Cryptography for Server Admins: A Comprehensive Overview. Securing your server infrastructure is paramount in today’s digital landscape, demanding a robust understanding of cryptographic principles. This guide delves into the essential aspects of cryptography, equipping server administrators with the knowledge to effectively protect their systems from increasingly sophisticated threats. We’ll explore symmetric and asymmetric encryption, hashing algorithms, digital certificates, secure communication protocols, and crucial key management practices, providing practical examples and best practices throughout.
From understanding the nuances of AES and RSA to implementing TLS/SSL certificates and mitigating common cryptographic attacks, this overview provides a solid foundation for building a secure and resilient server environment. We’ll also address the critical role of key management, exploring best practices for generation, storage, rotation, and recovery, emphasizing the importance of protecting your cryptographic keys as diligently as you protect your data.
Introduction to Cryptography for Server Administration

Cryptography is the cornerstone of modern server security, providing the essential tools to protect data confidentiality, integrity, and authenticity. Understanding its fundamental principles is crucial for any server administrator responsible for securing sensitive information and maintaining system integrity. This section will explore the core concepts and techniques used in server-side cryptography.Cryptography employs various algorithms to achieve its security goals.
These algorithms are mathematical functions that transform data in specific ways, making it unintelligible to unauthorized parties. The strength of these algorithms is critical, as they form the basis of secure communication and data protection within server environments. Proper selection and implementation are vital for effective server security.
Fundamental Cryptographic Concepts
Cryptography relies on several key concepts. Confidentiality ensures that only authorized parties can access sensitive data. This is achieved through encryption, which transforms readable data (plaintext) into an unreadable format (ciphertext). Integrity guarantees that data has not been tampered with during transmission or storage. This is often implemented using hash functions or digital signatures.
Authenticity verifies the origin and identity of data, ensuring it comes from a trusted source and hasn’t been forged. Digital signatures are a common method for establishing authenticity. Non-repudiation prevents senders from denying they sent a message, crucial for accountability.
Types of Cryptographic Algorithms
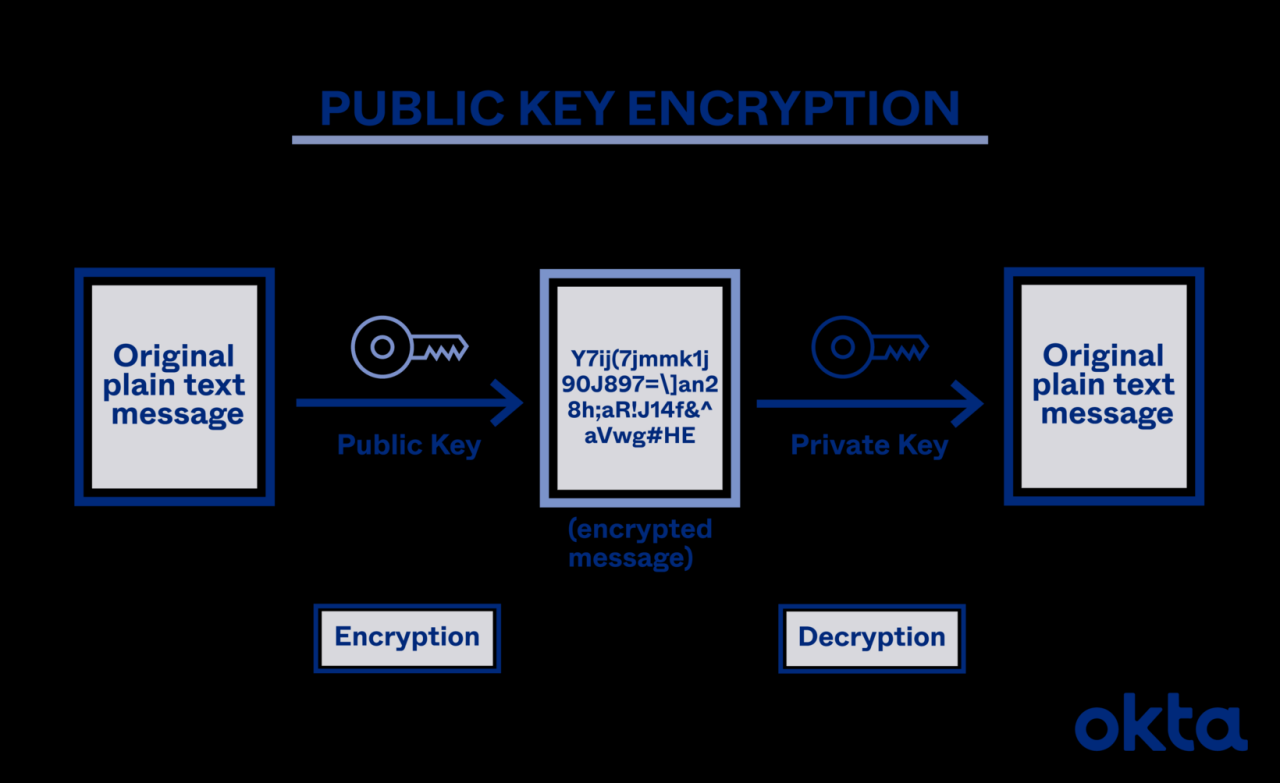
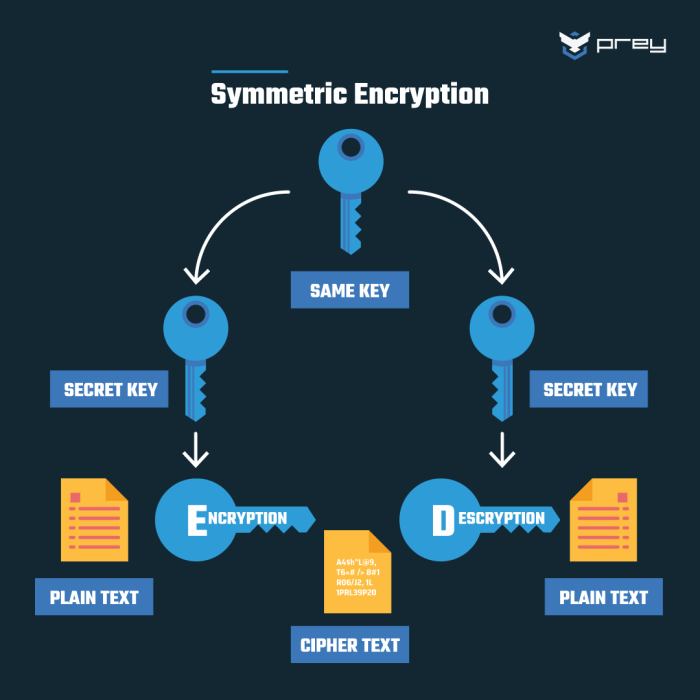
