges on robust cryptographic implementations, ensuring data confidentiality and integrity.
Asymmetric-key Cryptography
Asymmetric-key cryptography, also known as public-key cryptography, uses two separate keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, while the private key must be kept secret. This allows for secure communication even without prior key exchange. Asymmetric algorithms are typically slower than symmetric algorithms, so they are often used for key exchange, digital signatures, and authentication, rather than encrypting large datasets.
Common asymmetric algorithms include RSA and Elliptic Curve Cryptography (ECC). RSA is based on the difficulty of factoring large numbers, while ECC relies on the mathematical properties of elliptic curves. ECC is generally considered more efficient than RSA for the same level of security.
Hashing Algorithms
Hashing algorithms generate a fixed-size string of characters (a hash) from an input of any size. Hash functions are one-way functions; it’s computationally infeasible to reverse the process and obtain the original input from the hash. Hashing is used for data integrity checks, password storage, and digital signatures. If even a single bit of the input data changes, the resulting hash will be completely different.
This property allows servers to verify the integrity of data received from clients or stored on the server. Popular hashing algorithms include SHA-256 and SHA-3. It’s crucial to use strong, collision-resistant hashing algorithms to prevent attacks that exploit weaknesses in weaker algorithms.
Examples of Server Security Breaches Caused by Weak Cryptography
Several high-profile data breaches have been directly attributed to weaknesses in cryptographic implementations. The Heartbleed vulnerability (2014), affecting OpenSSL, allowed attackers to extract sensitive data from servers due to a flaw in the heartbeat extension. This highlighted the importance of using well-vetted, up-to-date cryptographic libraries and properly configuring them. Another example is the widespread use of weak passwords and insecure hashing algorithms, leading to numerous credential breaches where attackers could easily crack passwords due to insufficient computational complexity.
The use of outdated encryption algorithms, such as DES or weak implementations of SSL/TLS, has also contributed to server compromises. These incidents underscore the critical need for robust, regularly updated, and properly implemented cryptography in server security.
Encryption Techniques for Server Data
Protecting server data, both at rest and in transit, is paramount for maintaining data integrity and confidentiality. Effective encryption techniques are crucial for achieving this goal, employing various algorithms and key management strategies to safeguard sensitive information from unauthorized access. The choice of encryption method depends on factors such as the sensitivity of the data, performance requirements, and the overall security architecture.
Data Encryption at Rest
Data encryption at rest protects data stored on server hard drives, SSDs, or other storage media. This is crucial even when the server is offline or compromised. Common methods include full-disk encryption (FDE) and file-level encryption. FDE, such as BitLocker or FileVault, encrypts the entire storage device, while file-level encryption targets specific files or folders. The encryption process typically involves generating a cryptographic key, using an encryption algorithm to transform the data into an unreadable format (ciphertext), and storing both the ciphertext and (securely) the key.
Decryption reverses this process, using the key to recover the original data (plaintext).
Data Encryption in Transit
Data encryption in transit protects data while it’s being transmitted over a network, such as between a client and a server or between two servers. This is vital to prevent eavesdropping and data breaches during communication. The most common method is Transport Layer Security (TLS), formerly known as Secure Sockets Layer (SSL). TLS uses asymmetric encryption for key exchange and symmetric encryption for data encryption.
The server presents a certificate containing its public key, allowing the client to securely exchange a symmetric session key. This session key is then used to encrypt and decrypt the data exchanged during the session. Other methods include using Virtual Private Networks (VPNs) which encrypt all traffic passing through them.
Comparison of Encryption Algorithms
Several encryption algorithms are available, each with its strengths and weaknesses concerning speed, security, and key management. Symmetric algorithms, like AES (Advanced Encryption Standard) and ChaCha20, are generally faster than asymmetric algorithms but require secure key exchange. Asymmetric algorithms, like RSA and ECC (Elliptic Curve Cryptography), are slower but offer better key management capabilities, as they don’t require the secure exchange of a secret key.