Server environments utilize various cryptographic algorithms, categorized broadly into symmetric and asymmetric encryption. Symmetric encryption uses the same key for both encryption and decryption, offering speed but requiring secure key exchange. Asymmetric encryption, also known as public-key cryptography, uses a pair of keys – a public key for encryption and a private key for decryption. This eliminates the need for secure key exchange, offering greater flexibility and security for key management.
Hash functions, one-way functions that produce a fixed-size output (hash) from any input, are used for data integrity checks and password storage.
Examples of Cryptographic Algorithms
Symmetric algorithms include Advanced Encryption Standard (AES), a widely used and robust algorithm, and Triple DES (3DES), an older but still relevant algorithm. Asymmetric algorithms commonly used include RSA, known for its widespread use in digital signatures and secure communication, and Elliptic Curve Cryptography (ECC), which offers comparable security with smaller key sizes, making it efficient for resource-constrained environments. Popular hash functions include SHA-256 and SHA-3, offering varying levels of security and collision resistance.
Common Cryptographic Protocols, Cryptography for Server Admins: A Comprehensive Overview
Several protocols leverage cryptographic algorithms to provide secure communication and data exchange. Transport Layer Security (TLS), the successor to Secure Sockets Layer (SSL), is widely used to encrypt web traffic (HTTPS) and other network communications. It employs symmetric encryption for data transfer and asymmetric encryption for key exchange. Secure Shell (SSH) is a crucial protocol for secure remote login and command execution.
It utilizes public-key cryptography for authentication and symmetric encryption for secure data transmission. Secure Copy Protocol (SCP) utilizes SSH for secure file transfer. Internet Protocol Security (IPsec) provides secure communication at the network layer, often used in Virtual Private Networks (VPNs).
Symmetric-key Cryptography
Symmetric-key cryptography utilizes a single, secret key for both encryption and decryption of data. This shared secret must be securely exchanged between communicating parties before any encrypted communication can occur. The strength of symmetric-key cryptography hinges on the secrecy and length of this key, as well as the robustness of the underlying algorithm. Its primary advantage lies in its speed and efficiency compared to asymmetric methods.Symmetric-key encryption involves transforming plaintext into ciphertext using the secret key.
The decryption process reverses this transformation, using the same key to recover the original plaintext. This fundamental principle underpins a wide range of security applications in server administration.
Symmetric-key Algorithm Comparison: AES, DES, 3DES
Several symmetric-key algorithms exist, each with its strengths and weaknesses. AES (Advanced Encryption Standard), DES (Data Encryption Standard), and 3DES (Triple DES) are prominent examples. Understanding their differences is crucial for selecting the appropriate algorithm for specific security needs. AES is currently the most widely used and recommended standard, while DES and 3DES are considered legacy algorithms, vulnerable to modern cryptanalysis techniques.
AES: Advanced Encryption Standard
AES is a block cipher that operates on 128-bit blocks of data, using keys of 128, 192, or 256 bits. The longer the key, the greater the security. AES’s strength lies in its combination of speed, security, and relatively low resource consumption, making it suitable for a wide range of applications from encrypting sensitive data at rest to securing network communications.
Its widespread adoption and rigorous testing have established it as a highly trusted encryption standard.
DES: Data Encryption Standard
DES, an older algorithm, uses a 56-bit key and operates on 64-bit blocks. Its relatively short key length makes it vulnerable to brute-force attacks with modern computing power; therefore, it’s no longer considered secure for most applications.
3DES: Triple DES
DES attempts to enhance the security of DES by applying the DES algorithm three times with either two or three different keys. While more secure than single DES, it is significantly slower than AES and is also considered a legacy algorithm. Its complexity and performance limitations have largely led to its replacement by AES.
Practical Examples of Symmetric-key Cryptography in Server Security
Symmetric-key cryptography finds extensive use in securing servers. Examples include encrypting files stored on servers (data at rest), securing network traffic between servers (data in transit), and protecting database contents. File system encryption, using tools like LUKS (Linux Unified Key Setup), often employs symmetric encryption to protect data on hard drives. Virtual Private Networks (VPNs) commonly use symmetric encryption protocols like IPsec to secure communication between clients and servers.
Additionally, many database systems utilize symmetric encryption to protect sensitive data.
Comparison Table: AES, DES, and 3DES
| Algorithm | Key Size (bits) | Block Size (bits) | Strengths | Weaknesses |
|---|---|---|---|---|
| AES | 128, 192, 256 | 128 | Fast, secure, widely adopted, strong against known attacks | Requires careful key management |
| DES | 56 | 64 | Simple, relatively fast (by older standards) | Vulnerable to brute-force attacks, insecure for modern applications |
| 3DES | 112 or 168 | 64 | More secure than DES | Slower than AES, complex, considered a legacy algorithm |
Asymmetric-key Cryptography
Asymmetric-key cryptography, also known as public-key cryptography, forms the bedrock of many modern secure systems. Unlike symmetric-key cryptography, which relies on a single secret key shared between parties, asymmetric cryptography utilizes a pair of keys: a public key and a private key. This key pair is mathematically linked, allowing for secure communication and authentication without the need to exchange a secret key beforehand.
This fundamental difference significantly enhances security and scalability, especially in large networks.
Public-Key Cryptography Principles
Public-key cryptography operates on the principle of a one-way function, a mathematical operation easy to compute in one direction but computationally infeasible to reverse without possessing specific information (the private key). This one-way function underpins the security of the entire system. The public key can be freely distributed, used for encryption and verification, while the private key remains strictly confidential, used for decryption and signing.
The security relies on the computational difficulty of deriving the private key from the public key. Algorithms like RSA and ECC leverage complex mathematical problems, such as factoring large numbers or solving the elliptic curve discrete logarithm problem, to achieve this.
RSA and ECC in Server Security
RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are the two most prevalent asymmetric encryption algorithms. RSA’s security is based on the difficulty of factoring the product of two large prime numbers. It’s widely used for secure communication, digital signatures, and key exchange protocols like TLS/SSL, which secures web traffic. ECC, on the other hand, relies on the elliptic curve discrete logarithm problem.
It offers comparable security levels to RSA but with significantly smaller key sizes, resulting in faster performance and reduced computational overhead. This makes ECC particularly suitable for resource-constrained devices and environments where speed and efficiency are paramount, such as mobile applications and embedded systems used in servers. Many modern servers utilize ECC for TLS/SSL handshakes and other security functions due to its efficiency advantages.
Digital Signatures: A Step-by-Step Explanation
Digital signatures provide authentication and integrity verification for digital data. They ensure that a message originated from a specific sender and hasn’t been tampered with during transmission. The process involves the following steps:
- Hashing: The sender computes a cryptographic hash of the message. A hash function produces a fixed-size output (a hash) from an input of any size. Even a small change in the message drastically alters the hash.
- Signing: The sender then signs the hash using their private key. This creates the digital signature.
- Transmission: The sender transmits the original message and the digital signature to the recipient.