AES is widely considered a strong and efficient symmetric algorithm, while ECC is gaining popularity due to its improved security with smaller key sizes. The choice of algorithm depends on the specific security requirements and performance constraints.
Hypothetical Server-Side Encryption Scheme
This scheme employs a hybrid approach using AES-256 for data encryption and RSA-2048 for key management. Key generation involves generating a unique AES-256 key for each data set. Key distribution utilizes a hierarchical key management system. A master key, protected by hardware security modules (HSMs), is used to encrypt individual data encryption keys (DEKs). These encrypted DEKs are stored separately from the data, possibly in a key management server.
Key rotation involves periodically generating new DEKs and rotating them, invalidating older keys. The frequency of rotation depends on the sensitivity of the data and the threat model. For example, DEKs might be rotated every 90 days, with the old DEKs securely deleted after a retention period. This ensures that even if a key is compromised, the impact is limited to the data encrypted with that specific key.
The master key, however, should be carefully protected and rotated less frequently. A robust auditing system tracks key generation, distribution, and rotation activities to maintain accountability and enhance security.
Authentication and Authorization Mechanisms
Server security relies heavily on robust authentication and authorization mechanisms to verify the identity of users and processes attempting to access server resources and to control their access privileges. These mechanisms, often intertwined with cryptographic techniques, ensure that only authorized entities can interact with the server and its data, mitigating the risk of unauthorized access and data breaches.
Cryptography plays a crucial role in establishing trust and controlling access. Digital signatures and certificates are employed for server authentication, while access control lists (ACLs) and role-based access control (RBAC) leverage cryptographic principles to manage access rights. Public Key Infrastructure (PKI) provides a comprehensive framework for managing these cryptographic elements, bolstering overall server security.
Digital Signatures and Certificates for Server Authentication
Digital signatures, based on asymmetric cryptography, provide a mechanism for verifying the authenticity and integrity of server communications. A server generates a digital signature using its private key, which can then be verified by clients using the corresponding public key. This ensures that the communication originates from the claimed server and hasn’t been tampered with during transit. Certificates, issued by trusted Certificate Authorities (CAs), bind a public key to a specific server identity, facilitating the secure exchange of public keys.
Browsers, for instance, rely on certificates to verify the identity of websites before establishing secure HTTPS connections. If a server’s certificate is invalid or untrusted, the browser will typically display a warning, preventing users from accessing the site. This process relies on a chain of trust, starting with the user’s trust in the root CA and extending to the server’s certificate.
Access Control Lists (ACLs) and Role-Based Access Control (RBAC)
Access Control Lists (ACLs) are traditionally used to define permissions for individual users or groups on specific resources. Each resource (e.g., a file, a database table) has an associated ACL that specifies which users or groups have read, write, or execute permissions. While not inherently cryptographic, ACLs can benefit from cryptographic techniques to ensure the integrity and confidentiality of the ACL itself.
For example, encrypting the ACL with a key known only to authorized administrators prevents unauthorized modification.Role-Based Access Control (RBAC) offers a more granular and manageable approach to access control. Users are assigned to roles (e.g., administrator, editor, viewer), and each role is associated with a set of permissions. This simplifies access management, especially in large systems with many users and resources.
Cryptography can enhance RBAC by securing the assignment of roles and permissions, for example, using digital signatures to verify the authenticity of role assignments or encrypting sensitive role-related data.
Public Key Infrastructure (PKI) Enhancement of Server Security
Public Key Infrastructure (PKI) is a system for creating, managing, storing, distributing, and revoking digital certificates. PKI provides a foundation for secure communication and authentication. It ensures that the server’s public key is authentic and trustworthy. By leveraging digital certificates and certificate authorities, PKI allows servers to establish secure connections with clients, preventing man-in-the-middle attacks. For example, HTTPS relies on PKI to establish a secure connection between a web browser and a web server.
The browser verifies the server’s certificate, ensuring that it is communicating with the intended server and not an imposter. Furthermore, PKI enables the secure distribution of encryption keys and digital signatures, further enhancing server security and data protection.