- Verification: The recipient uses the sender’s public key to verify the signature. This involves computing the hash of the received message and comparing it to the hash extracted from the verified signature. If the hashes match, the signature is valid, confirming the message’s authenticity and integrity.
A mismatch indicates either tampering with the message or an invalid signature.
Secure File Transfer Using Asymmetric Encryption: A Hypothetical Scenario
Imagine a scenario where a server administrator needs to securely transfer a configuration file to a remote server. Using asymmetric encryption, this can be achieved as follows:
- Key Generation: The remote server generates a public-private key pair. The public key is then made available to the administrator (perhaps through a secure channel).
- Encryption: The administrator encrypts the configuration file using the remote server’s public key. Only the corresponding private key can decrypt it.
- Transmission: The encrypted file is transmitted to the remote server.
- Decryption: The remote server uses its private key to decrypt the file, ensuring only the intended recipient can access the configuration.
This method ensures confidentiality, as only the remote server possessing the private key can decrypt the file. The administrator does not need to share a secret key with the remote server, enhancing security.
Hashing Algorithms
Hashing algorithms are fundamental to server security, providing a one-way function to transform data of any size into a fixed-size string of characters, called a hash. This process is crucial for ensuring data integrity and securing passwords, among other critical applications. Unlike encryption, hashing is irreversible; it’s computationally infeasible to retrieve the original data from its hash. This irreversibility is key to its security properties.Hashing algorithms work by employing complex mathematical operations on the input data.
The resulting hash is highly sensitive to even minor changes in the input; a single bit alteration will drastically alter the output hash. This characteristic is exploited to detect data tampering and verify data authenticity. The strength of a hashing algorithm is measured by its resistance to various attacks, including collision attacks (finding two different inputs that produce the same hash) and pre-image attacks (finding the input that produces a given hash).
SHA-256, SHA-3, and MD5 Comparison
SHA-256 (Secure Hash Algorithm 256-bit), SHA-3 (Secure Hash Algorithm 3), and MD5 (Message Digest Algorithm 5) represent different generations of hashing algorithms, each with varying levels of security. MD5, an older algorithm, is now considered cryptographically broken due to vulnerabilities to collision attacks. This means attackers can create two different files with the same MD5 hash, undermining its integrity-checking capabilities.
SHA-256, a member of the SHA-2 family, offers significantly improved security, although it’s still susceptible to brute-force attacks given enough computational power. SHA-3, designed with a different underlying structure than SHA-2, is considered more resistant to potential future attacks and is generally recommended for new applications. The choice of algorithm depends on the security requirements and the sensitivity of the data being hashed.
SHA-3 is the current recommendation for strong security needs.
Hashing for Password Storage
Storing passwords in plain text is a catastrophic security risk. Hashing provides a secure alternative. When a user registers, their password is hashed using a strong algorithm like SHA-256 or SHA-3, and only the hash is stored in the database. When the user attempts to log in, their entered password is hashed, and the resulting hash is compared to the stored hash.
A match confirms authentication without ever revealing the actual password. To further enhance security, a salt (a random string) is typically concatenated with the password before hashing. This prevents attackers from using pre-computed rainbow tables to crack passwords, even if the hashing algorithm is compromised. The salt is stored alongside the hash, ensuring each user has a unique hashed password.
Hashing for Data Integrity Checks
Hashing is crucial for verifying data integrity. By generating a hash of a file or data set, any changes to the data will result in a different hash. This allows for the detection of unauthorized modifications or corruption. For example, software distribution often employs hashing. The software vendor provides a hash of the software package.
Users can then independently generate a hash of the downloaded software and compare it to the vendor’s hash. A mismatch indicates tampering or corruption during download or transfer. This mechanism ensures that the downloaded software is authentic and unaltered.
Best Practices for Hashing Algorithm Selection and Implementation
Selecting and implementing hashing algorithms requires careful consideration. The following best practices should be followed:
Choosing the right algorithm is paramount. For optimal security, SHA-3 is generally recommended for new systems. Avoid using outdated algorithms like MD5. The selection should also consider the performance implications; SHA-512, while secure, might be slower than SHA-256 depending on the workload.
Always use a sufficient salt length to prevent rainbow table attacks. A salt of at least 128 bits is generally recommended. The salt should be randomly generated and unique for each password or data set.
Regularly review and update hashing algorithms as new vulnerabilities are discovered and better algorithms are developed. Staying current with cryptographic best practices is essential for maintaining robust security.
Implement key derivation functions (KDFs) like PBKDF2 or Argon2 to further strengthen password hashing. KDFs increase the computational cost of cracking passwords, making brute-force attacks significantly more difficult.