Secure Communication Protocols
Secure communication protocols are crucial for maintaining the confidentiality, integrity, and authenticity of data exchanged between servers and clients. These protocols employ cryptographic techniques to protect sensitive information from eavesdropping, tampering, and forgery during transmission. Understanding the strengths and weaknesses of different protocols is vital for implementing robust server security.
Several widely adopted protocols ensure secure communication. These include Transport Layer Security (TLS)/Secure Sockets Layer (SSL), Secure Shell (SSH), and Hypertext Transfer Protocol Secure (HTTPS). Each protocol offers a unique set of security features and is susceptible to specific vulnerabilities. Careful selection and proper configuration are essential for effective server security.
TLS/SSL, SSH, and HTTPS Protocols
TLS/SSL, SSH, and HTTPS are the cornerstones of secure communication on the internet. TLS/SSL provides a secure connection between a client and a server, encrypting data in transit. SSH offers a secure way to access and manage remote servers. HTTPS, a secure version of HTTP, ensures secure communication for web traffic. Each protocol uses different cryptographic algorithms and mechanisms to achieve its security goals.
For example, TLS/SSL uses symmetric and asymmetric encryption, while SSH relies heavily on public-key cryptography. HTTPS leverages TLS/SSL to encrypt the communication between a web browser and a web server.
Comparison of Security Features and Vulnerabilities
While all three protocols aim to secure communication, their strengths and weaknesses vary. TLS/SSL is vulnerable to attacks like POODLE and BEAST if not properly configured or using outdated versions. SSH, although robust, can be susceptible to brute-force attacks if weak passwords are used. HTTPS inherits the vulnerabilities of the underlying TLS/SSL implementation. Regular updates and best practices are crucial to mitigate these risks.
Furthermore, the implementation details and configuration of each protocol significantly impact its overall security. A poorly configured TLS/SSL server, for instance, can be just as vulnerable as one not using the protocol at all.
Comparison of TLS 1.2, TLS 1.3, and Other Relevant Protocols
| Protocol | Strengths | Weaknesses | Status |
|---|---|---|---|
| TLS 1.0/1.1 | Widely supported (legacy) | Numerous known vulnerabilities, considered insecure, deprecated | Deprecated |
| TLS 1.2 | Relatively secure, widely supported | Vulnerable to some attacks, slower performance compared to TLS 1.3 | Supported, but transitioning to TLS 1.3 |
| TLS 1.3 | Improved performance, enhanced security, forward secrecy | Less widespread support than TLS 1.2 (though rapidly improving) | Recommended |
| SSH v2 | Strong authentication, encryption, and integrity | Vulnerable to specific attacks if not properly configured; older versions have known vulnerabilities. | Widely used, but updates are crucial |
Data Integrity and Hashing Algorithms
Data integrity, in the context of server security, refers to the assurance that data remains unaltered and accurate during storage and transmission. Maintaining data integrity is crucial because compromised data can lead to incorrect decisions, security breaches, and significant financial or reputational damage. Hashing algorithms play a vital role in ensuring this integrity by providing a mechanism to detect any unauthorized modifications.Data integrity is achieved through the use of cryptographic hash functions.
These functions take an input (data of any size) and produce a fixed-size string of characters, known as a hash value or message digest. Even a tiny change in the input data will result in a drastically different hash value. This property allows us to verify the integrity of data by comparing the hash value of the original data with the hash value of the data after it has been processed or transmitted.
If the values match, it strongly suggests the data has not been tampered with.
Hashing Algorithm Principles
Hashing algorithms, such as SHA-256 and MD5, operate on the principle of one-way functions. This means it is computationally infeasible to reverse the process and obtain the original input data from its hash value. The algorithms use complex mathematical operations to transform the input data into a unique hash. SHA-256, for example, uses a series of bitwise operations, modular additions, and rotations to create a 256-bit hash value.
MD5, while less secure now, employs a similar approach but produces a 128-bit hash. The specific steps involved vary depending on the algorithm, but the core principle of producing a fixed-size, unique output remains consistent.
Comparison of Hashing Algorithms
Several hashing algorithms exist, each with its own strengths and weaknesses regarding collision resistance and security. Collision resistance refers to the difficulty of finding two different inputs that produce the same hash value. A high level of collision resistance is essential for data integrity.
| Algorithm | Hash Size (bits) | Collision Resistance | Security Status |
|---|---|---|---|
| MD5 | 128 | Low – collisions readily found | Deprecated; insecure for cryptographic applications |
| SHA-1 | 160 | Low – practical collisions demonstrated | Deprecated; insecure for cryptographic applications |
| SHA-256 | 256 | High – no known practical collisions | Widely used and considered secure |
| SHA-512 | 512 | High – no known practical collisions | Widely used and considered secure; offers stronger collision resistance than SHA-256 |
While SHA-256 and SHA-512 are currently considered secure, it’s important to note that the security of any cryptographic algorithm is relative and depends on the available computational power. As computing power increases, the difficulty of finding collisions might decrease. Therefore, staying updated on cryptographic best practices and algorithm recommendations is vital for maintaining robust server security. For example, the widespread use of SHA-1 was phased out due to discovered vulnerabilities, highlighting the need for ongoing evaluation and updates in cryptographic techniques.
Key Management and Security Practices
Robust key management is paramount to the overall security of a server environment. Compromised keys can lead to complete system breaches, data theft, and significant financial losses. A well-designed key management system ensures the confidentiality, integrity, and availability of cryptographic keys throughout their lifecycle. This involves careful consideration of key generation, storage, distribution, and rotation.The security of a server’s cryptographic keys directly impacts its resilience against attacks.
Weak key generation methods, insecure storage practices, or flawed distribution mechanisms create vulnerabilities that attackers can exploit. Therefore, employing rigorous key management practices is not merely a best practice, but a fundamental requirement for maintaining server security.
Secure Key Generation
Secure key generation involves using cryptographically secure random number generators (CSPRNGs) to produce keys that are statistically unpredictable. Weak or predictable keys are easily guessed or cracked, rendering encryption useless. CSPRNGs utilize entropy sources, such as system noise or atmospheric data, to create truly random numbers. The length of the key is also critical; longer keys offer significantly stronger resistance to brute-force attacks.
For example, using a 2048-bit RSA key offers substantially more security than a 1024-bit key. The specific algorithm used for key generation should also be chosen based on security requirements and industry best practices. Algorithms like RSA, ECC (Elliptic Curve Cryptography), and DSA (Digital Signature Algorithm) are commonly employed, each with its own strengths and weaknesses.
Secure Key Storage
Storing cryptographic keys securely is crucial to preventing unauthorized access. Keys should never be stored in plain text or easily accessible locations. Hardware Security Modules (HSMs) are specialized devices designed to securely store and manage cryptographic keys. HSMs offer tamper-resistance and protect keys from physical and software attacks. Alternatively, keys can be encrypted and stored in secure, encrypted file systems or databases.
The encryption itself should utilize strong algorithms and keys, managed independently from the keys they protect. Regular backups of keys are also vital, stored securely in a separate location, in case of hardware failure or system compromise. Access control mechanisms, such as role-based access control (RBAC), should strictly limit access to keys to authorized personnel only.
Secure Key Distribution, Cryptography’s Role in Server Security
Securely distributing keys to authorized parties without compromising their confidentiality is another critical aspect of key management. Methods such as key exchange protocols, like Diffie-Hellman, allow two parties to establish a shared secret key over an insecure channel. Public key infrastructure (PKI) systems utilize digital certificates to securely distribute public keys. These certificates are issued by trusted certificate authorities (CAs) and bind a public key to an identity.