Consider using a key stretching technique to significantly increase the computational cost of generating a hash. This makes it exponentially harder for attackers to crack the passwords.
Digital Certificates and PKI
Digital certificates are the cornerstone of secure server communication, providing a mechanism to verify the identity of a server and encrypt communication channels. They leverage Public Key Infrastructure (PKI) to establish trust and ensure data integrity. Understanding digital certificates and PKI is crucial for any server administrator responsible for securing online services.Digital certificates are essentially electronic documents that bind a public key to an entity’s identity.
This binding is cryptographically verified, allowing clients to trust that they are communicating with the legitimate server they intend to connect to. This trust is established through a chain of trust, ultimately anchored in trusted root Certificate Authorities (CAs).
Components of a Public Key Infrastructure (PKI)
A PKI comprises several key components working in concert to establish and manage trust. These components ensure the secure issuance, management, and revocation of digital certificates. Without a robust PKI, the security provided by digital certificates would be significantly weakened.
- Certificate Authority (CA): A trusted third party responsible for issuing and managing digital certificates. CAs verify the identity of certificate applicants before issuing certificates. Examples of well-known CAs include DigiCert, Let’s Encrypt, and Sectigo.
- Registration Authority (RA): An optional component that assists the CA in verifying the identity of certificate applicants. RAs handle the initial vetting process, reducing the workload on the CA.
- Certificate Repository: A database or directory that stores issued certificates, allowing clients to access and verify them. This repository facilitates the retrieval of certificates for authentication and encryption.
- Certificate Revocation List (CRL): A list of certificates that have been revoked by the CA. This is a crucial mechanism for managing compromised certificates, ensuring that invalid certificates are not trusted.
- Online Certificate Status Protocol (OCSP): An alternative to CRLs, OCSP allows clients to verify the status of a certificate in real-time by querying the CA. This offers more up-to-date revocation information compared to CRLs.
PKI in Server Identity Verification
PKI plays a critical role in verifying server identities. When a client connects to a server secured with an SSL/TLS certificate, the client verifies the certificate’s authenticity through the CA’s chain of trust. This process ensures that the server is who it claims to be, preventing man-in-the-middle attacks. For example, when accessing a banking website, the browser verifies the website’s SSL/TLS certificate issued by a trusted CA, confirming the authenticity of the bank’s server before establishing a secure connection.
Obtaining and Installing a Server SSL/TLS Certificate
The process of obtaining and installing a server SSL/TLS certificate involves several steps. The specific steps may vary depending on the CA and the server’s operating system, but the general process remains consistent.
- Generate a Certificate Signing Request (CSR): This request contains information about the server, including its public key and domain name. This CSR is submitted to the chosen CA.
- Submit the CSR to a CA: The chosen CA verifies the information in the CSR, often requiring domain verification to ensure that the applicant controls the domain. This verification may involve email verification, DNS record verification, or file verification.
- Receive the Certificate: Upon successful verification, the CA issues the SSL/TLS certificate, which is digitally signed by the CA. This certificate binds the server’s public key to its identity.
- Install the Certificate: The certificate is installed on the server’s web server software (e.g., Apache, Nginx). This involves configuring the web server to use the certificate for secure communication.
- Verify the Installation: After installation, it’s crucial to verify the certificate’s proper installation using tools like online SSL checkers. This ensures that the certificate is correctly configured and that the website is served securely.
For instance, Let’s Encrypt offers a free, automated process for obtaining and installing SSL/TLS certificates. Tools like Certbot simplify this process, automating the generation of CSRs, submission to Let’s Encrypt, and installation on the server. Other CAs provide similar automated processes, although they may charge for their services.
Secure Communication Protocols
Secure communication protocols are fundamental to protecting data transmitted between servers and clients. These protocols employ a range of cryptographic techniques to ensure confidentiality, integrity, and authenticity of data in transit. Understanding their security features and applications is crucial for any server administrator responsible for maintaining secure systems.
TLS/SSL Security Features
TLS (Transport Layer Security) and its predecessor, SSL (Secure Sockets Layer), are widely used protocols that provide secure communication over a network. They establish an encrypted connection between a client and a server, protecting data from eavesdropping and tampering. Key security features include:
- Symmetric Encryption: After establishing a secure connection, TLS/SSL uses symmetric encryption algorithms (like AES) to encrypt and decrypt data efficiently.
- Asymmetric Encryption: The initial handshake uses asymmetric encryption (like RSA) to exchange a symmetric key securely without ever transmitting it in plain text.