Secure channels, such as VPNs or TLS-encrypted connections, should always be used for key distribution. Minimizing the number of copies of a key and employing key revocation mechanisms are further essential security measures. The use of key escrow, while sometimes necessary for regulatory compliance or emergency access, should be carefully considered and implemented with strict controls.
Secure Key Management System Design
A hypothetical secure key management system for a server environment might incorporate the following components:
- A centralized key management server responsible for generating, storing, and distributing keys.
- HSMs for storing sensitive cryptographic keys, providing hardware-level security.
- A robust key rotation policy, regularly updating keys to mitigate the risk of compromise.
- A comprehensive audit trail, logging all key access and management activities.
- Integration with existing security systems, such as identity and access management (IAM) systems, to enforce access control policies.
- A secure communication channel for key distribution, utilizing encryption and authentication protocols.
- Key revocation capabilities to quickly disable compromised keys.
This system would ensure that keys are generated securely, stored in tamper-resistant environments, and distributed only to authorized entities through secure channels. Regular audits and security assessments would be essential to verify the effectiveness of the system and identify potential weaknesses.
Addressing Cryptographic Vulnerabilities
Cryptographic vulnerabilities, when exploited, can severely compromise the security of server-side applications, leading to data breaches, unauthorized access, and significant financial losses. Understanding these vulnerabilities and implementing effective mitigation strategies is crucial for maintaining a robust and secure server environment. This section will examine common vulnerabilities and explore practical methods for addressing them.
Cryptographic systems, while designed to be robust, are not impervious to attack. Weaknesses in implementation, algorithm design, or key management can create exploitable vulnerabilities. These vulnerabilities can be broadly categorized into implementation flaws and algorithmic weaknesses. Implementation flaws often stem from incorrect usage of cryptographic libraries or insecure coding practices. Algorithmic weaknesses, on the other hand, arise from inherent limitations in the cryptographic algorithms themselves, although advancements are constantly being made to address these.
Side-Channel Attacks
Side-channel attacks exploit information leaked during cryptographic operations, such as timing variations, power consumption, or electromagnetic emissions. These attacks bypass the intended security mechanisms by observing indirect characteristics of the system rather than directly attacking the algorithm itself. For example, a timing attack might measure the time taken to perform a cryptographic operation, inferring information about the secret key based on variations in execution time.
Mitigation strategies include using constant-time implementations of cryptographic functions, which ensure that execution time is independent of the input data, and employing techniques like power analysis countermeasures to reduce information leakage.
Padding Oracle Attacks
Padding oracle attacks target the padding schemes used in block cipher modes of operation, such as CBC (Cipher Block Chaining). These attacks exploit predictable error responses from the server when incorrect padding is detected. By carefully crafting malicious requests and observing the server’s responses, an attacker can recover the plaintext or even the encryption key. The vulnerability stems from the server revealing information about the validity of the padding through its error messages.
Mitigation strategies involve using robust padding schemes like PKCS#7, implementing secure error handling that avoids revealing information about the padding, and using authenticated encryption modes like AES-GCM which inherently address padding issues.
Real-World Examples of Exploited Cryptographic Vulnerabilities
The “Heartbleed” bug, discovered in 2014, exploited a vulnerability in the OpenSSL library that allowed attackers to extract sensitive data from affected servers. This vulnerability was a result of an implementation flaw in the handling of TLS/SSL heartbeat messages. Another example is the “POODLE” attack, which exploited vulnerabilities in SSLv3’s padding oracle to decrypt encrypted data. These real-world examples highlight the critical need for robust cryptographic implementation and regular security audits to identify and address potential vulnerabilities before they can be exploited.
Future Trends in Cryptography for Server Security: Cryptography’s Role In Server Security
The landscape of server security is constantly evolving, driven by advancements in computing power and the emergence of new threats. Cryptography, the cornerstone of server security, is no exception. Future trends are shaped by the need to address vulnerabilities exposed by increasingly sophisticated attacks and the potential disruption caused by quantum computing. This section explores these emerging trends and their implications for server security.The rise of quantum computing presents both challenges and opportunities for cryptography.
Quantum computers, with their immense processing power, pose a significant threat to many currently used cryptographic algorithms, potentially rendering them obsolete. However, this challenge has also spurred innovation, leading to the development of new, quantum-resistant cryptographic techniques.
Post-Quantum Cryptography
Post-quantum cryptography (PQC) encompasses cryptographic algorithms designed to be secure against attacks from both classical and quantum computers. Several promising PQC candidates are currently under consideration by standardization bodies like NIST (National Institute of Standards and Technology). These algorithms rely on mathematical problems believed to be intractable even for quantum computers, such as lattice-based cryptography, code-based cryptography, multivariate cryptography, and hash-based cryptography.
For instance, lattice-based cryptography utilizes the difficulty of finding short vectors in high-dimensional lattices, offering a strong foundation for encryption and digital signatures resistant to quantum attacks. The transition to PQC will require significant effort, including algorithm selection, implementation, and integration into existing systems. This transition will be a gradual process, involving careful evaluation and testing to ensure interoperability and security.
Quantum Computing’s Impact on Server Security
Quantum computing’s impact on server security is multifaceted. While it threatens existing cryptographic systems, it also offers potential benefits. On the one hand, quantum computers could break widely used public-key cryptography algorithms like RSA and ECC, compromising the confidentiality and integrity of server data and communications. This would necessitate a complete overhaul of security protocols and infrastructure. On the other hand, quantum-resistant algorithms, once standardized and implemented, will offer enhanced security against both classical and quantum attacks.
Furthermore, quantum key distribution (QKD) offers the potential for unconditionally secure communication, leveraging the principles of quantum mechanics to detect eavesdropping attempts. However, QKD faces practical challenges related to infrastructure and scalability, limiting its immediate applicability to widespread server deployments.
Potential Future Advancements in Cryptography
The field of cryptography is constantly evolving, and several potential advancements hold promise for enhancing server security.
- Homomorphic Encryption: This allows computations to be performed on encrypted data without decryption, enabling secure cloud computing and data analysis. Imagine securely analyzing sensitive medical data in the cloud without ever decrypting it.
- Fully Homomorphic Encryption (FHE): A more advanced form of homomorphic encryption that allows for arbitrary computations on encrypted data, opening up even more possibilities for secure data processing.
- Differential Privacy: This technique adds carefully designed noise to data before release, allowing for statistical analysis while preserving individual privacy. This could be particularly useful for securing server logs or user data.
- Zero-Knowledge Proofs: These allow one party to prove the truth of a statement without revealing any information beyond the truth of the statement itself. This is valuable for authentication and authorization, allowing users to prove their identity without disclosing their password.
These advancements, along with continued refinement of existing techniques, will be crucial in ensuring the long-term security of server systems in an increasingly complex threat landscape. The development and adoption of these technologies will require significant research, development, and collaboration across industry and academia.
Outcome Summary
Ultimately, securing servers relies heavily on a multi-layered approach to cryptography. While no single solution guarantees absolute protection, a well-implemented strategy incorporating strong encryption, robust authentication, secure protocols, and proactive vulnerability management provides a significantly enhanced level of security. Staying informed about emerging threats and advancements in cryptographic techniques is crucial for maintaining a strong security posture in the ever-changing threat landscape.
By understanding and effectively utilizing the power of cryptography, organizations can significantly reduce their risk and protect valuable data and systems.
Questions Often Asked
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption.
How often should encryption keys be rotated?
Key rotation frequency depends on the sensitivity of the data and the threat landscape. Best practices suggest regular rotation, potentially every few months or even more frequently for highly sensitive data.
What are some common examples of cryptographic vulnerabilities?
Common vulnerabilities include weak key generation, improper key management, known vulnerabilities in specific algorithms (e.g., outdated TLS versions), and side-channel attacks.
What is post-quantum cryptography?
Post-quantum cryptography refers to cryptographic algorithms that are believed to be secure even against attacks from quantum computers.