- Message Authentication Codes (MACs): TLS/SSL employs MACs to verify data integrity, ensuring that data hasn’t been altered during transmission.
- Certificate-based Authentication: Server authentication is typically performed using digital certificates issued by trusted Certificate Authorities (CAs), verifying the server’s identity.
SSH Security Features
SSH (Secure Shell) is a cryptographic network protocol used for secure remote login and other secure network services over an unsecured network. Its core security relies on:
- Public-key Cryptography: SSH uses public-key cryptography for authentication and key exchange, eliminating the need to transmit passwords in plain text.
- Symmetric Encryption: After authentication, SSH employs symmetric encryption algorithms to secure the communication channel.
- Integrity Checks: SSH incorporates mechanisms to verify data integrity and protect against tampering.
HTTPS Security Features
HTTPS (Hypertext Transfer Protocol Secure) is an extension of HTTP that uses TLS/SSL to encrypt communication between a web browser and a web server. It leverages the security features of TLS/SSL, providing confidentiality, integrity, and authenticity for web traffic. This ensures that sensitive data, such as passwords and credit card information, is protected during online transactions.
Comparison of Security Mechanisms
TLS/SSL, SSH, and HTTPS all employ cryptographic techniques to secure communication, but their specific mechanisms and applications differ. TLS/SSL and HTTPS focus on securing application-layer data, while SSH primarily secures remote login and other network services. HTTPS builds upon the foundation of HTTP, adding the security layer provided by TLS/SSL. SSH often utilizes public-key cryptography for authentication, while TLS/SSL typically relies on certificate-based authentication.
Examples of Protocol Usage
- TLS/SSL: Secures web browsing (HTTPS), email (IMAP/SMTP over SSL), and online banking transactions.
- SSH: Enables secure remote access to servers, secure file transfer (SFTP), and secure network management.
- HTTPS: Protects sensitive data transmitted over the web, ensuring confidentiality and integrity for e-commerce and other online services.
Key Differences and Use Cases
| Protocol | Primary Use Case | Authentication Method | Encryption Type | Data Protected |
|---|---|---|---|---|
| TLS/SSL | Secure application-layer communication | Certificate-based (primarily) | Symmetric (AES), Asymmetric (RSA) | Data in transit between client and server |
| SSH | Secure remote login and network services | Public-key cryptography | Symmetric | Remote login sessions, file transfers |
| HTTPS | Secure web communication | Certificate-based | Symmetric (AES), Asymmetric (RSA) | Web traffic, including sensitive data |
Implementing Cryptography on Servers
Implementing cryptography effectively on your servers is crucial for maintaining data integrity, confidentiality, and the overall security of your systems. This section details the practical steps involved in securing your server infrastructure using cryptographic techniques. We’ll cover configuring SSL/TLS certificates for web servers, securing SSH access, implementing disk encryption, and finally, provide a checklist of best practices to ensure comprehensive server security.
SSL/TLS Certificate Configuration on a Web Server
Configuring SSL/TLS certificates on a web server involves obtaining a certificate, configuring your web server to use it, and ensuring proper chain validation. The process varies slightly depending on the web server software (Apache, Nginx, etc.) but generally involves these steps: obtaining a certificate from a Certificate Authority (CA) or generating a self-signed certificate (for testing environments only), configuring the server to use the certificate and private key, and testing the configuration to ensure secure communication (HTTPS) is established.
For example, in Apache, this typically involves placing the certificate and key files in specific directories and modifying the Apache configuration file (httpd.conf or a virtual host configuration file) to enable SSL and specify the paths to the certificate and key. Nginx configuration is similar, involving modification of the server block configuration file to specify the SSL certificate and key locations.
Securing SSH Access to a Server
Securing SSH access involves using strong passwords or, preferably, SSH keys for authentication. SSH keys provide a more secure alternative to passwords, eliminating the risk of password guessing or brute-force attacks. The process typically involves generating an SSH key pair (public and private key) on the client machine, copying the public key to the authorized_keys file on the server, and then using the private key to authenticate.
Additional security measures include restricting SSH access by IP address, disabling password authentication entirely, and regularly updating the SSH server software to patch any known vulnerabilities. For instance, configuring `PermitRootLogin no` in the SSH server configuration file (`sshd_config`) prevents direct root login, forcing users to use `sudo` for elevated privileges, which provides an additional layer of security.
Data Encryption at Rest Using Disk Encryption
Disk encryption protects data stored on a server’s hard drive even if the physical server is compromised. This is achieved using cryptographic techniques to encrypt the entire hard drive, rendering the data unreadable without the decryption key. Common methods include using operating system-level encryption tools such as BitLocker (Windows) or FileVault (macOS), or using third-party encryption solutions. The process typically involves selecting an encryption algorithm (e.g., AES-256), setting up a strong encryption key, and then encrypting the entire drive.
The decryption key must be securely stored and managed; losing this key renders the data irretrievably lost. For Linux systems, tools like LUKS (Linux Unified Key Setup) provide robust disk encryption capabilities.
Mastering cryptography is crucial for server admins, ensuring data integrity and security. However, the constant digital demands can lead to burnout; taking breaks is essential, and you might find helpful tips in this article on digital detox: 9 Trik Jitu Digital Detox: Boost Produktivitas dalam 14 Hari. Returning to our topic, understanding encryption algorithms and key management practices is paramount for effective server administration and preventing data breaches.
Security Best Practices Checklist for Implementing Cryptography on Servers
Implementing cryptography effectively requires a multifaceted approach. A comprehensive checklist ensures all crucial aspects are addressed.
- Use strong, unique passwords or SSH keys for all accounts.
- Regularly update server software and security patches.
- Enable disk encryption to protect data at rest.
- Use strong cryptographic algorithms (e.g., AES-256 for symmetric encryption, RSA-2048 or higher for asymmetric encryption).
- Implement robust access control measures, limiting access to only authorized personnel.
- Regularly audit security logs to detect and respond to potential threats.
- Use a reputable Certificate Authority (CA) for SSL/TLS certificates.
- Employ a strong random number generator for key generation.
- Implement regular security assessments and penetration testing.
- Establish a comprehensive incident response plan to handle security breaches.
Cryptographic Attacks and Vulnerabilities
The security of any cryptographic system relies on the strength of its algorithms and the diligence of its implementation. However, even the most robust systems are susceptible to various attacks, exploiting weaknesses in algorithms, implementations, or key management. Understanding these vulnerabilities is crucial for server administrators to effectively protect their systems and data. This section details common attacks and vulnerabilities, emphasizing the importance of robust security practices.
Common Cryptographic Attacks
Cryptographic attacks aim to compromise the confidentiality, integrity, or authenticity of data protected by cryptographic techniques. Several categories of attacks exist, each exploiting different weaknesses.
- Brute-force attacks: These attacks involve systematically trying every possible key until the correct one is found. The effectiveness of a brute-force attack depends on the key length and the computational power available to the attacker. Longer keys exponentially increase the time required for a successful attack.
- Man-in-the-middle (MITM) attacks: In a MITM attack, an attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. This attack often relies on exploiting weaknesses in authentication or encryption protocols.
- Known-plaintext attacks: These attacks leverage knowledge of both the plaintext (original message) and the corresponding ciphertext (encrypted message) to deduce the encryption key. The success of this attack depends on the algorithm’s resilience to such attacks.
- Chosen-plaintext attacks: Similar to known-plaintext attacks, but the attacker can choose the plaintext to be encrypted and observe the resulting ciphertext. This allows for more targeted analysis of the encryption algorithm.
- Side-channel attacks: These attacks exploit information leaked through channels other than the intended communication path. Examples include timing attacks (measuring the time taken for cryptographic operations) and power analysis (monitoring power consumption during cryptographic operations).
Vulnerabilities Associated with Weak Cryptographic Algorithms and Implementations
Using outdated or poorly implemented cryptographic algorithms significantly increases the risk of successful attacks. Weak algorithms may have known vulnerabilities that can be easily exploited, while poor implementations can introduce unintended weaknesses. For example, improper padding in encryption schemes can create vulnerabilities that allow attackers to recover plaintext. The use of weak random number generators can also compromise the security of cryptographic keys.
Key Management and Secure Storage
Secure key management is paramount to the overall security of a cryptographic system. Compromised keys render the entire system vulnerable. This includes the secure generation, storage, distribution, and rotation of keys. Keys should be stored using hardware security modules (HSMs) or other secure methods to prevent unauthorized access. Regular key rotation helps mitigate the impact of any key compromise.
Real-World Incidents Involving Cryptographic Vulnerabilities
Several high-profile incidents highlight the consequences of cryptographic vulnerabilities. The Heartbleed bug (CVE-2014-0160), a vulnerability in OpenSSL, allowed attackers to extract sensitive data, including private keys, from affected servers. The widespread adoption of OpenSSL made this vulnerability particularly damaging. The widespread use of weak encryption algorithms in various systems has also led to numerous data breaches. These incidents underscore the importance of using strong, well-vetted cryptographic algorithms and implementing them securely.
Key Management and Security Best Practices
Effective key management is paramount for the security of any cryptographic system. Compromised keys render even the strongest encryption algorithms vulnerable. This section details best practices for generating, storing, protecting, and rotating cryptographic keys, emphasizing the critical role of key escrow and hardware security modules (HSMs).Key management encompasses the entire lifecycle of a cryptographic key, from its generation to its eventual destruction.
Neglecting any aspect of this lifecycle can significantly weaken the overall security posture. Robust key management practices are crucial for maintaining data confidentiality, integrity, and authenticity.
Key Generation and Storage
Strong key generation involves using cryptographically secure random number generators (CSPRNGs) to ensure unpredictability. Keys should be of sufficient length to withstand brute-force attacks; the recommended length varies depending on the algorithm and the sensitivity of the data being protected. For example, AES-256 requires a 256-bit key, while RSA keys are typically much longer. Stored keys must be protected from unauthorized access using strong encryption, access control mechanisms, and secure storage locations.
Never store keys directly in plain text. Employing robust encryption, such as AES-256 with a strong key, is crucial.
Key Rotation and Expiration
Regular key rotation is a critical security measure. Periodically replacing cryptographic keys minimizes the impact of a potential compromise. If a key is compromised, only the data encrypted with that specific key is at risk. A well-defined key rotation schedule, coupled with automatic key replacement mechanisms, reduces the administrative burden and ensures timely updates. The frequency of key rotation depends on the sensitivity of the data and the threat landscape; more sensitive data may require more frequent rotations.
For example, session keys used for secure communication might be rotated every few hours, while long-term encryption keys for data at rest might be rotated annually.
Key Escrow and Recovery Mechanisms
Key escrow involves storing a copy of a cryptographic key in a secure location, typically accessible by authorized personnel in case of emergencies, such as key loss or employee turnover. While providing a recovery mechanism, key escrow also introduces security risks, as it creates a potential point of compromise. Therefore, stringent access controls and robust security measures are essential for managing key escrow systems.
Multi-party computation techniques can mitigate the risk by requiring multiple parties to collaborate to access the key. Implementing a robust key recovery process, including well-defined procedures and authorized personnel, is crucial.
Hardware Security Modules (HSMs)
Hardware Security Modules (HSMs) are specialized hardware devices designed to protect cryptographic keys and perform cryptographic operations securely. HSMs provide a physically secure environment for key storage and processing, reducing the risk of compromise. They often incorporate tamper-resistant mechanisms to prevent unauthorized access and modification. HSMs are commonly used in high-security environments, such as financial institutions and government agencies, where the protection of cryptographic keys is paramount.
They offer a high level of security and are often integrated into existing security infrastructures. Using an HSM significantly reduces the risk associated with storing and managing cryptographic keys.
Recommendations for Secure Key Management
The following recommendations summarize best practices for secure key management:
- Use cryptographically secure random number generators (CSPRNGs) for key generation.
- Employ strong encryption algorithms and sufficient key lengths.
- Implement robust access control mechanisms to restrict access to keys.
- Store keys securely, ideally within a Hardware Security Module (HSM).
- Establish a regular key rotation schedule based on risk assessment.
- Develop and implement a comprehensive key escrow and recovery plan.
- Regularly audit key management processes and security controls.
- Maintain detailed documentation of key management procedures.
- Use strong password management practices to protect access to key management systems.
- Keep software and firmware of key management systems up-to-date.
Ultimate Conclusion: Cryptography For Server Admins: A Comprehensive Overview
Mastering cryptography is no longer optional for server administrators; it’s a necessity. This comprehensive overview has armed you with the foundational knowledge and practical strategies to fortify your server security posture. By understanding the intricacies of various cryptographic algorithms, protocols, and best practices, you can confidently navigate the complex world of server security, proactively mitigating risks and ensuring the confidentiality, integrity, and availability of your critical data and systems.
Remember that ongoing vigilance and adaptation to evolving threats are key to maintaining a robust security framework.
FAQs
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, offering speed but requiring secure key exchange. Asymmetric encryption uses a pair of keys (public and private), enhancing security but being slower.
How often should I rotate my cryptographic keys?
Key rotation frequency depends on the sensitivity of the data and the risk level. Regular rotation, often annually or even more frequently for high-risk systems, is crucial to minimize the impact of potential compromise.
What are some common cryptographic attacks I should be aware of?
Common attacks include brute-force attacks, man-in-the-middle attacks, and various forms of cryptanalysis targeting weaknesses in algorithms or implementations. Staying updated on security vulnerabilities is essential.
What is a Hardware Security Module (HSM)?
An HSM is a physical device designed to securely store and manage cryptographic keys. They offer enhanced protection against theft or unauthorized access compared to software-based key management.